Digital Operational Resilience Act (DORA) Compliance for SAP Solutions

The Digital Operational Resilience Act (DORA) is a regulation that mandates standards for cybersecurity and operational resilience in the financial sector within the European Union (EU). It provides standards for governing risks in Information and Communications Technology (ICT) to ensure banks, insurers, investment firms, and other financial institutions are able to deliver critical services by effectively resisting, responding and recovering from ICT disruptions. The act took effect on January 17, 2025, with oversight from the European Supervisory Authorities EBA, ESMA, and EIOPA, to define and enforce technical standards for the regulation.
The Five Pillars of DORA
DORA’s core objective is to support the integrity and continuity of financial services against ICT risks including cyberattacks. The regulation includes the following five pillars:
- Risk Management: a comprehensive governance and control framework covering ICT asset inventory, protection, detection, response, recovery, backup, logging and monitoring, change management, and resilience-by-design.
- Incident Management and Reporting: consistent handling of ICT incidents and mandatory reporting of major incidents.
- Operational Resilience Testing: vulnerability assessments and penetration testing focused on critical functions.
- Third-Party Risk Management: oversight for ICT vendors and providers including outsourced services.
- Information Sharing: mechanisms to share cyber threat information and intelligence to strengthen sector-wide resilience.
The Impact of DORA for SAP Solutions
For many financial services organizations, SAP solutions support critical functions such as procurement and supplier operations, human resource management, and finance and controlling. Therefore, they are often part of the ICT fabric that must be governed, monitored, tested, and recoverable for DORA compliance. Under DORA, SAP solutions require tight integration with:
- ICT Risk Governance, including the definition of key risk indicators and controls testing.
- SOC Operations, including detection, triage, and handling of incidents.
