Compliance Reporting for the SAP Security Baseline
The SAP Security Baseline is a widely used benchmark for securing SAP applications. The benchmark includes SAP recommendations for system hardening, authentication and authorization, logging and auditing, and other areas. The recommendations draw on SAP security notes, guides and whitepapers. The SAP Security Baseline was updated by SAP earlier this year and provides an up-to-date framework for safeguarding SAP ABAP, HANA and Java systems against known vulnerabilities and threats. Note 2253549 includes a link to the latest version of the framework.
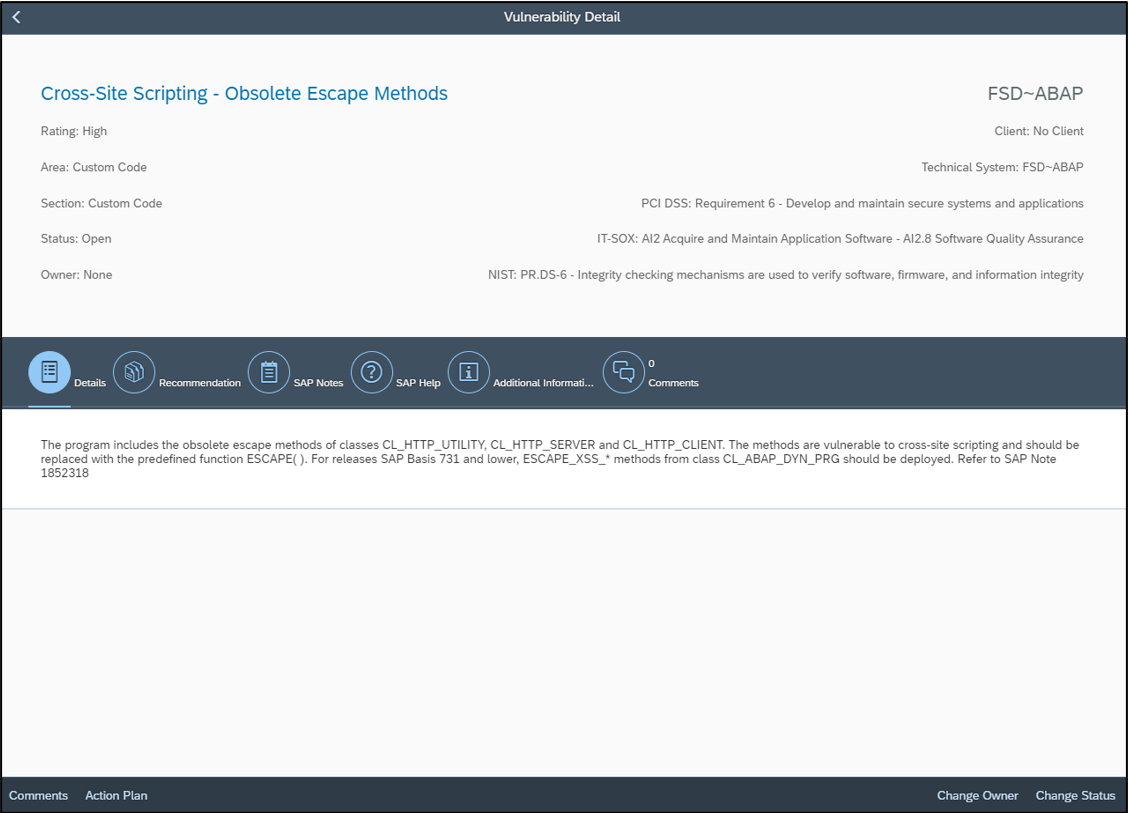
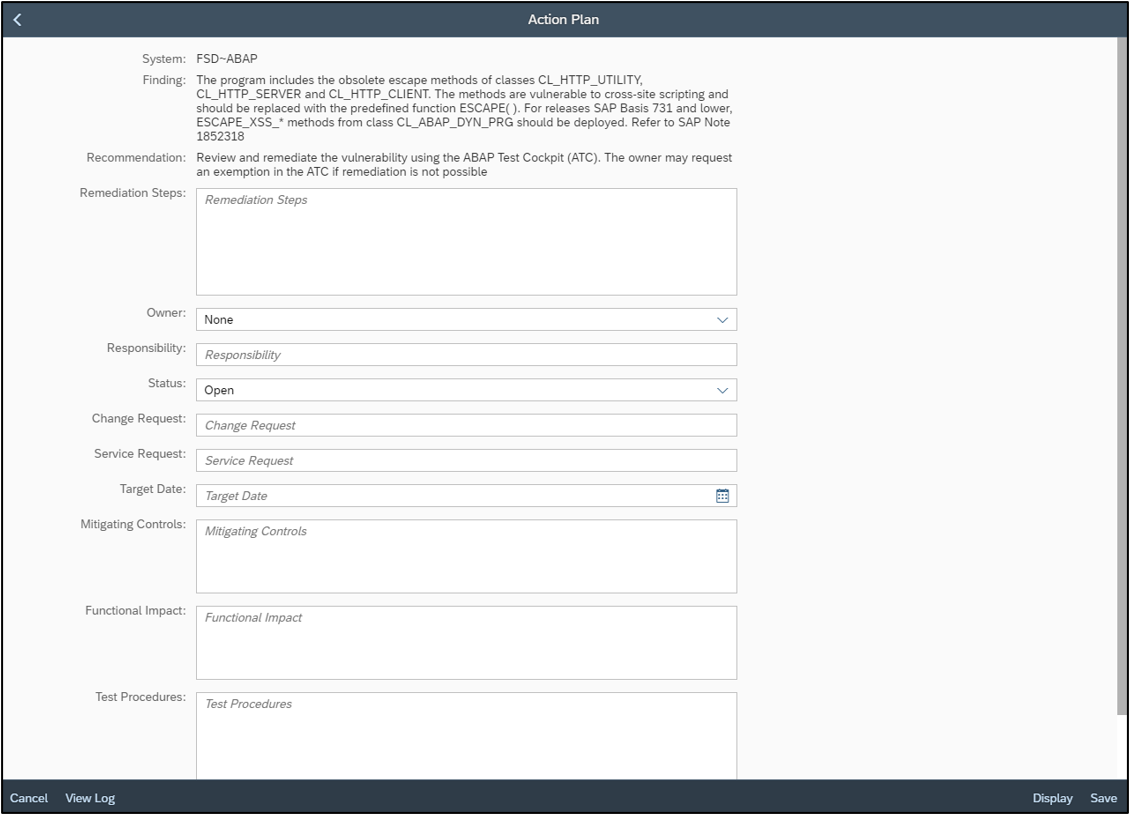
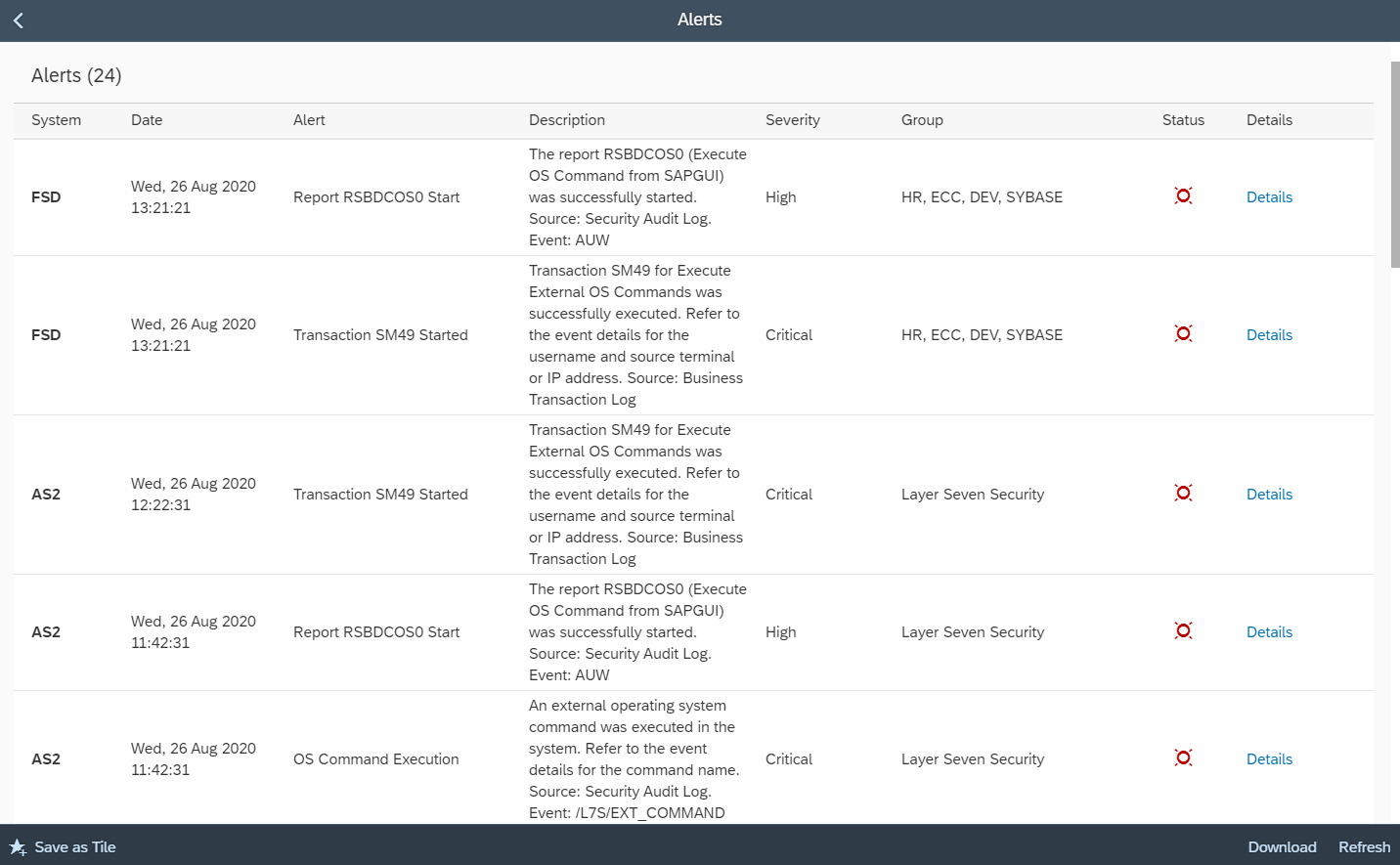
The Cybersecurity Extension for SAP Solution Manager performs automated gap assessments for SAP systems against the SAP Security