Is SAP ASE the Most Vulnerable Point in Your SAP Landscape?
SAP Adaptive Server Enterprise (ASE) is a widely-used relational database server for SAP solutions. As part of the drive to HANA, SAP is expected to withdraw support for third party databases including Oracle, IBM and Microsoft. Standard support for Oracle 19c, for example, will end in April 2024. Oracle 19c is the highest release of Oracle certified for SAP. In contrast, maintenance and support for ASE is expected to continue beyond 2030. This includes both on-premise and cloud deployments. ASE is used within the SAP Cloud Platform and SAP HANA Enterprise Cloud for persistence services.
The database layer in SAP landscapes will increasing comprise of SAP HANA and ASE database systems. However, unlike HANA, security for ASE is often overlooked by SAP customers. As a result, ASE can be a vulnerable target for threat actors in SAP landscapes. This article will discuss the key aspects of ASE security and methods for automating vulnerability management, security patching and threat detection for ASE.
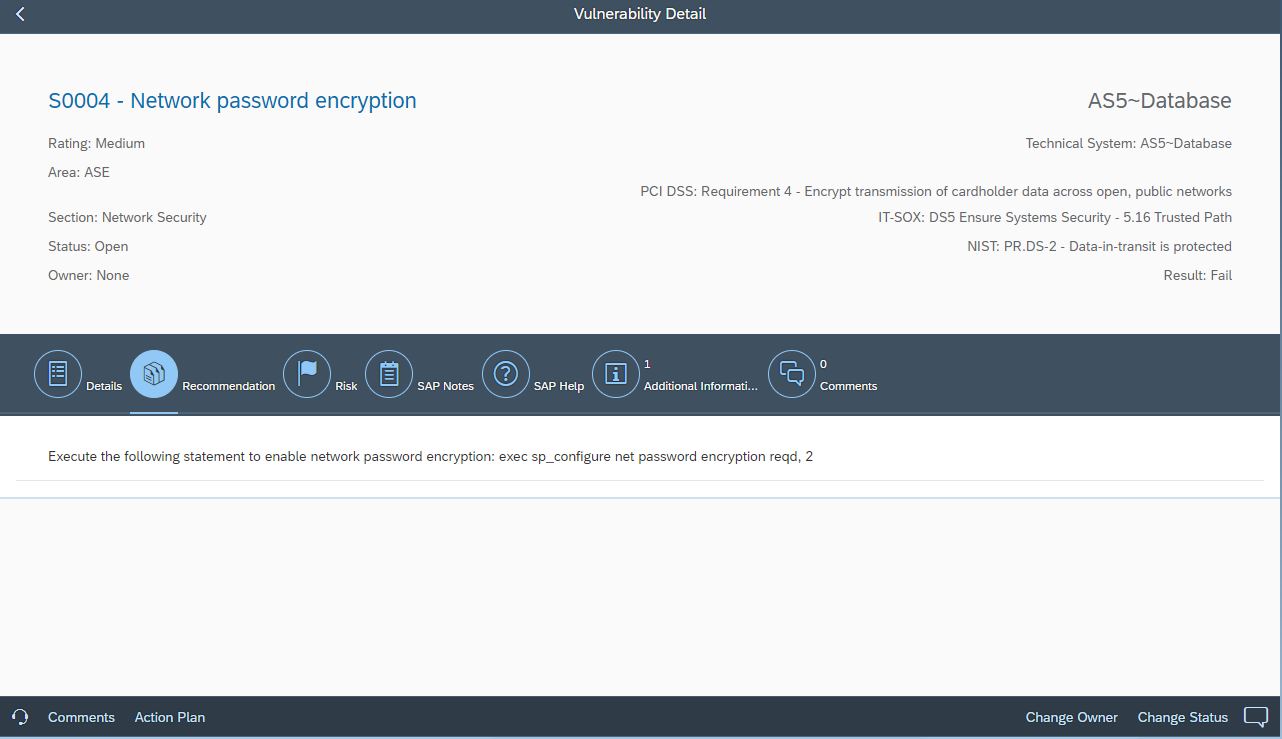
SAP ASE supports both password-based authentication for database users and external authentication using Kerberos, LDAP, or PAM. For password authentication, strict password policies are recommended governing password complexity, failures, expiration, and reuse. The transmission of passwords over the network layer should be secured using SSL through the FIPS 140-2 validated cryptographic module. For external authentication, it is recommended to enable message confidentiality, integrity and origin-checks to secure procedures for remote authentication.
