Maintaining System Inventories with SAP Solution Manager
Maintaining an accurate and complete inventory of SAP systems is an important requirement for cybersecurity. It enables organizations to assess and prioritize risk management, ensure systems are not accidentally overlooked and exposed to threats, plan and track maintenance activities such as upgrades to apply security patches, and recover rapidly from security incidents including data breaches and successful ransomware attacks. For this reason, compliance frameworks such as CIS, NIST and PCI-DSS include requirements for asset management. The requirement is also the subject of the new bill Strengthening Agency Management and Oversight of Software Assets Act approved by the U.S Senate Homeland Security and Governmental Affairs Committee in September.
In many organizations, SAP asset inventories are maintained in spreadsheets or asset management tools that require manual updating. This can lead to inaccuracies if these approaches fail to keep pace with changes in complex and evolving SAP landscapes. Landscape Management in SAP Solution Manager provides an automated solution for managing system inventories by discovering and mapping SAP assets and automatically updating system information. Landscape Management is included in the standard usage rights for Solution Manager.
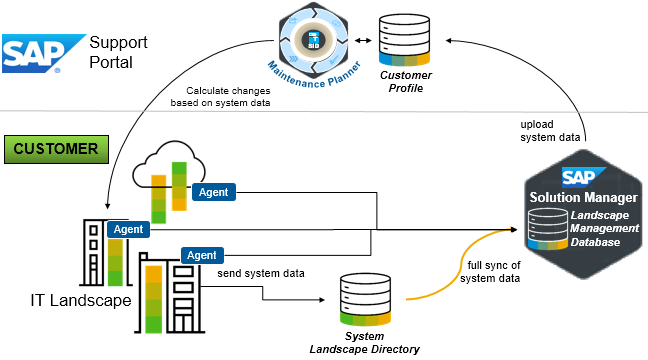
System information is sourced by Landscape Management from the System Landscape Directory (SLD). The SLD is the central repository of system information required for SAP lifecycle management. SAP landscapes may have multiple SLDs for backup or to support different environments, but the supplier for Landscape Management is the central SLD. The SLD includes a software catalog for each system known as CR Content. It also includes a Common Information Model (CIM) for sharing hardware and software information. CR and CIM data is automatically synched from the SLD with Landscape Management via SAP agents. The data can also be automatically or manually imported into Solution Manager in landscapes that do not have an SLD. The data is then synched from Landscape Management with the Maintenance Planner in the SAP Support Portal. This is one of the primary reasons why SAP Solution Manager is required in SAP landscapes even if customers are not actively using any SolMan scenarios.
Landscape Management is accessed from the SAP Solution Manager Administration workgroup in the Fiori Launchpad.
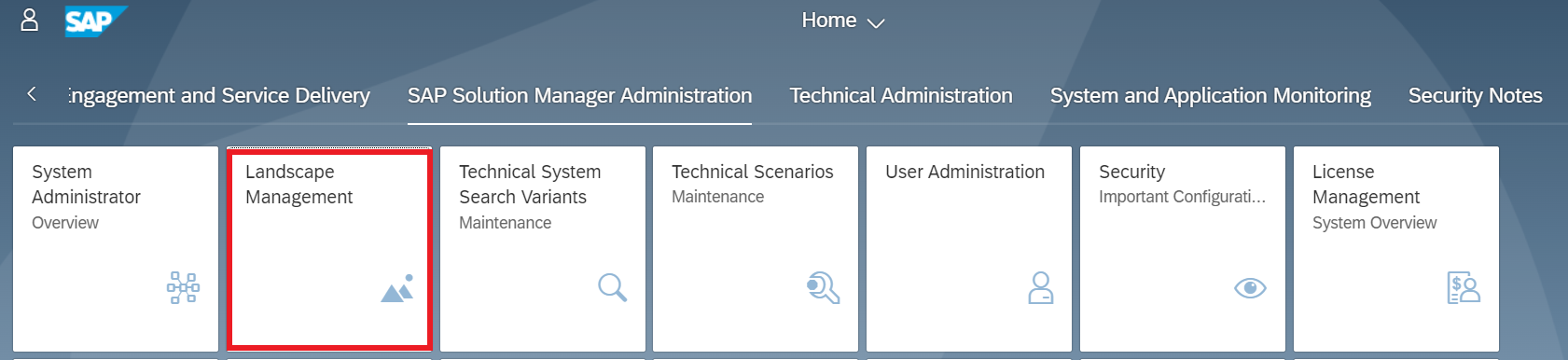
System information is categorized by application server, database, host and component areas. For technical systems, you can select a system from the selection screen and click on Display to display the full system information.
