Securing the SAP Cloud Connector
The SAP Cloud Connector is an agent that links SAP BTP applications with on-premise SAP systems. As a reverse proxy, it enables internal systems to connect securely with BTP services without exposing the systems to direct external access. Permitted connections between BTP resources and backend systems can be maintained directly in the Cloud Connector rather than network firewalls. The Cloud Connector supports HTTP and RFC connections between BTP and SAP systems, as well as direct database connections.
The Connector links directly to external services. Therefore, it should be positioned in a DMZ and segmented from internal SAP systems. Since the DMZ is a separate physical or logical network, segmentation would protect internal SAP systems in the event of a compromise in the Cloud Connector. Systems in SAP landscapes should be configured to accept requests only from trusted Connectors. A failover instance of the Connector is recommended for high availability. This is known as a Shadow Connection, maintained in the High Availability section of the Connector UI.
The Connector should be installed in a dedicated server that does not share resources with other services, especially application services. Access to the Cloud Connector at the OS level should be restricted and OS auditing should be enabled to monitor file operations for the Connector. This includes the Secure Storage in the File System (SSFS) that stores encryption keys and other sensitive data for the Connector. It is also recommended to enable hard-drive encryption for the server hosting the Connector. This will safeguard sensitive configuration data against the unauthorized access and changes. Separate Cloud Connector instances are recommended for connecting to productive and non-productive subaccounts in BTP.
The Connector uses file-based authentication which cannot support multiple users. It is delivered with a single Administrator user that has full administrative rights for the Connector. LDAP-based user authentication should be configured to support multiple users and avoid the use of the Administrator user as a shared account. This would also support traceability for user actions and more granular access control by allowing the use of display and monitoring roles that do not include administrative privileges.
