Secure Your Custom Code with the Cybersecurity Extension for SAP
The Cybersecurity Extension for SAP Solution Manager now supports static code analysis for custom SAP programs. Released in September, version 3.3 performs code vulnerability detection for hard coded users, passwords, hosts, systems, and clients, SQL injection, cross-site scripting, missing or insufficient authorization checks, directory traversal, sensitive table reads and writes, OS command injection, and insecure communication methods and passwords.
The ABAP checks are integrated with SAP Code Inspector (SCI) and ABAP Test Cockpit (ATC). They can be applied for new developments and existing custom programs. For existing programs, periodic scans are scheduled in the ATC. Scan results are also viewed using ATC. The results below are displayed in SAP Eclipse.
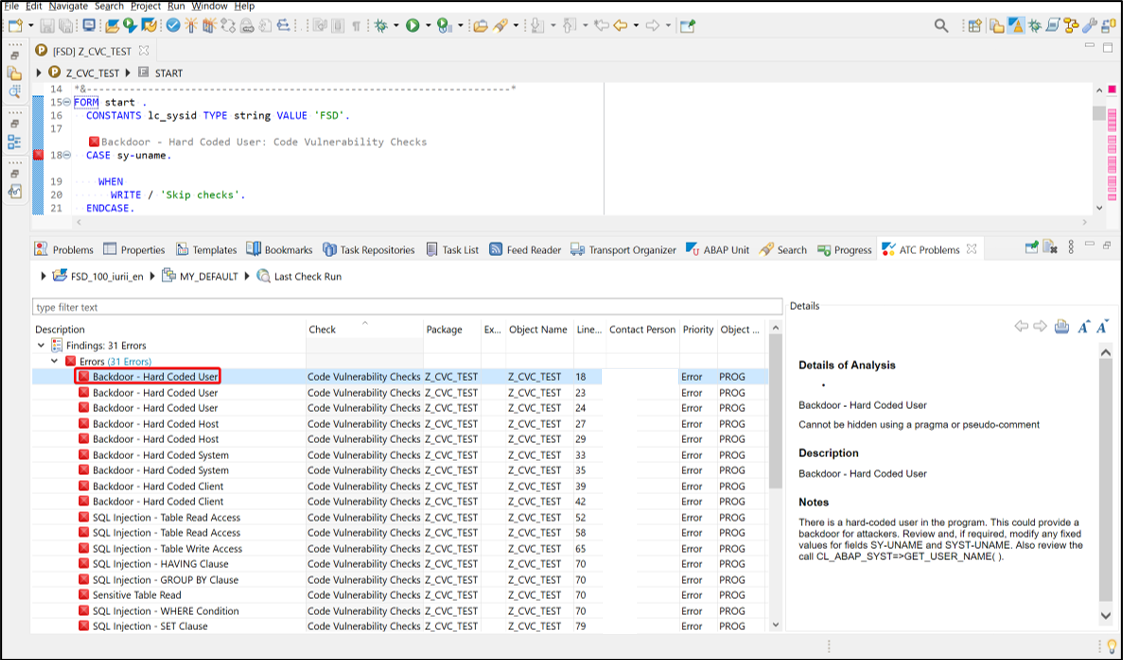
The details of vulnerabilities including the impacted lines of code in the relevant objects can viewed by clicking on each error.
Findings are integrated with the Vulnerability Report in SAP Solution Manager. Remediation plans can be recorded and tracked using action plans in Solution Manager. Alternatively, exemptions can be requested for vulnerabilities in the ATC.
