Patch Your SAP Systems with SAP Solution Manager
Regularly patching SAP systems is the single most important action you can take to secure business-critical SAP applications from cyber threats. Despite the concern surrounding zero-day vulnerabilities, every known SAP exploit targets existing vulnerabilities patched by SAP through security notes. In other words, there is no evidence of the exploitation of zero-day vulnerabilities for SAP applications. However, there is a multitude of evidence for the exploitation of known vulnerabilities that have been fully patched by SAP.
This includes well-known SAP vulnerabilities such as ICMAD, RECON and 10KBLAZE. Notes 3123396 and 3123427 patch SAP for ICMAD. Note 2934135 secures SAP against RECON exploits. Protection against 10KBLAZE can be applied through notes 1408081, 821875, and 1421005. Some the notes for 10KBLAZE have been available since 2006. This is 13 years before CISA released an alert for the exploits.
Organizations take an average of three months to implement hot news notes for critical SAP vulnerabilities. Yet threat actors can weaponize SAP vulnerabilities within 72 hours of a patch release. Therefore, it is important to minimize the window of opportunity for attackers by rapidly discovering, analyzing and implementing SAP security notes.
Most software tools for SAP patch management automate the discovery of SAP security notes but do not support notes analysis and implementation. System Recommendations (SysRec) is the only solution that supports the full lifecycle of SAP security notes. SysRec is a standard application in SAP Solution Manager, recommended by SAP for patch management. It is automatically enabled during the installation and setup of Solution Manager.
Discovery
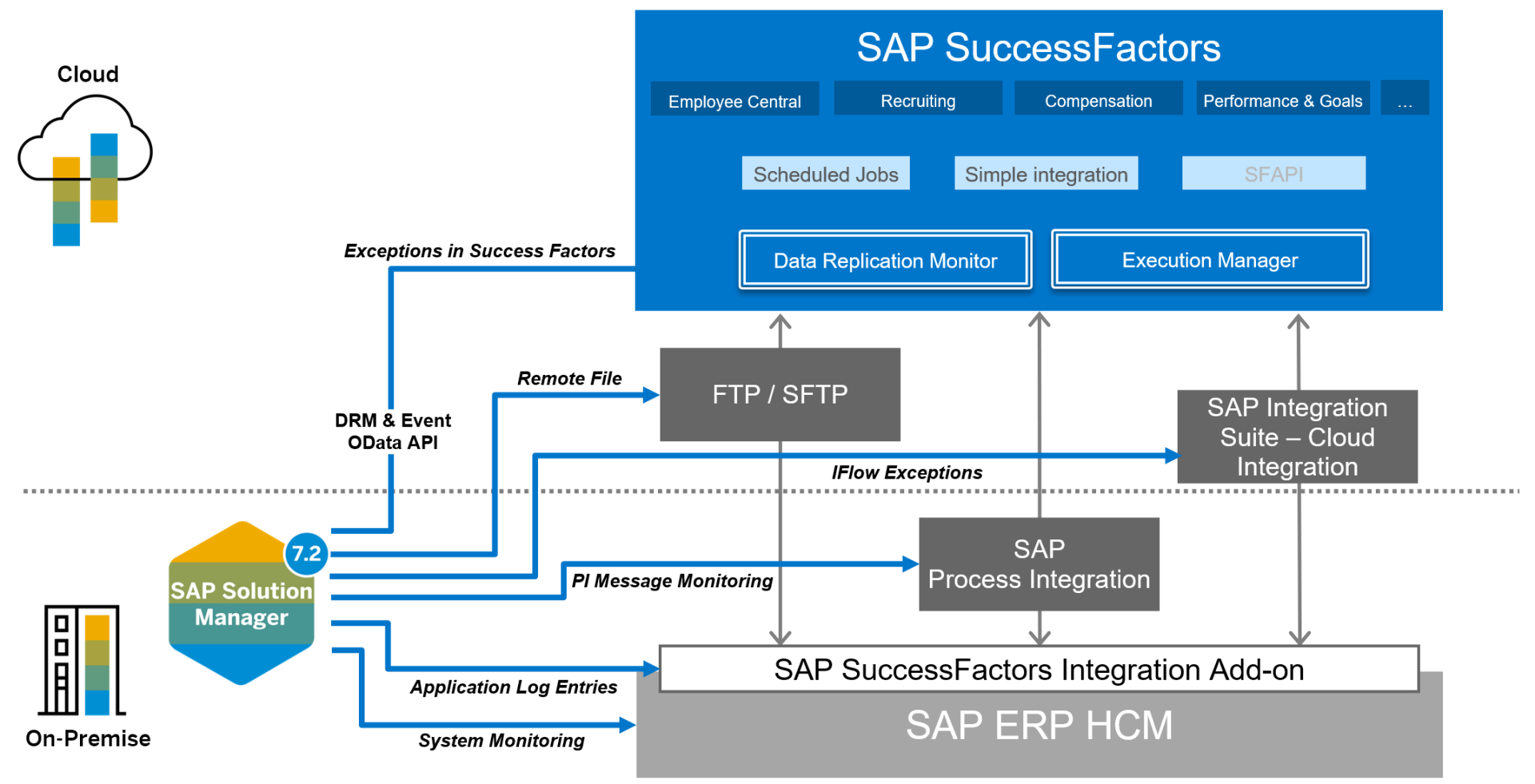
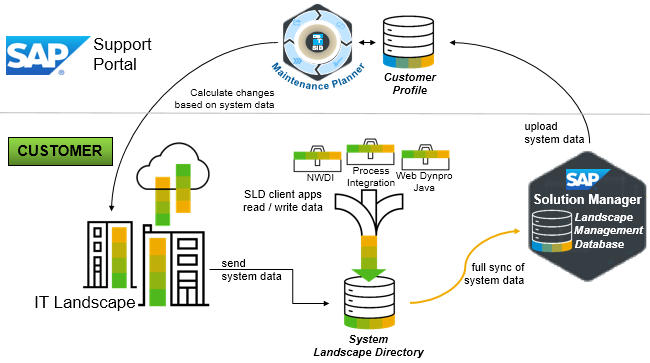