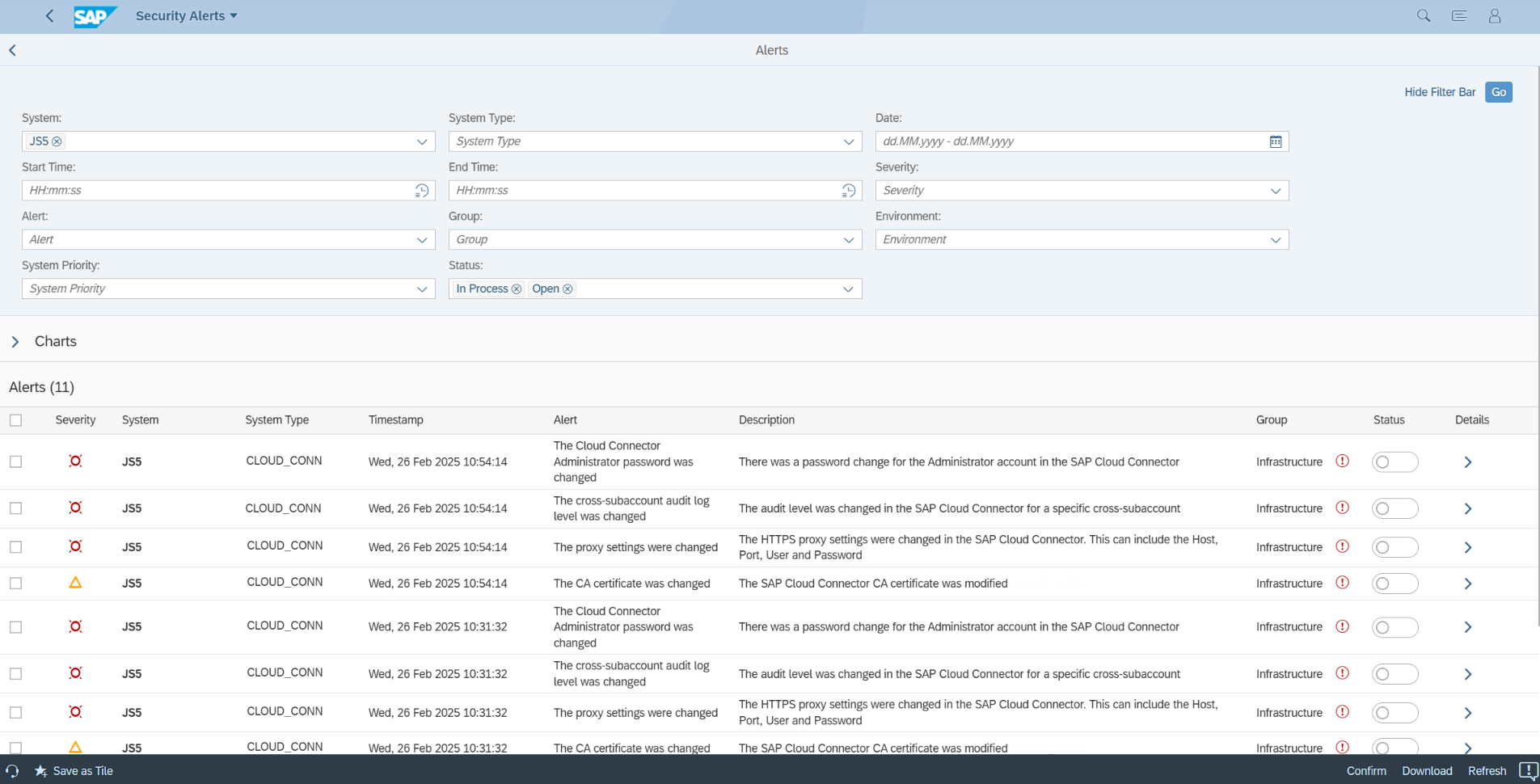
The Administrator user is shipped with a well-known default password. The password is stored as a hash in the file system. Although the Connector prompts users to change the password during installation, it is critical to monitor changes to the Administrator account to ensure that the password does not revert back to the default. This could lead to the compromise of the Administrator account and therefore the Cloud Connector.
Connections from SAP BTP to the Cloud Connector are SSL-encrypted. Currently, supported protocols are HTTP, HTTPS, RFC, RFC with SNC, LDAP, LDAPS, TCP, and TCP over TLS. Connections from the Connector to backend systems should be authenticated and encrypted. Therefore, HTTPS and RFC SNC are recommended over HTTP and RFC. Permissions for technical users should granted based on the principle of least privilege and should not include full administrative rights. Whitelisting is also recommended to restrict access to only the required BTP applications for each subaccount and resources in backend systems.
The self-signed X.509 certificate used for the Connector UI should be replaced by a certificate issued by a certificate authority. Supported TLS ciphers for UI certificates should be SHA256 or greater bit length. Support for less secure ciphers should be disabled in the configuration of the Connector.
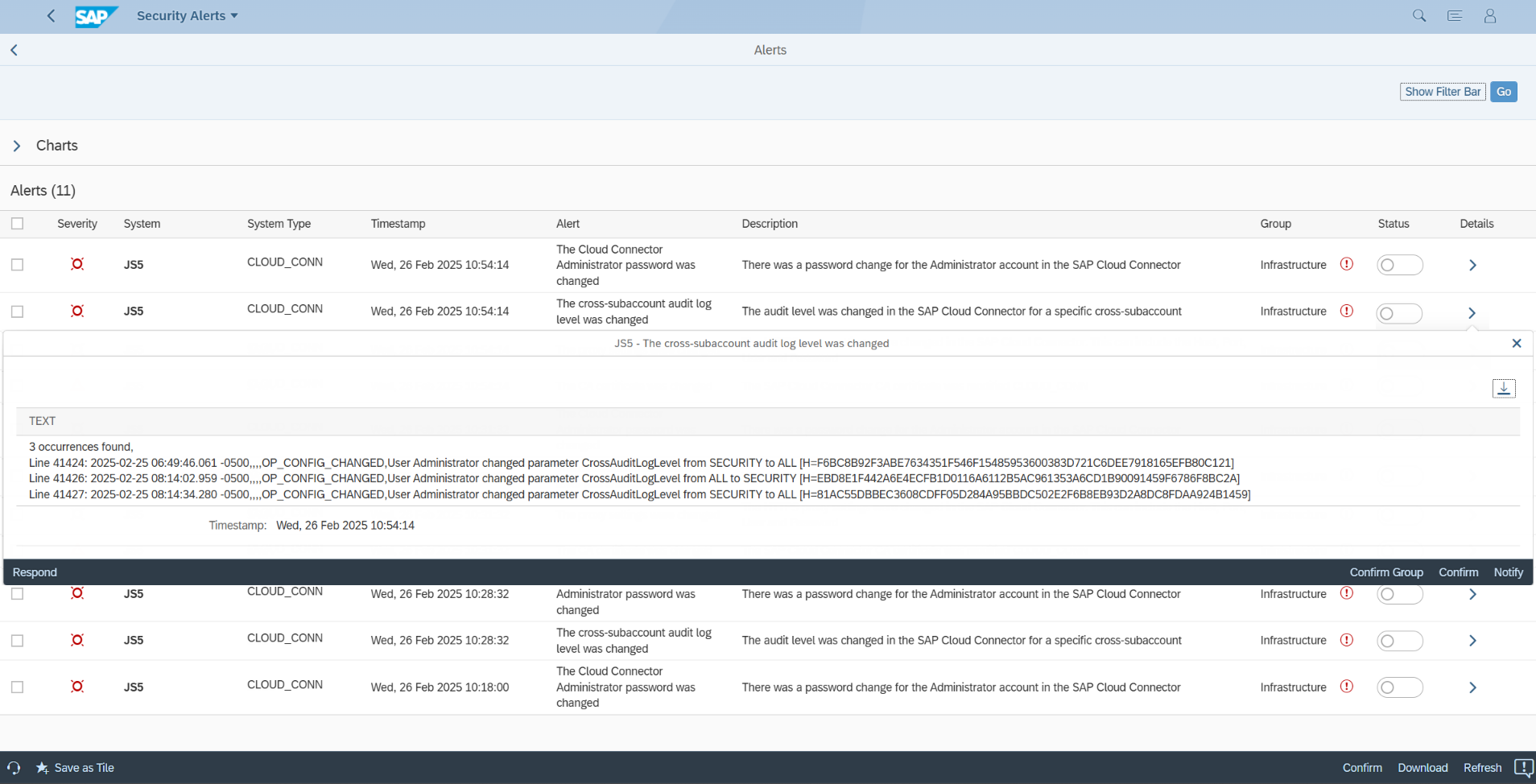
The audit log level should be set to SECURITY (default) or ALL. It should not be set to OFF. The value SECURITY will lead the Connector to log blocked requests and configuration changes. The value ALL will enable the Connector to log all requests including successful connections. Logs are stored in the file system. A separate file is created for each day. Deletion of older log files can be enabled using the setting Automatic Cleanup setting in the Audits section of the Administration UI. The Cloud Connector includes a script to verify the integrity of the audit logs and protect against log tampering. The location of the log files can be modified from the default directory, although the performance of the Connector may be impacted if you change the location from the host for the Connector to another server in the network.
