How to Discover Actively Exploited Vulnerabilities in Your SAP Systems
SAP systems have a wide attack surface. Threat actors can enumerate and exploit multiple known vulnerabilities in SAP components and programs to compromise SAP solutions. Automated vulnerability scans often reveal hundreds of weaknesses in SAP systems. Remediating each vulnerability requires extensive planning and testing for each impacted system. Most organizations do not have the resources to remediate every vulnerability to close all possible attack vectors in their SAP solutions. A prioritized approach focused on remediating high-risk vulnerabilities can be used to concentrate efforts. Organizations can also focus on vulnerabilities that are being actively exploited in their SAP systems. This involves correlating user and system activity captured in SAP logs with vulnerabilities that have been identified in systems.
This correlation is performed automatically by the Cybersecurity Extension for SAP (CES). CES is an addon for SAP Solution Manager and SAP Focused Run. CES will also be available as an extension for SAP Cloud ALM in 2024.
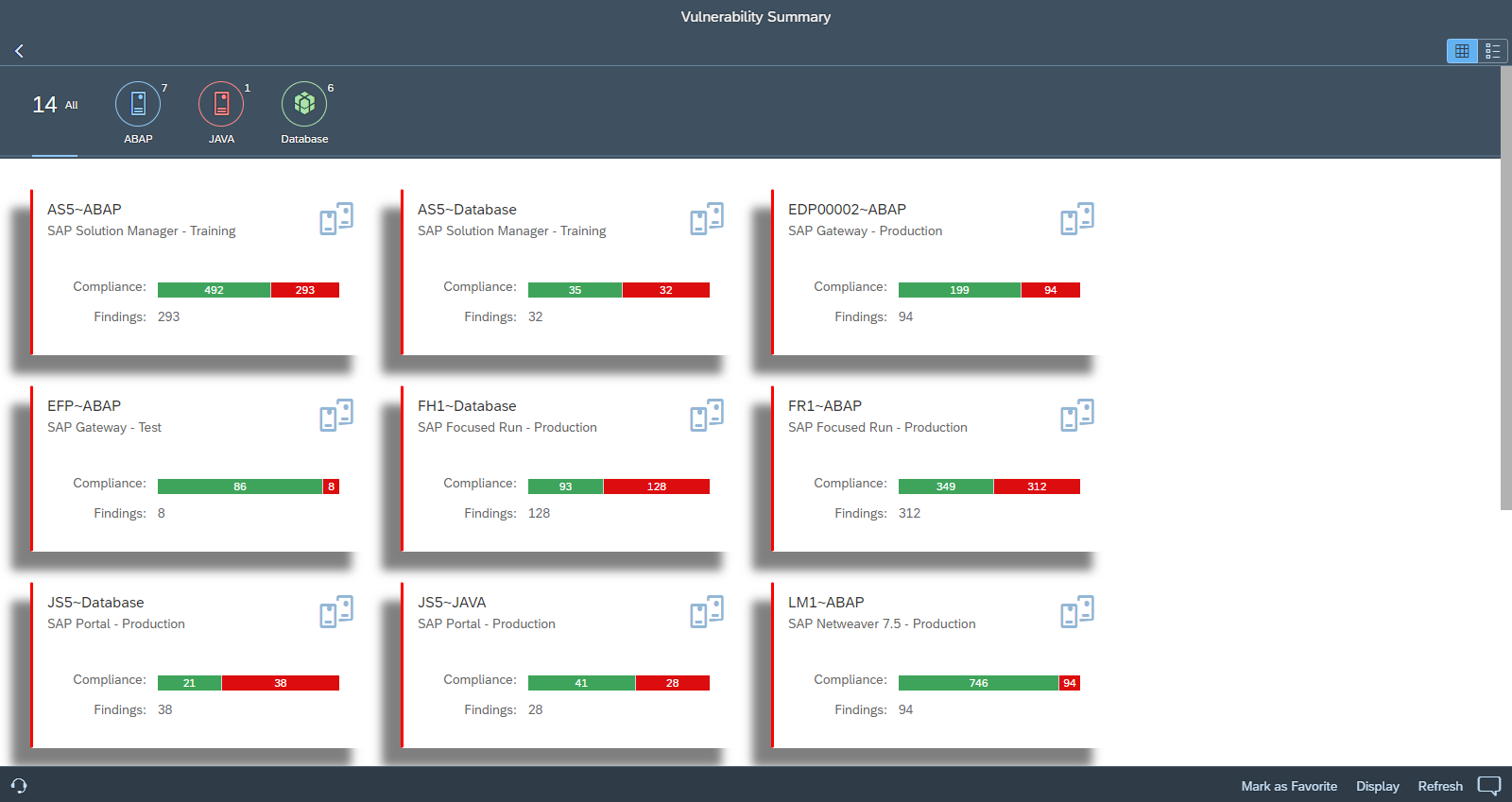
CES performs daily automated scans to detect over 4000 vulnerabilities in SAP applications and supporting databases and operating systems. The vulnerabilities are analyzed and managed using the Vulnerability Management application in CES. The application displays a summary of vulnerability scan results when accessed. Users can switch between the system card view and the dashboard view in the summary.
