
Code Vulnerability Analysis for SAP
Secure custom SAP programs against code injection, cross-site scripting, SQL injection and other attacks
Fast, automated vulnerability scanning for custom SAP programs
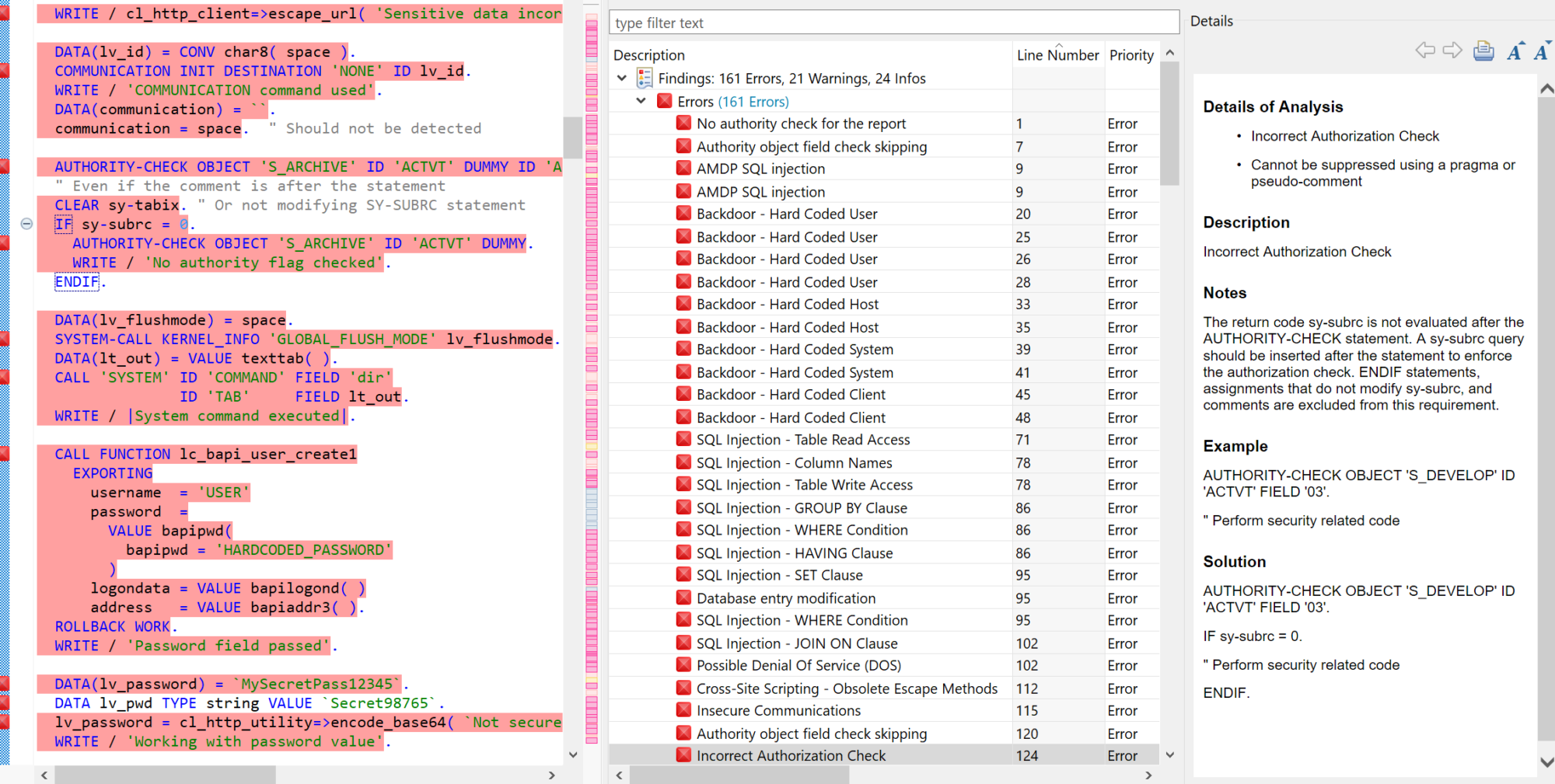
Code Vulnerability Analysis for SAP performs static and dynamic scans to detect vulnerabilities in custom SAP programs. The tool applies 1,000+ test cases to reveal security weaknesses in internal or third-party developed ABAP and UI5 applications. This includes vulnerabilities such as hardcoded users, passwords, and other backdoors, code injection, OS command injection, SQL injection, cross-site scripting, directory traversal, missing or insufficient authorization checks, and calls to sensitive programs, tables, transactions and other objects. Code Vulnerability Analysis for SAP integrates with existing development tools such as the ABAP Test Cockpit and Eclipse Tools. It also integrates with the Transport Management System to detect and block transport requests containing insecure code.
Code Vulnerability Analysis for SAP is available as a standalone solution. It is also included with subscriptions for the Cybersecurity Extension for SAP.
Find the Right Solution for Your Organization


Request a Demo
Schedule a live demo of the Code Vulnerability Analysis for SAP to experience industry-leading protection for your SAP systems using a platform recommended by SAP.

