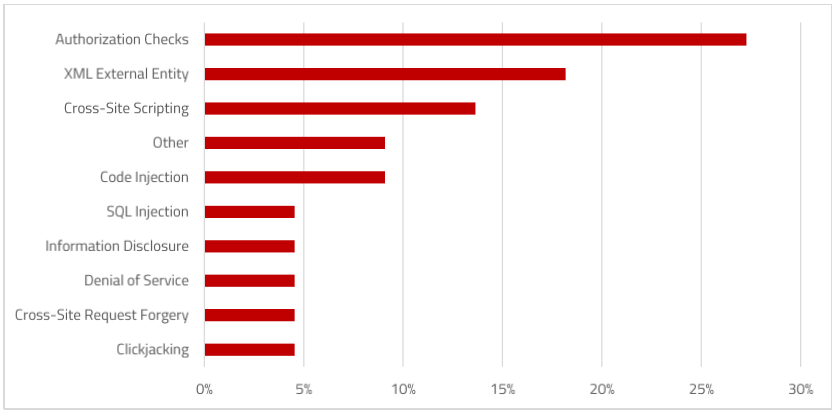
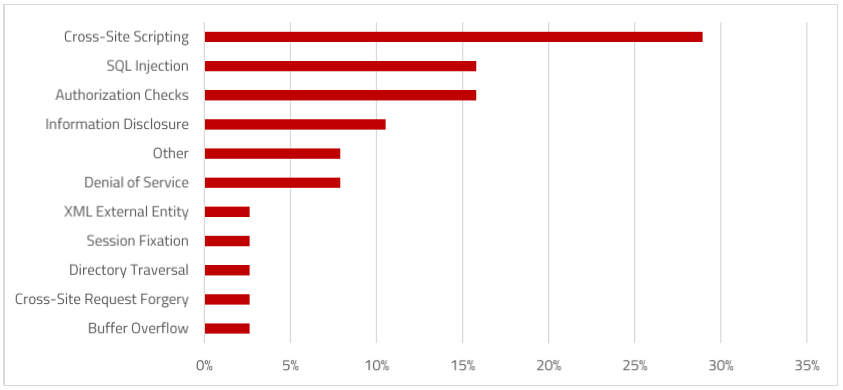
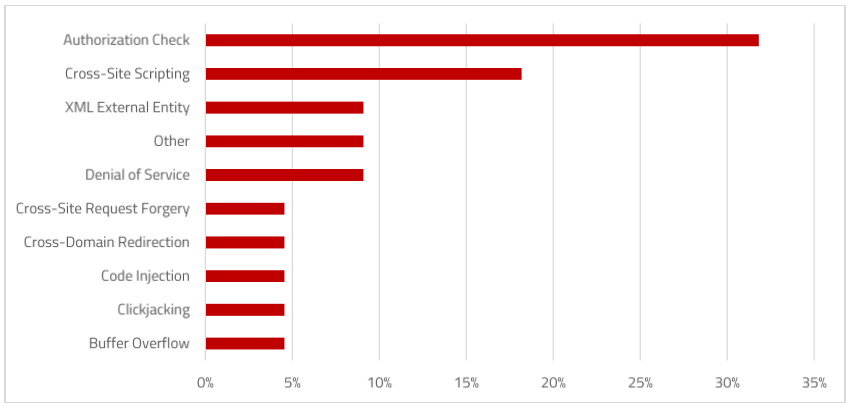
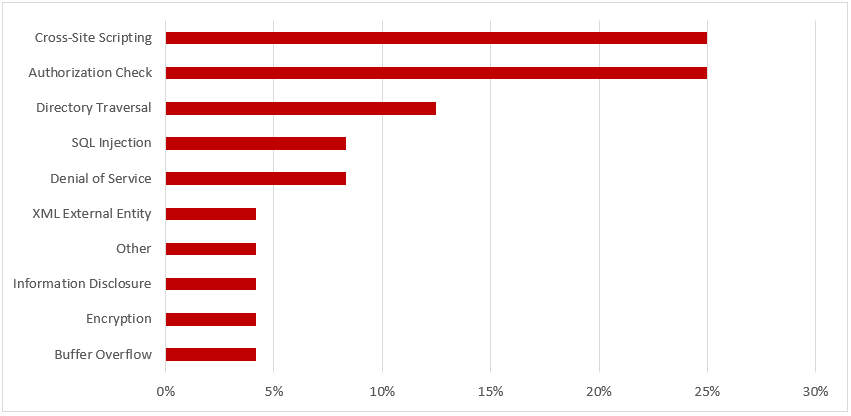
SAP Security Notes, April 2017
Note 2419592 includes further corrections for a code injection vulnerability in TREX that was originally patched by SAP through Note 2234226 in February 2016. The vulnerability impacts the TREXNet protocol used for internal communications by TREX components and servers. TREXNet communication does not require any authentication. Therefore, the protocol can be abused to execute dangerous commands including OS commands using the administrative privileges of the <SID>ADM user. As a result, SAP recommends running TREX in an isolated subnet. Detailed instructions are documented in the TREX Installation Guide. However, the corrections included in Note 2419592 block access to the TREXNet interface from outside the TREX landscape. Therefore, it protects unsegmented systems against malicious commands targeting the protocol. TREX versions 7.10 and 7.25 must be upgraded to revisions 74 and 37 respectively to apply the corrections.
Note 2235515 includes an important update for SNOTE to log information related to the RFC destination used to download notes. SNOTE can be abused to download malicious packages from attacker controlled servers if the default RFC destination is changed. SNOTE executes program SCWN_NOTE_DOWNLOAD during runtime. The program will use an alternative RFC destination maintained in table CWBRFCUSR if a destination is defined in the table. For more information refer to Note 2235514.
Notes 2410082, 2372301, 2400292 and 2387249 deal with weaknesses in XML input validation that expose several ABAP and Java applications to XML External Entity (XXE) attacks. The impact of successful XXE exploits include sensitive information disclosure and denial of service.
Finally, Note 2407616 provides an update for saprules.xml to secure against a high-risk vulnerability that could enable attackers to execute remote commands against SAP GUI. saprules.xml is used by the SAP GUI Security Module to protect clients against potentially malicious commands from back-end SAP servers.