Baseline. The extension identifies compliance gaps in SAP systems to highlight configuration, user and other issues that do not meet SAP requirements defined in the baseline. The extension eliminates the need for periodic, manual audits and supports on-demand compliance reporting.
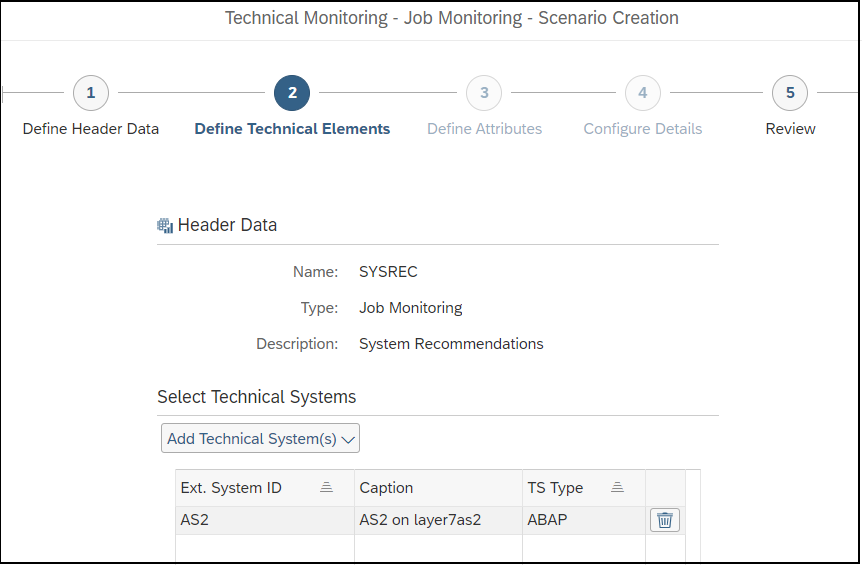
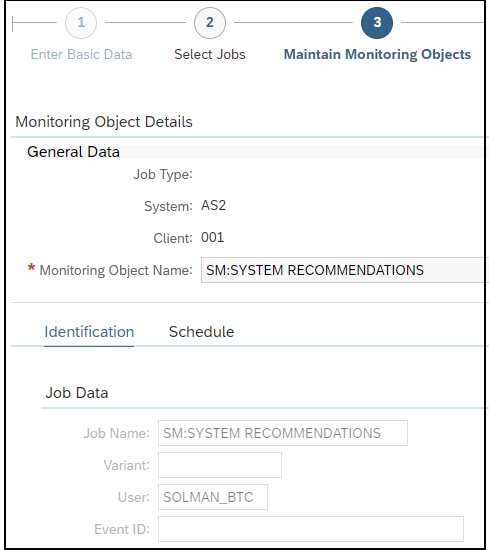
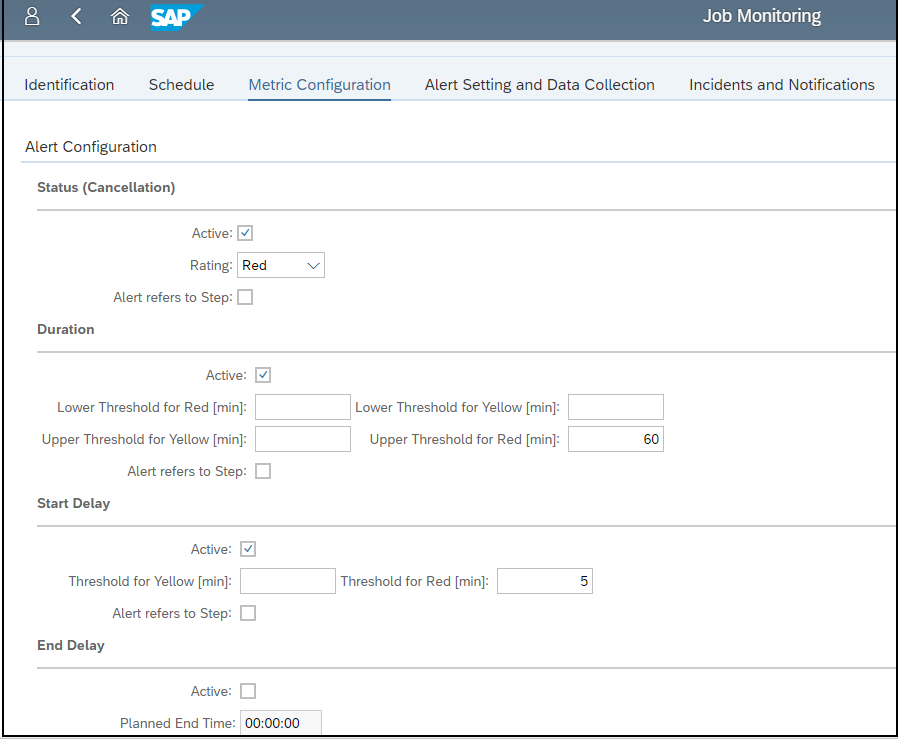
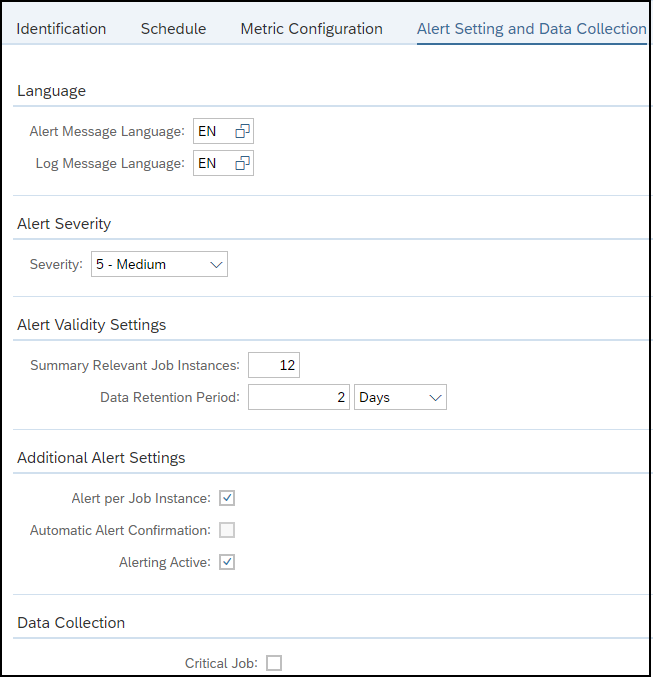
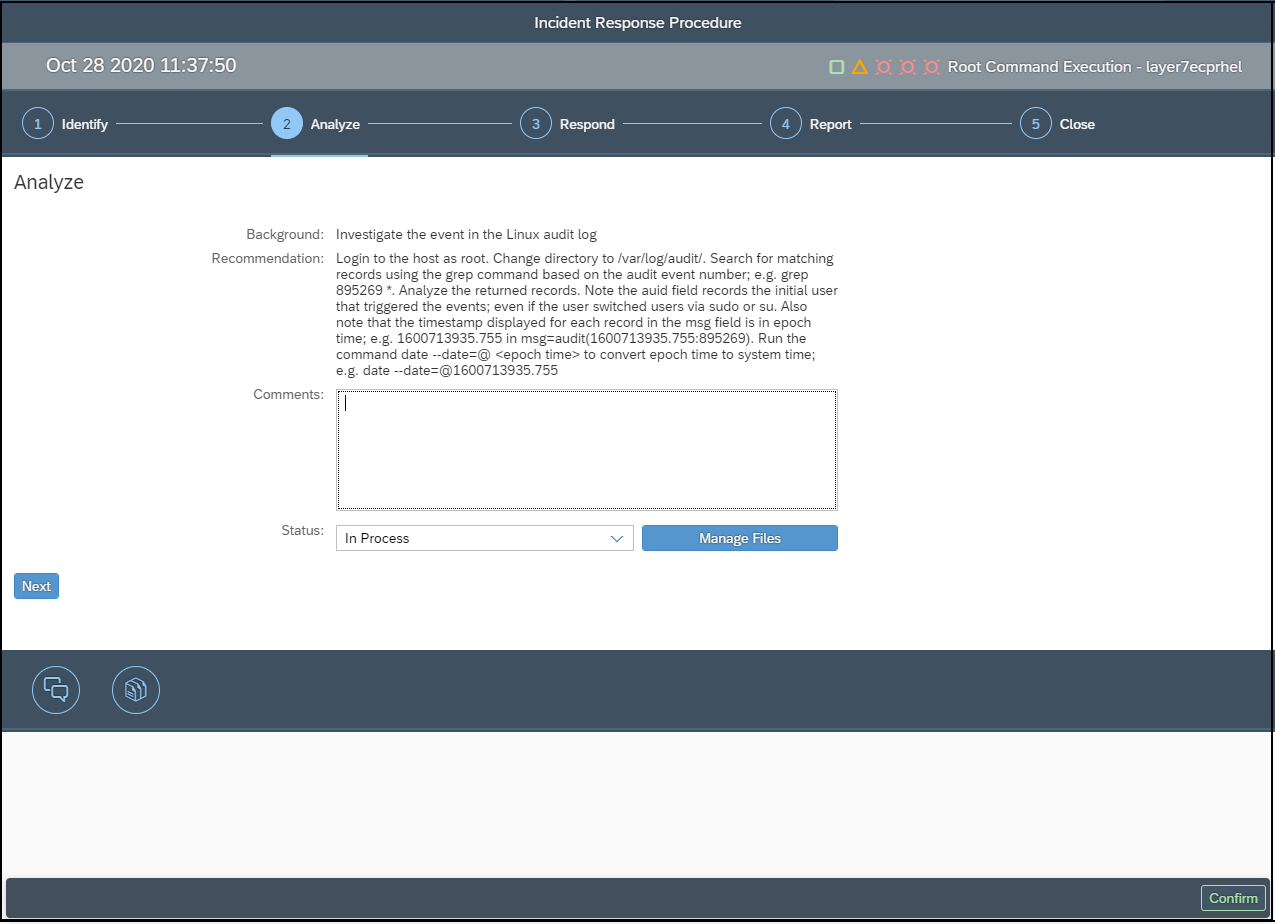
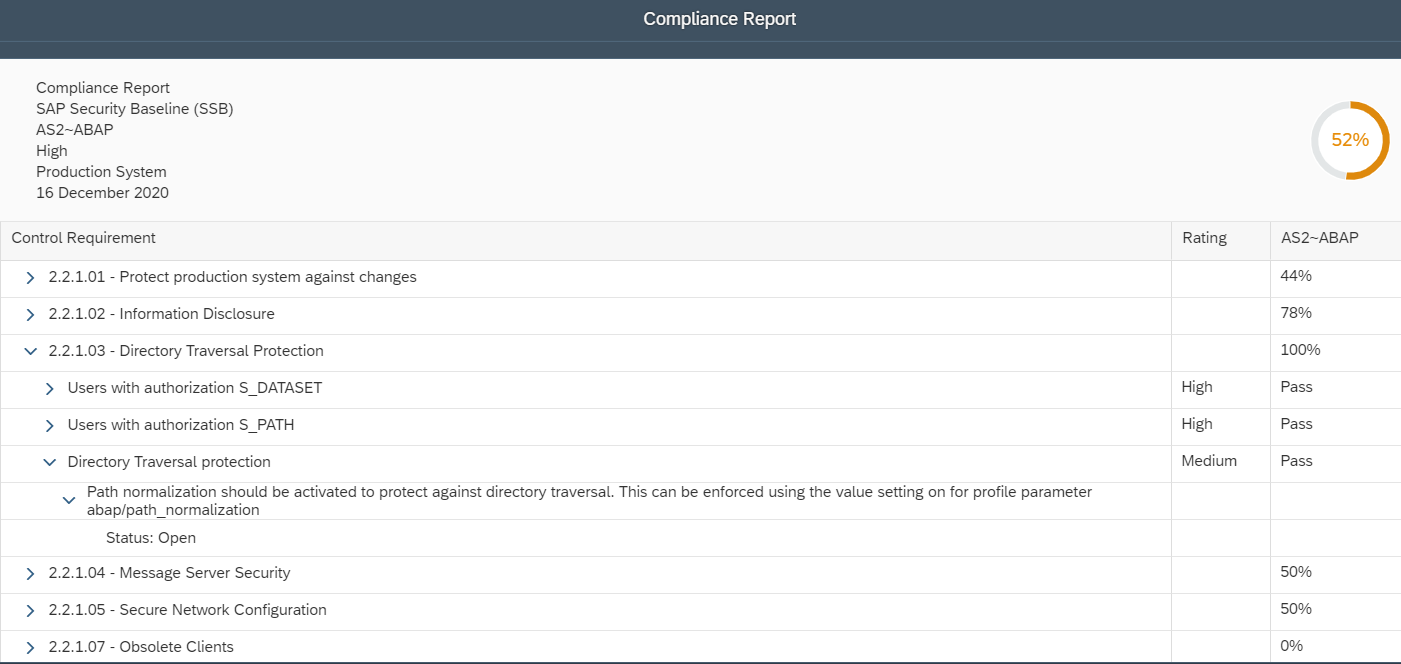
Control gaps are automatically discovered via daily background jobs. The gaps are reported in the Compliance Report application, accessible from the Fiori launchpad for SAP Solution Manager.
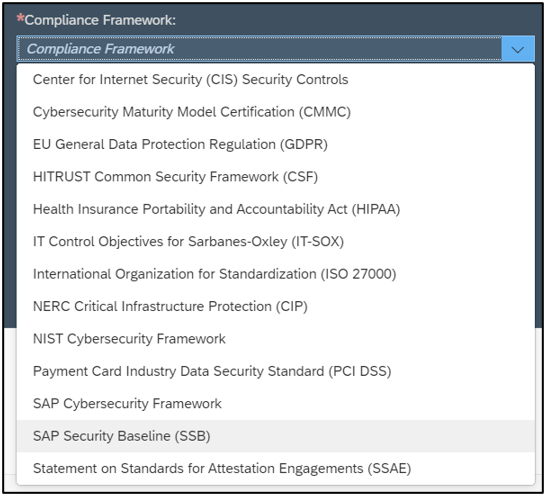
The SAP Security Baseline template can be selected from the list of supported frameworks.