ASE includes several pre-defined roles for provisioning required privileges to database users. They are managed using the sso security officer role. Access to this role should be restricted to authorized users. Other critical roles include the sa security administration role, and roles for operations, replication, job scheduling, web services, and system administration.
ASE also includes multiple default accounts that should be locked if not in use. This includes the accounts probe, sybmail, jstask, and mon_user. The sa account has system-wide privileges. The password for the account is blank on install. The account should be locked after the initial database configuration. The use of the guest account is not recommended since it inherits the permissions of the public role.
Remote users can be authorized to execute remote procedure calls (RPC) in ASE. Remote user IDs are mapped to local IDs by ASE to authorize access to RPCs. The use of remote users should be avoided.
Vulnerable services in ASE should be disabled to reduce the attack surface. This includes the extended stored procedures xp_cmdshell and xp_sendmail. Other stored procedures should be enabled to support enhanced security checks. For example, sp_extrapwdchecks should be activated to check for password reuse.
Column and table-level encryption can be enabled to protect data at rest. Encrypted data is transparent to applications and therefore does not impact operations. ASE supports the Advanced Encryption Standard (AES) encryption algorithm and 256-bit key lengths. AES is a NIST-approved cipher standard.
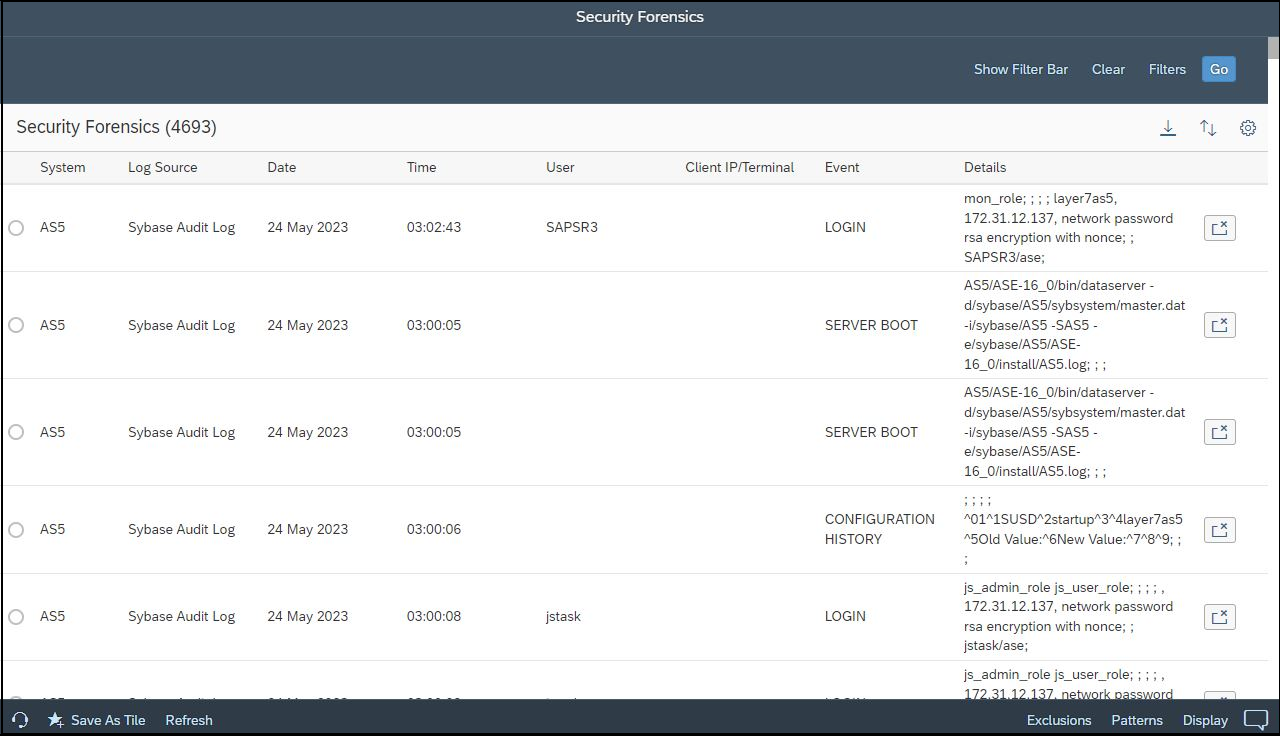
Auditing is disabled by default in ASE. Once enabled, audit options should be activated to log specific events to the audit log. This should include auditing of the sa account and critical roles such as sso, configuration changes, login failures, role and account changes including user passwords, and the execution of stored procedures. It is also recommended to enable auditing for data binds, changes to encryption keys, and the importing/ exporting of data to/from external files.
