Securing Microsoft Platforms with the Cybersecurity Extension for SAP
SAP systems consist of multiple integrated technological layers. SAP solutions comprise the application layer. The application layer is supported by database and operating system layers. The layers are closely integrated to form a software ecosystem linked through several connections including trust relationships that bond the layers to form an SAP system. The layers are more tightly integrated in SAP HANA installations where application, database and OS functions can share physical resources.
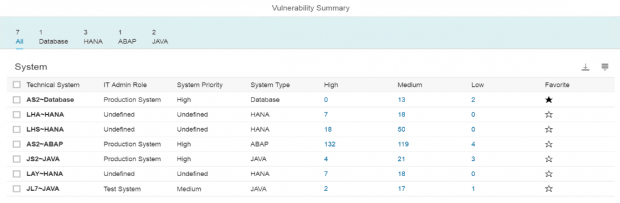
Since SAP systems are comprised of multiple layers, security must be applied across all layers within a system. Threat actors can bypass secure SAP applications by targeting weaknesses at the database or OS level to compromise SAP systems. Ransomware, for example, can lead to a denial-of-service for SAP services by exploiting vulnerable operating systems. Application-level data protection mechanisms can be bypassed by exfiltrating data in SAP solutions directly from the database.
The need to secure databases and operating systems in SAP systems is more pressing when SAP applications are coupled with Microsoft platforms that are widely targeted by threat actors and suffer from a host of known vulnerabilities and exploits. The Cybersecurity Extension for SAP is the only security solution that secures all layers within SAP systems including databases and operating systems.