System Card View:
Dashboard View:
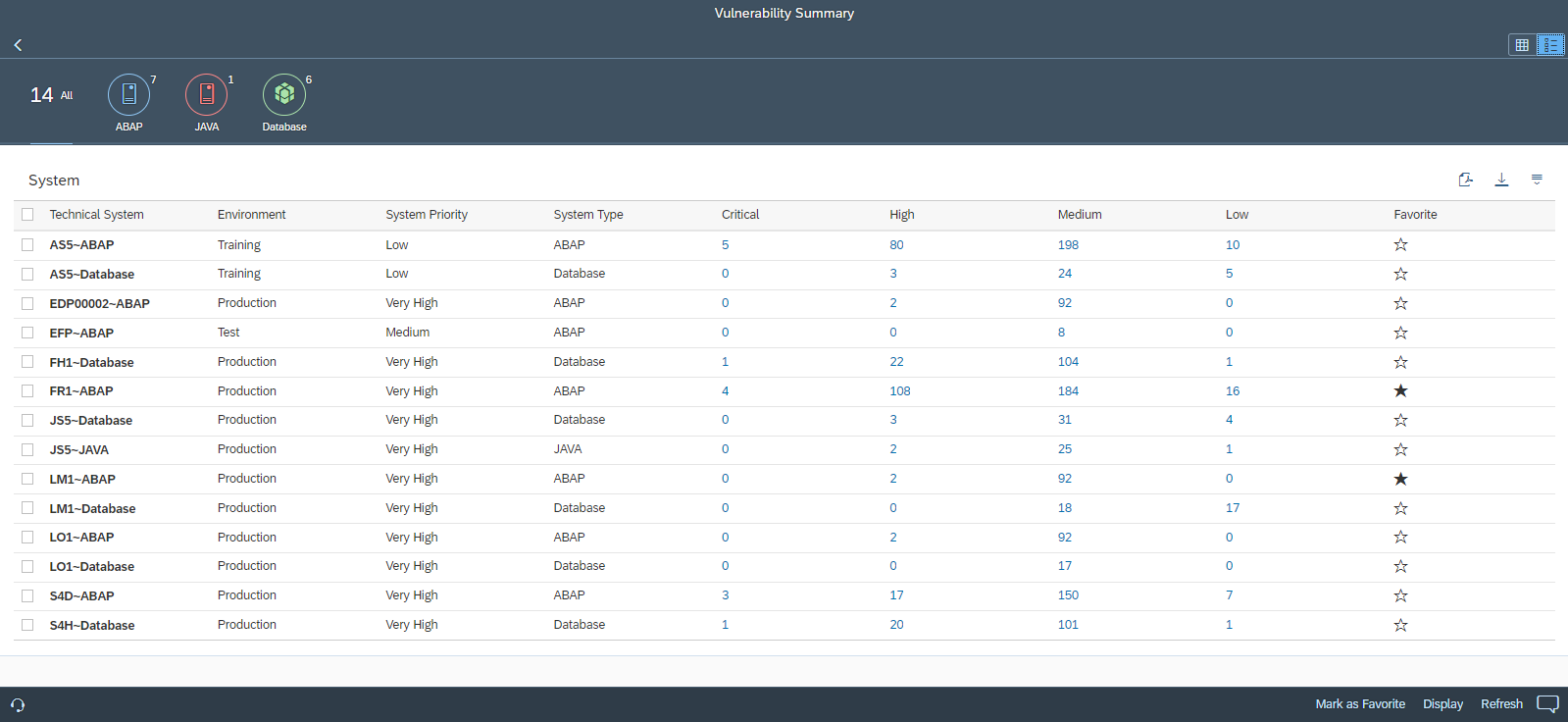
Users can select one or more system from the Summary to drilldown to the findings.
