Securing Oracle Databases for SAP
According to Gartner research, 70 percent of SAP customers have yet to migrate to S/4HANA. Based on current rates of adoption, SAP is unlikely to achieve its goal of migrating ECC customers to S/4HANA by 2027. As a result, the majority of SAP solutions continue to be driven by conventional databases. One of the most common database platforms for SAP is Oracle.
Oracle databases including several important security features to protect data at rest and in transit. This includes network encryption for securing communications between application and database servers, transparent database encryption for encrypting database tables, columns or complete tablespaces, granular access control using Database Vault, and Unified Auditing to support advanced policy-based logging. However, poorly configured Oracle databases can provide a vulnerable target for attackers to access and compromise data in SAP systems, bypassing application-level security and detection.
This article details best practices for securing Oracle databases against common vulnerabilities and exploits to protect against SAP attacks targeted at the database layer.
One of the most important steps is disabling the OPS$ mechanism in Oracle. In earlier versions of Oracle, the password for the SAP database user was retrieved from Oracle tables via an operating system user. The user was able to logon to the database via a shell prompt using credentials maintained at the OS level. The OPS$ mechanism enables threat actors to logon remotely to Oracle using locally-created users with the same IDs as OS users that are authenticated externally. This was deprecated from Oracle 11g. The encrypted password for the SAP database user is now stored in the Secure Storage File System (SSFS). The OPS$ mechanism is disabled using the value FALSE for the database parameter REMOTE_OS_AUTHENT.
Other important parameters include 07_DICTIONARY_ACCESSIBILITY to limit access to objects in the system SYS schema, global_names for blocking database connections from unauthorized domains, remote_login_passwordfile for preventing the use of password files to authenticate users, and options for enforcing robust password policies for database users including password complexity and expiration.
There are several standard users that are enabled in Oracle databases when a new database is created. The default passwords for the users should be changed after the install. Refer to the Oracle Help Center for the full list of standard users.
Users in the PUBLIC group should not be able to execute sensitive packages such as UTL_ORAMTS, UTL_HTTP and HTTPURITYPE. These packages can be used to send data to external destinations. All database users are members of the PUBLIC group.
The WITH_ADMIN privilege should not be included in permissions and roles granted to users, except for Oracle-maintained users. Users with the privilege can grant the permissions and roles to other users.
Critical system and table privileges should be restricted to authorized users only. This includes ALTER SYSTEM, GRANT ANY PRIVILEGE and BECOME USER. The last privilege enables users to inherit the privileges of other users.
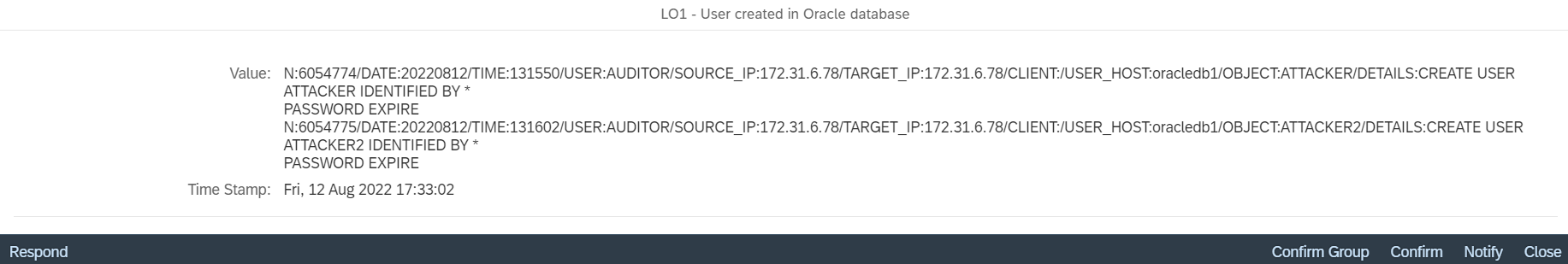
Auditing should be enabled for specific database events. Examples include role and user changes, profile changes, database links, granting object and system privileges, changes to stored procedures, and schema triggers. Logging of successful and unsuccessful attempts to alter the audit trail in the SYS.AUD$ table is also recommended.
