Explore Service Level Reporting in SolMan 7.2
Service Level Reporting (SLR) in SAP Solution Manager performs regular checks against key performance indicators using information available from the EarlyWatch Alert (EWA), Business Warehouse (BW) and the Computer Center Management System (CCMS). The checks can be for single systems or systems grouped into solutions. Reports run automatically on a weekly or monthly schedule but can also be triggered manually for on-demand reporting. SLRs can be displayed in HTML or Microsoft Word. SAP Solution Manger automatically distributes SLRs by email to recipients maintained in distribution lists.
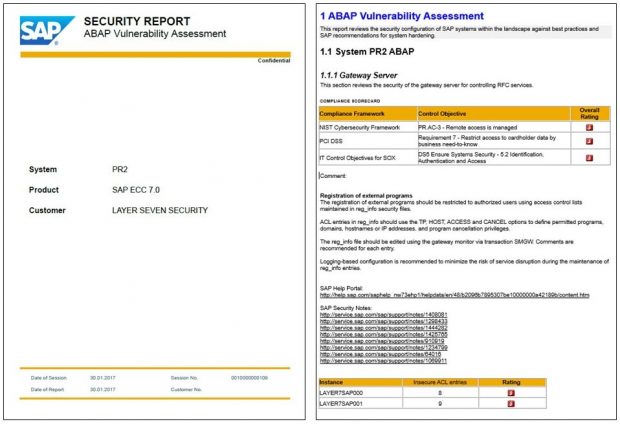
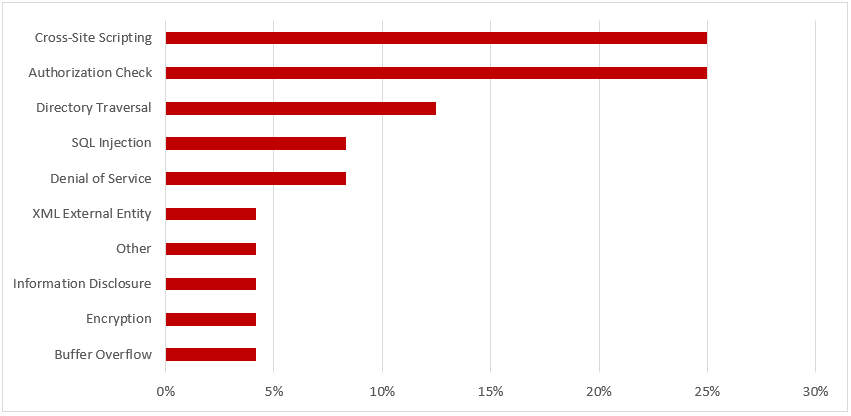
Security-related metrics stored in internal or external BW systems can be read by SLR to create dynamic, detailed and user friendly vulnerability reports. This includes areas such as settings for profile parameters, access control lists in gateway security files, trusted RFC connections or destinations with stored logon credentials, unlocked standard users and standard users with default passwords, active ICF services, filter settings in the security audit log, missing security notes, and users with critical authorizations, profiles or transactions. For HANA systems, it includes database parameters, audit policies, the SYSTEM user, and users with critical SQL privileges. For Java systems, it includes properties for the UME and the invoker servlet. Furthermore, since event data from monitored systems is stored in BW and CCMS, SLR can also report on metrics for events in audit logs including the security audit log and syslog. The latter is particularly relevant for HANA systems which can write logs to operating system files.
SLRs are created and customized in the area for SAP Engagement and Service Delivery in the Fiori Launchpad.
Variants need to be maintained for each report including relevant systems, solutions, data sources, metrics, thresholds and schedule (weekly or monthly).
Once activated, the reports are executed by a regular automated job and accessed through the tile for Service Level Reports.
Comments can be included in SLRs before the reports are automatically distributed by email. SLRs include details of each vulnerability check, risk ratings, and links to relevant SAP Notes and documentation at the SAP Help Portal. Reports also include a gap assessment against compliance frameworks such NIST, PCI-DSS and IT-SOX. SLRs are archived by Solution Manager for trend analysis.