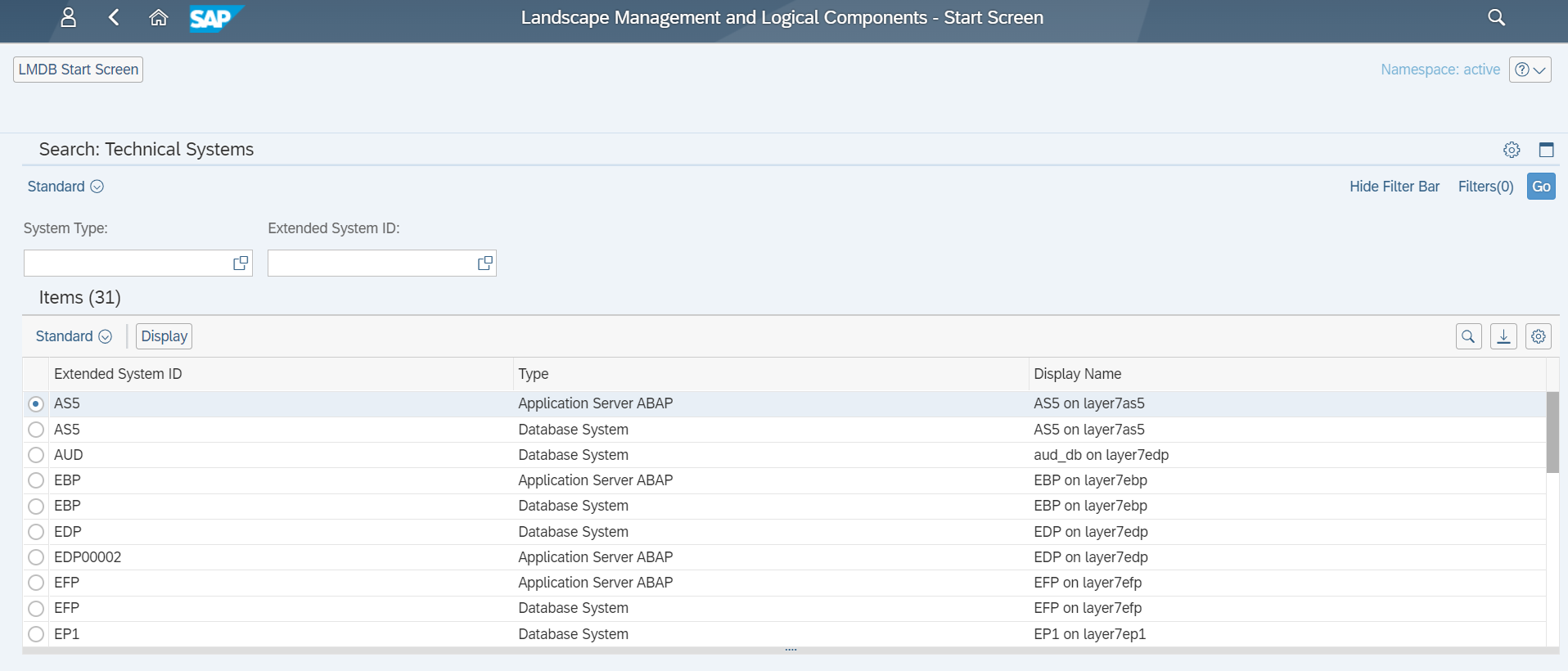
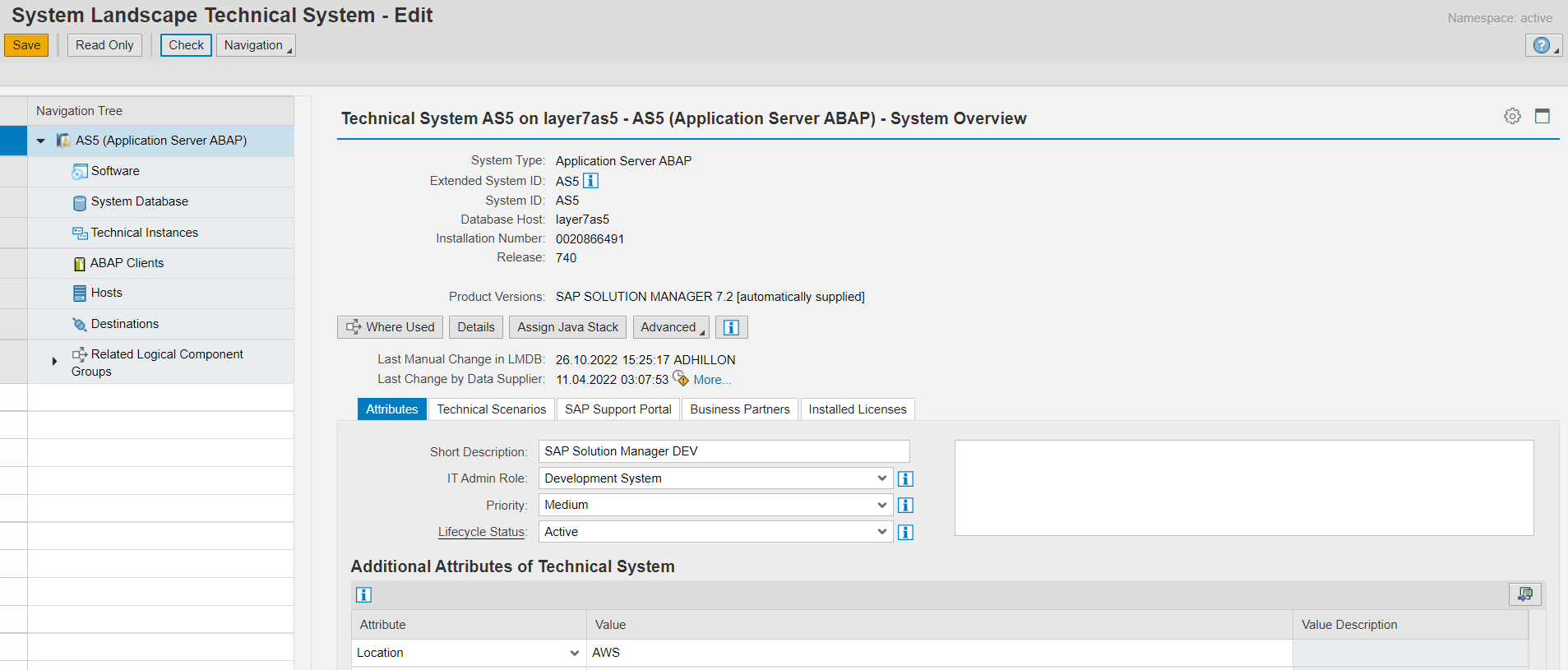
The initial screen summarizes the key attributes for the system such as the SID, database, installation number, release information and SAP products installed in the system. This section also includes the environment, location and lifecycle status. The priority of the system can be used to classify systems based on their business importance using a low to very high rating scale.
The tabs for Technical Scenarios, SAP Support Portal, Business Partners, and Installed Licenses detail the active SolMan scenarios for the system, the system number, key personnel including system owners, business contacts, architects, and technical support with email addresses and telephone numbers, and license information.
