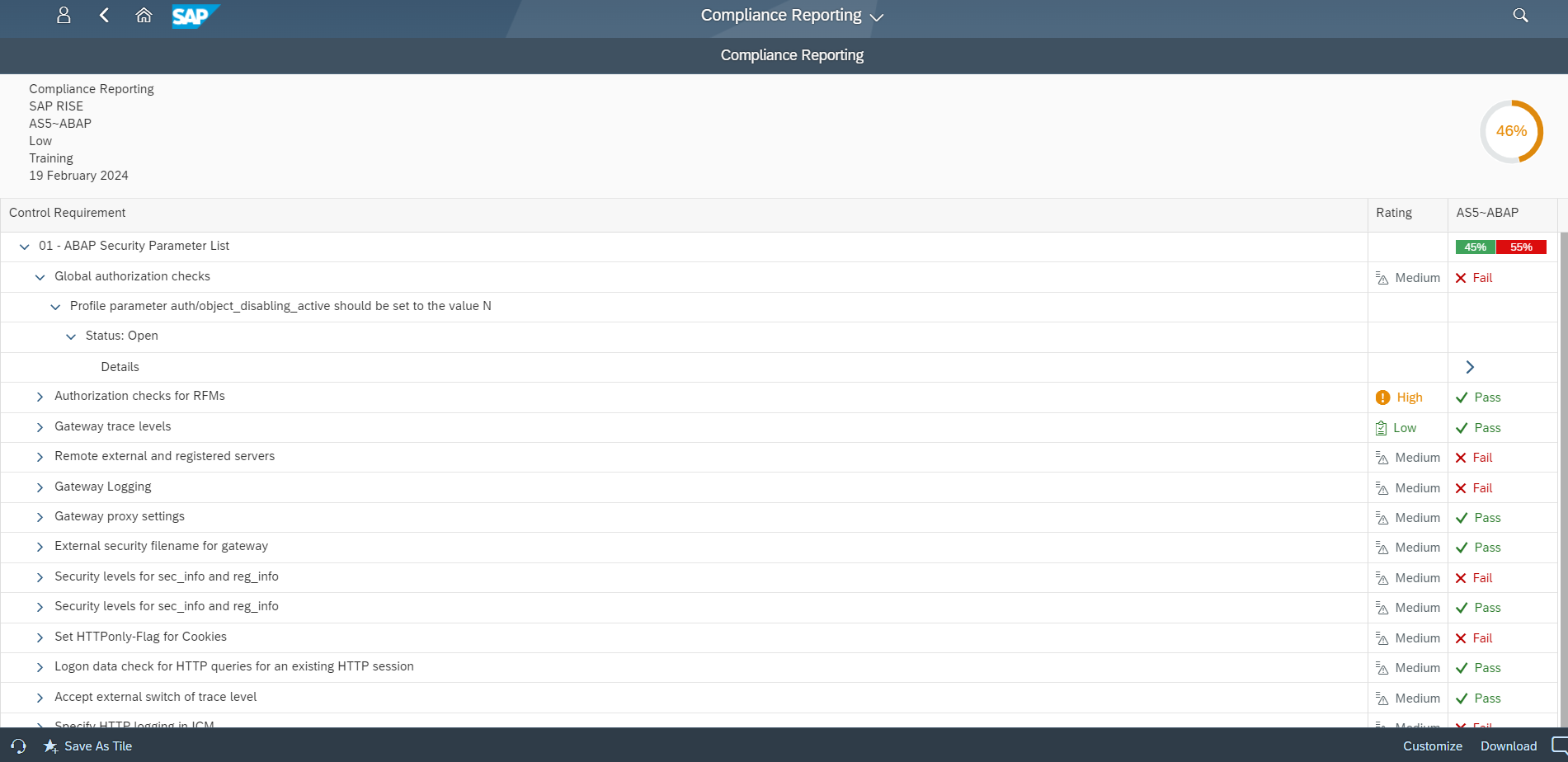
SAP Security Notes, July 2024
Note 3483344 addresses a high-risk missing authentication check in SAP Product Design Cost Estimation (PDCE), included in the S4CORE component of SAP S/4HANA. The vulnerability can be exploited to escalate privileges and read sensitive information. The correction included in the note deactivates the affected functions to remove the vulnerability. There is no workaround provided by SAP. The note applies to versions 102-103 of S4CORE and 104-108 of S4COREOP.
Note 3490515 patches a vulnerability in SAP Commerce which enables users to misuse the forgotten password functionality to gain access to a Composable Storefront B2B site for which early login and registration is activated, without requiring the merchant to approve the account beforehand. If the site is not configured as an isolated site, this can also grant access to other non-isolated early login sites, even if registration is not enabled for those other sites. The issue materializes when both early login and registration are set to true. It does not affect setups that utilize classic accelerator storefronts and is specific to B2B scenarios. A workaround in the note includes steps for disabling early login and registration.