- Service Management, including approvals, evidence, and testing for changes.
- Supplier Management, including managing hosting providers, system integrators, and external integrations such as APIs.
DORA effectively obliges organizations to manage SAP solutions as regulated platforms, requiring baseline controls, continuous monitoring, regular patching, frequent testing, and periodic reporting.
DORA Compliance with the Cybersecurity Extension for SAP
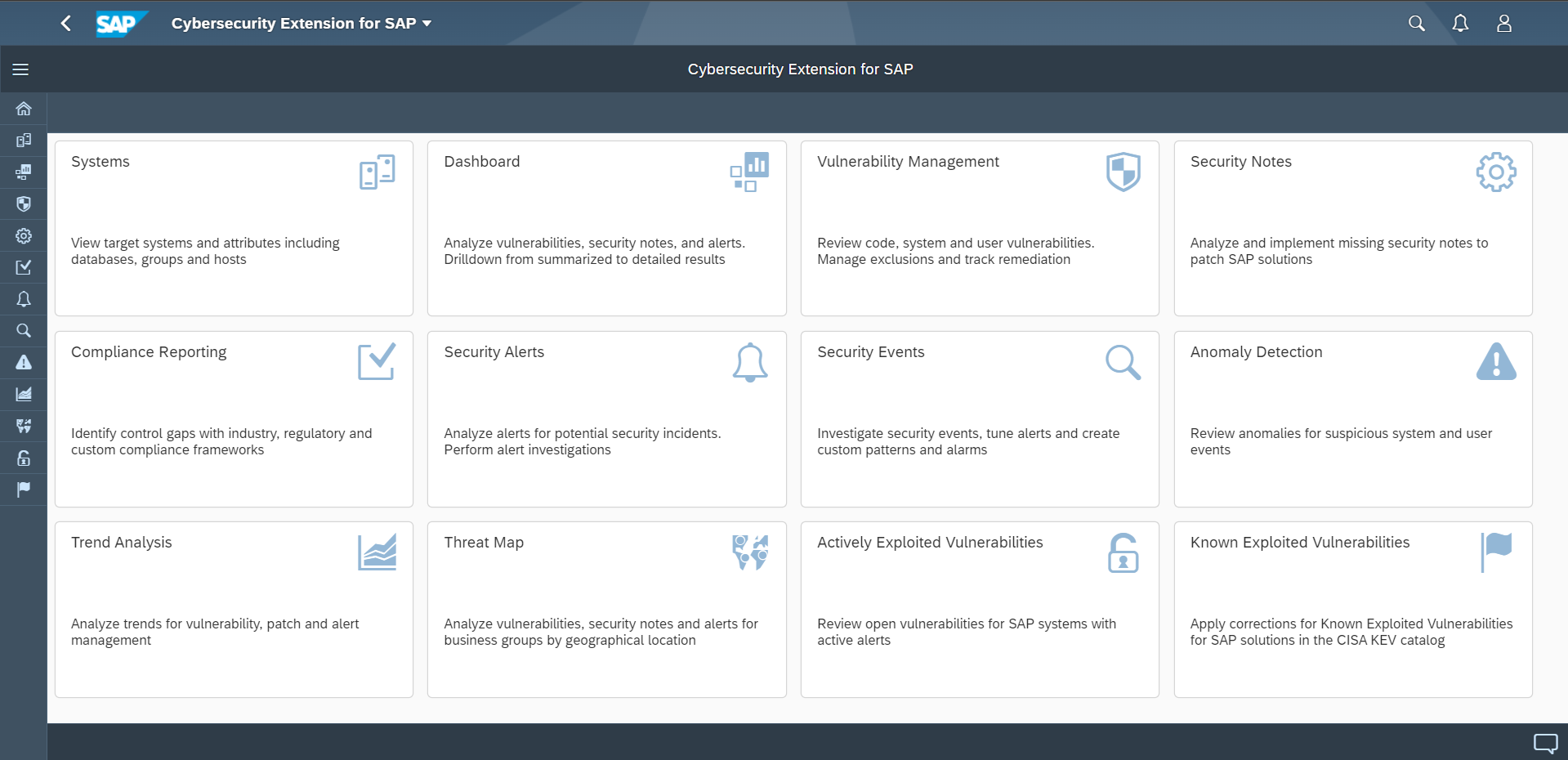
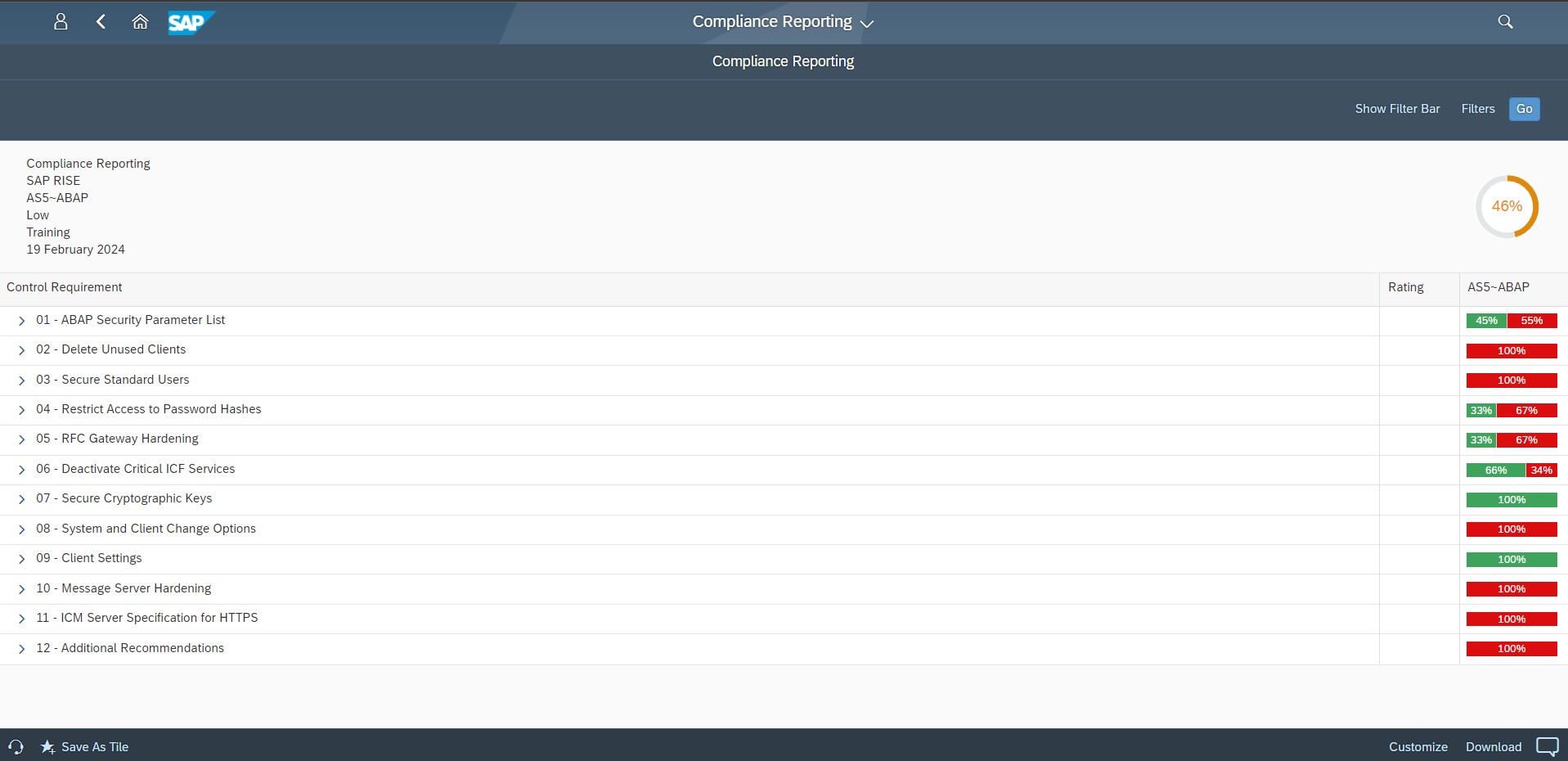
The Cybersecurity Extension for SAP (CES) enables organizations to comply with DORA by identifying and managing ICT risks in SAP solutions, detecting and responding to security incidents, securing third party integrations, and verifying and reporting compliance with SAP security benchmarks. The solution supports compliance with each of the five pillars in DORA for SAP systems.
Pillar 1 – Risk Management
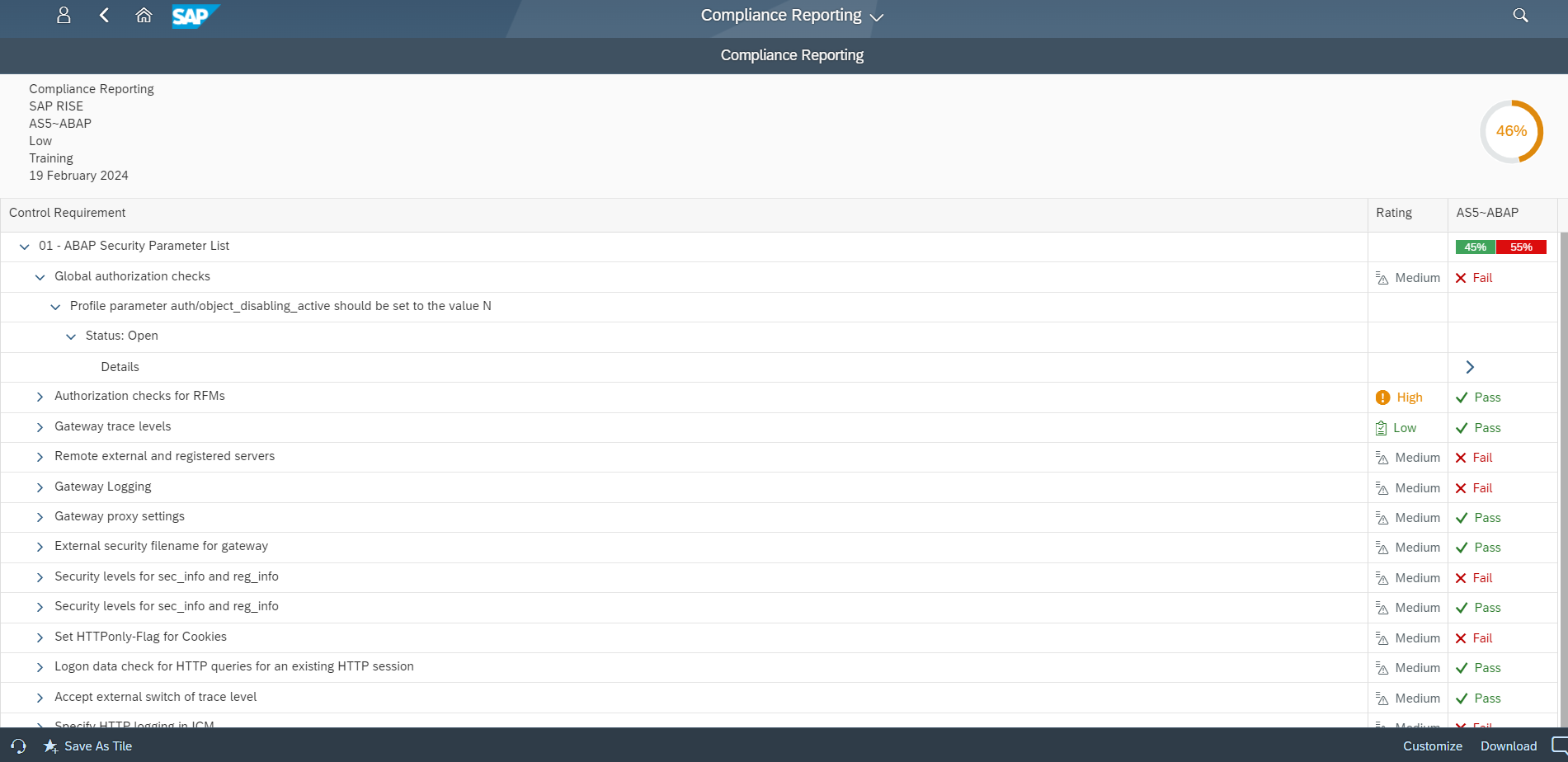
- Continuous SAP security monitoring including the detection of security-related changes in SAP solutions.
