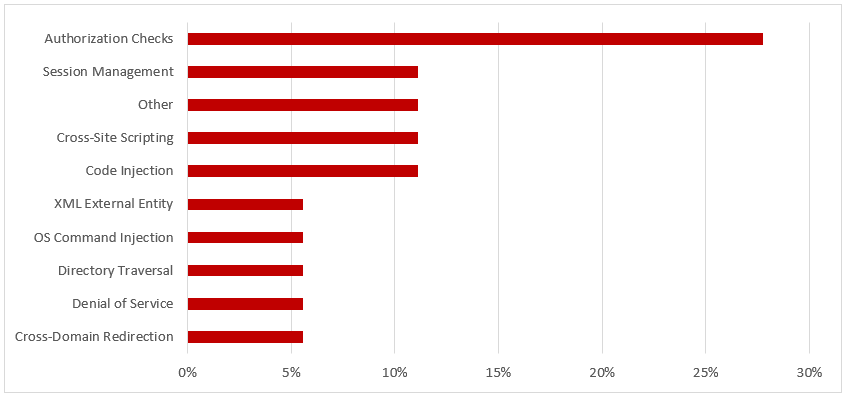
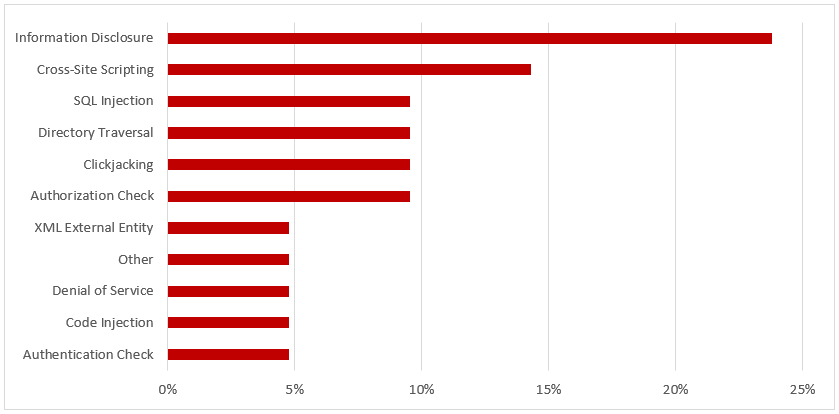
SAP Security Notes, December 2018
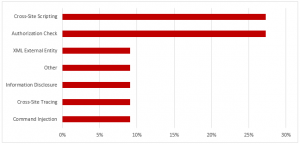
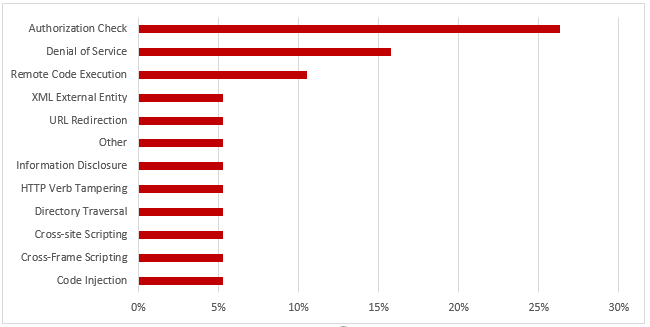
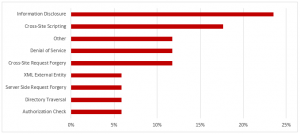
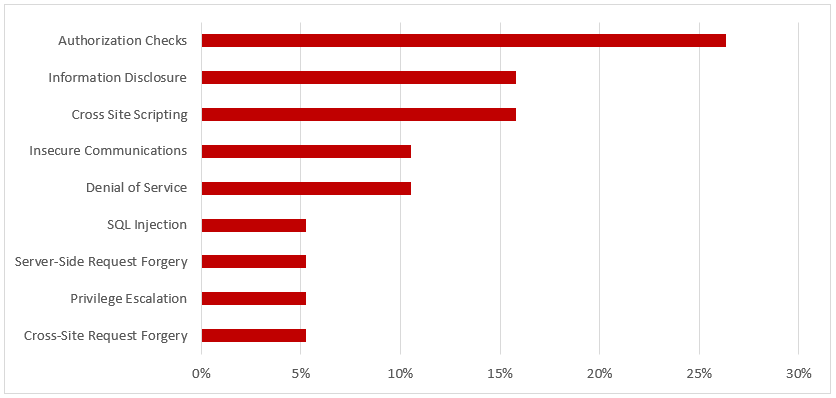
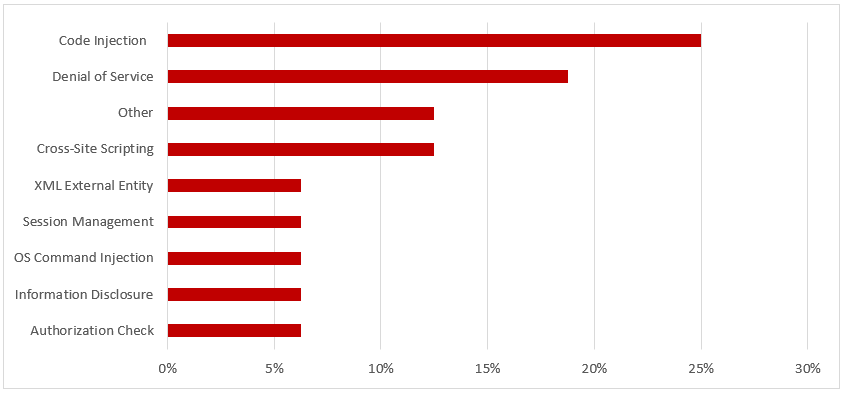
Hot News Note 2711425 patches a critical Cross-Site Scripting (XSS) vulnerability in SAP Hybris Commerce storefronts. The vulnerability could be exploited by attackers to modify web content and compromise user-related authentication data. It affects versions 6.2 through 6.7 and 18.08 of SAP Hybris Commerce, including all but the latest patch releases. The vulnerability carries a CVSS v3.0 base score of 9.3/10 and scores particularly high in terms of impact to confidentiality and integrity. The related exploit is relatively non-complex and does not require any privileges in the target system. In addition to applying the automated updates referenced in Note 2711425, manual steps may be required to remove the vulnerability in cases where custom HTTP headers are used for caching, SAP Hybris Commerce is positioned behind a HTTP reverse proxy or load balancer, or the system is used in conjunction with a content delivery network (CDN).
