
Cybersecurity Extension for SAP
SAP-Certified Cybersecurity Protection for SAP Solutions
Standard Edition
Secure your SAP solutions from cyber attack with the Cybersecurity Extension for SAP
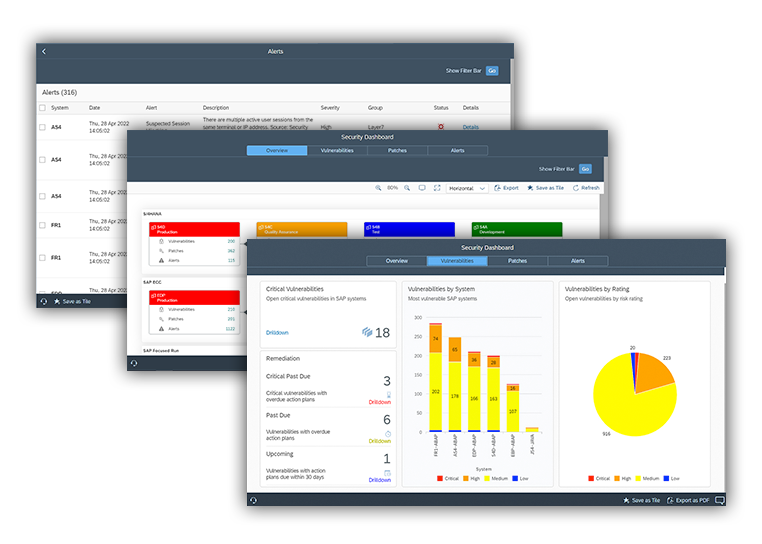
The Cybersecurity Extension for SAP automates vulnerability management, custom code security, and threat detection to secure SAP solutions against advanced persistent threats.
The software protects on-premise, cloud and hybrid SAP systems. It delivers near real-time security intelligence to detect vulnerabilities and indicators of compromise in SAP applications. The solution is available as a subscription service.
The Cybersecurity Extension for SAP is certified by SAP for integration with SAP S/4HANA. It also supports SAP ABAP, SAP HANA and SAP J2EE solutions.
The solution supports cross-stack security for SAP systems including application, database and host layers.
The standard edition of the Cybersecurity Extension for SAP can be installed in SAP Solution Manager and SAP Focused Run. A version for other SAP NetWeaver AS ABAP systems such as SAP GRC is planned for Q4 2024.
The cloud edition is software-as-a-service, optimized for SAP RISE customers.
Secure Your Transition to SAP S/4HANA
Manage User Risks, Secure Custom Code and Protect Cloud Systems
Key Features
Better than the Competition
Review the product comparison to see how Layer Seven Security stacks up to the competition including SAP, OSP and SBP.
Sign Up for a Demo
Schedule a live demo of the Cybersecurity Extension for SAP® Solutions to experience industry-leading protection for your SAP systems.