The Overview section displays the open vulnerabilities for the selected systems. Results can be filtered and sorted by area, environment, rating and other variables.
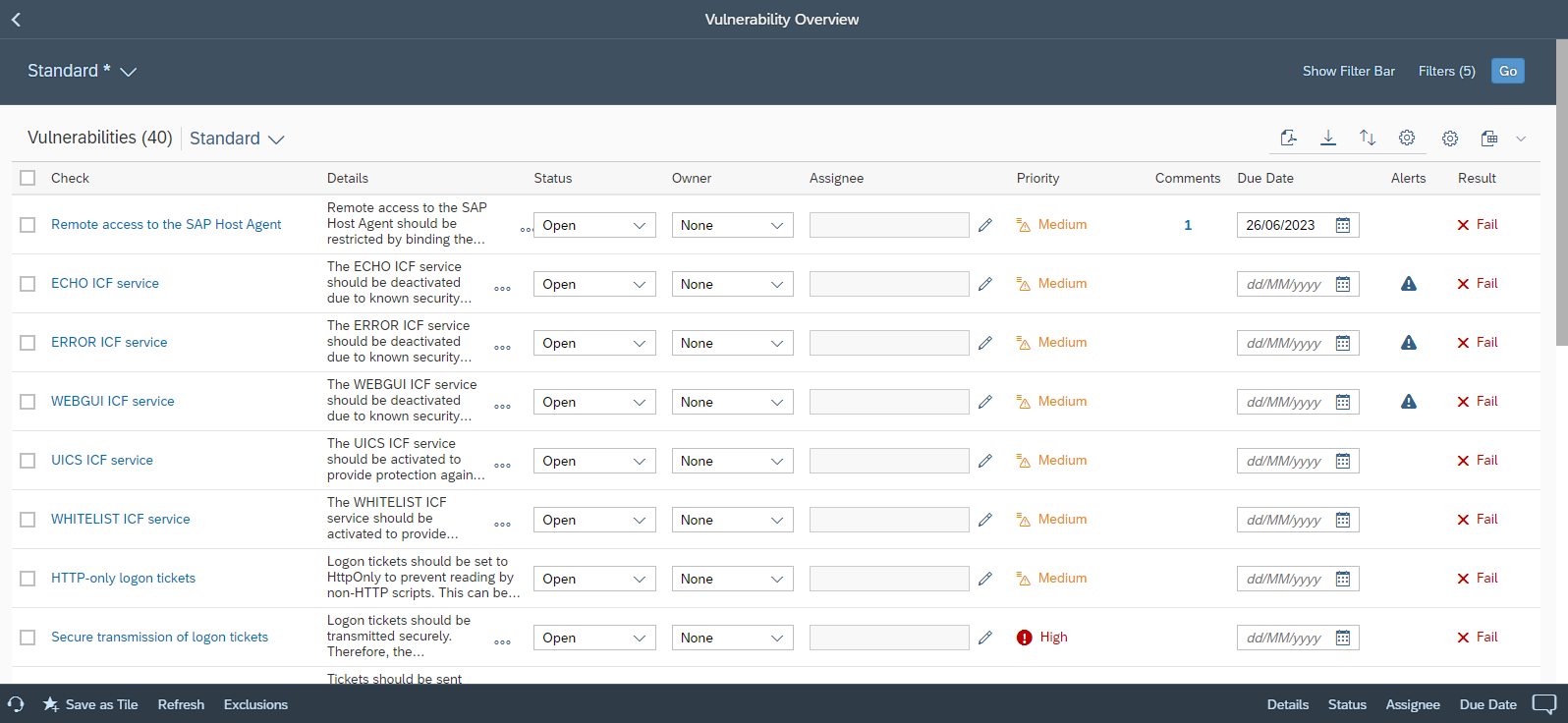
Responsibility for remediating vulnerabilities can be assigned to specific owners and assignees directly in the Overview. Target dates can also be maintained for the removal of the root causes of issues. Remediation plans can be maintained in the Action Plan tab in the detailed display for each vulnerability.
