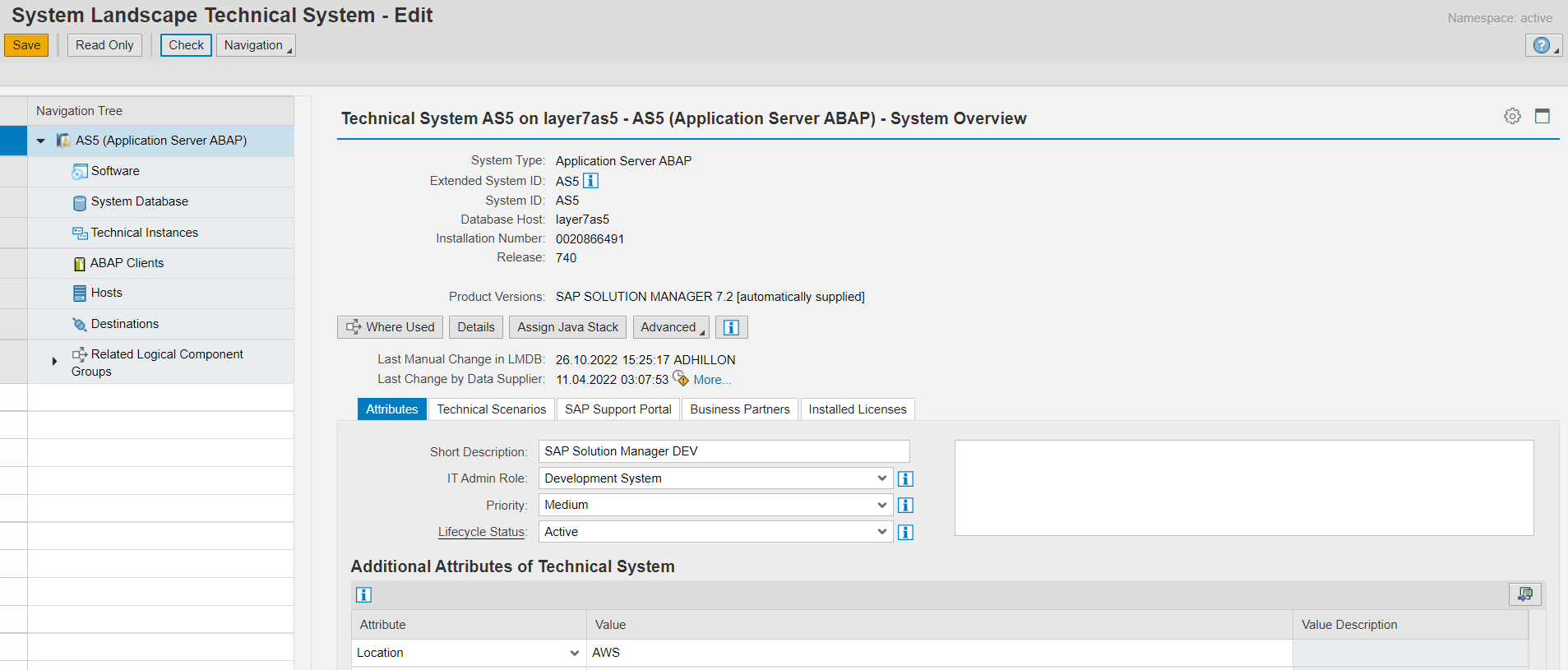
The Most Critical SAP Security Notes of 2024
Security notes are released by SAP on the second Tuesday of every month to address vulnerabilities in SAP solutions. The vulnerabilities are discovered by external security researchers and reported as part of SAP’s disclosure program. They are also discovered directly by SAP through its’s ongoing research and testing. Security notes are scored by SAP using version 3.0 of the Common Vulnerability Scoring System (CVSS). CVSS generates a score from 0 to 10 based on the severity of the vulnerability. SAP also assigns a priority level for each note. Critical notes are categorized as hot news.
There were over 150 security notes released in 2024 to address vulnerabilities in SAP solutions. The average CVSS score was 5.9. Approximately 1 in 4 of the notes were categorized as hot news or high priority. This article reviews the most important security notes of 2024, based on CVSS score. Hot news notes should be prioritized for implementation. Often, workarounds included in some notes can be applied to mitigate risks if the corrections cannot be applied immediately.
Note 3479478 [CVE-2024-41730] is the one of the highest rated notes of 2024 with a CVSS score of 9.8. The note patches a missing authentication check in SAP BusinessObjects Business Intelligence Platform (BOBJ). The vulnerability can be exploited by attackers to compromise logon tickets using a REST endpoint if Single Sign-On is enabled. The property Trusted_Auth_Shared_Secret can be set to Disabled in the effected files to mitigate the vulnerability if BOBJ cannot be upgraded to the required patch level immediately.
Note 3455438 also has a CVSS score of 9.8. The note addresses code injection and remote code execution vulnerabilities in open-source components bundled in SAP CX Commerce. This includes API tools in Swagger UI and database drivers in Apache Calcite Avatica. The solutions referenced in the note remove the vulnerable components in Swagger UI and upgrade Apache Calcite Avatica to the recommended version. There are no workarounds.
Note 3448171 patches CVE-2024-33006 for a critical file upload vulnerability in SAP NetWeaver Application Server ABAP (AS ABAP). The CVE is rated 9.6. The vulnerability can be exploited to bypass malware scanning and completely compromise SAP systems. The correction and workaround detailed in the note apply signature checks for the FILESYSTEM and SOMU_DB content repositories. The vulnerability impacts most version of the SAP_BASIS component in AS ABAP.
Note 3425274 [CVE-2019-10744] patches a code injection vulnerability in SAP Build Apps. The vulnerability arises from specific versions of the Lodash open-source JavaScript library used for programming tasks included in SAP Build Apps. Applications should be rebuilt with version 4.9.145 or later to prevent the vulnerability.
SAP Build Apps is also vulnerable to CVE-2024-29415, a severe Server-Side Request Forgery (SSRF) vulnerability detailed in note 3477196.
Note 3536965 [CVE-2024-47578] addresses SSRF and information disclosure vulnerabilities in Adobe Document Services of SAP NetWeaver AS for JAVA (AS Java). Updating the ADSSAP software component to the recommended patch level will remove the vulnerabilities in the relevant web applications and services in AS Java.
Note 3433192 [CVE-2024-22127] deals with a code injection vulnerability in the Administrator Log Viewer plug-in of AS Java. The vulnerability requires administrative privileges for successful exploitation. Therefore, restricting the use of the Administrators role can mitigate the vulnerability.
Note 3420923 [CVE-2024-22131] patches a vulnerable RFC service in AS ABAP to prevent a critical code injection vulnerability. The workaround in the note recommends restricting access to function modules for CA-SUR using authorization object S_RFC.
Other important notes include 3413475 for multiple CVEs in SAP Edge Integration Cell and 3412456 [CVE-2023-49583] which addresses an escalation of privileges vulnerability in node.js applications created using SAP Business Application Studio, SAP Web IDE Full-Stack or SAP Web IDE for SAP HANA.