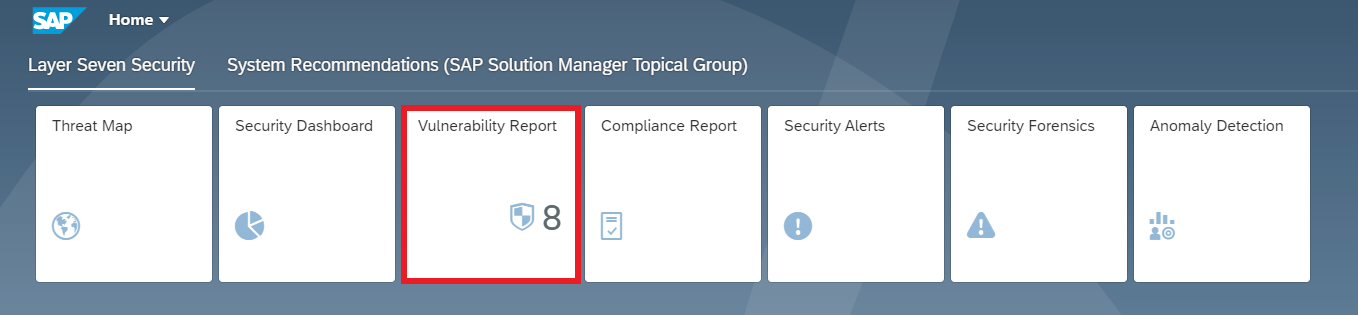
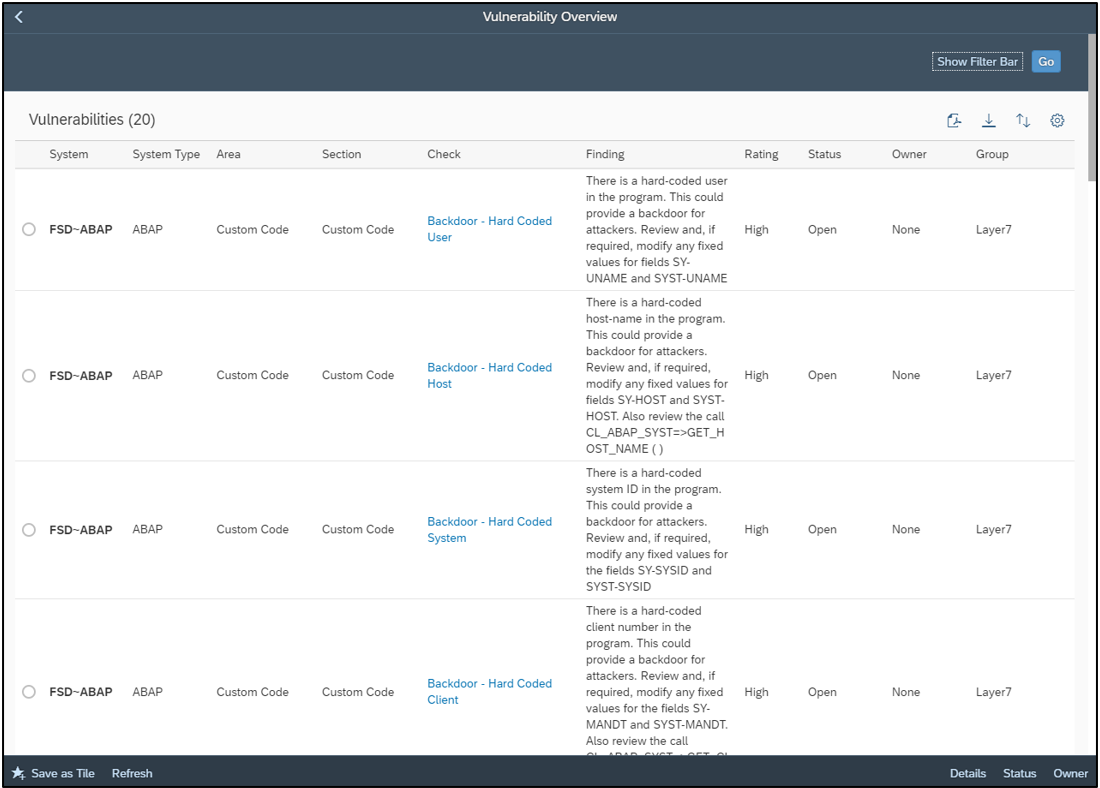
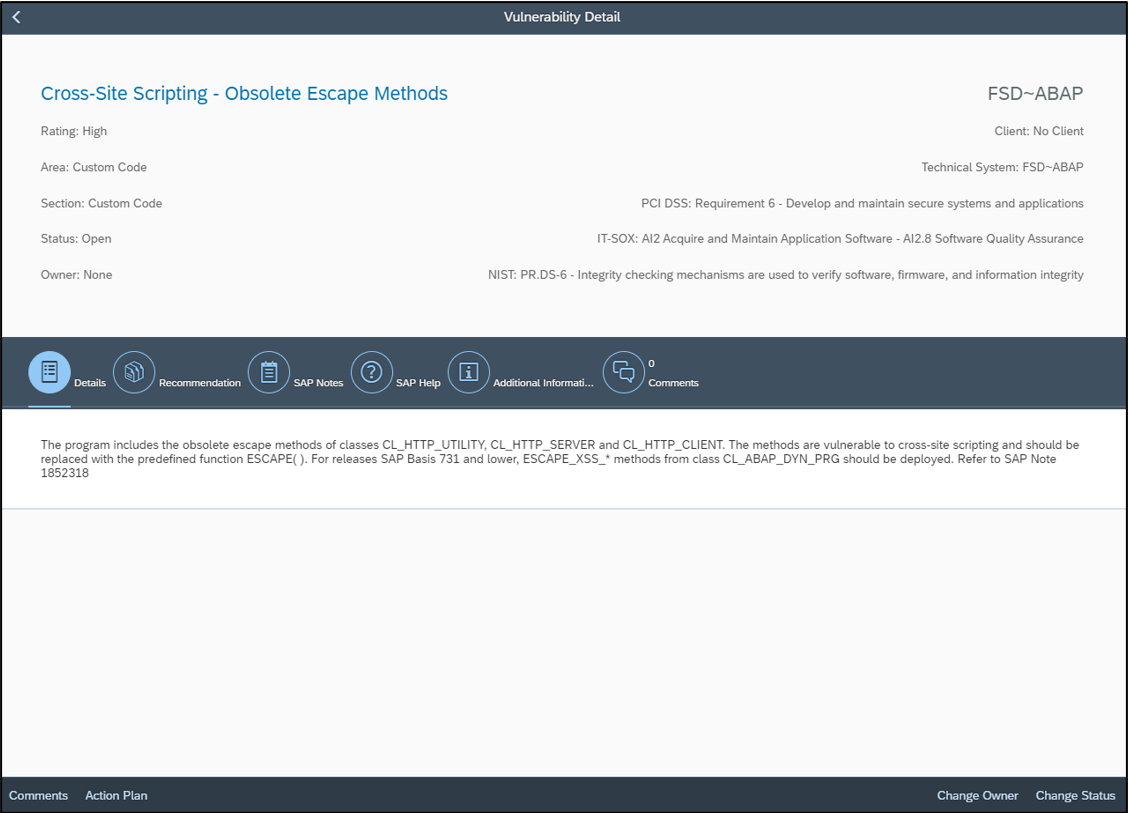
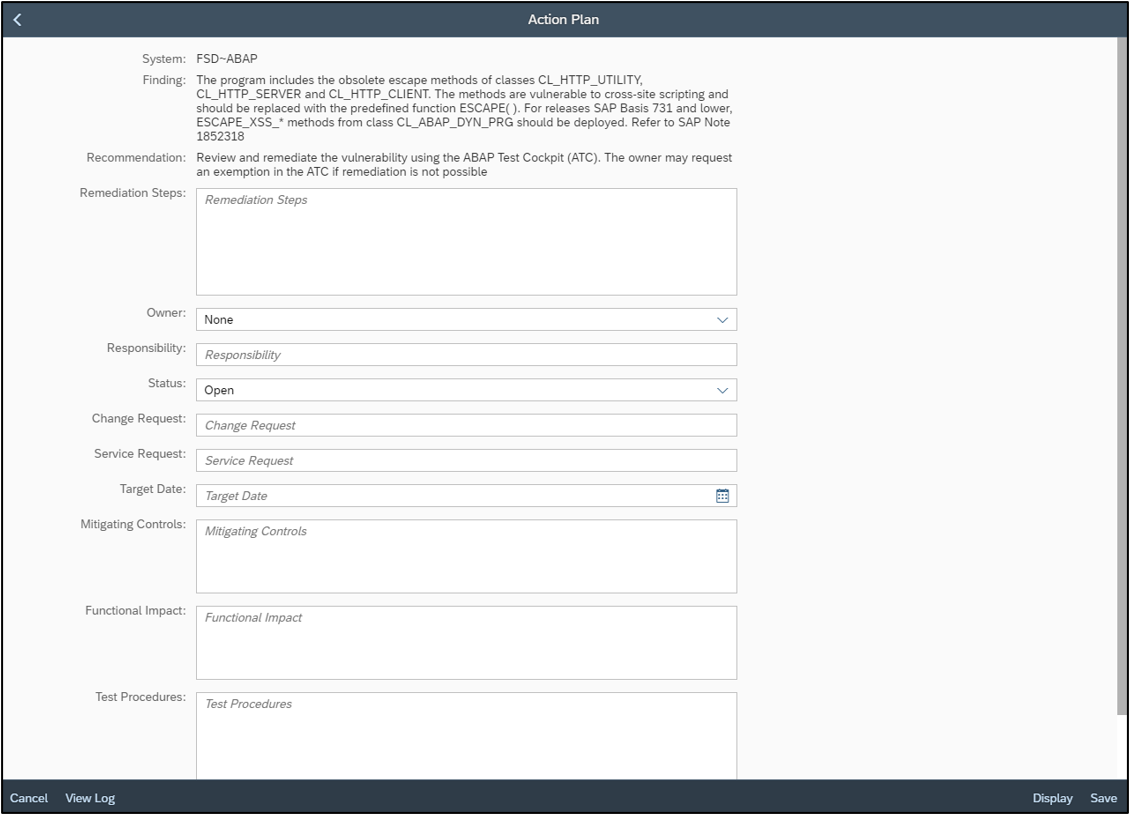
Automatic blocking for transport requests containing security-related errors can be enforced in the Change and Transport System (CTS). Furthermore, the SAP BAdI CTS_REQUEST_CHECK can be implemented to trigger security checks during the release of a transport request.
Checks can be applied from central systems for remote systems. The procedures are outlined in SAP Note 2364916 and a Technical Article in the SAP Community.