HTTP and RFC traces enabled through the Connector may disclose sensitive information such as passwords and credit card data to Administrators. This can be mitigated by requiring two separate users to activate a trace. The file writeHexDump must be created in the scc_config directory for Connectors installed in Linux hosts. The owner of the file must be different than the OS user for Connector processes and not a member of the OS user group sccgroup. The owner of the file will be required to change the file content from allowed=false to allowed=true before an administrator can activate a trace.
Each version of the Cloud Connector is supported by SAP for only 12 months. Therefore, the Connector should be upgraded regularly. It should also be upgraded regularly in response to security notes for the Connector released by SAP. This includes Hot News note 2696233 that deals with multiple critical vulnerabilities in the Cloud Connector. Version 2.11.3 or higher is required to address the vulnerabilities in the note.
The SAP Cloud Connector is an important interface between SAP cloud services and on-premise systems in today’s hybrid SAP landscapes. As an external-facing agent with access to business-critical internal SAP systems, securing the Connector is essential to protect SAP solutions from targeted attacks. The Cybersecurity Extension for SAP automatically scans and detects security misconfigurations and user-related issues in the SAP Cloud Connector that may expose the Connector to such attacks. It also monitors the patch level to ensure the Connector stays updated to the recommended version in response to security vulnerabilities. Finally, the Cybersecurity Extension for SAP monitors the audit log for the Cloud Connector to automatically alert for security incidents. This includes configuration changes, changes to the Administrator account including passwords, changes to connected BTP subaccounts and backend systems, the activation of traces, settings for logging and auditing, role changes, certificates, LDAP, SNC, and many other areas.