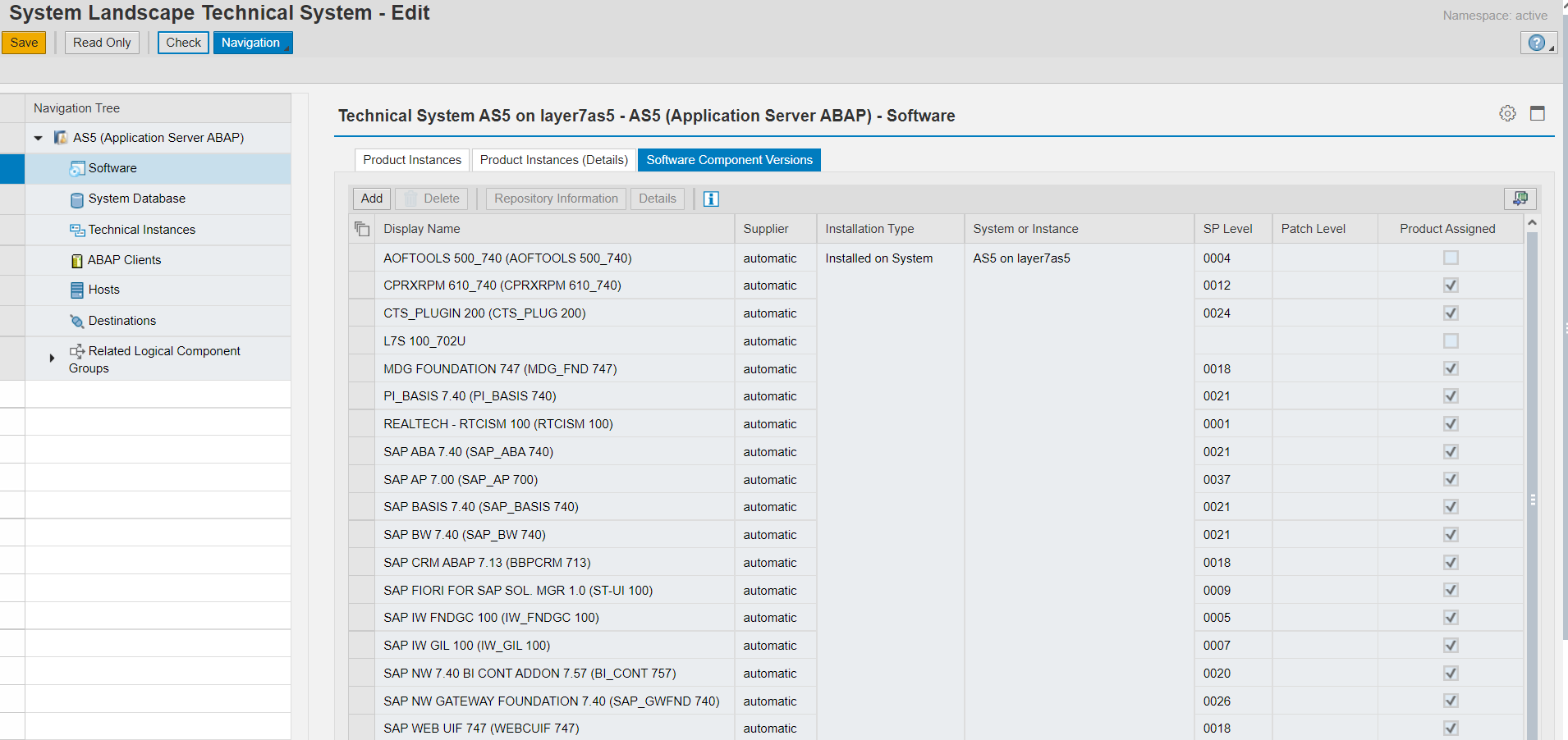
The Software section lists the installed software components including version and support pack level. This information is used by SAP Solution Manager during the calculation of relevant notes including security notes.
The Database, Instances and Clients section include information such as the database type, release and host name, instance names, numbers and directories, and active clients and roles.