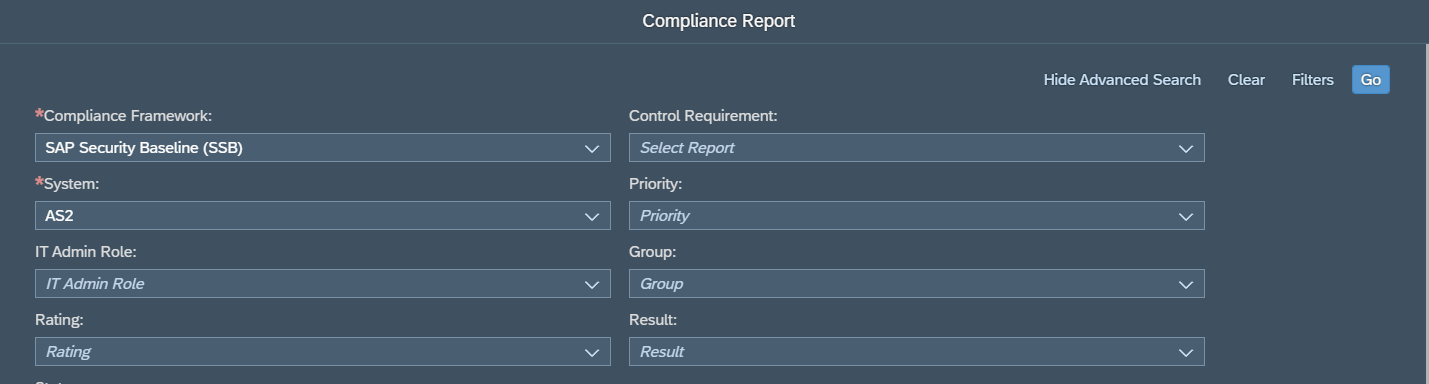
There are optional filters to select specific baseline requirements and systems based on environment or priority. Reports can also be filtered to include or exclude requirements based on risk rating and compliance result. Once the framework and system is selected, users can select Go to view the results.
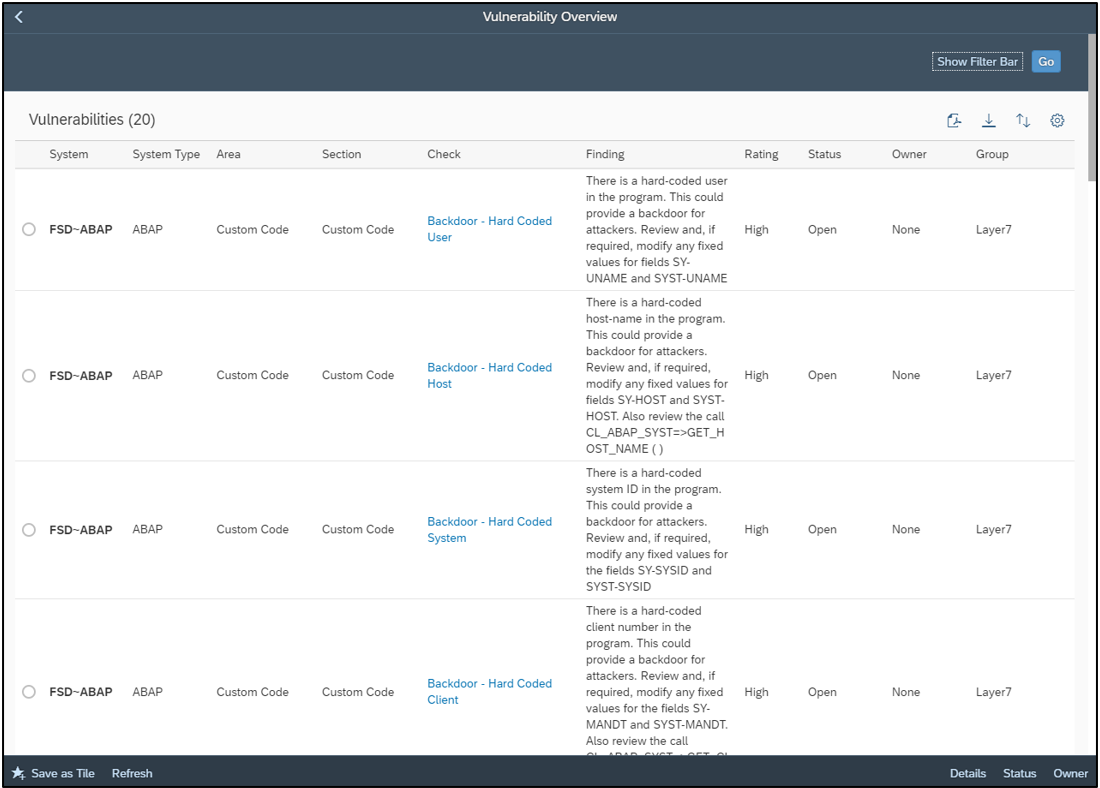
The overall compliance level for the system is displayed the report header. The results for each requirement of the SAP Security Baseline are displayed in the main body of the report.
