Countering the Threat of Corporate Espionage
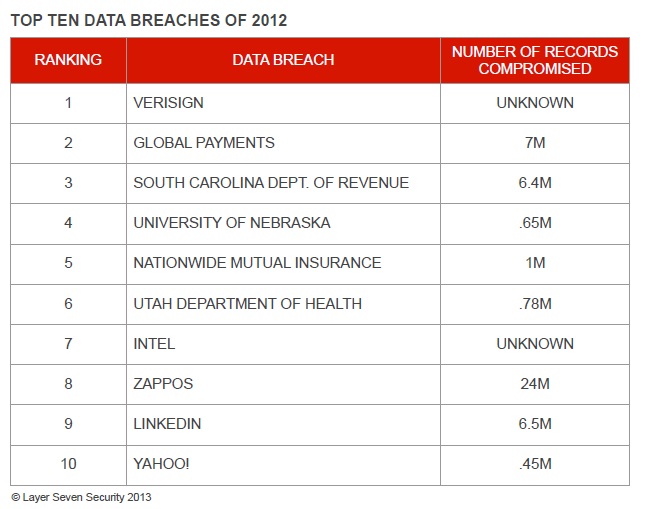
According to the results of a survey released by HBGary during the recent 2013 RSA Conference in San Francisco, more than 70 percent of American investors are interested in reviewing the cybersecurity practices of public companies and nearly 80 percent would not invest in companies with a history of cyberattacks. The survey of 405 U.S. investors also found that more than 66 percent of investors are likely to research whether a company has been fined or sanctioned for data breaches before making an investment decision. The survey underscores the fact that today’s investors are acutely aware of the impact of a successful breach on brand reputation and financial performance. This includes the breach of both customer data and intellectual property (IP).
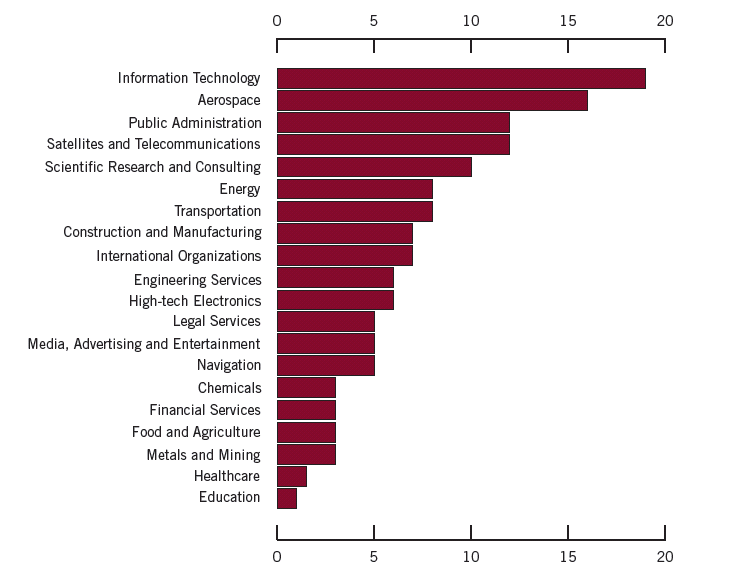
Although the former tends to attract more public attention, the latter has a more pervasive effect on corporate competiveness and performance. A 2012 FBI report entitled Economic Espionage: A Foreign Intelligence Threat to American Jobs and Homeland Security revealed that the cost of IP theft to U.S companies resulting from commercial espionage was over $13 Billion in the last fiscal year. IP-intensive industries account for almost 35 percent of U.S. gross domestic product (GDP) and over 60 percent of merchandise exports. Furthermore, they support 40 million jobs in the United States.