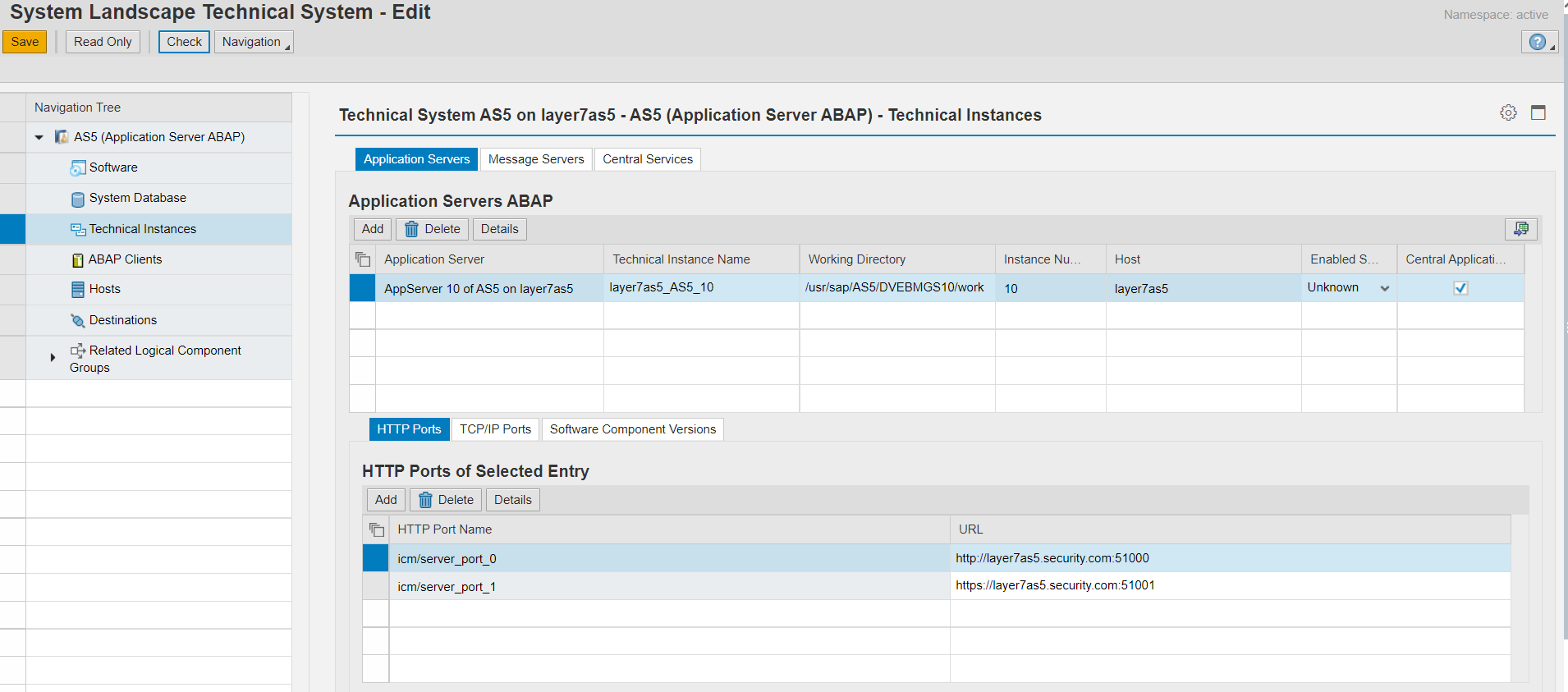
The Hosts section will include host-level information such as the host name, FQDN, IP address, OS type and version, CPU, and details of whether the host is physical, logical or virtual.
