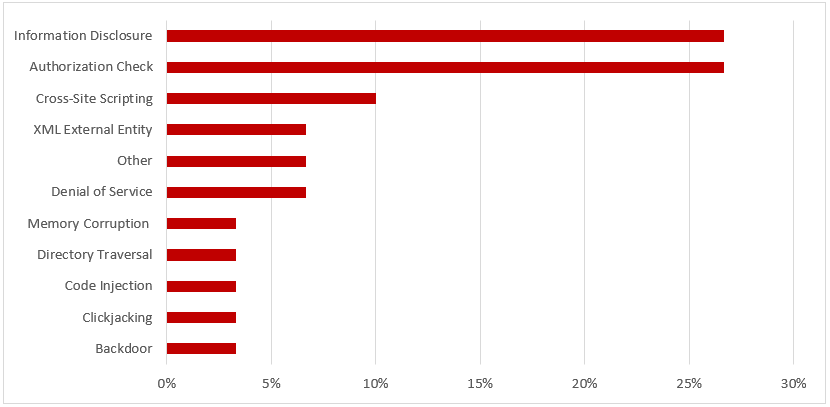
SAP Security Notes, October 2017
SAP issued an important update for Hot News Note 2371726 originally released in November 2016. The note addresses a code injection vulnerability in Text Conversion which enables SAP standard text to be replaced by industry specific text. Function module BRAN_DIR_CREATE in Text Conversion enables an authenticated development user to inject operating system commands and execute these from the SAP system via that function. Developer rights through the S_DEVELOP authorization object are required for the successful execution of the exploit. Nonetheless, the note carries a CVSS score of 9.10/ 10 and rates high in terms of impact to data confidentiality, integrity and availability. The note includes corrections for SAP Basis versions 700 – 751 which restrict the range of supported special characters and the directory created by function module BRAN_DIR_ CREATE.
Note 2486657 patches a high-risk directory traversal vulnerability in the API Engine of AS Java which arises from insufficient path validation performed by the Servlet API for resource requests. This could lead attackers to read the content of arbitrary files on servers and expose sensitive data to corruption or deletion. The Note includes instructions for updating versions 7.10 – 7.50 of AS Java to the latest patch level including the vulnerable components ENGINEAPI, J2EE ENGINE, J2EE ENGINE CORE and JEECOR.
Note 2476937 delivers a patch for a critical denial of service vulnerability in the SAP Standalone Enqueue Server which is used to support direct TCP connections between clients and servers that bypass dispatchers and message servers. Attackers can trigger resource exhaustion in the Server using specific requests. The Note includes kernel patches for SAP Kernel versions 7.21 – 7.53.
Note 2408073 includes updated instructions for manual activities required to prepare SAP systems to process digitally signed Notes. The note also includes sample files to test the security features once they are enabled.