Audit events are written to system audit tables. The tables can be read using SQL commands. Only select and truncate commands are supported for the audit tables. The event details include a unique event ID, timestamp, the ID of the account that performed the audited event, and the details of objects that were accessed or modified.
The Cybersecurity Extension for SAP leverages the database connectivity of SAP Solution Manager (SolMan) and SAP Focused Run (FRUN) to automatically detect security vulnerabilities in ASE installations that could be exploited by threat actors. This includes vulnerabilities in the following areas:
Settings for external authentication
Policies for password authentication
Users with critical roles
Disabling of default accounts
Remote users
Deactivation of vulnerable database services
Transport layer security
Database encryption
Auditing and logging
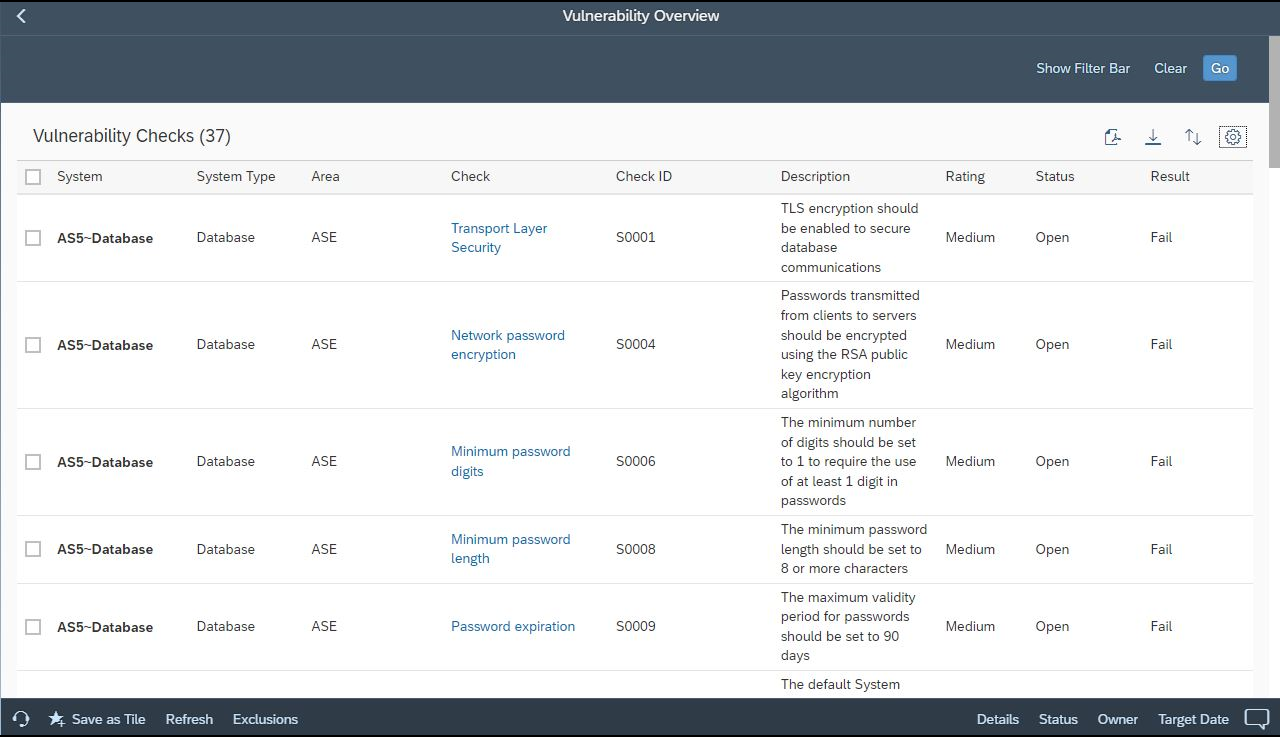
The Extension provides detailed recommendations to remediate vulnerabilities and harden ASE installations against targeted exploits.
