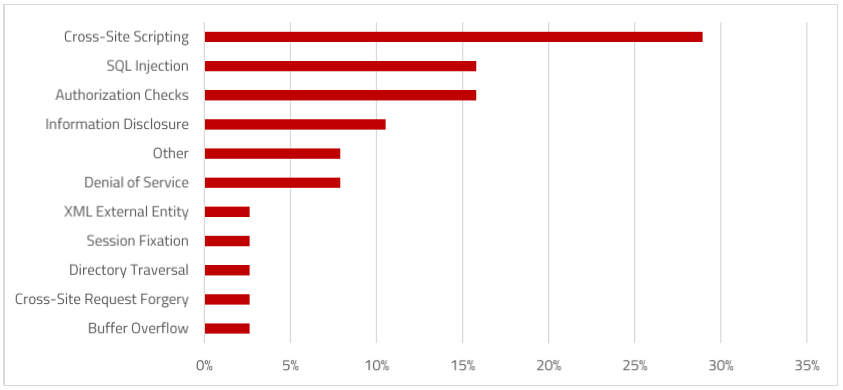
SAP Security Notes, March 2017
Note 2424173 deals with vulnerabilities in SAP HANA that were the subject of media attention in March. This includes coverage from the television news channel MSNBC. The vulnerabilities impact areas such as User Self Service Tools that support account-related tasks including password resets and self-registration through a web interface.
The Note carries a CVSS of 9.8/10. The exploit range and impact are high. The attack complexity is low and no specific privileges are required to execute the related exploits.
Attacks that exploit the vulnerable areas of user self-service appear to target the SYSTEM user in SAP HANA. The SYSTEM user is a powerful default user that should be deactivated after the initial install of the database. Any compromise of the SYSTEM user can lead to anonymous and privileged access to SAP HANA, leading to the complete compromise of the platform and data stored or processed by HANA.
User self-service tools are disabled in the default configuration of SAP HANA. Activation requires the creation of a technical user, configuring SMTP services and maintaining relevant parameters in the xsengine.ini file.
User self-service parameters and the status of the SYSTEM user can be monitored using SAP Solution Manager. The latter includes successful and unsuccessful logon attempts. Automatic alerts can be enabled for vulnerable settings and any action performed by the SYSTEM user.
Other critical corrections include Note 2319506 which removes a blind SQL injection vulnerability in Database Monitors for Oracle. The exploit addressed by the Note targets vulnerable input parameters in the function modules STUO_GET_ORA_ SYS_TABLE and STUO_GET_ORA_SYS_ TABLE_2 used to read or modify system tables.
Notes 2381388 and 2378999 remove missing authorization checks in the stock transfer process of Materials Management, a widely-deployed module of SAP ERP.
Finally, Note 2429069 addresses a session fixation vulnerability in SAP HANA 2.0 that enables attackers to decipher the session IDs of concurrent users.