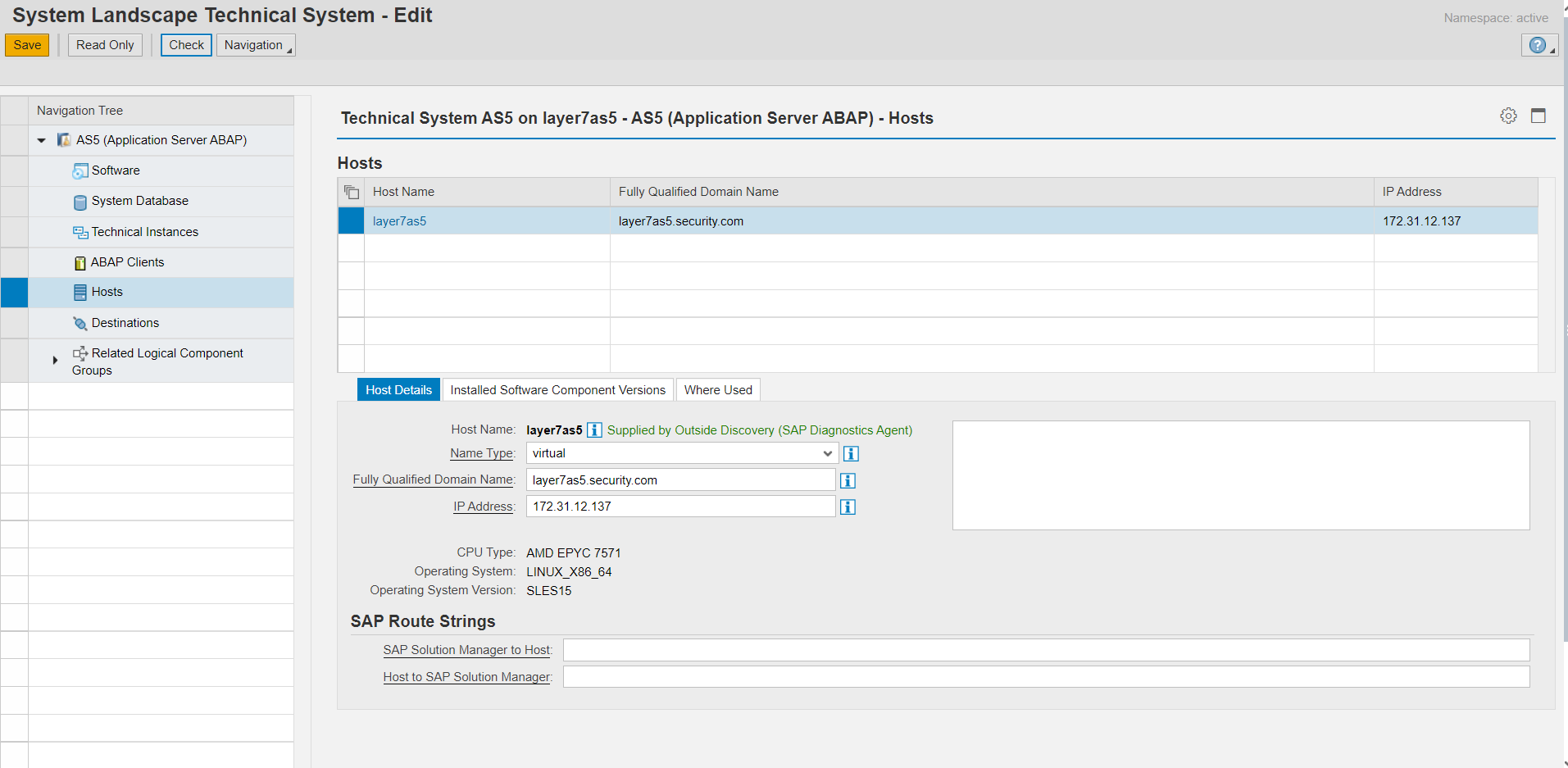
The Destinations section lists the active RFC destinations in the system by client.
