
Protect Your SAP Systems from Cyber Attack
Partner with an Approved SAP Services Partner to Secure Your SAP Systems
Security is the most common roadblock for successful transformation projects. This includes implementations for SAP RISE/ Cloud ERP, SAP S/4HANA and SAP BTP. The inability to adequately address security concerns leads to delays in 50% of projects, costing an average of $4M. The concerns are justified. Research suggests that insecure SAP deployments in the cloud can be exploited within 3 hours of go-live. Threat activity has been observed for SAP vulnerabilities within 72 hours of public disclosure. The estimated impact of disruption to the availability of SAP systems in large organizations is up to $25M.
Layer Seven Security proactively manage security risks in SAP solutions and support successful SAP transformations and migrations. As an approved SAP Services Partner, we perform a comprehensive security assessment to identify vulnerabilities and threats in SAP solutions. Powered by the SAP-Certified Cybersecurity Extension for SAP, the assessment includes the areas below.
Security Configuration & Hardening
Unsecure SAP systems can lead to significant security, compliance, and operational risks. The discovery and exploitation of even a single misconfiguration by threat actors in SAP systems can expose critical data or disrupt business operations.
Layer Seven Security perform automated scans for 5000+ known vulnerabilities in SAP solutions including SAP /4HANA, HANA and SAP ECC. Vulnerabilities are rated using the Common Vulnerability Scoring System (CVSS) and detailed recommendations are provided to remediate security issues and harden SAP systems.
Custom Code Vulnerabilities
SAP systems often contain custom-developed programs and applications intended to customize SAP solutions for the unique requirements of each customer. This code can introduce vulnerabilities that can be exploited by attackers to compromise SAP solutions.
Layer Seven Security review custom SAP ABAP programs and SAP UI5 applications to identify code-level vulnerabilities such as SQL injection, code injection, cross-site scripting, directory traversal, read/writes for sensitive SAP tables, use of critical function modules and other objects, and missing or insufficient authorization checks.
SAP Security Patches
SAP regularly releases Security Notes to address newly discovered vulnerabilities. Attackers actively monitor these updates to identify weaknesses in unpatched systems. Applying patches promptly prevents exploitation of known issues and blocks common attack vectors.
Layer Seven Security discover relevant unapplied SAP security patches for SAP solutions including critical hot news and high priority notes. The analysis is based on installed software components and versions in each system. Workarounds are provided for the vulnerabilities addressed by security notes, wherever applicable.
SAP Interfaces
SAP systems are highly integrated with other applications, partners, and cloud services. The integrations are powered by RFC, IDoc, BAPI, OData, web service and other interfaces, These interfaces are high-risk entry points to SAP solutions that can be exploited to gain unauthorized access, inject malicious data, or move laterally within networks.
Layer Seven Security review SAP integrations to identify insecure interfaces with missing or weak authentication and encryption or users with excessive privileges. We confirm that interfaces are configured with least-privilege technical, non-dialog users. We also identify unnecessary trusted connections and connections with hardcoded credentials, and confirm strong authentication mechanisms and secure network protocols such as HTTPS and SNC are enforced to verify users and protect data in transit.
Security Compliance
Security compliance is essential to maintain stakeholder trust. SAP solutions manage critical business processes, financial data, and sensitive personal information. Therefore, they are subject to strict regulatory and security standards.
Layer Seven Security audit SAP solutions to verify compliance with standards such as SOX, PCI-DSS, GDPR and NIST. We also perform compliance assessments for SAP security standards such as the SAP Security Baseline and the Security Guide for S/4HANA. For SAP RISE/ Cloud ERP customers, we identify compliance gaps with mandatory security standards in note 3250501 – Information on Mandatory Security Parameters & Hardening Requirements for ABAP Systems in SAP Enterprise Cloud Services (ECS). SAP RISE/ Cloud ERP solutions must comply with these standards to meet requirements for SAP support.
SAP Penetration Testing
Penetration testing simulates real-world attack to find exploitable weaknesses in systems before they are discovered and exploited by threat actors. It’s a proactive, evidence-driven approach to protect critical business systems, validate security controls, and reduce the risk of a data breach.
Layer Seven Security deploy manual and automated techniques to simulate attacks against SAP systems. We mimic the behavior of potential hackers to identify and fingerprint SAP targets in SAP networks. Once detected, we identify misconfigurations and other vulnerabilities in SAP components, services and work processes to formulate an attack methodology.
Finally, we execute a series of attack vectors against targets to systematically compromise servers and access sensitive data. In doing so, we demonstrate the real-world impact of a security breach without modifying or disrupting SAP systems.
User Permissions including SAP Authorizations, Roles & Profiles
Effective access control and segregation of duties (SoD) are essential to reduce the risk of fraud, safeguard sensitive information, and support regulatory compliance with standards such as SOX and GDPR.
Layer Seven Security assess permissions for SAP users to identify users with excessive or unnecessary access privileges. This administrative and functional privileges for business processes in SAP S/4HANA and SAP ECC. We also identify users with permissions that violate the principle of the Segregation of Duties in S/4HANA and SAP ECC.
