Verizon Data Breach Investigations Report (DBIR) 2013: ‘This isn’t a threat you can afford to ignore’
The breadth and depth of the 2013 Verizon Data Breach Investigations Report (DBIR) is unprecedented. Released this Monday, the reports brings together the investigations performed by nineteen law enforcement agencies, research institutions and private security firms that combat data breaches including the European Cybercrime Centre (EC3), U.S Secret Service and the Department of Homeland Security. The global study represents the most comprehensive assessment of the drivers of information leakages. The findings and recommendations in the study are based on the analysis of 47,000 security incidents and over 600 confirmed breaches. They provide an unparalleled insight into attackers and their methods, enabling organizations to establish more effective countermeasures against such threats.
Threat Actors
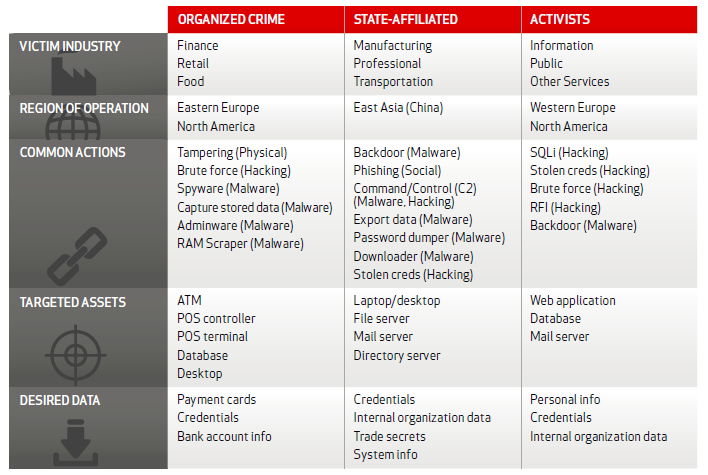
The study categorizes threat actors into three key groups: Organized Crime, State-Affiliated and Activists. These groups tend to originate from distinct regions, target different types of assets and data, and employ distinctive attack methods. Organized crime actors, for example, generally stem from Eastern Europe and North America and target financial information in companies within the finance, retail and food industries using methods such as hacking and malware.
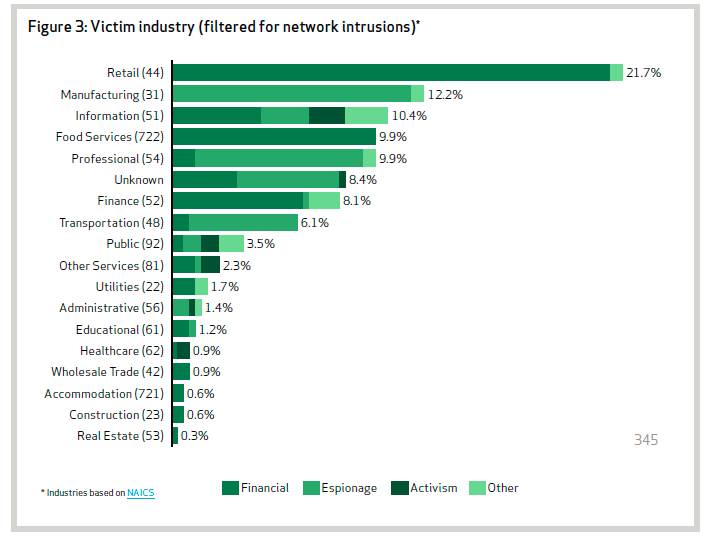
Activists comprise the largest group and are generally opportunistic. Organized criminals are more targeted but not as targeted and relentless as state-sponsored spies that use the most sophisticated methods to steal intellectual property, financial data or insider information from organisations. The graph below demonstrates that state-sponsored actors target a variety of sectors including education, finance and utilities. Nearly three-quarters of espionage attacks were targeted not at the public sector but at companies within manufacturing, professional services and transportation industries.
Threat Actions
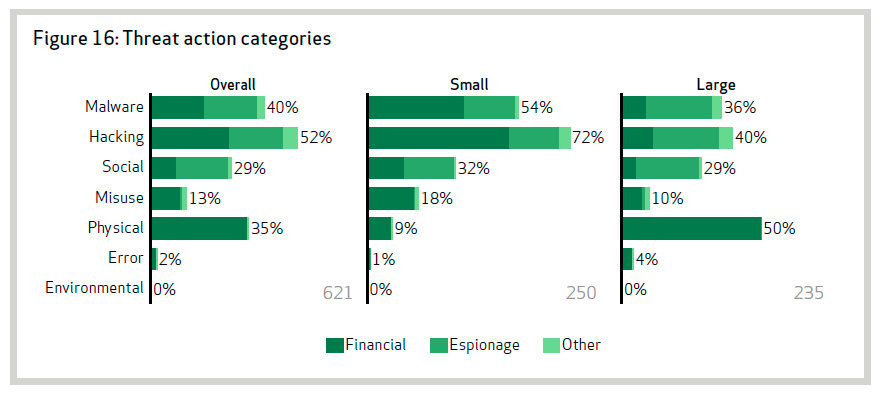
All threat actors employ hacking and malware methods to varying extents. This includes brute force attacks, spyware, backdoors, SQL injection, and the use of stolen credentials. Hacking involves attempts to access information systems usually through bypassing logical security measures, whereas malware is the use of malicious software, scripts or code, designed to alter the performance of systems. Both methods are increasingly scalable, automated and anonymous due to the greater accessibility of systems through the Internet and interconnectedness between systems and organizations.