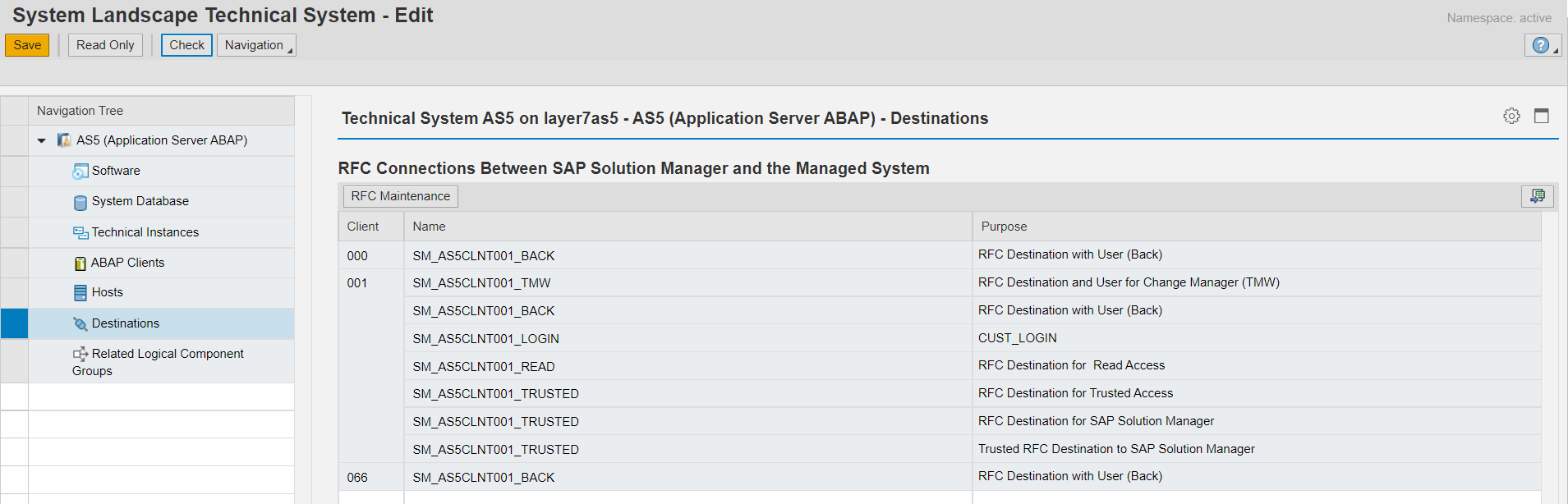
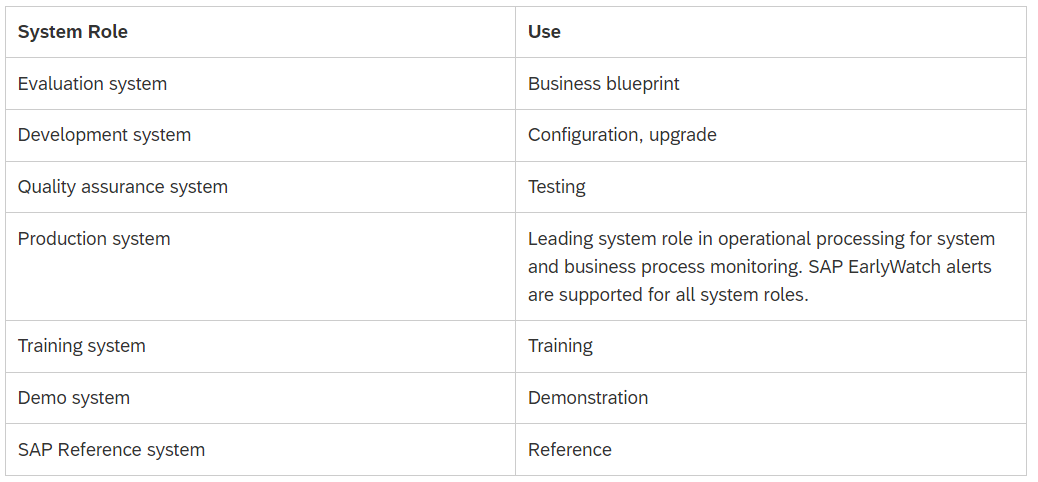
Finally, the Component Groups section details the logical component groups for the system. This is often used to group systems based on their role. The system roles below are predefined by SAP. However, users can create and maintain custom component groups to cluster systems by business group, function, location, or other areas.