For notes discovery, SysRec performs a daily check for the latest security notes. Therefore, customers are notified immediately as soon as new notes are released by SAP. SysRec connects directly to the SAP Support Portal to identify new notes. It calculates relevant notes based on software information for SAP systems stored in the Landscape Management Database (LMDB). The LMDB is synced to the SAP NetWeaver System Landscape Directory (SLD). The SLD is the source of system information in SAP landscapes including installed software components, databases and operating systems and the versions of components and platforms. Notes calculation takes into account the implementation status of notes. Therefore, fully implemented notes are automatically excluded by SysRec.
It is important to note that the results returned by SysRec are based on installed components, regardless of usage. All installed components must be maintained and patched even if they are not actively used since they are part of the attack surface.
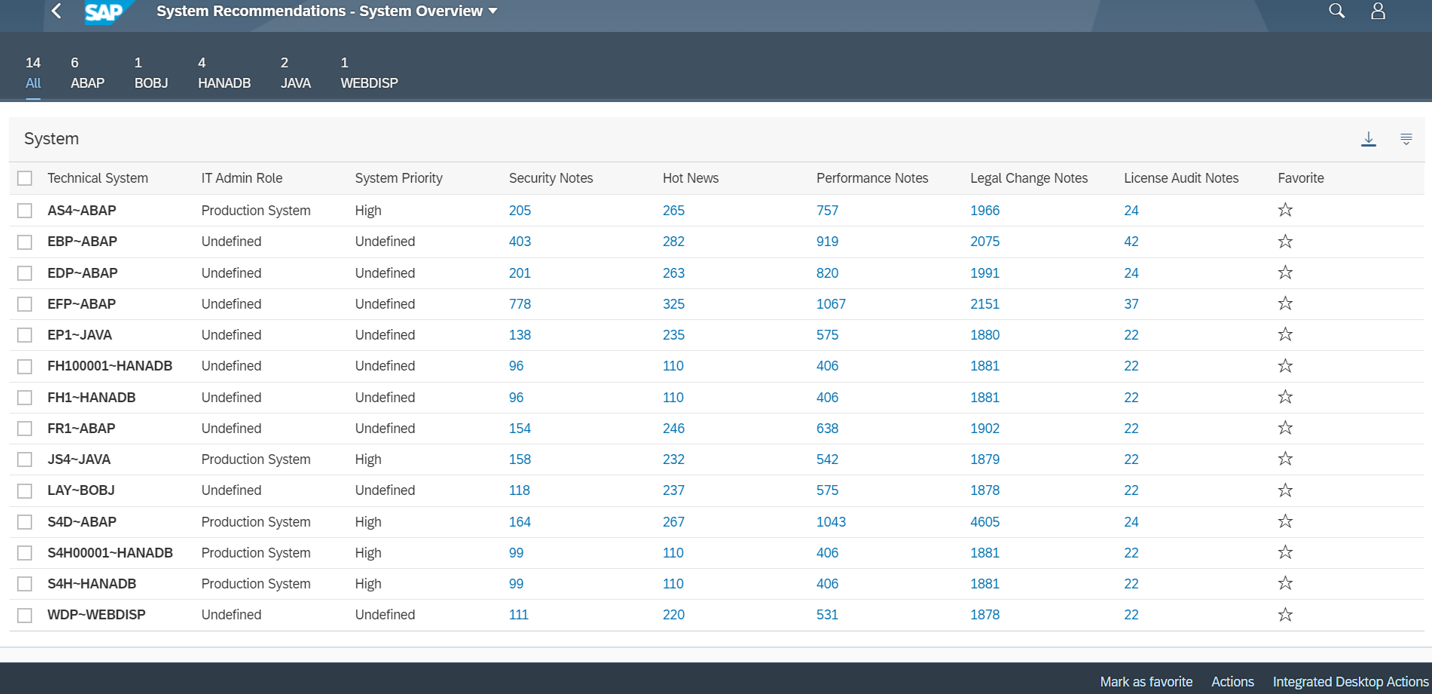
System Recommendations is widely used by SAP administrators to manage not only SAP security notes but also correction, legal, performance and other notes. SAP security teams that rely on third party solutions for notes discovery often clash with SAP administrators since security notes returned by their tools do not align with the results of SysRec. SAP administrators are inclined to trust the results of SAP applications such as SysRec over third party solutions. This can lead to disputes and delays within organizations as SAP administration and security teams fail to align on the notes that should be implemented. The risk is avoided when both teams use System Recommendations and are therefore aligned on the required security notes.
Analysis
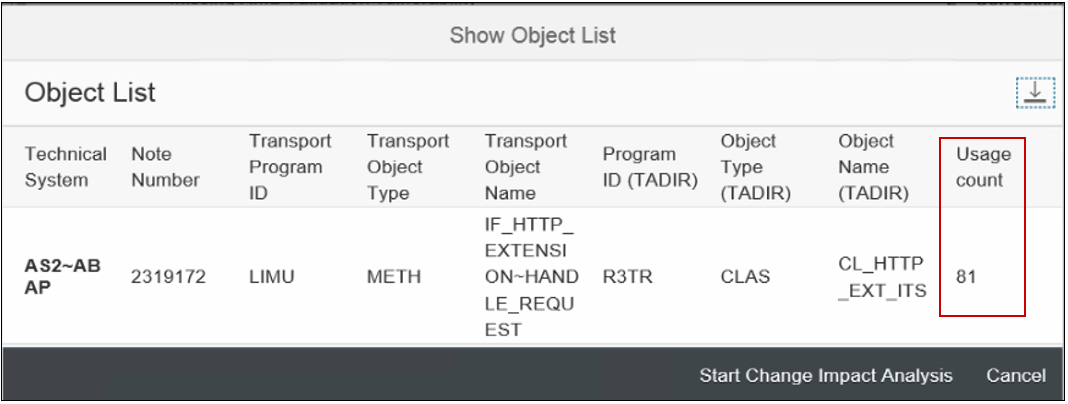
