Discover, Implement and Test Security Notes using SAP Solution Manager 7.2
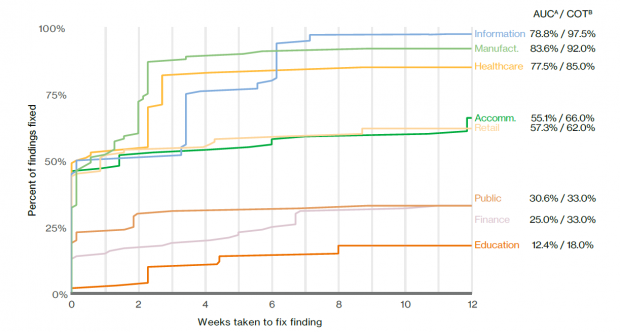
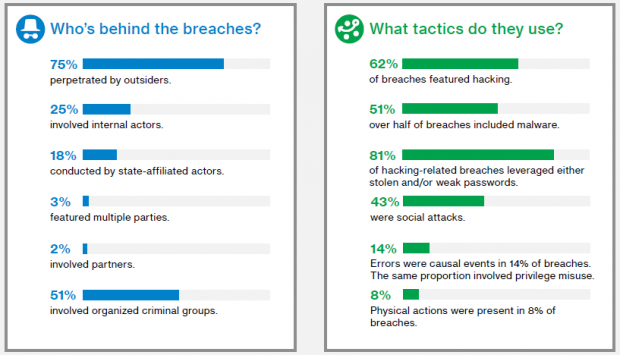
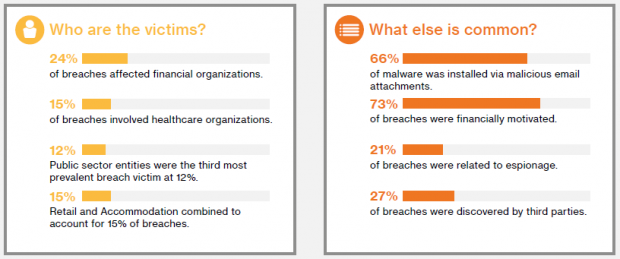
The results of the recent Verizon DBIR revealed significant differences between industries in terms of vulnerability patching. Organizations in sectors such as information technology and manufacturing typically remove over 75% of vulnerabilities within 3 weeks of detection. At the other end of the spectrum, 75% or more of vulnerabilities discovered in financial and public sector organizations and educational institutions remain unpatched for longer than 12 weeks after discovery.
The DBIR masks important differences between patching for devices and applications. Servers, for example, are generally more effectively patched than routers and switches.
Patch cycles for SAP infrastructure and applications are typically more drawn-out than most other technologies. There are several reasons for this. The most important is the lack of visibility into the impact of SAP patches. This leads to a reluctance to apply corrections that may disrupt the performance or availability of systems.
SAP Solution Manager 7.2 overcomes this challenge by enabling customers to pinpoint the impact of security notes before they are applied in systems. Change impact analysis is performed using Usage and Procedure Logging (UPL) and Business Process Change Analyzer (BPCA) integrated with System Recommendations (SysRec).
SysRec provides a real-time analysis of missing security notes and support packs for ABAP and non-ABAP systems including Java and HANA. It connects directly to SAP Support to discover relevant notes and packs for systems configured in the LMDB – SolMan’s landscape information repository. It also connects to each managed system within SAP landscapes to check the implementation status of notes.
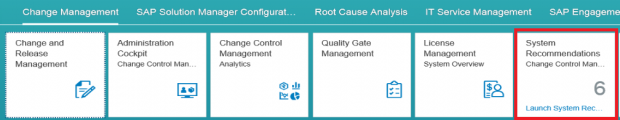
System Recommendations is accessed through the Change Management group in the Fiori launchpad for SAP Solution Manager.
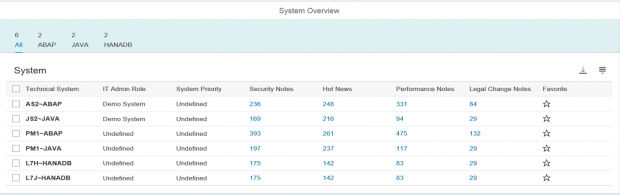
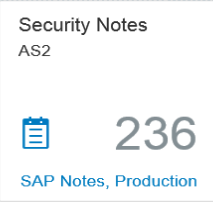
The dashboard below is displayed after the SysRec tile is selected and summarizes notes across the landscape. IT Admin Role and System Priority are attributes maintained in the LMDB. Views can be personalized to sort or filter by attributes or notes.