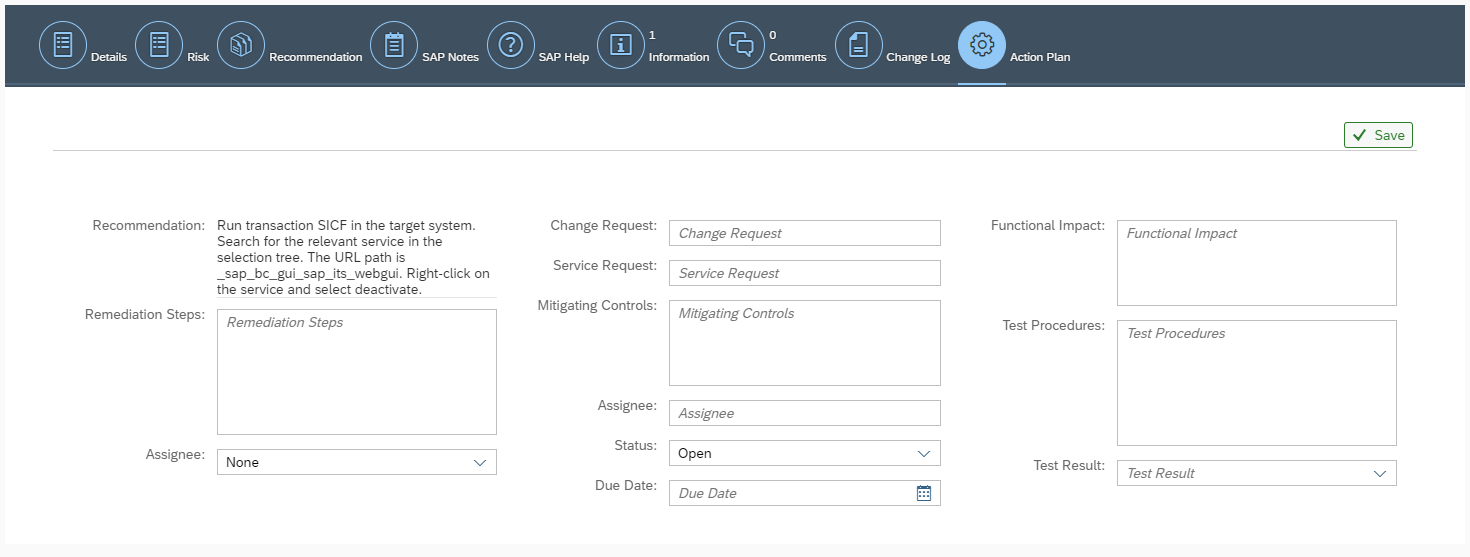
Actively exploited vulnerabilities are identified and flagged based on automated and continuous correlation with event logs and alerts in CES. Results can be filtered to focus on vulnerabilities that have active alerts. Users can also create and publish alarms to their Launchpads for actively exploited vulnerabilities using the Save as Tile option.
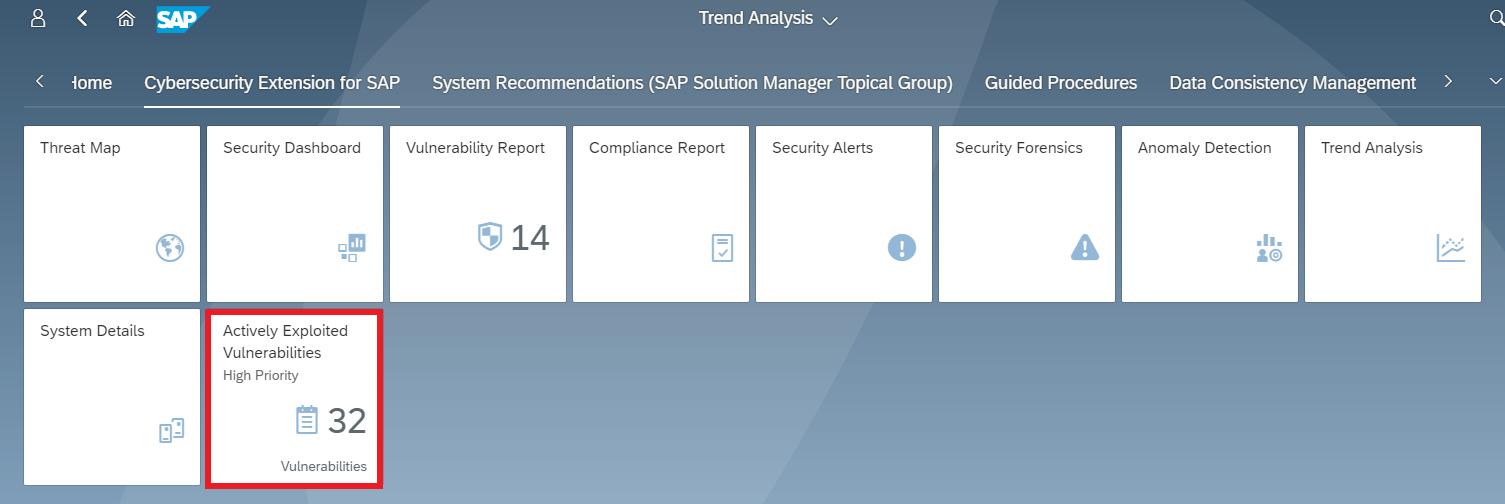
In the example below, there is an open alert for the successful call of a vulnerable ICF service in a system. Although the vulnerability