International Corporate Espionage: Annual Cost of Intellectual Property Theft Estimated at $250 Billion for U.S Economy
According to NSA Director General Keith Alexander, cyber-espionage has led to “the greatest transfer of wealth in history.†This is supported by not only a recent report by Symantec, which places the cost of intellectual property theft in the United States at $250 billion a year, but a prominent report on cyber-espionage released by Mandiant Corporation in February this year.
The report is based on security breaches investigated by Mandiant at nearly 150 organizations between 2006 – 2013. It focuses upon the cyber-espionage activities of one of the more than twenty prolific Advanced Persistent Threat (APT) groups in the world. The group labeled as APT1 is believed to be state-sponsored and operating from the Pudong area of Shanghai. It is considered to be a branch of Unit 61398 of the People’s Liberation Army of China. The official mandate of the unit is vaguely defined as ‘computer network operations’ but there is considerable evidence to suggest that the actual mission is the collection of political, economic, and military intelligence. APT1 is estimated to control a large physical infrastructure comprised of thousands of Command and Control servers. Given the size of the infrastructure, the group is believed to be staffed with several hundred resources that are required to be proficient in network and information security and the English language.
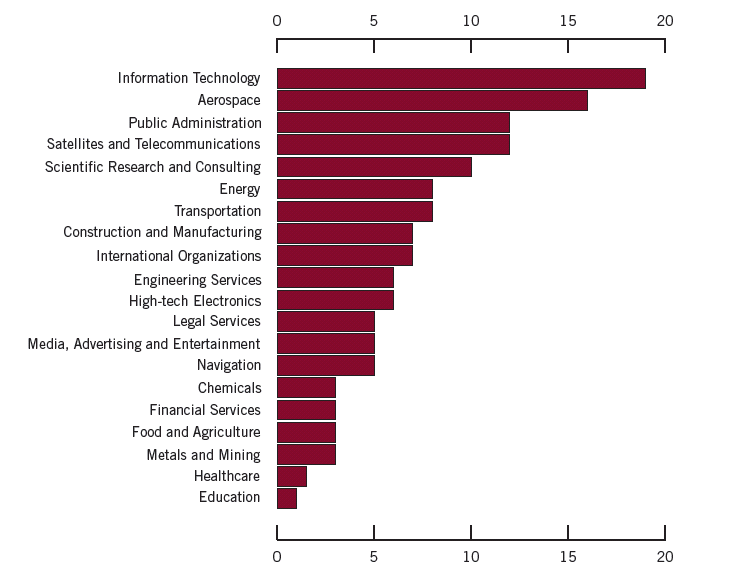
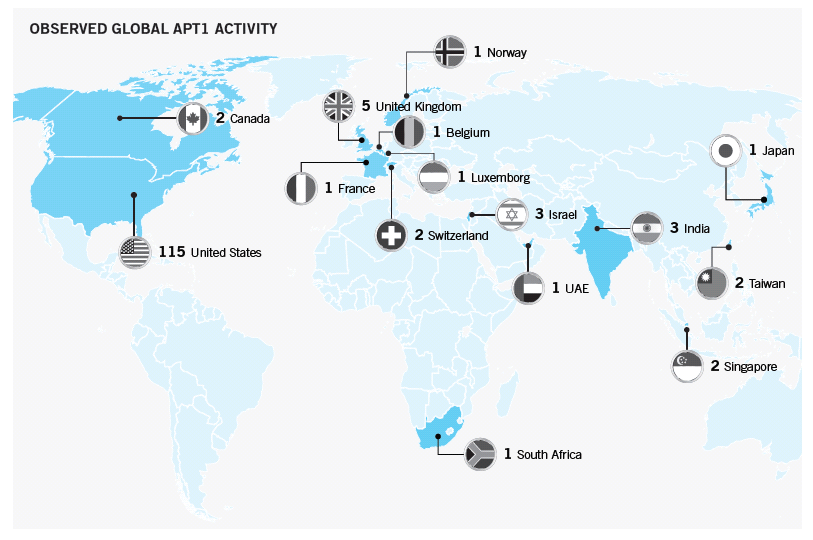
According to the report, APT1 compromised at least 141 companies in 20 major industries since 2006. Almost nine out of ten victims were headquartered in countries where English is the native language. The industries targeted by the group “match industries that China has identified as strategic to their growth, including four of the seven strategic emerging industries that China identified in its 12th Five Year Plan” (Mandiant, 2013). Graph 1.1 below demonstrates that the targets span a wide range of industries including Information Technology, Aerospace, Public Administration and Energy, but also, less expectedly, Manufacturing, Media, Advertising & Entertainment, Financial Services and Healthcare. Graph 1.2 displays the geographical distribution of companies compromised by APT1.
The compromises led directly to the theft of several forms of intellectual property including technology blueprints, manufacturing processes, business plans, policy and procedure documents, partnership agreements, pricing information, parts lists, test results, meeting agendas and minutes, emails and contact lists. They also led to the theft of information related to network architectures and resources and user credentials for business systems. One of the most notable breaches involved the loss of 6.5 terabytes of data over a ten month period from a single organisation.
APT1 employ a signature attack methodology that begins with a spear phishing campaign to penetrate an organization’s network. Emails are targeted at specific employees or groups of employees and appear to be from names that are familiar to recipients. Furthermore, the subject lines and contents of emails usually contain information that is directly relevant to the target. They are delivered with malicious attachments or hyperlinks to malicious files. Files names are personalized and are carefully constructed to appear harmless. Examples include Employee-Benefit-and-Overhead-Adjustment-Keys.zip, Updated_Office_Contact_v1.zip and Oil-Field-Services-Analysis-And-Outlook.zip.
The opening of a malicious file releases an executable that installs a backdoor in the recipient’s system. This enables APT1 to send commands to the compromised system remotely. “APT intruders employ this tactic because while network firewalls are generally adept at keeping malware outside the network from initiating communication with systems inside the network, they are less reliable at keeping malware that is already inside the network from communicating to systems outside” (page 30).
Initial backdoors are beachheads designed to establish a foothold in the network, perform reconnaissance, retrieve files and pave the way for the installation of standard, more powerful backdoors that communicate over HTTP or custom protocols. APT1 deploy standard backdoors to create, modify, delete and execute programs, upload and download files, create and remove directories, start and stop processes, capture screenshots, keystrokes and mouse movements, discover systems and users, and extract passwords. Backdoors are usually installed on multiple systems to maintain a presence in the network. Communication between backdoors and Command and Control servers is difficult to distinguish from regular traffic and is often hidden in encrypted SSL tunnels.
The installation of standard backdoors is followed by privilege escalation usually through the breaking of password hashes for target systems in order to obtain legitimate user credentials. Stolen credentials are used to logon directly to systems, VPNs and portals. Compromised data and objects are packaged in archive files and transferred out of networks through backdoors or protocols such as FTP.
In the words of the report, ATP1’s “ability to adapt to their environment and spread across systems makes them effective in enterprise environments with trust relationships” (page 27). SAP environments are archetypal models of such environments. Systems in these environments and landscapes are configured with numerous trusted connections, often using the most privileged user profiles. Trust relationships in SAP systems have well-known security concerns and should only be used for connections between systems with identical security classifications and established with minimal authorisations. You can read more about securing SAP trust relationships in our white papers. The papers also include guidance on measures to protect SAP servers and clients against unauthorized remote access, password attacks and other malicious actions by groups such as APT1.