Securing SAP Systems from Log4J Exploits
The Cybersecurity and Infrastructure Security Agency (CISA) has designated the recent Log4J vulnerability as one of the most serious in decades and urged organizations to immediately address the vulnerability in applications.
Log4j is an open-source logging framework maintained by the Apache Foundation. The framework includes the API Java Naming and Directory Interface (JNDI). Strings passed through JNDI can force Log4J to query remote LDAP or other servers, download serialized Java code from the malicious servers, and execute the code during deserialization if message lookup substitution is enabled. This can lead to the complete compromise of impacted applications and systems. The remote code execution vulnerability impacts all versions of Log4J2 up to and including 2.14.1 in Java 8 or higher.
Message lookup substitution is disabled by default in Log4j 2.15.0. It has been removed altogether from 2.16.0. Therefore, customers should upgrade to the latest version of Log4J. The vulnerability is addressed by CVE-2021-44228 which has a base CVSS score of 10.0.
CISA has added CVE-2021-44228 to the Known Exploited Vulnerabilities Catalog due to evidence of widespread active exploitation of the vulnerability by multiple threat actors. This includes nation state groups originating from China, Russia, Iran, and North Korea. According to some reports, threat actors are exploiting the vulnerability to deploy ransomware payloads or to gain access to target networks. The access is then brokered to other threat actors.
Log4J is included in multiple SAP applications including SAP HANA XSA. The central note 3131047 includes available patches for impacted solutions. Refer to the SAP’s official response for details of all impacted products. Note 3129883 includes manual procedures for a workaround that will disable the loading of external code in Log4J using the J2EE Config Tool.
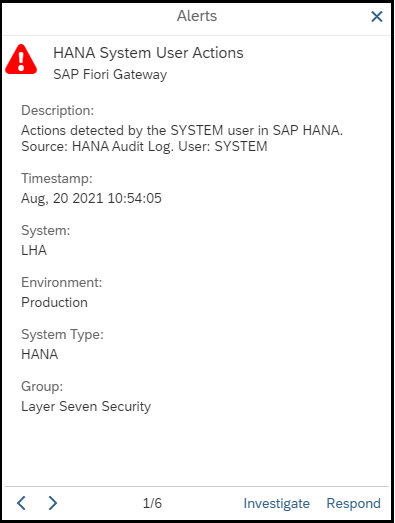
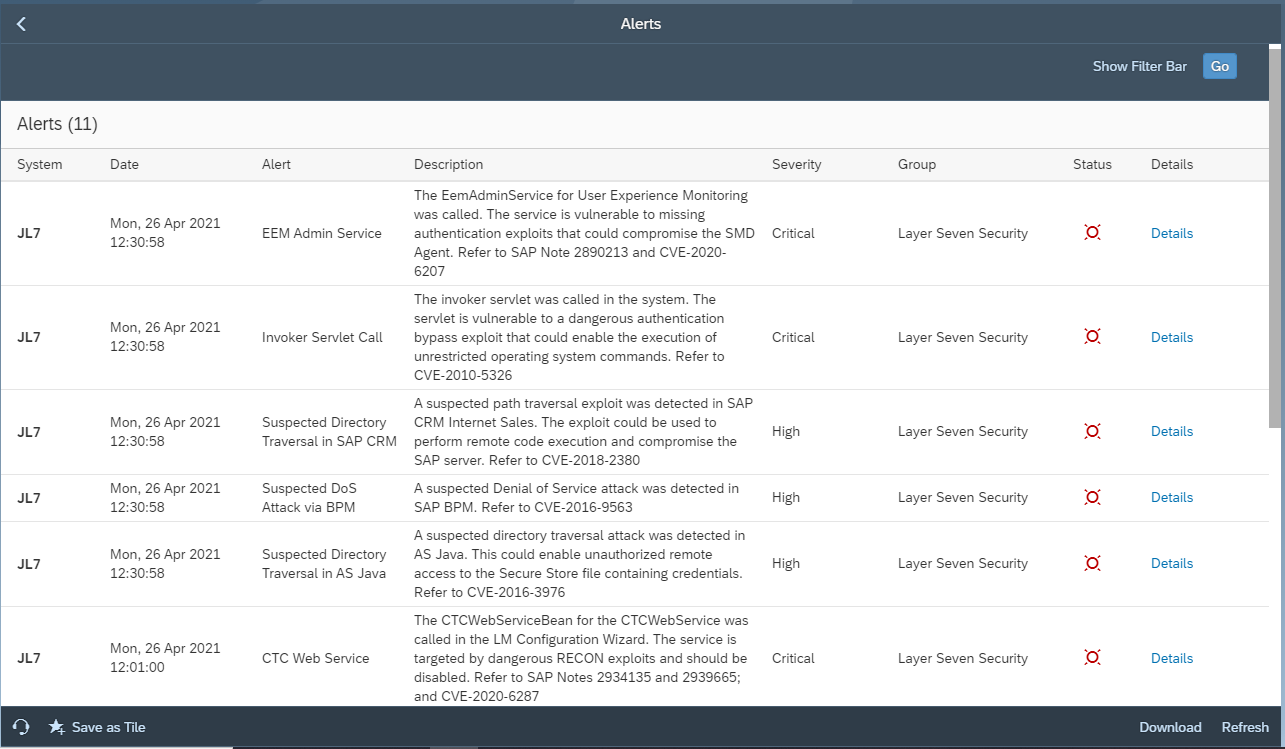
The Cybersecurity Extension for SAP identifies vulnerable SAP systems that have not been patched for the Log4J vulnerability. It also detects and alerts for suspected exploits targeted against SAP Java and Web Dispatcher installations based on exploit signatures. This includes known obfuscations and bypass methods.