is rated as medium-risk, the active exploitation of the vulnerability in the system indicates that the finding should be prioritized for remediation.
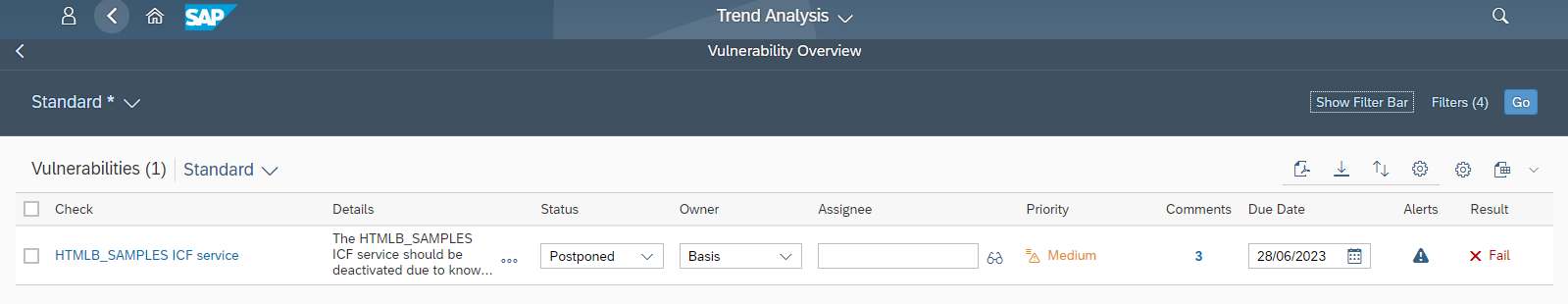
The alert for the vulnerability can be analyzed by clicking on the alert icon for the vulnerability. This directs to the details of the alert in the Security Alerts application in CES.
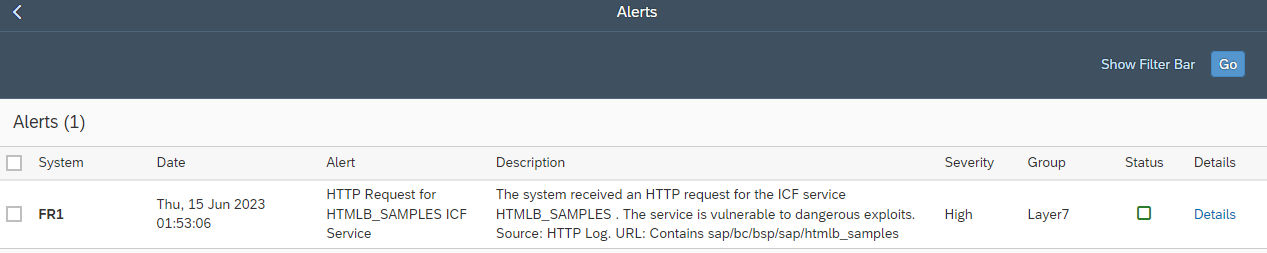
The automated discovery and reporting of actively exploited vulnerabilities is supported in version 5.0 and higher of the Cybersecurity Extension for SAP.