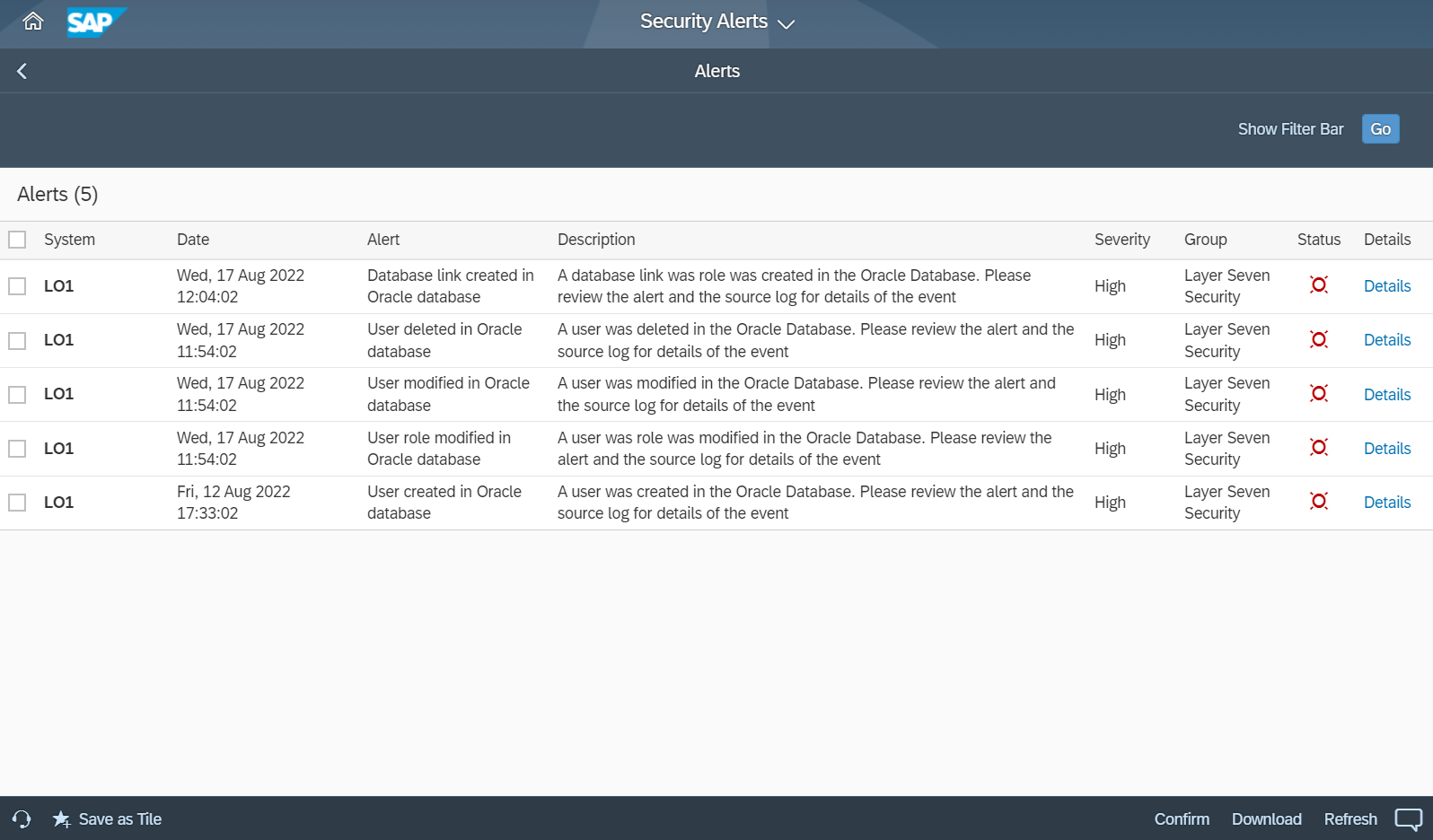
The Cybersecurity Extension for SAP (CES) performs comprehensive vulnerability scans for Oracle databases supporting SAP applications. The SAP-certified add-on automatically detects Oracle vulnerabilities including insecure authentication mechanisms, database misconfigurations, standard users with default passwords, users with critical roles and privileges, and incomplete audit policies.
CES also monitors Oracle database logs to detect and alert for security incidents and potential data breaches. CES is the only solution that secures the entire SAP stack including application, database and host layers. For host monitoring, CES also supports vulnerability management and threat detection for Oracle Linux operating systems, as well as other Linux variants including Red Hat Enterprise Linux (RHEL) and SUSE Enterprise Linux Server (SLES). In next month’s blog, we will discuss security and monitoring for Microsoft platforms supporting SAP systems, including SQL Server and Windows Server. Coverage for both platforms is included in the Cybersecurity Extension for SAP.