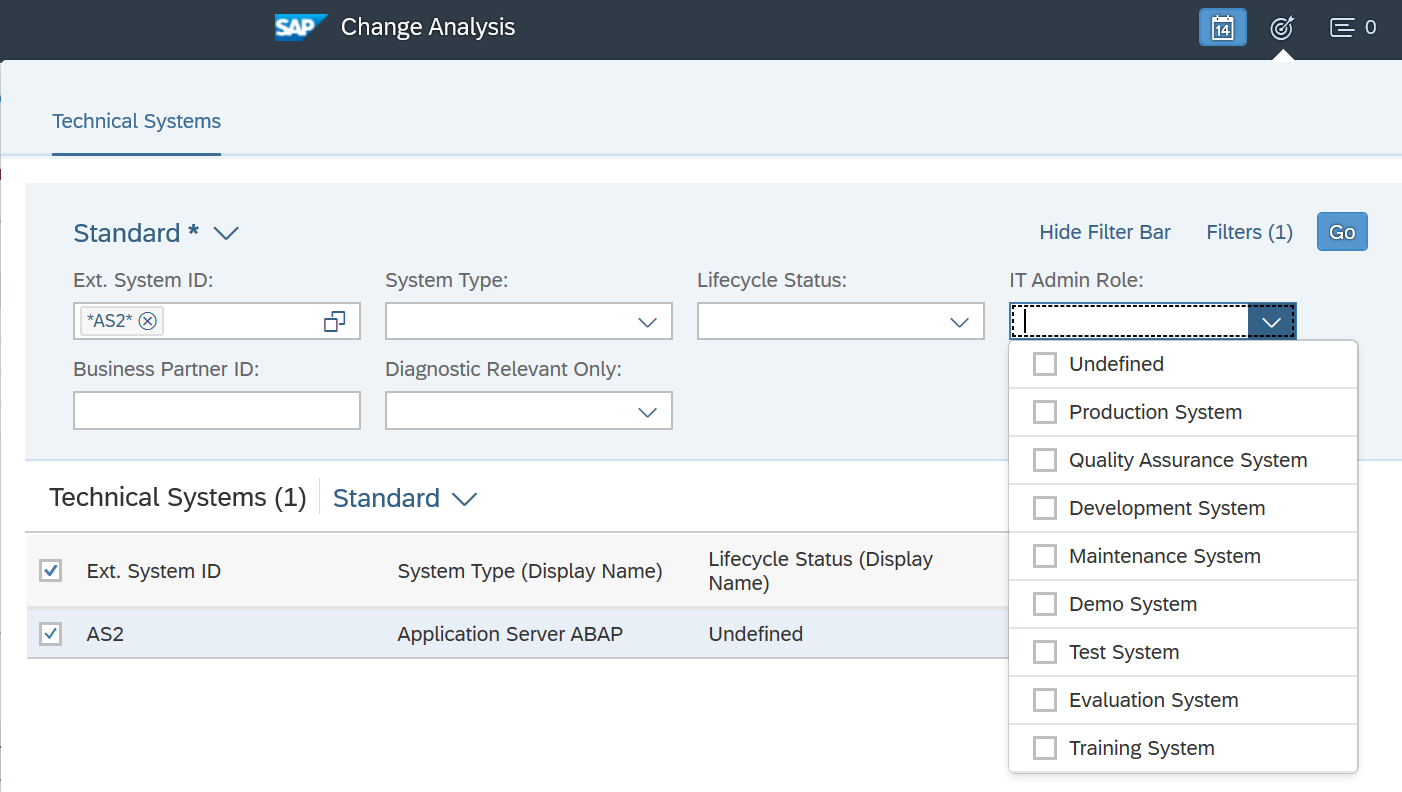
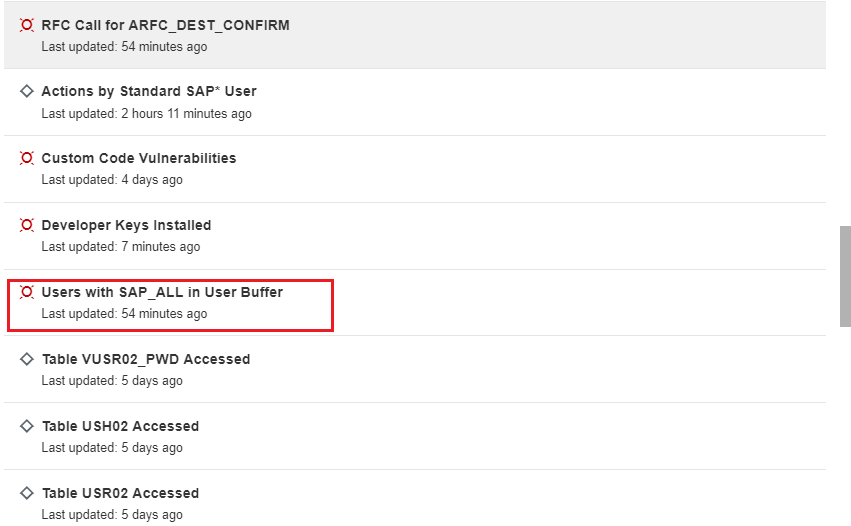
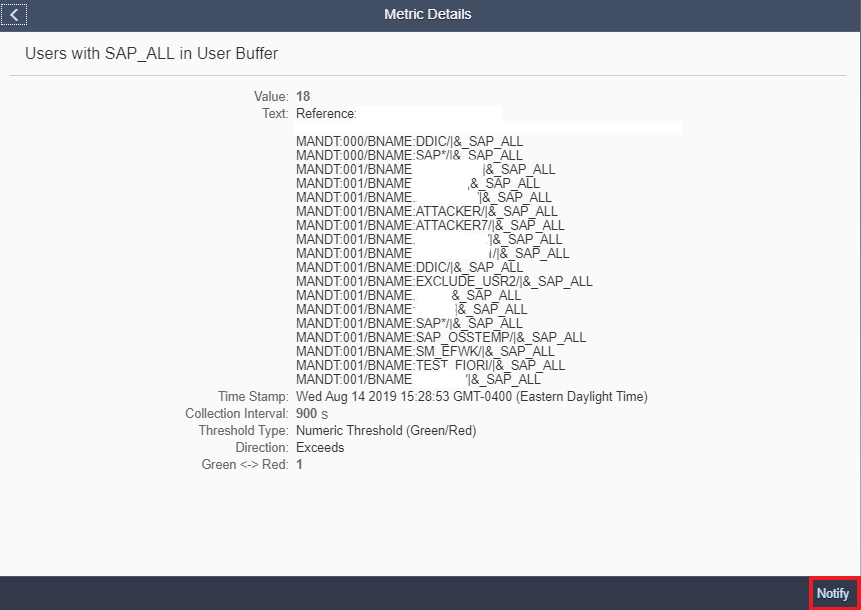
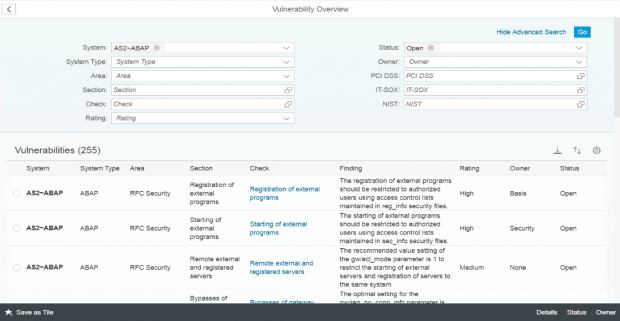
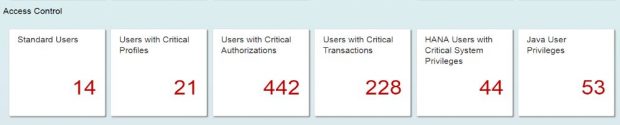
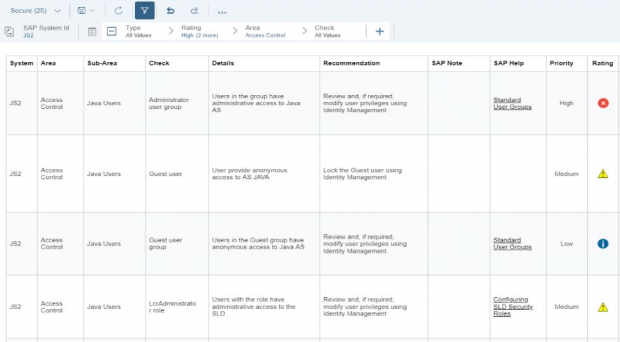
Together with over 2000 vulnerability checks for SAP solutions, the Cybersecurity Extension for SAP performs automated vulnerability scans for Microsoft