Securing the SYSTEM User in SAP HANA
The SYSTEM user is the most powerful database user in SAP HANA with system-wide privileges including permissions to create and maintain other users, perform system changes, stop and start services, and create and drop databases and tables. The user is created during the initial setup of SAP HANA. Once the system is setup, the SYSTEM user should be deactivated and other users should be created for administrative tasks. The user is not required for HANA updates but should be reactivated for system upgrades, installations and migrations. This includes support stack and enhancement pack upgrades.
Since the SYSTEM user is a well-known administrative user with full system privileges, it is often targeted by threat actors. This article outlines measures to secure the user against attacks and detect and alert for actions performed by the user.
1. Reset Initial Password
Initial passwords for the SYSTEM user for both the system database and the first tenant database are set by hardware partners or administrators. The password should be reset immediately after the handover. The reset can be performed using SQL statements or the SAP HANA cockpit by a user with the USER ADMIN or DATABASE ADMIN privilege. Password resets can also be performed by the <sid>adm user from the system database.
2. Deactivate the User
The SYSTEM should not be used for data-to-day activities, especially in production systems. Create alternative dedicated users for each administrative scenario and then deactivate the SYSTEM user. The user can be temporarily reactivated for emergency tasks, when required. Deactivation can be performed using the SQL statement ALTER USER SYSTEM DEACTIVATE USER NOW and reactivation using the statement ALTER USER SYSTEM ACTIVATE USER NOW. The status of the user can be confirmed by reviewing the values in the columns USER_DEACTIVATED, DEACTIVATION_TIME, and LAST_SUCCESSFUL_CONNECT for the SYSTEM user in the USERS system view.
3. Create Audit Policies