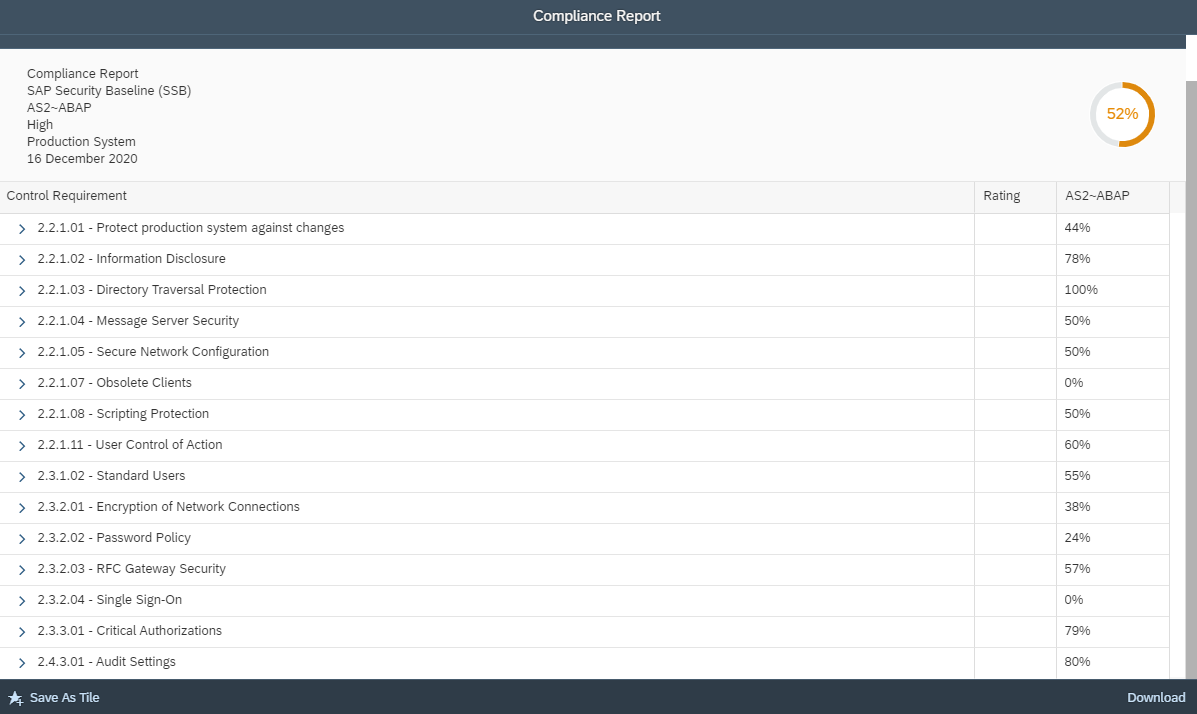
Users can drilldown into each requirement to review the results for specific controls. Control ratings and descriptions are included in the report to support analysis.
Reports can be exported to CSV or PDF. The Report Detail option specifies whether results are exported at the Requirement, Control or Description level.
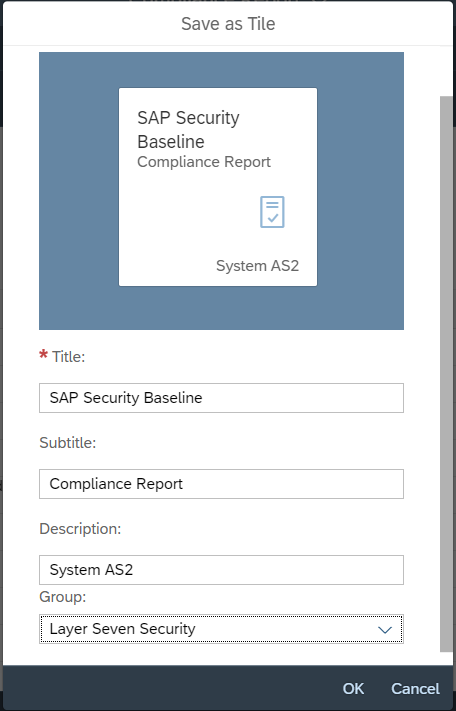
Users can also save shortcuts for prefiltered reports to the Fiori launchpad.