Securing OS Platforms with the Cybersecurity Extension for SAP
Securing SAP hosts is a critical component of SAP system hardening. Vulnerable operating systems can provide a pathway to SAP applications, databases and other components, bypassing security mechanisms applied in such layers. This can lead to the compromise of SAP systems including the corruption of critical files and tables. It can also support ransomware attacks that disrupt the availability of SAP services.
The Cybersecurity Extension for SAP Solution Manager performs daily automated scans to identify vulnerabilities in SAP hosts. For Linux operating systems, this includes authentication settings, firewall configurations, file and service permissions, root access, missing security patches, vulnerable packages and services, and misconfigured settings for logging and auditing. It also includes the detection of open TCP/ UDP ports that are targeted by attackers, including FTP, RPC, RDP, SSH, and Telnet.
OS findings are mapped to SAP systems, supporting holistic security across code, application, database and operating system layers.
The Extension also monitors OS logs to identify indicators of compromise in SAP hosts. Alerts and notifications are triggered for security incidents and channeled to SIEM and service desk systems. This includes the following scenarios:
- Changes to operating system configuration, profile, and kernel parameters
- Firewall and other network settings
- File system mounts and unmounts
- Group, user and password changes
- Cron jobs
- Daemon and service changes
- OS scripts
- External connections
- Sudo users
- Root and sudo commands
- Failed logon and file access attempts
- Critical file changes
- File permission changes
- OS code injection
- User locks and unlocks
- Changes to audit settings and records
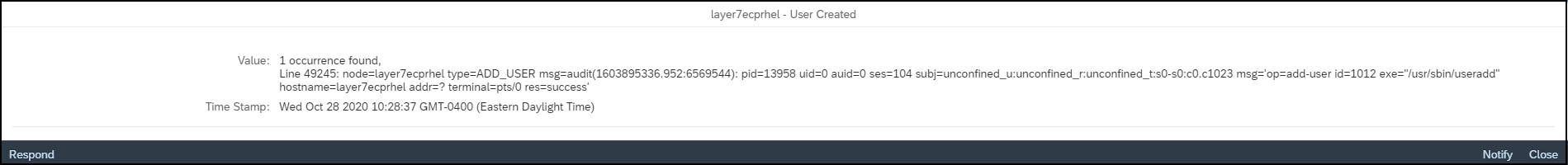
Audit records from the Linux audit log are displayed in the alert details. The records include the audit event number and auid of the initial user that triggered the event.
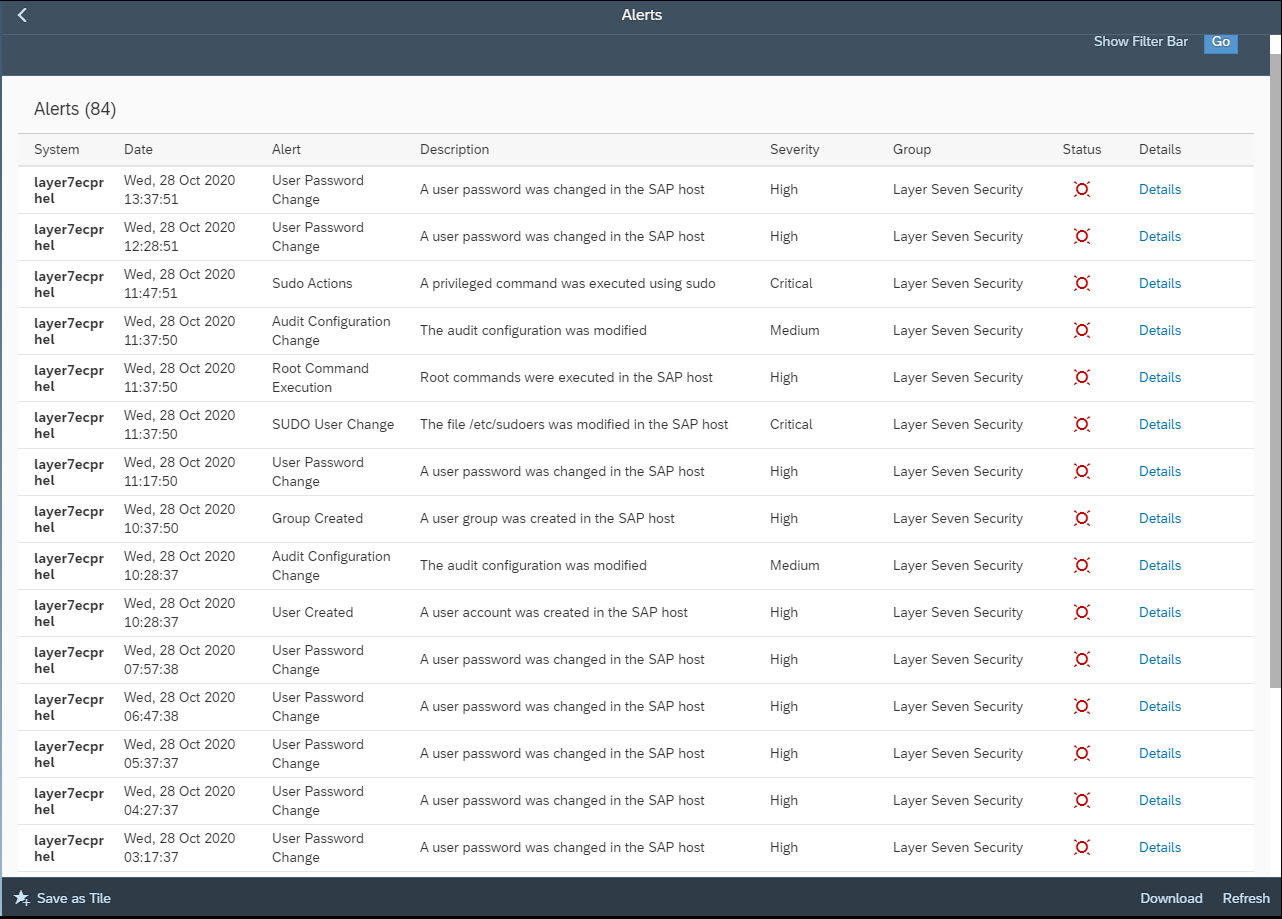
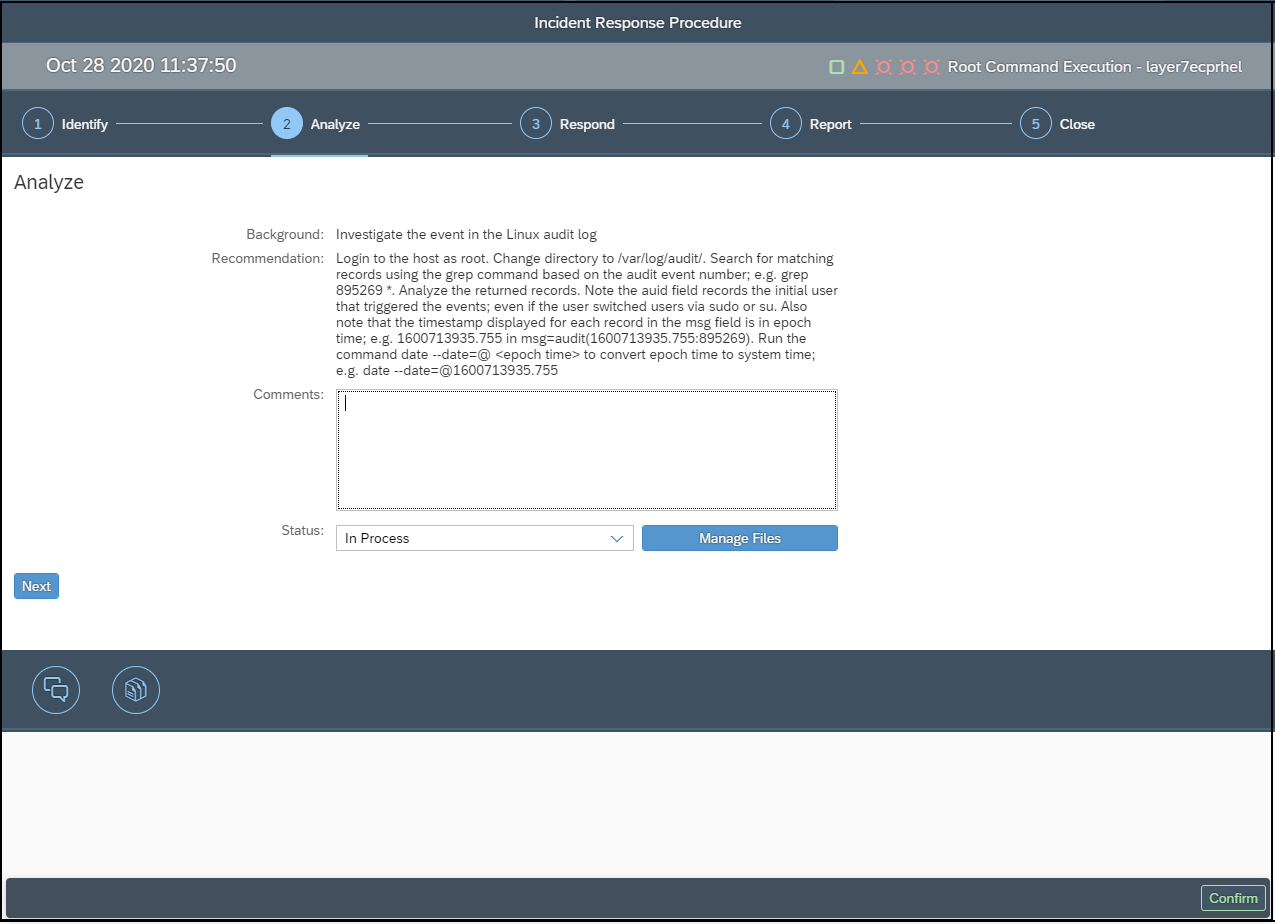
The Cybersecurity Extension for SAP Solution Manager includes integrated incident response procedures to support forensic investigations. Users can select the Respond option from an alert to start an investigation and document the findings.
The Extension currently supports monitoring for Red Hat Enterprise Linux (RHEL) and SUSE Linux Enterprise Server (SLES). Support for IBM AIX and Microsoft Windows Server is expected in 2021.