Implementation & Assessment Process
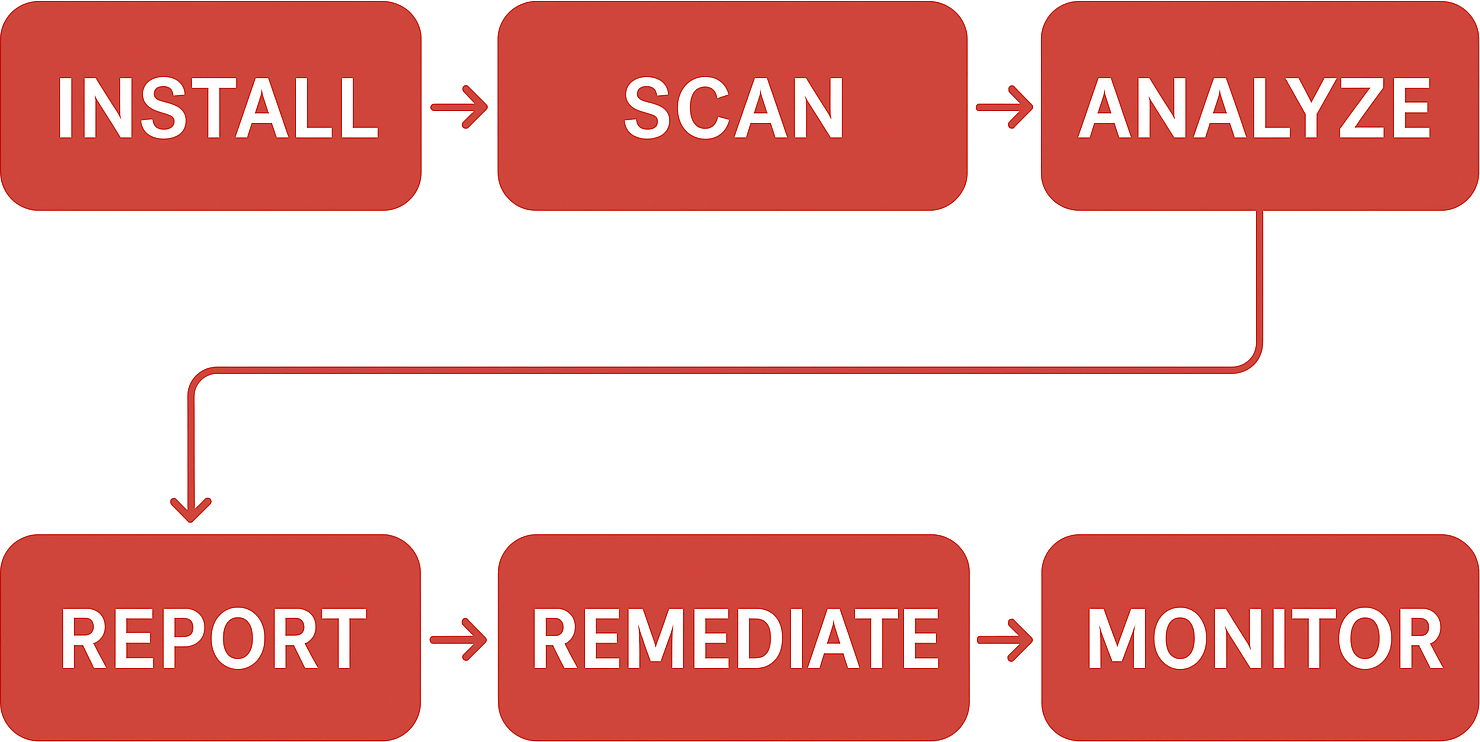
The typical timeframe for the assessment is 2 weeks for up to 5 SAP System IDs (SIDs) and 4 weeks for up to 20 SIDs. The Cybersecurity Extension for SAP requires approximately 6 hours of effort from SAP Basis and Security teams to install and configure, supported by Solution Engineers at Layer Seven Security. The software is installed in SAP systems using the SAP Add-On Installation Tool SAINT.
Once installed, the Cybersecurity Extension for SAP scans the target systems for security vulnerabilities. The results are available immediately and analyzed using applications accessed from the SAP Fiori launchpad. The solution will run daily scheduled scans to update results. Findings are exported from the software to support the deliverables of the assessment including executive and detailed reports.
The reports are shared with customers through secure channels. The findings and recommendations are presented by Layer Seven Security during a formal close-out. The addons are uninstalled using SAINT after the successful completion of the assessment.
Benefits:
Deliverables:
The Cybersecurity Extension for SAP ensures your SAP systems are compliant, protected and equipped for audits and certifications. Flexible licensing options let you choose between 30–90-day terms for one-time assessments or 12–36-month plans for sustained monitoring. From targeted security assessments to continuous monitoring, contact Layer Seven Security to discuss how you can leverage the Cybersecurity Extension for SAP to protect your mission-critical SAP systems from cyber threats.
Contact Layer Seven Security
Schedule a call with our SAP cybersecurity specialists to discuss how we can help secure your SAP systems from cyber threats.



