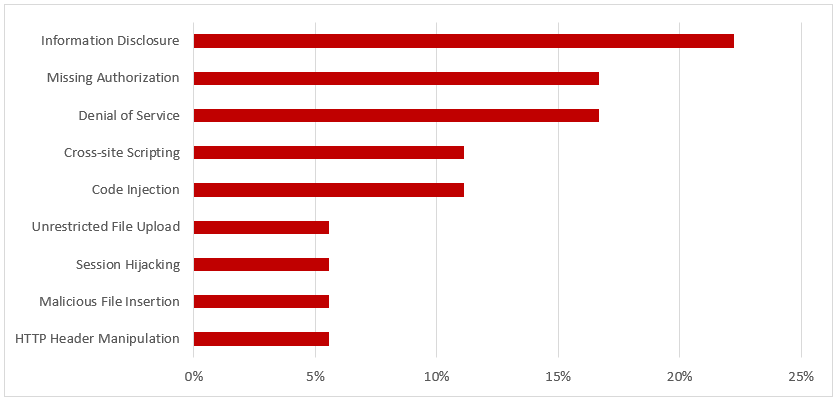
Note 2642680 deals with a high-risk XML External Entity (XXE) vulnerability in SAP NetWeaver Application Server Java (AS Java) caused by missing validation for XML documents received from untrusted sources. The vulnerability could lead to the compromise of the SAP file system or enable attackers to provoke a denial of service.
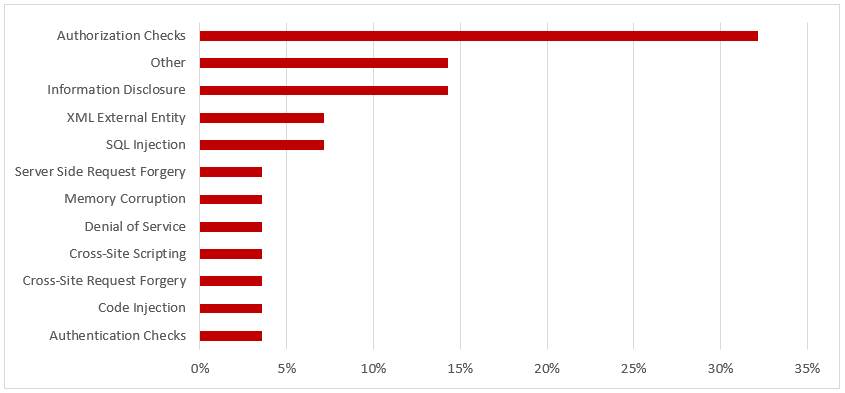
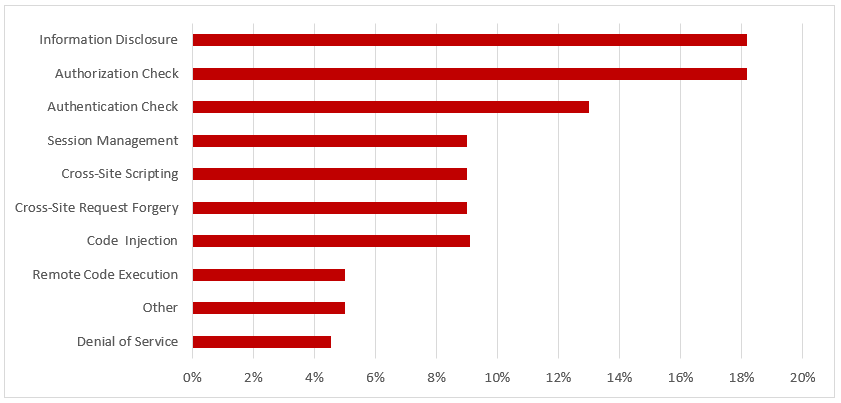
Note 2658279 patches an insufficient authorization check impacting the AS Java keystore service.
Note 2698996 removes a missing authorization check in SAP Customizing Tools. The note introduces a check for object S_RFC_ADM to prevent an escalation of privileges.