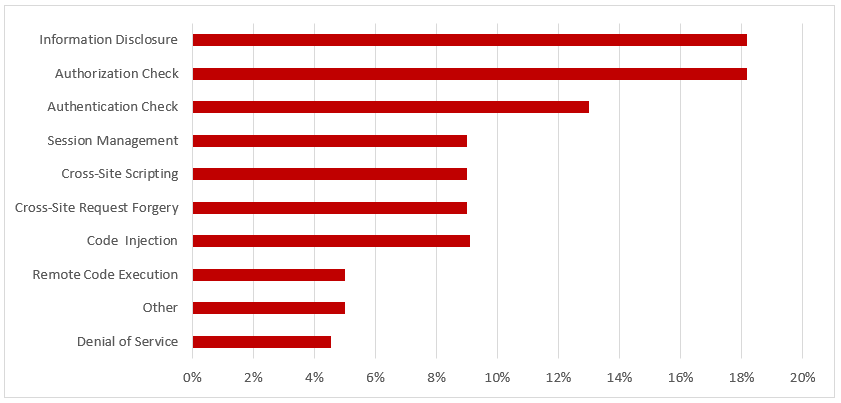
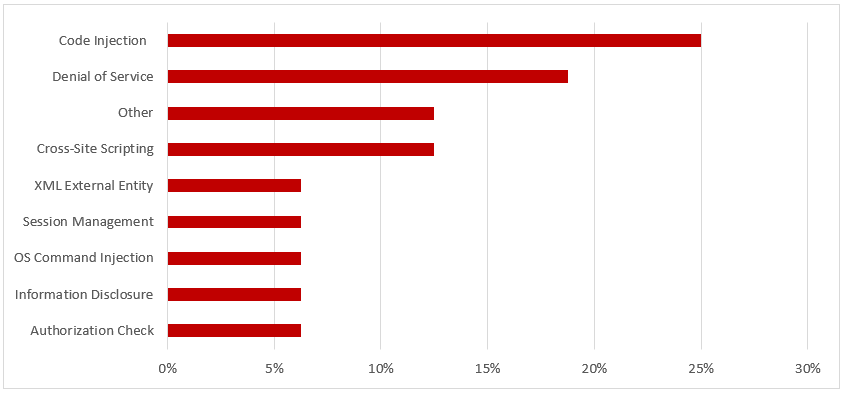
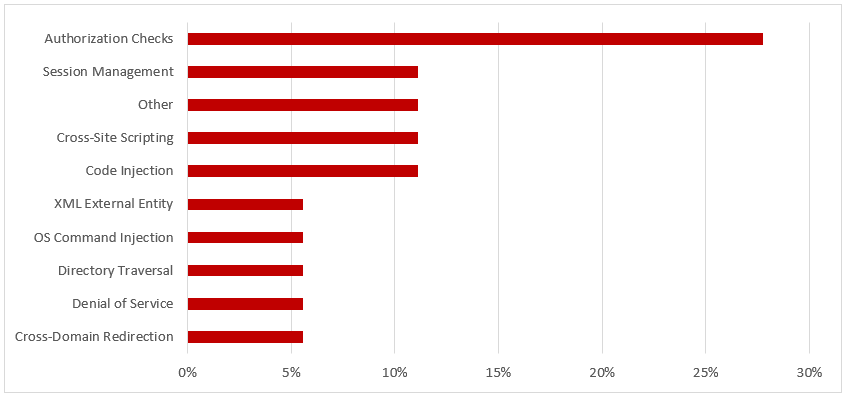
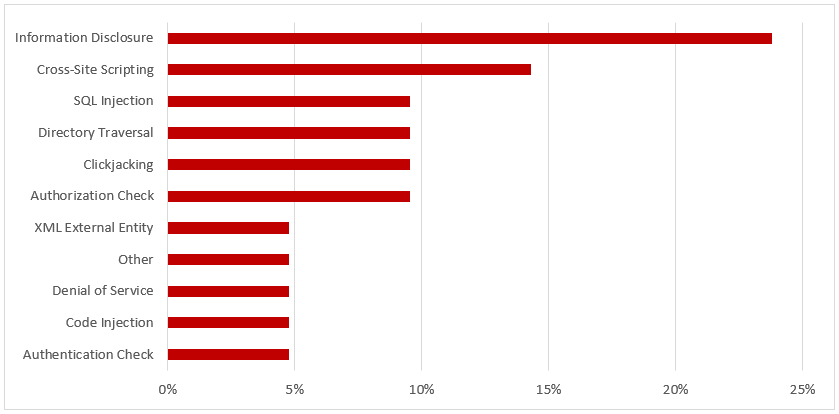
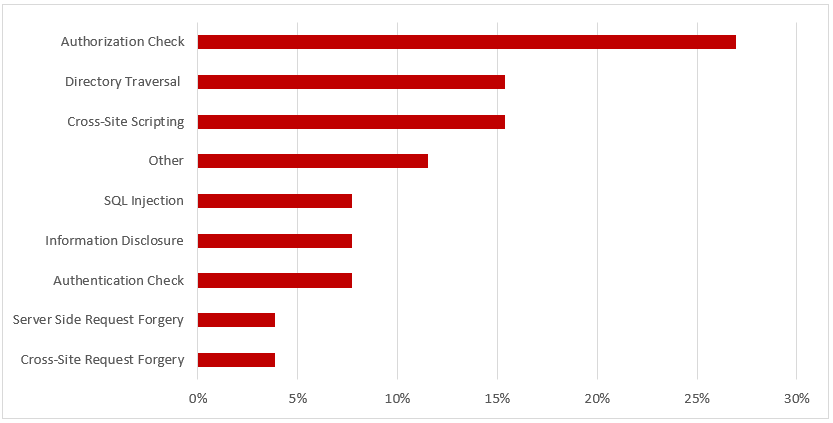
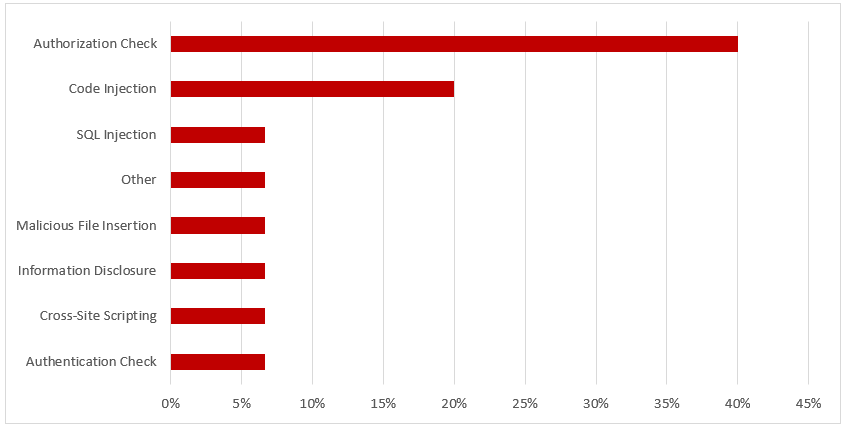
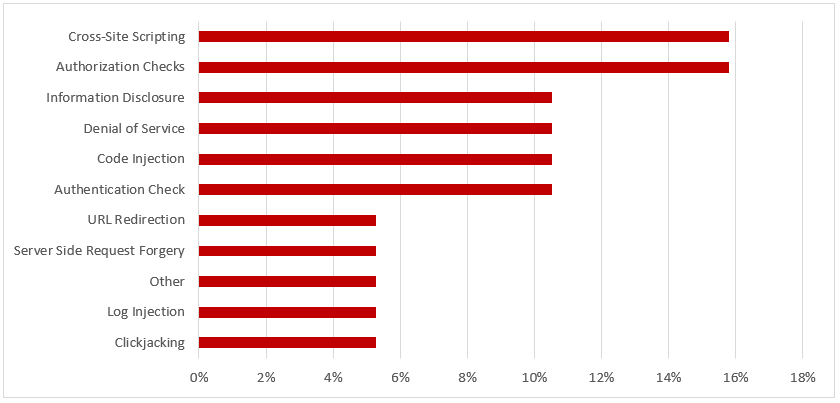
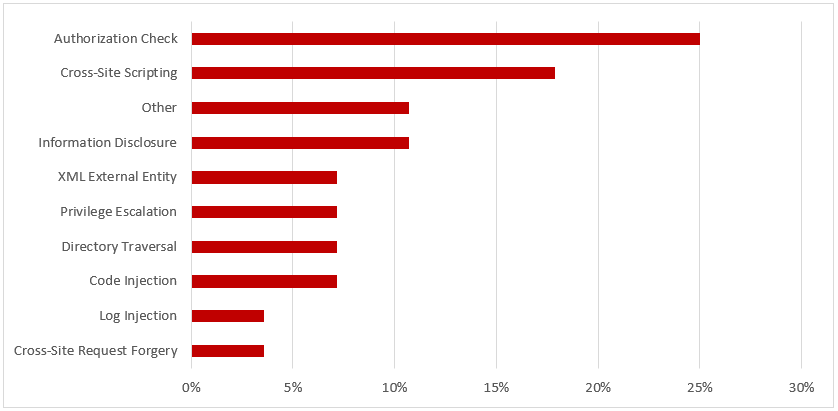
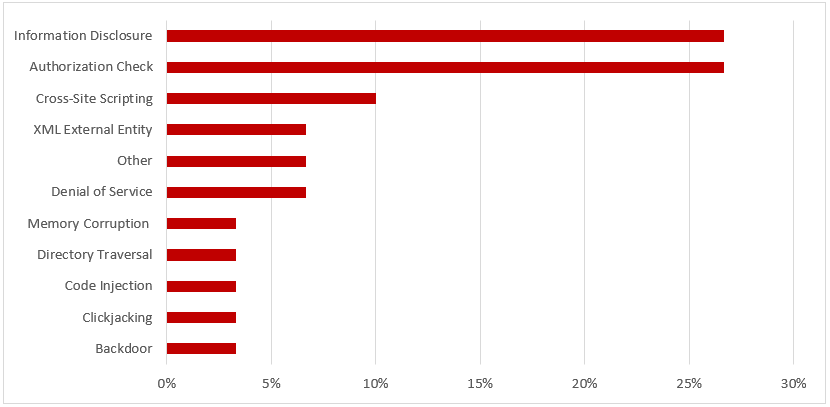
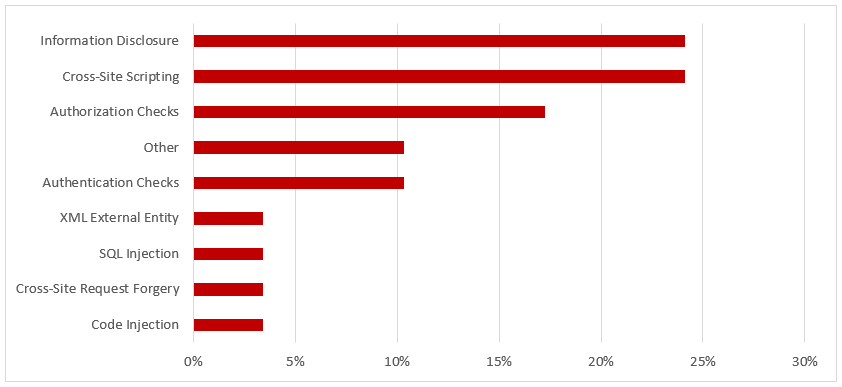
SAP Security Notes, June 2018
Hot News Note 2622660 includes critical security updates for web browser controls delivered with SAP Business Client. The Client provides a unified environment for SAP applications including Fiori, SAP GUI, and Web Dynpro. It supports browser controls from Internet Explorer (IE) and Chrome for displaying HTML content. Security corrections for the WebBrowser control