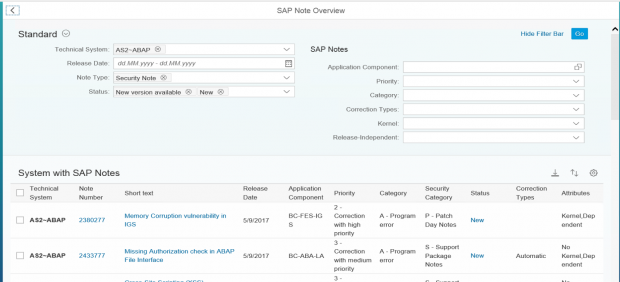
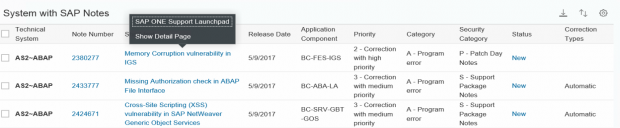
You can apply a wider selection of filters in the detailed section of SysRec to further breakdown the results.
Once the filters are applied, the selection can be saved as a Fiori to tile to avoid reapplying the filters during future sessions. The tile is saved to the launchpad and the counter in the tile automatically updates based on the current status of the system.
The details for each note can be read by clicking on the short text.
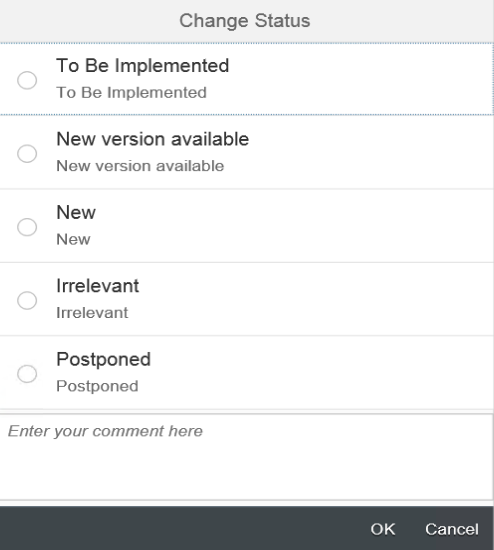
The Actions option allows users to change the status of notes and add comments. Status options are customizable.
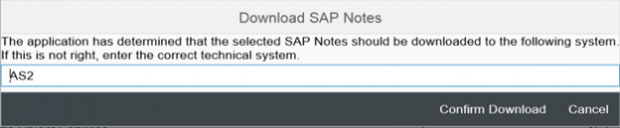
Corrections can be downloaded directly from SAP Support by selecting Integrated Desktop Actions – Download SAP Notes.
Once selected, you can change the target system before the download. The note will be available in SNOTE within the target system after the download.
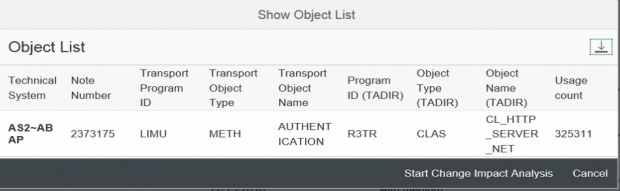
Change impact analysis is performed at both a technical and business level. For technical analysis, SysRec reads data collected by Usage and Procedure Logging (UPL) to display information related to the usage level of objects such as programs, methods and function modules impacted by notes. This is performed by selecting the relevant notes and then Actions – Show Object List.
The results below reveal that Note 2373175 is impacting the standard SAP class CL_HTTP_SERVER_NET. This class was used 325311 times in system AS2 during the timeframe defined for UPL.
For business impact analysis, SysRec integrates with Business Process Change Analyzer (BPCA). BPCA reads solution documentation maintained in Solution Manager to discover modules, transactions, reports, and other areas impacted by notes.
SysRec’s ability to perform comprehensive and reliable change impact analysis for security notes enables customers to overcome one of the most significant roadblocks to effectively patching SAP systems. The usage data collected through UPL together with the solution documentation leveraged using BPCA provides SAP customers with the insights to develop test strategies targeted at the actual areas impacted by notes and narrow the window of vulnerability for unpatched systems.
In a forthcoming article, we will discuss how to import SAP templates and create and execute test plans using Test Management in SAP Solution Manager 7.2.