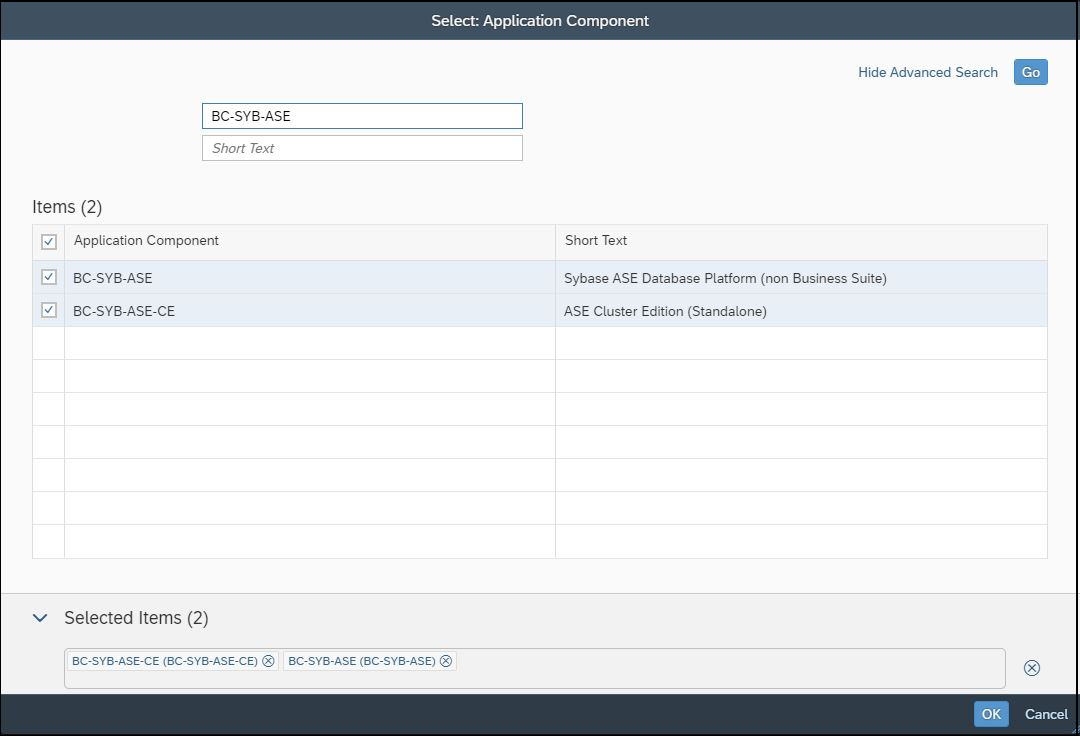
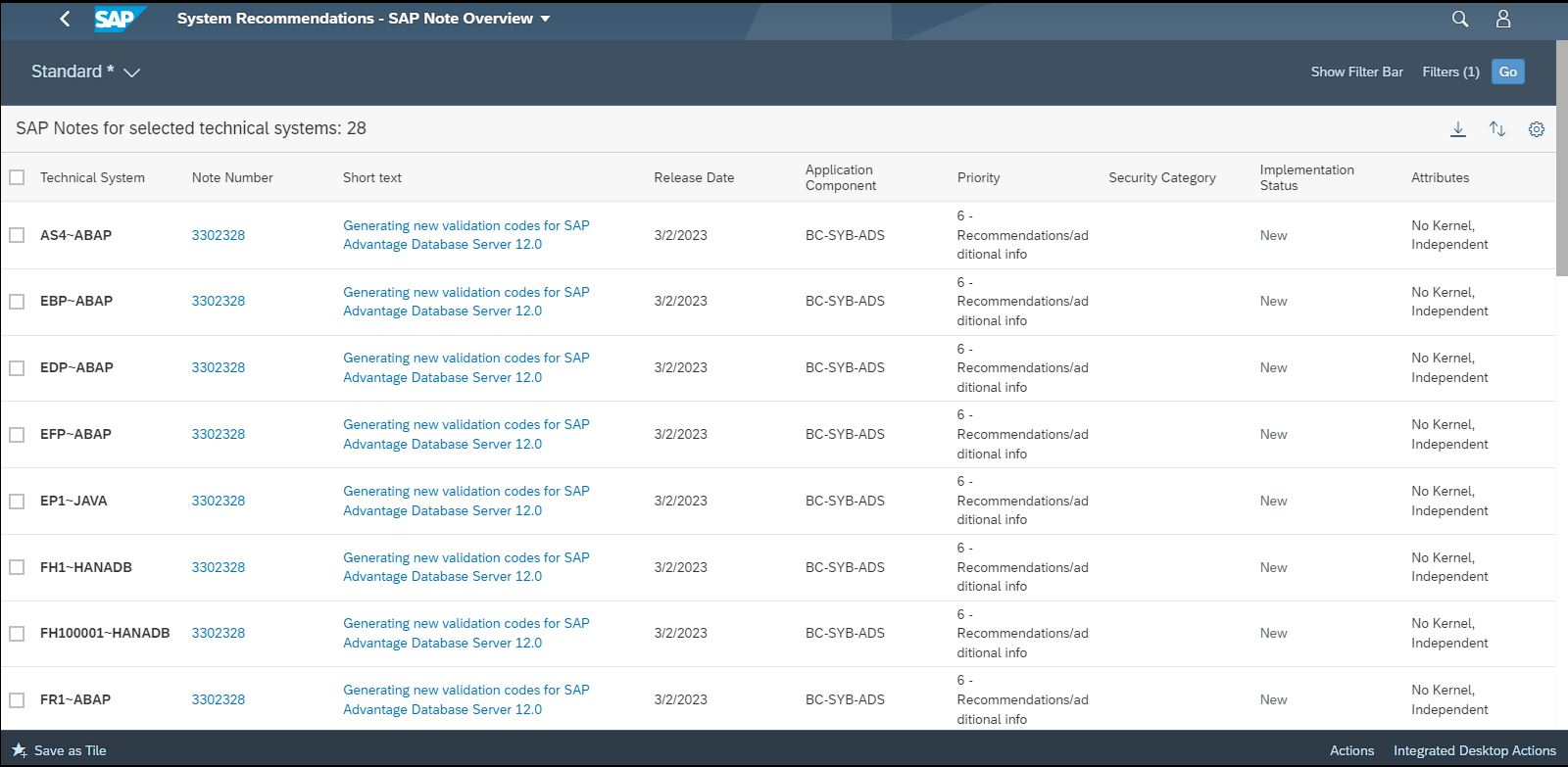
Security notes for ASE are reported by System Recommendations (SysRec) in SAP Solution Manager. SysRec connects directly to SAP Support to calculate required notes. The Cybersecurity Extension for SAP integrates with SysRec to automatically identify and remove potential false positive notes based on installed application components. You can filters notes in SysRec for the ASE components BC-SYB-*.