of the .NET framework in IE are delivered directly by Microsoft. Unlike IE, the browser control for Chrome is embedded in SAP Business Client using the open source Chromium Embedded Framework (CEF). Security fixes are provided by the Chromium project and delivered by SAP through periodic Security Notes. Note 2622660 was updated in June for corrections addressed by Chromium release 67.0.3396. The critical rating of the note is due to the fact that the highest CVSS rating of the security corrections bundled in the fixes is 9.8/10.
Note 2537150 was also re-released with updated support pack information. The Note includes corrections to automatically terminate active sessions for users whose passwords have been changed in SAP BusinessObjects.
Notes 2629535 and 2626762 patch high-risk vulnerabilities in open-source components bundled in SAP Internet Sales. The vulnerabilities could be exploited to provoke a denial of service or bypass authentication and authorization controls. SAP Internet Sales is often tightly integrated with back-end SAP systems for order fulfillment and processing.
Finally, there were several important notes released for SAP Solution Manager. Note 2546807 provides manual instructions for successfully connecting agents for Wily Introscope to managed systems. Introscope is included in Solution Manager to support diagnostics and monitoring. Note 2574394 includes steps for authenticating and encrypting connections from Solution Manager to Diagnostics Agents using TLS. Instructions for securing connections from Diagnostics Agents to Solution Manager are available in Note 2593479.