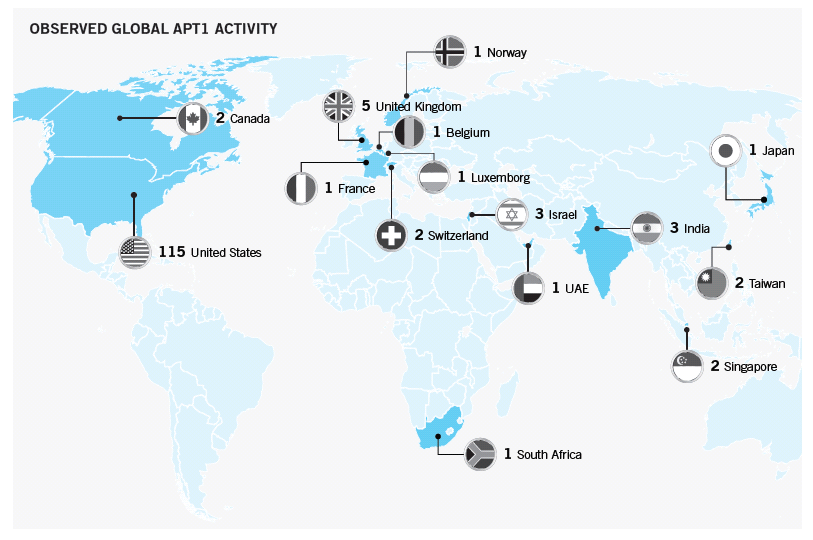
Legal protections such as copyrights, patents and trademarks do not effectively protect intellectual property that is susceptible to theft to regions in which such protections are ineffectively enforced. The importance of IP to the national economy and the difficultly of enforcing rights outside the U.S has led the Department of Homeland Security to brand IP theft as one of the most dangerous threats to national security. In the words of the Assistant Director of the FBI’s Counterintelligence Division, “with each year, foreign intelligence services and their collectors become more creative and more sophisticated in their methods to undermine American business and erode the one thing that most provides American business its leading edge; our ability to innovate.” In a statement to a subcommittee of the House of Representatives last year, the Assistant Director cited the efforts of a foreign corporation to extract information related to the production of titanium dioxide from the DuPont Corporation in 2011. DuPont is an industry leader in the market for titanium dioxide, estimated to be worth $12 Billion.
Although IP theft is far from new, it is amplified by globalization, the increasing interconnectedness of business partners and the accessibility of electronically-stored intellectual property.
In response, the U.S Government Accountability Office (GAO) recommends a variety of technical controls designed to manage access to information, ensure system integrity and encrypt sensitive data. This includes measures to safeguard network boundaries, enforce authentication and authorization, protect against malware, secure communication paths, and analyze, detect and patch vulnerabilities.
The protection of intellectual property within SAP environments requires a combination of countermeasures covering the triad of people, process and technology. The importance of the first and second of these areas should not be understated. Data breaches often result not from the absence of effective technical controls but employee actions or inactions caused by a lack of awareness and training. Therefore, data protection policies and procedures, including incident response plans, are an important component of strategies to safeguard intellectual property. Process-level measures should include risk assessments to isolate and classify IP, and to identify relevant threats.
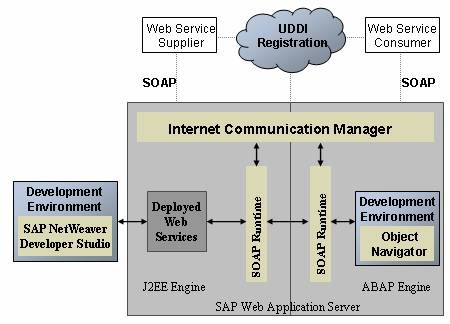
Technical countermeasures should include secure landscape architectures. Firewalls and proxy servers should be used to filter access to SAP systems with properly configured ingress and egress rules. Furthermore, network traffic should be monitored and controlled through in-line intrusion prevention systems and Security Information and Event Management (SIEM) systems capable of detecting and responding to certain types of attacks. Data Leak Prevention (DLP) technologies can also be deployed to block the exfiltration of confidential data. Unfortunately, network-level controls are often side-stepped by targeted and sophisticated attacks. DLP, for example, can be by-passed by encoding, encrypting and transmitting data out of corporate networks using protocols such as VOIP rather than methods such as SMTP and FTP, commonly monitored by DLP systems.
Therefore, technical countermeasures must be applied within multiple, interdependent areas to safeguard SAP assets. This includes application, platform, program and end-user areas. Layer Seven Security’s new white paper, Defense in Depth: An Integrated Strategy for SAP Security, outlines a layered approach to protecting data in SAP systems. The paper discusses methods to secure SAP applications, programs, servers, databases, and other components against attacks that attempt to exploit common weaknesses in such environments and extract proprietary, sensitive and valuable forms of intellectual property from organizations.