Monitor Table Access with SAP Solution Manager
There has never been a greater need to monitor access to sensitive data in SAP systems. SAP data is increasingly accessible from access points outside network perimeters. Data in SAP systems is also targeted by attackers for cybercrime and corporate espionage. This article demonstrates how you can use SAP Solution Manager to detect and contain potential information leaks in your SAP systems before they lead to a full-blown data breach. The demonstration leverages the advanced diagnostics capabilities of the Monitoring and Alerting Infrastructure (MAI) in Solution Manager. MAI connects directly to SAP systems to monitor event data in SAP log files and tables.
The specific scenario that will be used to demonstrate the monitoring capabilities of MAI is access to SAP logon data in table USR02 using data browsing transactions such as SE16. However, the scenario can be adapted for other sensitive data including financial, employee and product-related information in SAP tables.
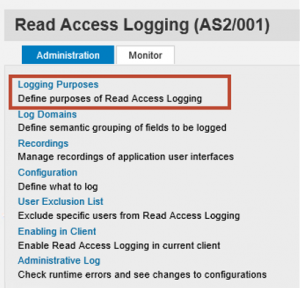
The first step is to configure a logging scenario to log access to table USR02 through SE16. This can be transported from a source system or configured directly in a target system using Read Access Logging (RAL). For the configuration option, we will define a log purpose and domain.
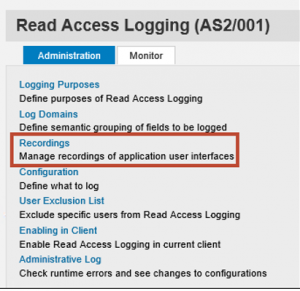
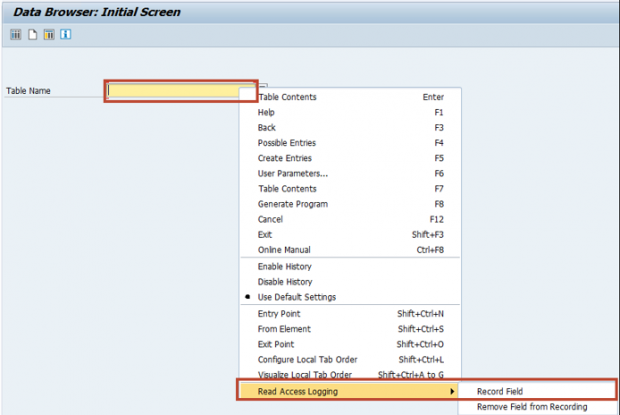
The next step is to create a recording to capture the data fields and values using SAP GUI. Read Access Logging also supports logging scenarios for data accessed through web browsers, web services, remote function calls, and OData services via the SAP Gateway.
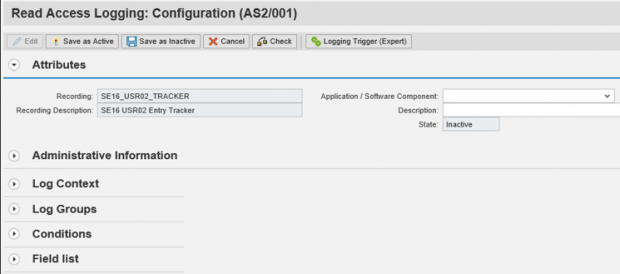
Once the recording is completed, we will define the log contexts, groups and conditions in the RAL configuration.
Finally, we will maintain User Exclusion Lists for users that should be excluded from logging and activate the scenario.
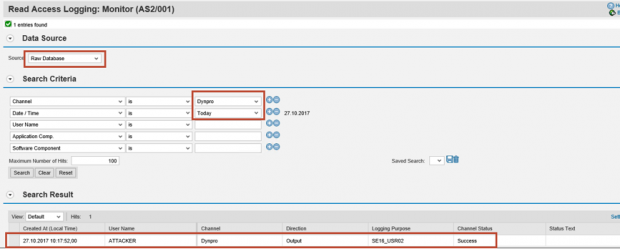
The activation of the scenario will trigger logging for access to table USR02 through SE16. The log records can be read using the RAL Monitor.