The Extension also monitors ASE audit logs in real-time to detect and alert for potential breaches such as the use of default users that should be locked, changes to roles and user permissions, failed logins, locked users, database configuration changes including audit settings, successful calls to sensitive stored procedures, the installation of Java programs, password resets, remote procedure calls to/from external servers, the deployment of web services, and commands that transfer table contents to/ from external files.
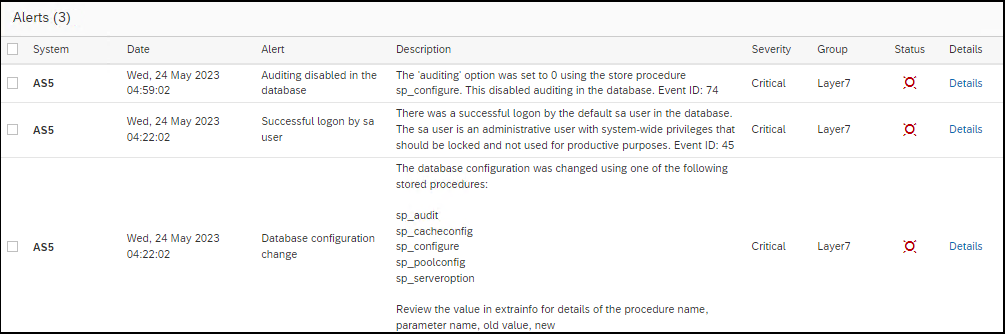
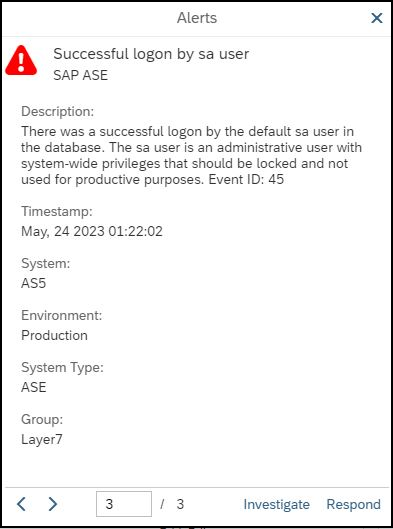
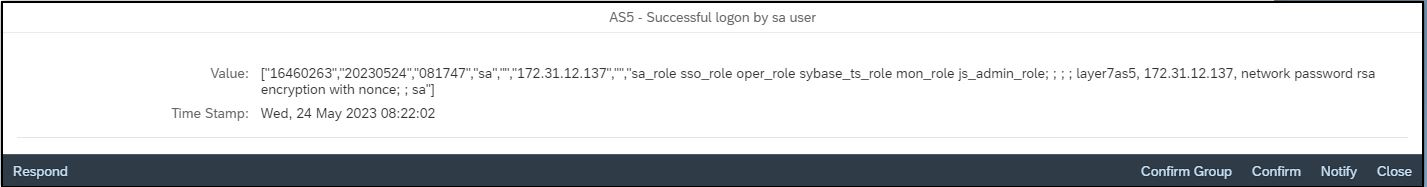
Alerts can be investigated using built-in incident response procedures and workflows.
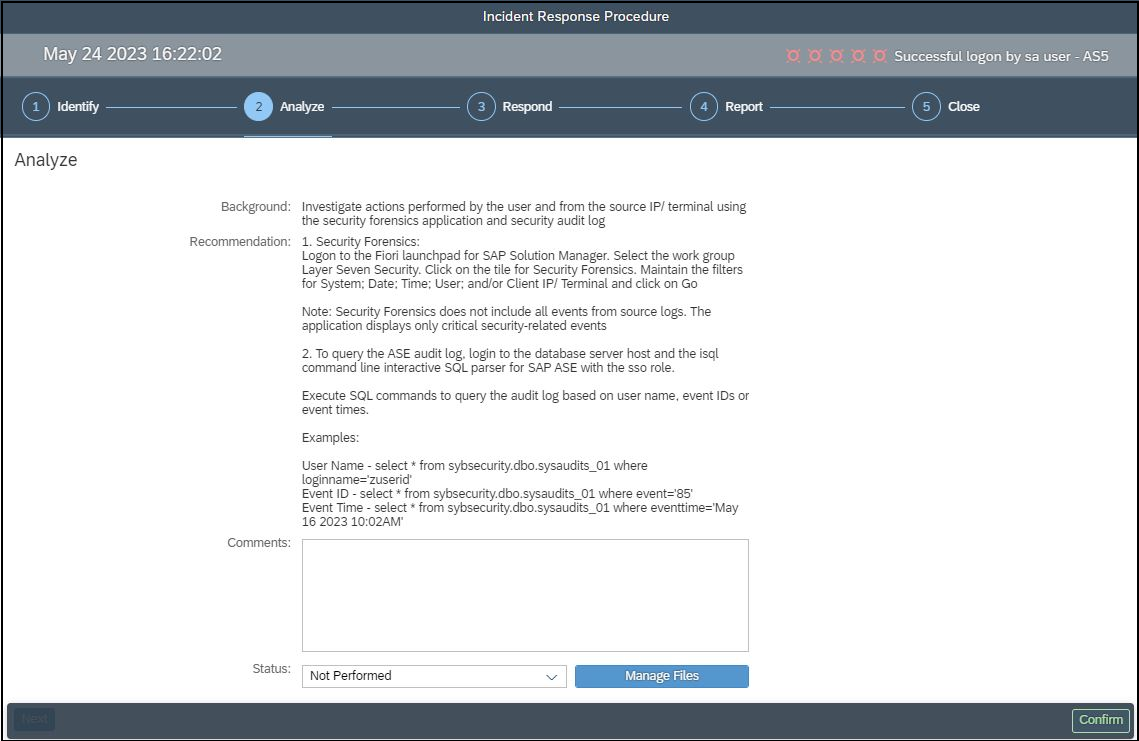
Audit records are replicated from ASE installations to the Cybersecurity Extension for SAP to support archiving and forensic analysis and to protect against log corruption.
To learn more, contact Layer Seven Security.