Recommendations
According to the DBIR, “All kinds of organizations, from government agencies to iconic consumer brands, internet startups to trusted financial institutions have reported major data breaches in the last year. Nobody’ immune, no target is too small, or too large. The methods used by hackers to gain access to data are numerous, wide-reaching and ever-growing. This isn’t a threat you can afford to ignore”. Although attacks may be inevitable, there are clear, concrete measures that organisations should undertake to prevent such attacks from leading to data breaches. Breaches not only have the potential to cause financial and reputational harm, they increasingly require public disclosure: the European Union is expected to introduce mandatory reporting requirements this year. Forty-six states of the U.S have already done so. Furthermore, SEC reporting requirements mandate public companies to disclose the nature and extent of cybersecurity incidents to shareholders through corporate filings.
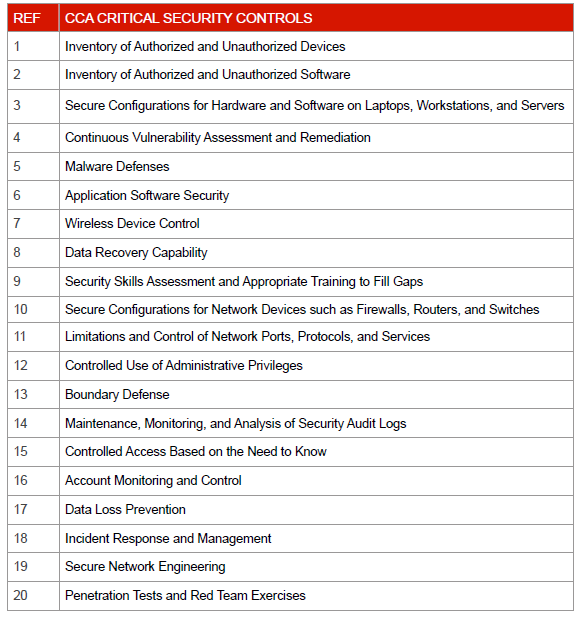
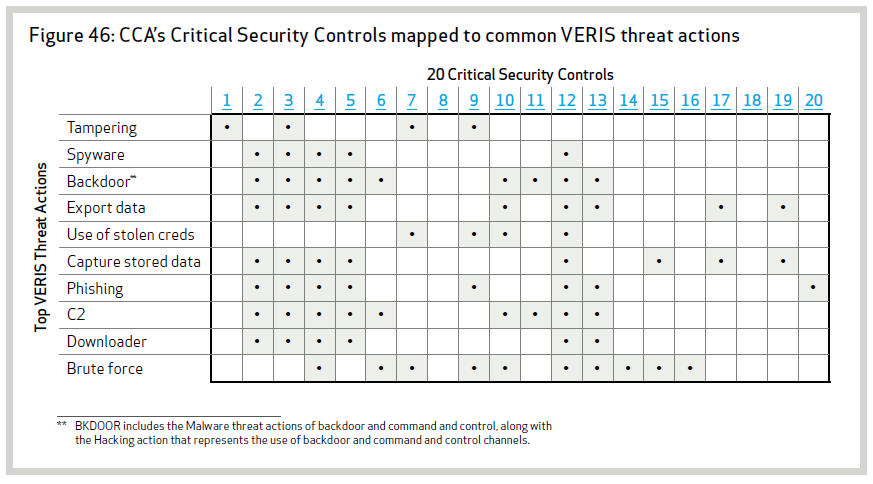
Organisations should implement common security measures to minimize the risk of a data breach, as well as detect and contain successful attacks. The specific recommendations made by the study include the implementation of the 20 Critical Security Controls (CSC) advocated by the Consortium for Cybersecurity Action (CCA). The controls are listed in the table below.
The following table maps the CSC to the most common threat actions identified by the DBIR and demonstrates that effective data breach prevention strategies require a combination of measures in the areas of people, process and technology.
The majority of the 20 Common Security Controls are directly applicable to SAP systems. The improper configuration of SAP applications, platforms, programs and clients can expose such systems to many of the threats identified by the DBIR and the risk of a data breach. The consequences can be disastrous when poorly configured systems are combined with inadequate boundary and malware defenses, insecure network and landscape architectures, ineffective access controls, and the absence of regular vulnerability assessment and penetration testing. Layer Seven Security has developed a comprehensive white paper to guide SAP customers on measures required to secure SAP systems against data breaches. The paper advocates a strategy based on the concept of defense in depth. You can download the paper here.