Securing Custom SAPUI5 Applications using the Cybersecurity Extension for SAP
SAPUI5 is the foundation of Fiori applications in SAP solutions such as SAP HANA and S/4HANA. It provides a HTML5 framework for developing flexible and user-friendly applications that perform consistently across all browsers, platforms, and devices, and integrate with ABAP programs using APIs such as OData services.
The SAPUI5 library is based on the jQuery JavaScript library. Therefore, although SAP Web IDE is recommended by SAP, UI5 applications can be developed using any development environment that supports JavaScript development. SAPUI5 applications generate their own JavaScript code and handle HTML rendering. Consequently, the applications are more susceptible to code-level vulnerabilities than Web Dynpro applications that use an abstract programming model. Application developers should ensure custom SAPUI5 applications meet stringent security standards during all phases of the development lifecycle. Custom applications are part of the attack surface for SAP systems and vulnerable applications are often targeted by threat actors to compromise SAP solutions. Since custom applications are not maintained by SAP and not patched by SAP security notes, customers are directly responsible for ensuring custom applications are secure and protected against misuse.
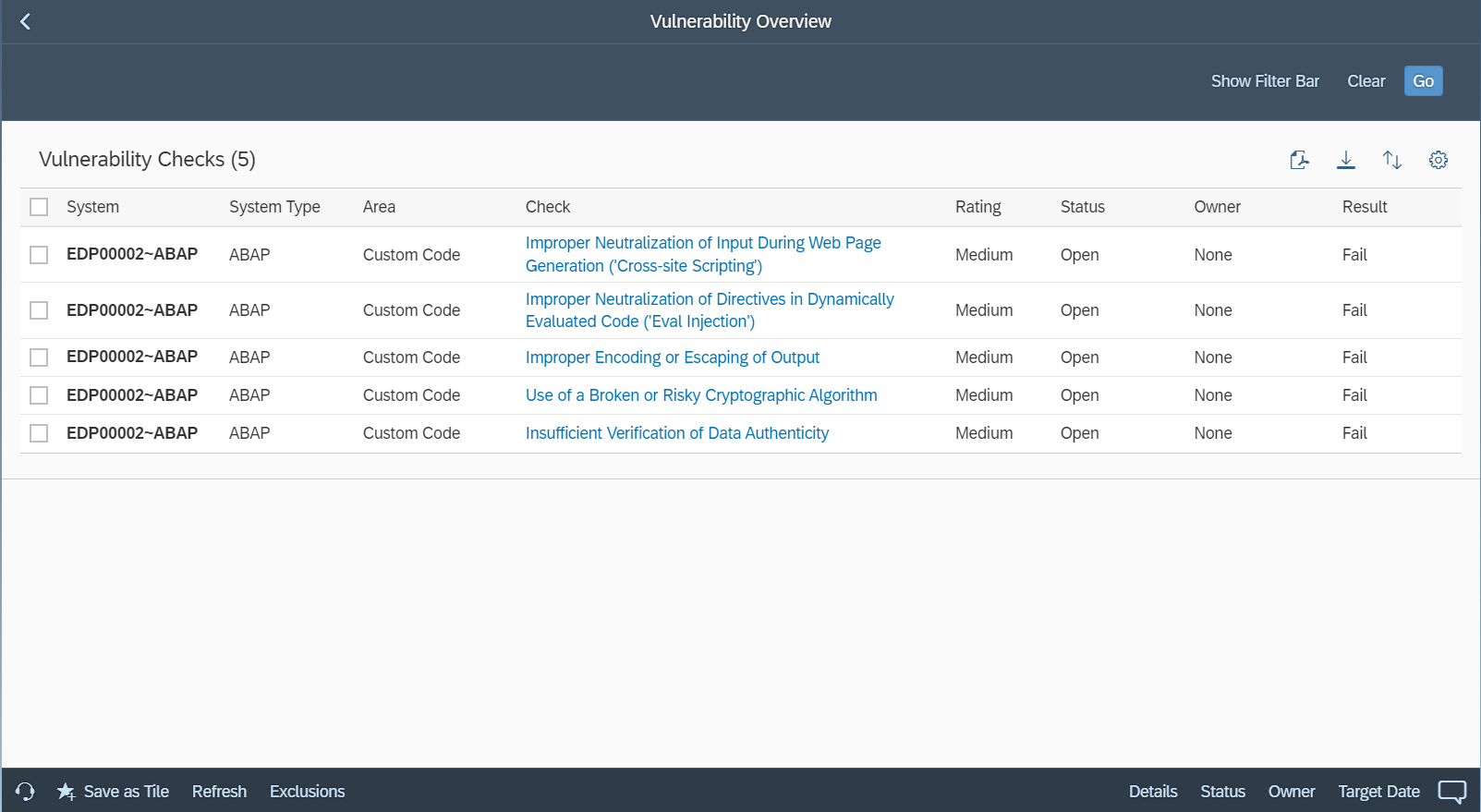
Automatic static source code scanning is a proven method to effectively and efficiently detect software vulnerabilities in custom applications during and after development. In addition to static code scanning for over 100 vulnerabilities in custom ABAP programs, the Cybersecurity Extension for SAP (CES) supports the automatic detection of more than 900 vulnerabilities in custom SAPUI5 applications. This includes vulnerabilities such as code injection, SQL injection, cross-site scripting, directory traversal, and missing or insufficient authentication or authorization checks. CES enables SAP customers to securely develop and deploy custom SAPUI5 applications to support the needs of end-users, in accordance with best practices for secure coding.