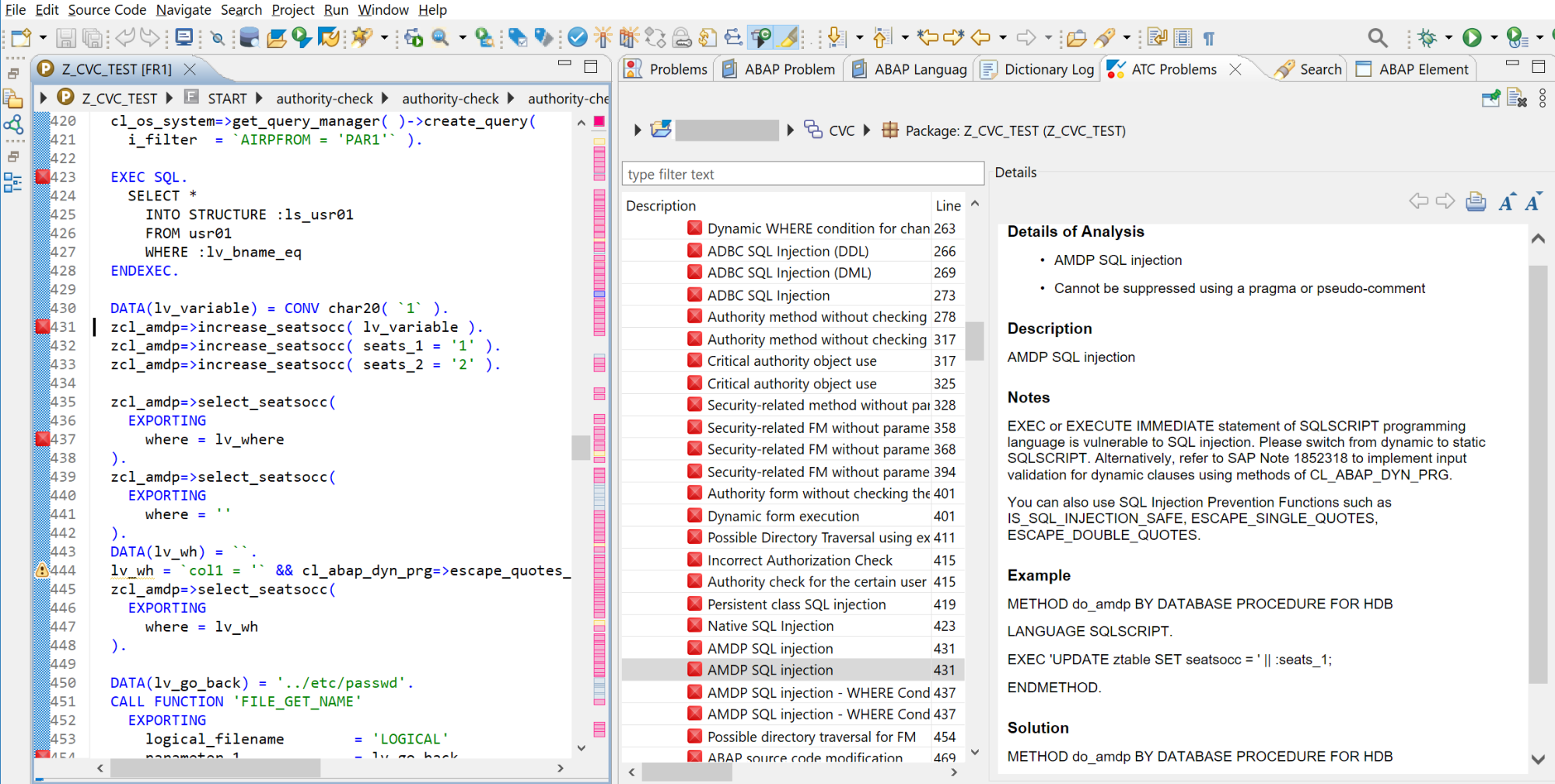
Note 3454858 addresses an information disclosure vulnerability in SAP NetWeaver Application Server ABAP (AS ABAP) and ABAP Platform. The note updates function module F4_DXFILENAME_TOPRECURSION to restrict access to the file system and prevent users from traversing to unauthorized directories.
Note 3456952 patches SAP NetWeaver AS ABAP and ABAP Platform to prevent developers bypassing an API configured for malware scanning using classes CL_HTTP_REQUEST and CL_HTTP_ENTITY.
Notes 3482217 and 3468681 address multiple cross-site scripting vulnerabilities in SAP Business Warehouse and SAP Knowledge Management, respectively.