SysRec supports detailed notes analysis through integration with Usage and Procedure Logging (UPL) and the ABAP Call Monitor (SCMON). UPL and SCMON support change impact analysis by revealing function modules, methods, programs and other objects impacted by security notes before they are applied. It includes usage statistics for impacted objects. This information enables SAP administrators to determine the scope and extent of testing for security notes. Notes impacting many objects with high usage counts may require detailed integration or regression testing. Conversely, notes impacting few objects with low usage counts indicates that customers may be able to employ less complex and more rapid test approaches such as smoke tests. Change impact analysis in SysRec provides the insights required by SAP customers to pinpoint the effect of security notes in SAP systems. This addresses the root cause of long patch cycles that increase the period of vulnerability for SAP systems.
Implementation
System Recommendations enables users to download corrections from the SAP Support Portal directly to the target SAP system. This is performed using the option for Integrated Desktop Actions. The user is prompted to select the target system before the download and can therefore select non-productive SIDs when analyzing notes for productive SIDs. SysRec automatically calls SNOTE in the target system after the download to apply the note.
Integrated Desktop Actions also enables users to create a Request for Change (RfC) in Change and Request Management (ChaRM) for security notes. ChaRM is commonly used by SAP customers to manage the lifecycle of SAP changes and includes workflows to control requests including phases for requirements, approval, testing, and promotion to production.
If you would like to learn more about patching SAP systems using System Recommendations, request a pre-release of Layer Seven Security’s new whitepaper for SAP Security Patching, scheduled for Q3 2022.