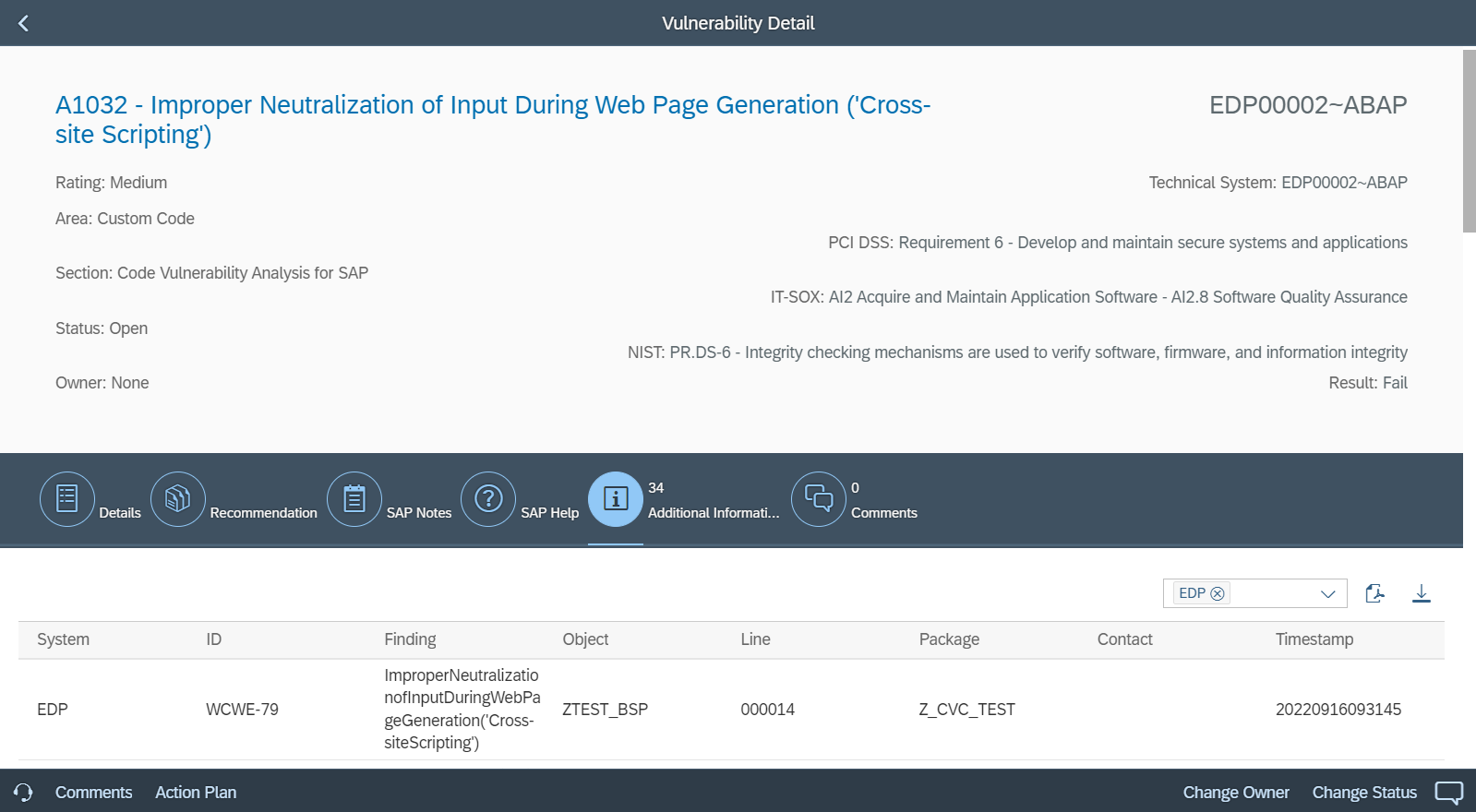
CES provides detailed information for vulnerabilities detected in custom SAPUI5 applications, including risk analysis, remediation guidance, and details of the impacted lines of code, objects, packages and owners. Findings are also mapped to the Common Weakness Enumeration (CWE) framework to monitor for compliance against coding best practices. CWE is software development standard supported by US-CERT and the National Cyber Security Division of the U.S. Department of Homeland Security. The results of static code scan results for custom SAPUI5 applications can be reviewed and managed using SAP Code Inspector (SCI) and exported as Excel/ PDF reports. The results are also integrated with the Vulnerability Report in CES, accessed from the Fiori launchpad for SAP Solution Manager.