- SAP-specific vulnerability management including the detection of 5000+ security weaknesses in SAP.
- Custom code security including the detection of 300+ vulnerabilities in custom ABAP programs and SAP UI5 / Fiori applications.
- SAP patch management including the detection of relevant security notes and support packages.
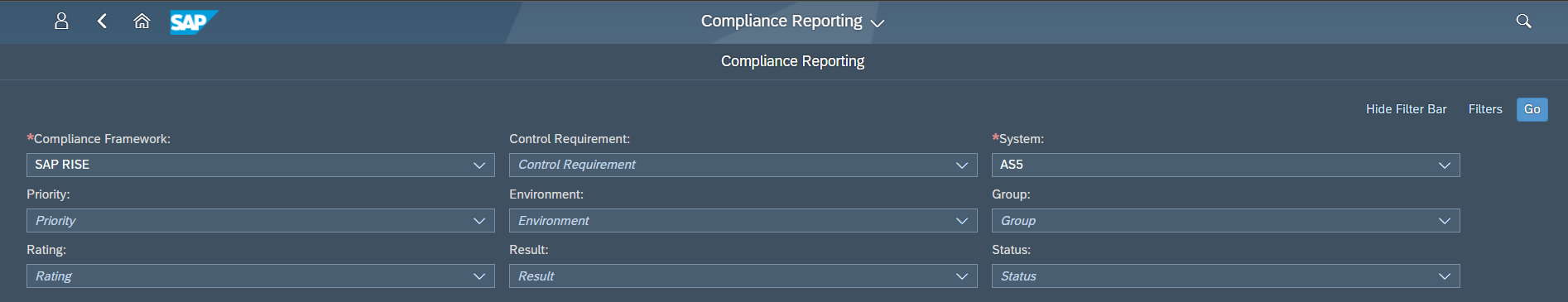
- Alignment to SAP-specific baselines and cloud hardening benchmarks including the SAP Security Baseline, security guidance for S/4HANA, and SAP RISE/ECS mandatory security requirements.
Pillar 2 – Incident Management and Reporting
- Threat detection: Detection and alerting for 1500+ Indicators of Compromise (IOC) in SAP solutions including application, database and host-level logs.
- Risk-based prioritization of SAP alerts based on operational impact for rapid classification.
- Standard operating procedures and workflows for investigating, tracking and reporting on incident investigations.
Pillar 3 – Operational Resilience Testing
- Compliance monitoring and baseline checks to validate SAP hardening.
- Threat detection exercises for SAP attack paths including privilege escalation, interface abuse, suspicious admin changes, and calls to critical SAP function modules, reports, services, and transactions.
- Daily vulnerability scanning to support risk identification and mitigation.
Pillar 4 – Third-Party Risk Management
- Visibility into external interfaces in SAP solutions including cloud connections.
- Evidence for SAP RISE / managed-service security requirements.
- Accountability for system integrators against SAP security standards.
Pillar 5 – Information Sharing
- SAP-specific security intelligence including threat detection patterns, CVEs, and zero-day vulnerabilities.
- Standardized reporting for information sharing with cross-functional teams and sector forums.
The Cybersecurity Extension for SAP supports digital resilience and DORA compliance by ensuring security for SAP solutions is measurable, monitored, and audit-ready. It provides continuous evidence evidence of SAP hardening, while strengthening operational resilience through incident detection, streamlined response, and reduced exposure to cyber risks.