CISA, FBI Warn Organizations to Protect Against State-Sponsored Malware

The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) issued a joint statement to advise organizations to prepare for increased cyber activity in the wake of the Russian invasion of Ukraine. According to the advisory, there is a risk that Russian cyber attacks will spread to government and business networks in the US and other NATO countries as a result of the growing international support for Ukraine and anticipated retaliation for sanctions imposed on Russia.
Threat actors deployed destructive malware against organizations in Ukraine in the lead up to the invasion. This included the wipers WhisperGate and HermeticWiper, designed to permanently corrupt data in infected hosts, rendering them unbootable. Both strains of malware masquerade as ransomware but have no decryption or data-recovery capabilities.
In response, CISA and the FBI urge all organizations to adopt a heightened posture towards cybersecurity and protecting their critical assets. Specifically, organizations are advised to secure remote access to networks, patch software to address known vulnerabilities, limit the attack surface by disabling unnecessary ports and services, and monitor, detect and respond to potential intrusions.
During this time of heightened risk, organizations can license the Cybersecurity Extension for SAP from Layer Seven Security free of charge for up to three months. According to Ian Thomson, Chief Operating Officer at Layer7, “Layer Seven Security is committed to supporting organizations protect their crucial SAP assets during this critical period. Our flagship solution the Cybersecurity Extension for SAP will be provided to customers without charge to help them secure mission-critical SAP applications and infrastructure from advanced persistent threats”.
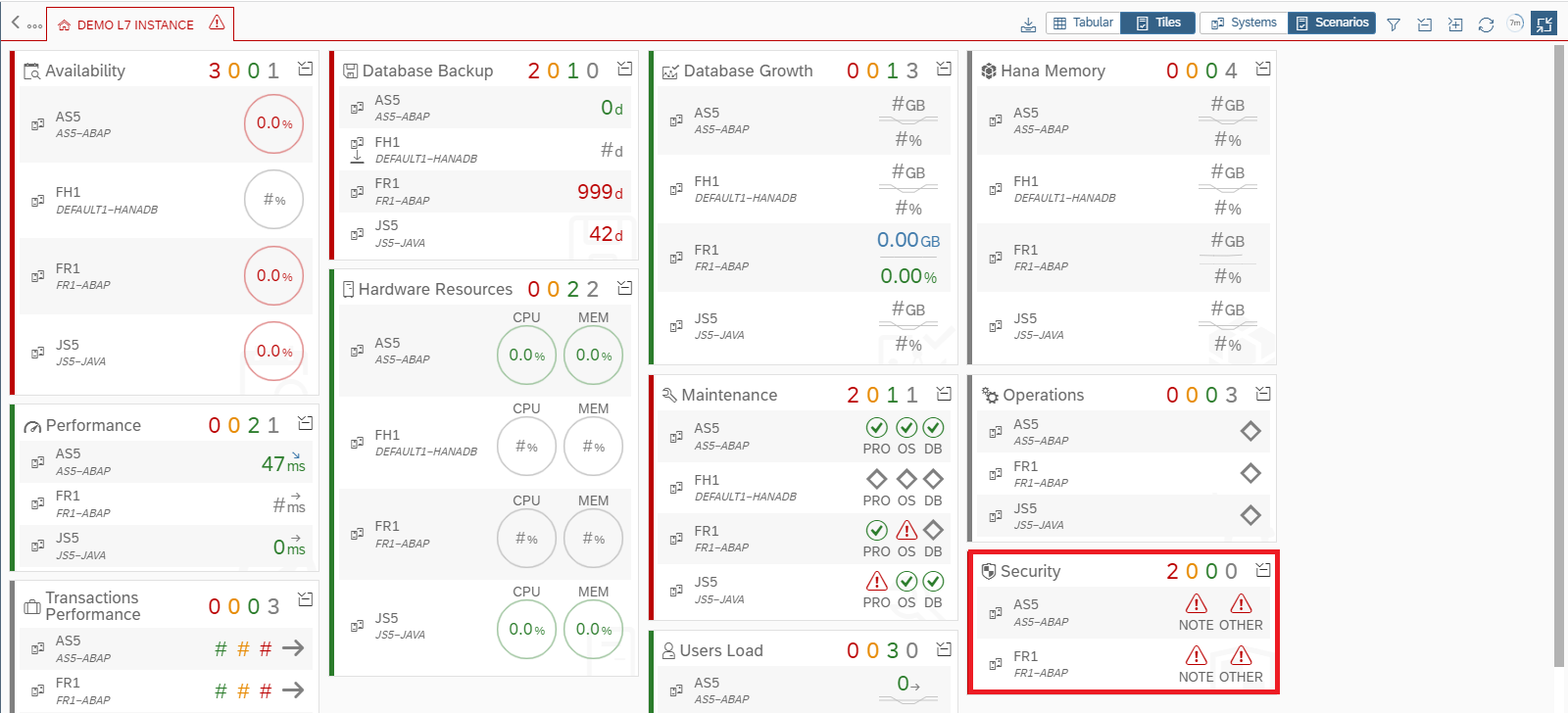
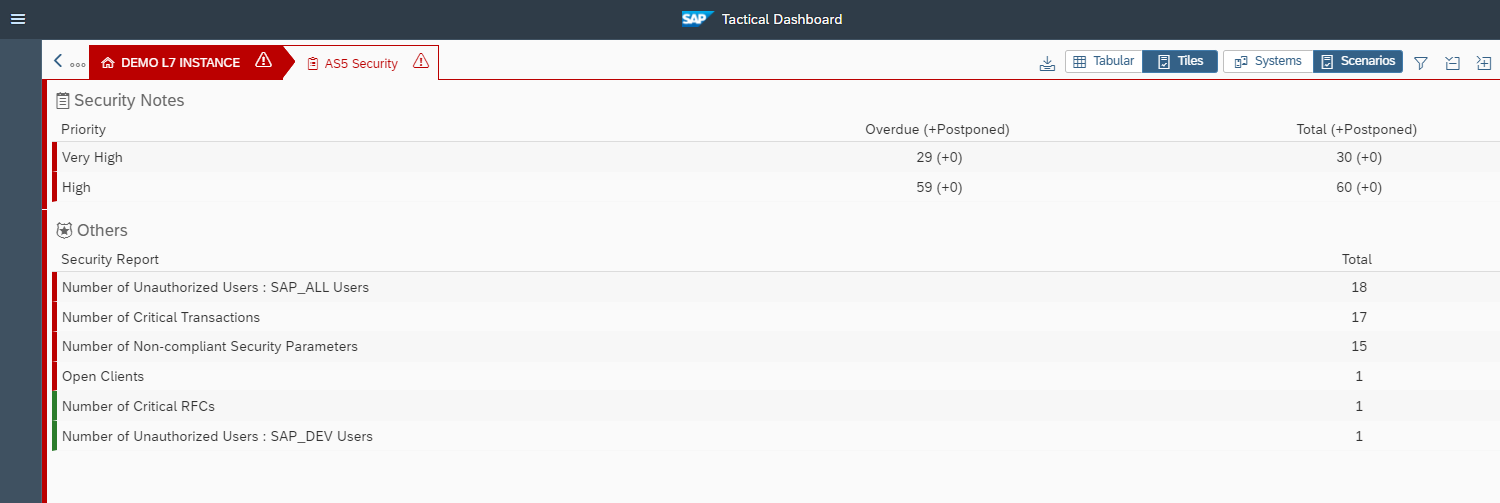
The Cybersecurity Extension for SAP is an SAP-Certified addon for SAP Solution Manager. It implements leading-edge vulnerability management for SAP applications, databases, hosts and components, including application gateways such as the SAProuter and Web Dispatcher. It integrates with System Recommendations for detecting and managing the lifecycle of SAP security notes. The solution identifies vulnerabilities in custom ABAP code and monitors event logs in SAP systems to detect and alert for over 600 indicators of compromise. The solution also applies advanced anomaly detection powered by SAP HANA to detect unusual system and user behavior.
Contact Layer Seven Security using the link below to discuss licensing the Cybersecurity Extension for SAP free of charge to secure your SAP applications.