Configure audit policies to log for all actions performed by the SYSTEM user and changes to the user such as password changes and user activation/ deactivation. Once activated, the policies will automatically log events to the audit trail. Audit policies can be created using SQL statements or the Auditing tab of the SAP HANA cockpit with the AUDIT ADMIN privilege. Actions should include both successful and unsuccessful events. Events can be written to one of the supported audit trail targets specified in each policy or the default audit trail if none is specified. Maximum retention periods can also be specified for each policy.
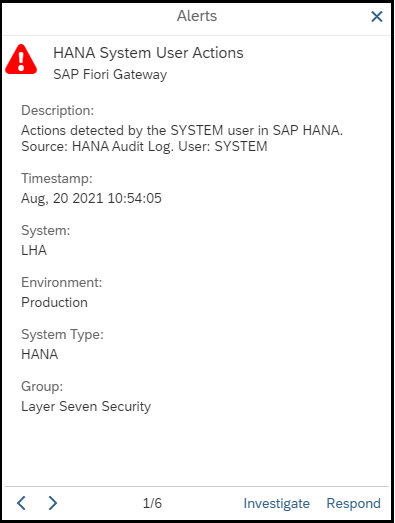
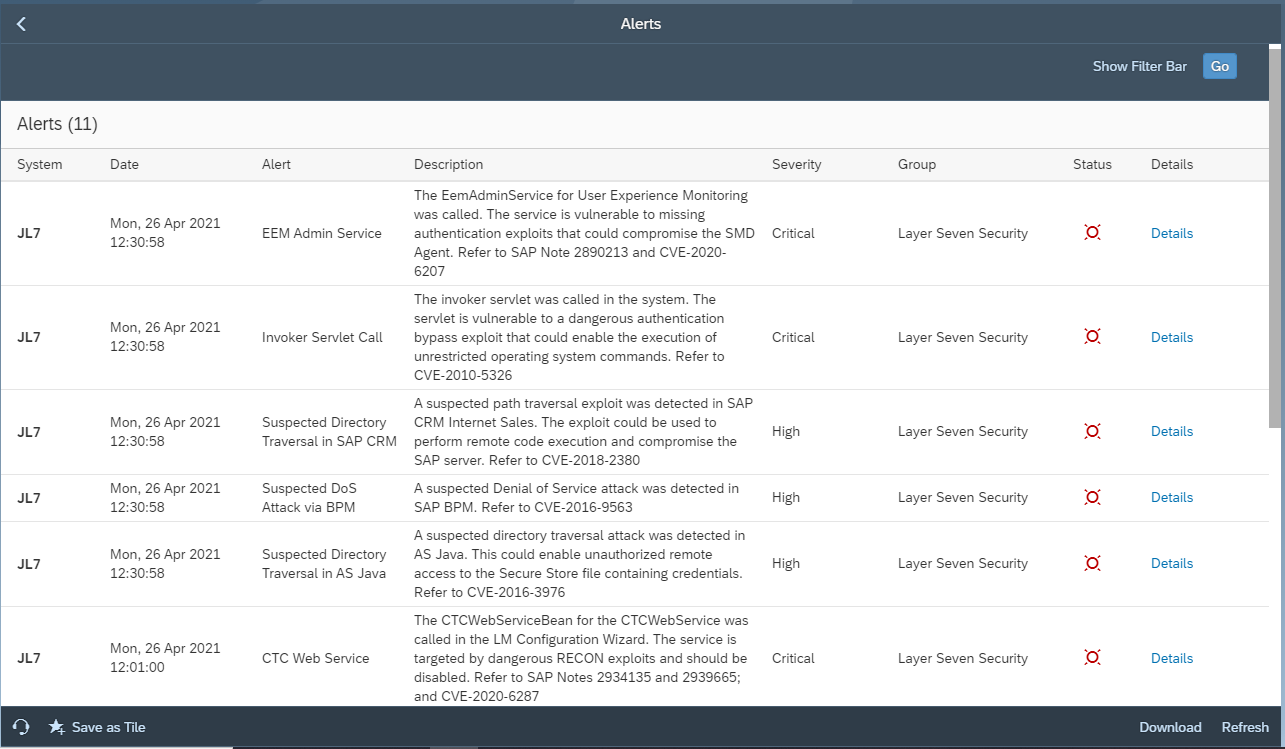
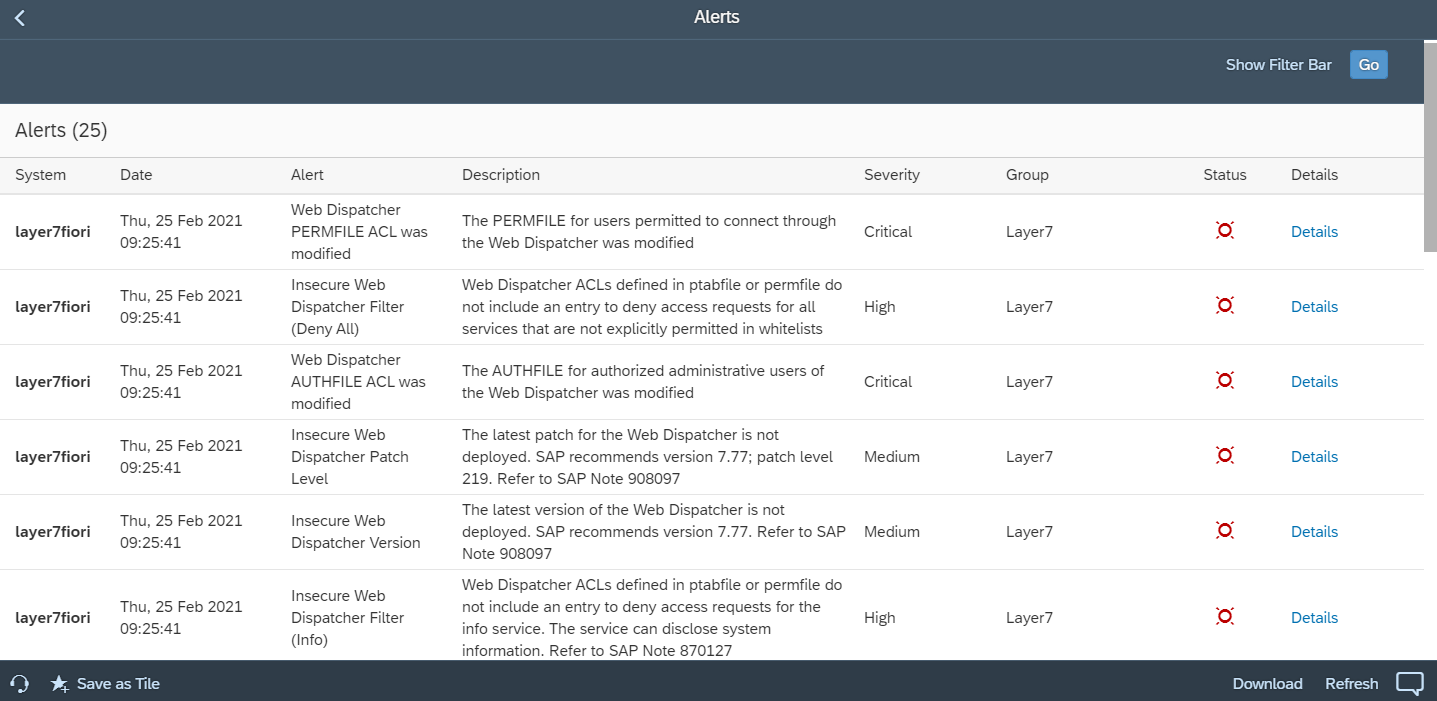
4. Monitor the Audit Trail
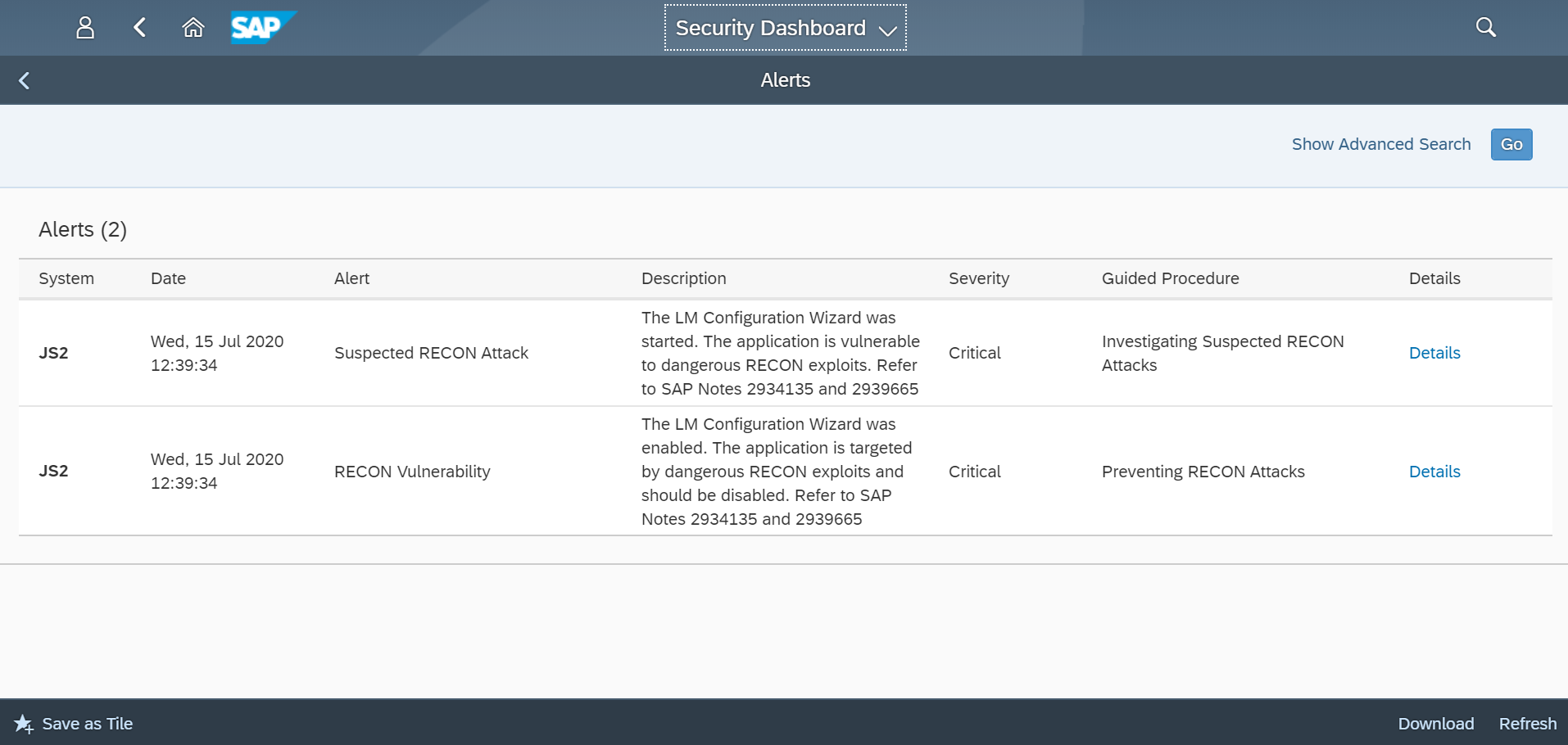
Monitor HANA audit logs using System Monitoring in SAP Solution Manager. Configure automated alerts and email/ SMS notifications for actions performed by the SYSTEM user or changes to the user. Integrate alerts with SIEM systems for SOC monitoring. Finally, investigate alerts using guided procedures in SAP Solution Manager.