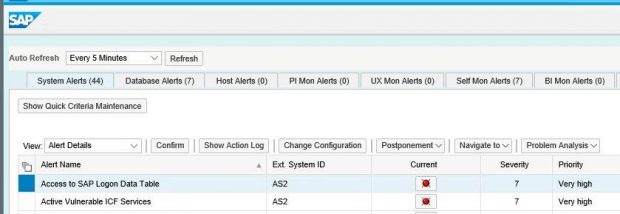
Although RAL logs access to sensitive data with timestamps and usernames, it does not trigger an alert or notification for logged events. Therefore, the next step is to configure metrics, alerts and notifications using MAI in SAP Solution Manager.
Custom metrics and alerts are defined in the Template Maintenance section of System Monitoring within Solution Manager Configuration. Metrics and alerts can be at the database, host, system or instance level and are contained in monitoring templates. For custom metrics, we need to specify a metric name, data type and unit of measure. We also have to specify options for data collection including collector types and intervals. For the RAL scenario, we will use the RFC option for a table connector with a collection interval of 5 minutes. We will also specify the RAL table and configuration ID in the metric input parameters. Based on the configuration, MAI will connect to the RAL table in each system every 5 minutes and search for the configuration ID of the logging scenario.
For the alert, we will define a custom name and description, select the category and severity, and maintain the notification settings to automatically generate an email and/ or SMS for the alert. We will also maintain recipient lists for the notifications. To avoid alert flooding, we can adjust the interval for follow-up notifications based on number of minutes, hours or days. We can also group multiple alerts into a single notification. To activate the alert, we need to assign the metric to the alert and then assign the template containing the alert to the target systems in the landscape.
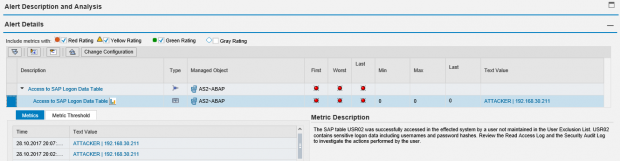
Below is the alert and email notification generated by Solution Manager for the RAL event. The alert details include the username and source IP address of the user that accessed table USR02 using transaction SE16. This is displayed in the Text Value.
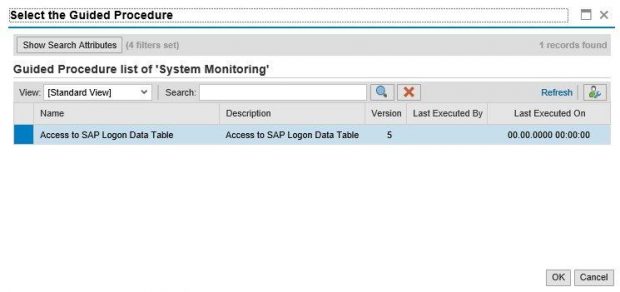
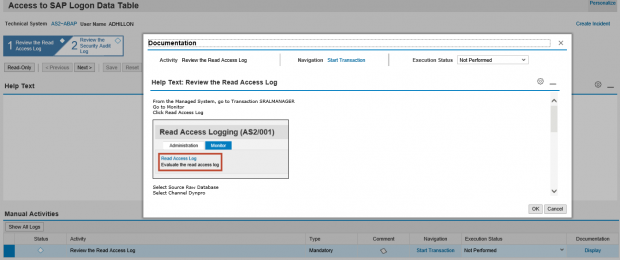
The third step is the configuration of a guided procedure to support the investigation of the alert. This can be performed using the Guided Procedure Authoring Tool in Solution Manager. In the example below, we have created a 2-step guided procedure to firstly, access the RAL Monitor in order to review the event and secondly, investigate other actions performed by the user logged in the Security Audit Log. The Guided Procedure includes automatic transaction jumps to the required screens and reports in the target system.
Log settings, monitoring templates and guided procedures can be licensed and transported directly into managed systems and SAP Solution Manager to accelerate the implementation of threat detection using MAI. Contact Layer Seven Security to learn more.