SAP Security Notes, July 2025
There are multiple hot news notes released in July for insecure deserialization vulnerabilities in SAP NetWeaver AS Java solutions and components. The vulnerabilities arise from the processing of untrusted user-provided serialized data without adequate input validation. This can lead to malicious code execution and authentication bypass. Notes 3610892, 3621236, 3620498 and 3621771 correct deserialization vulnerabilities in the XML Data Archiving Service, Enterprise Portal Administration, Federated Portal Network, and the Log Viewer, respectively. Workarounds are provided where available, including instructions for disabling the LogViewer. Note that log files can be analyzed directly in the file system or using SAP Management Console (SAP MMC) after it is disabled.
Note 3578900 addresses an insecure deserialization vulnerability in the Live Auction Cockpit of SAP Supplier Relationship Management (SRM). The CVSS score for the vulnerability is rated 10.0. The note also addresses other lower-priority vulnerabilities in SRM including XML External Entity (XXE), Cross-site Scripting (XSS), Open Redirect, and Information Disclosure.
Note 3618955 patches a critical code injection vulnerability in SAP S/4HANA and SAP SCM that could enable attackers to take full control of the SAP solutions through the creation and execution of reports containing malicious code.
Note 3623440 introduces additional authorization checks using object S_RZL_ADM with activity 01 to remove a vulnerability that could lead to an escalation of privileges in SAP NetWeaver AS ABAP.
Note 3623255 applies authorization checks using object SCRMMW for a vulnerable function module that could be exploited to trigger a denial of service in SAP Business Warehouse (BW).
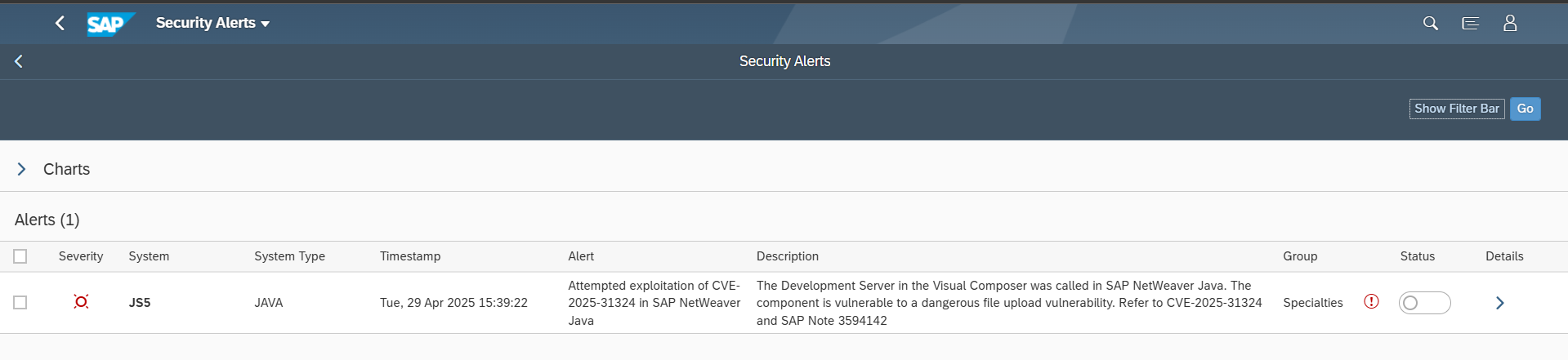
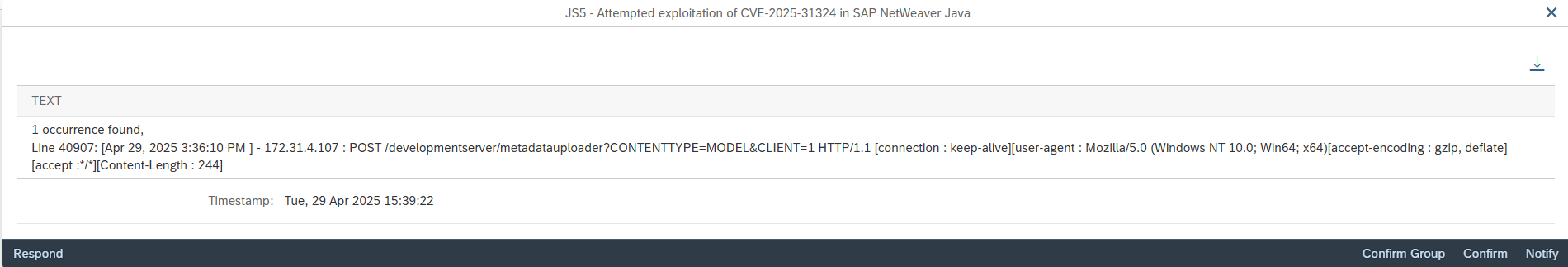
Other important notes include 3565279 which patches older versions of Apache Struts in SAP BusinessObjects Business Intelligence (BOBJ) that are vulnerable to an insecure file operations vulnerability, and 3610591 for a directory traversal vulnerability in SAP NetWeaver Visual Composer.