SQL Server and Microsoft Server to detect more than 300 known security weaknesses in the platforms. This includes active vulnerable services that widen the attack surface for databases and hosts, authentication settings including password policies, file and table encryption, users with administrative privileges including system and user administration, the availability of standard users, logging and auditing, open ports and services, and host firewall settings.
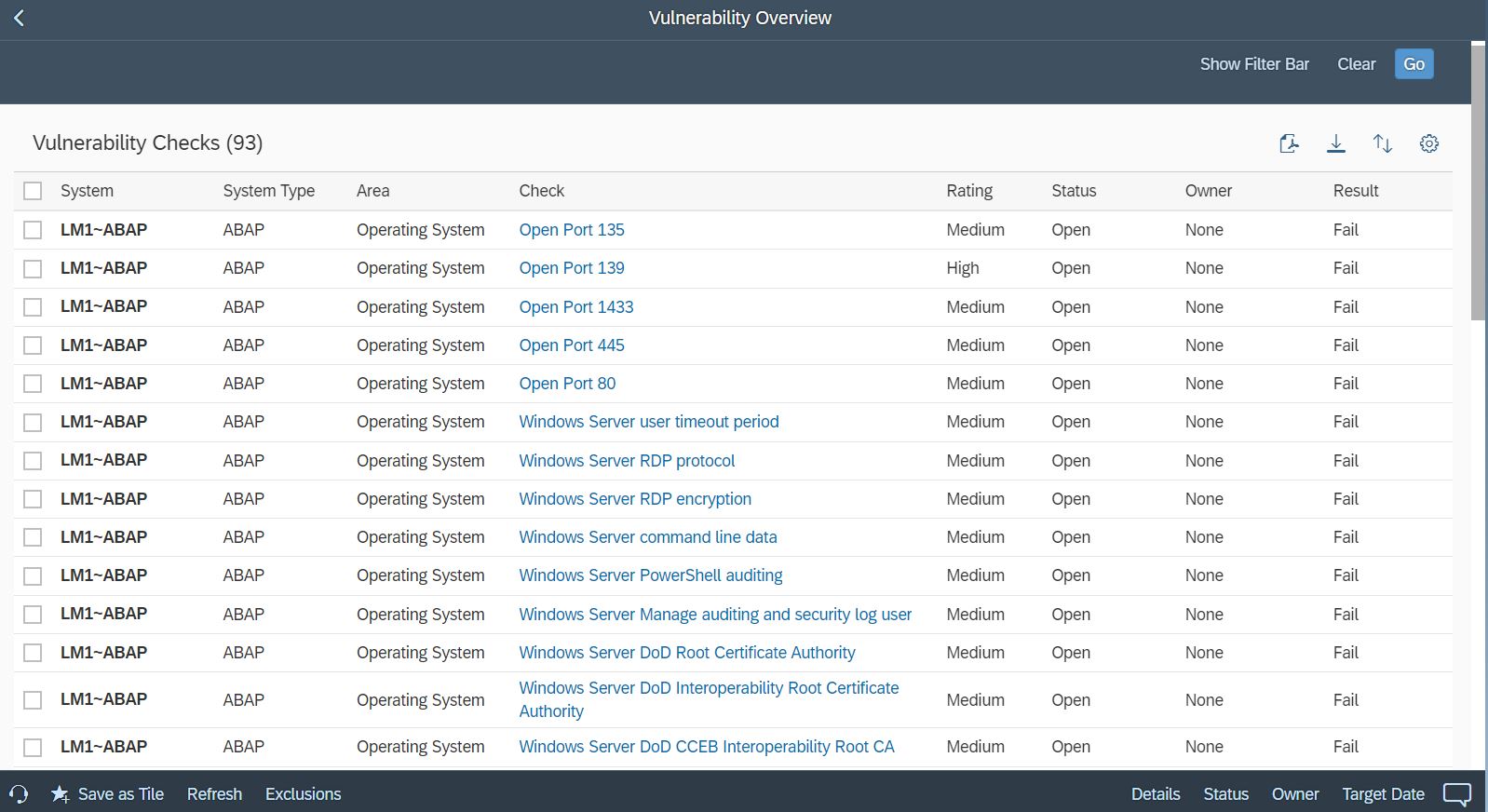
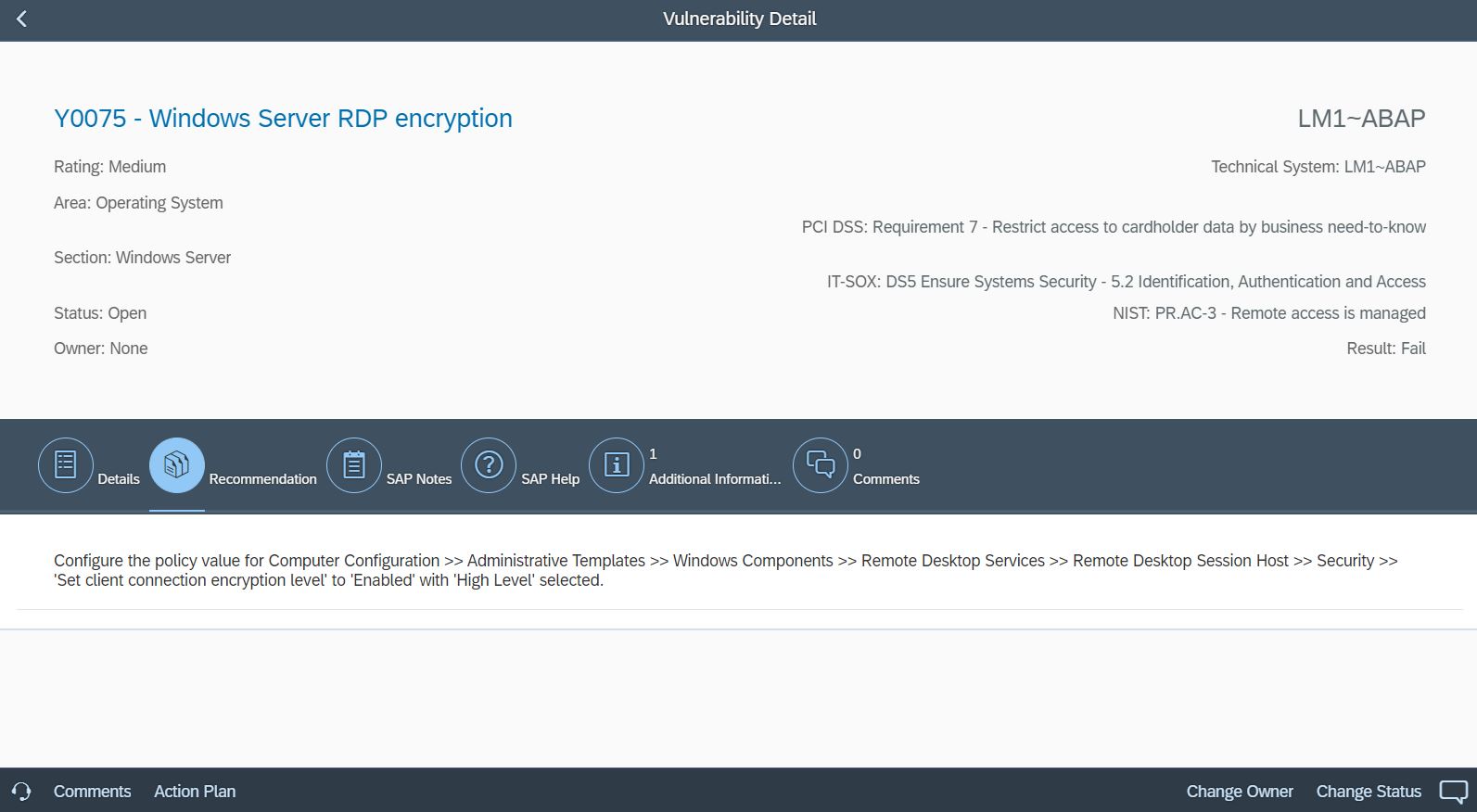
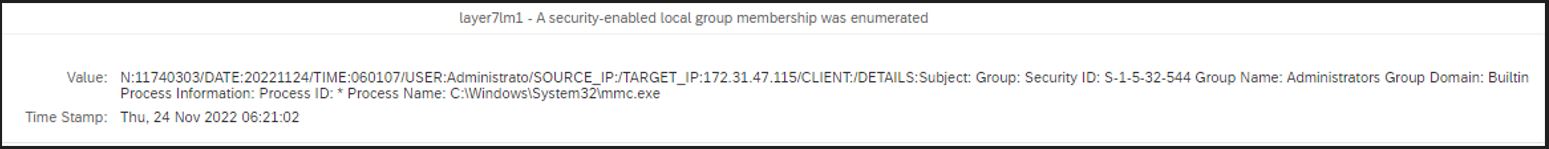
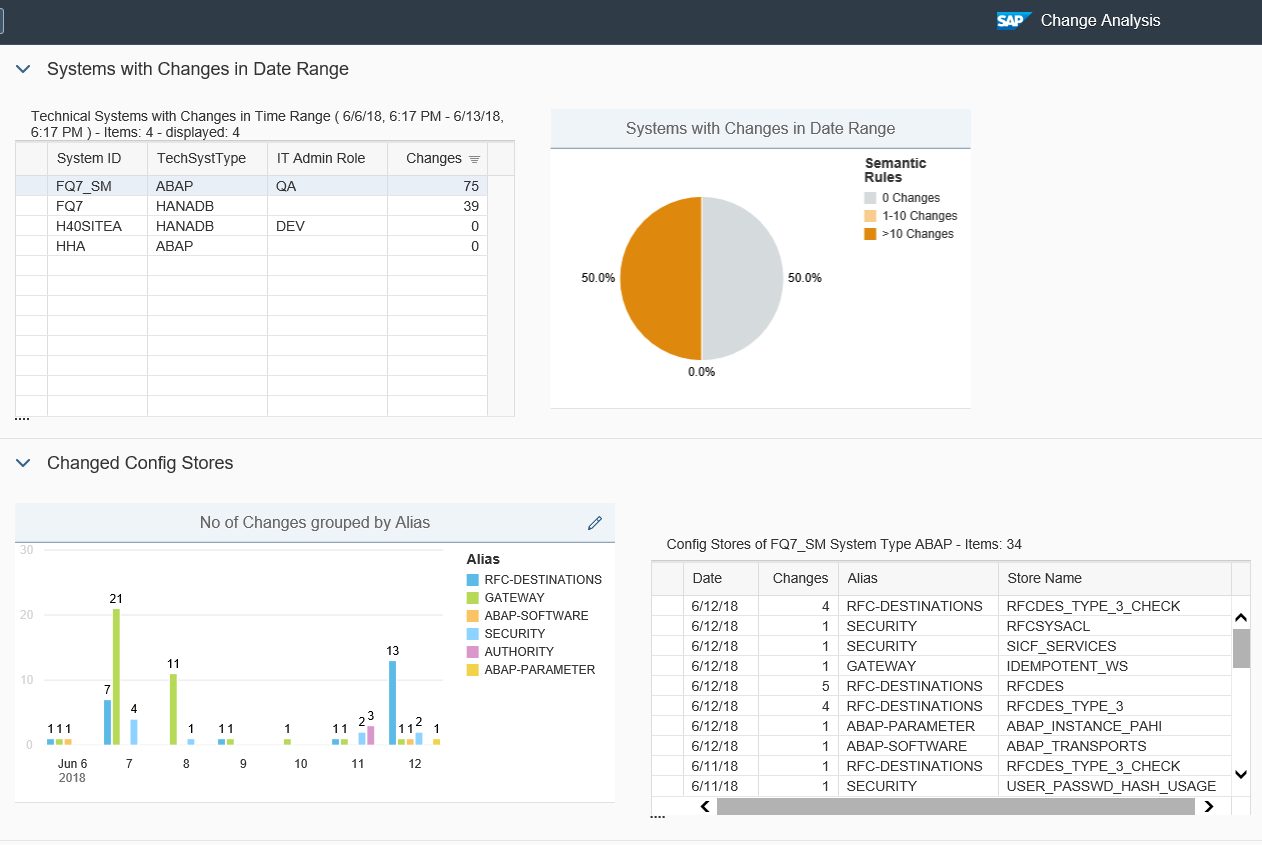
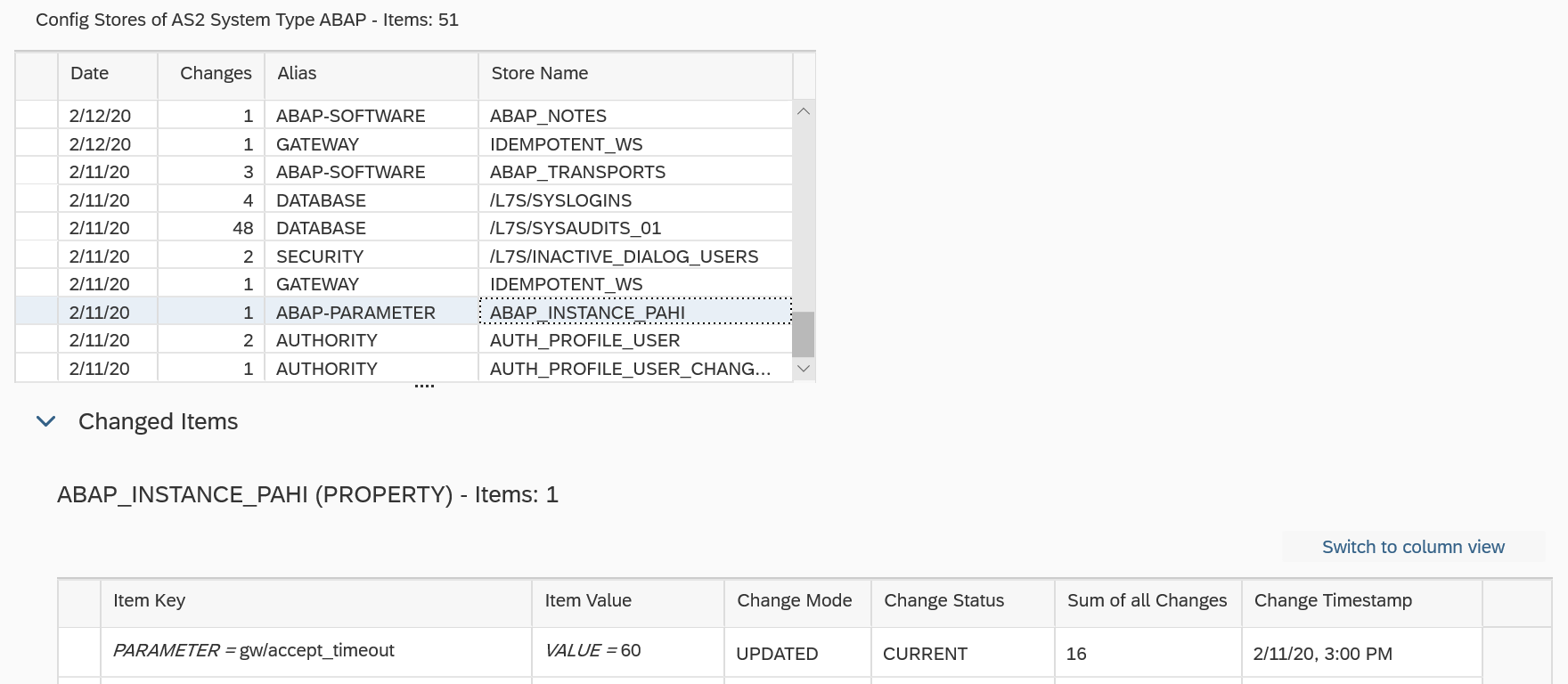
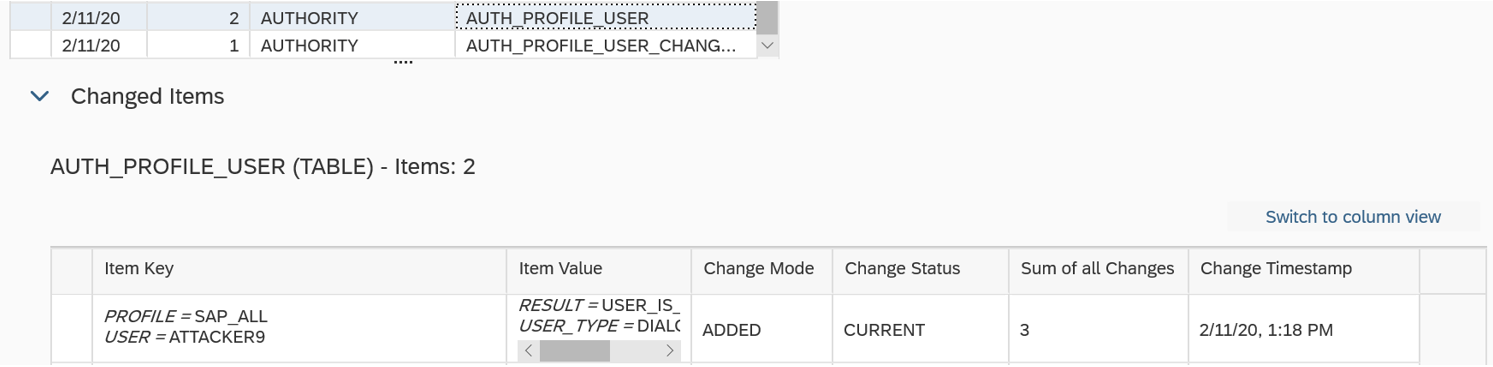
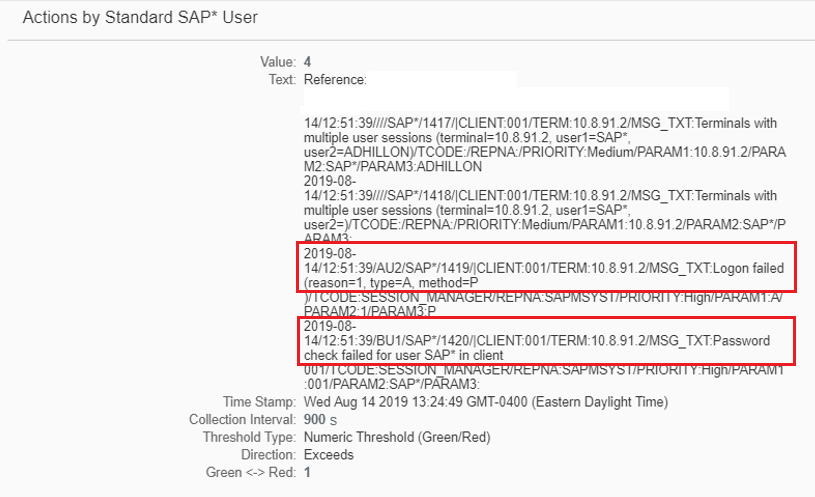
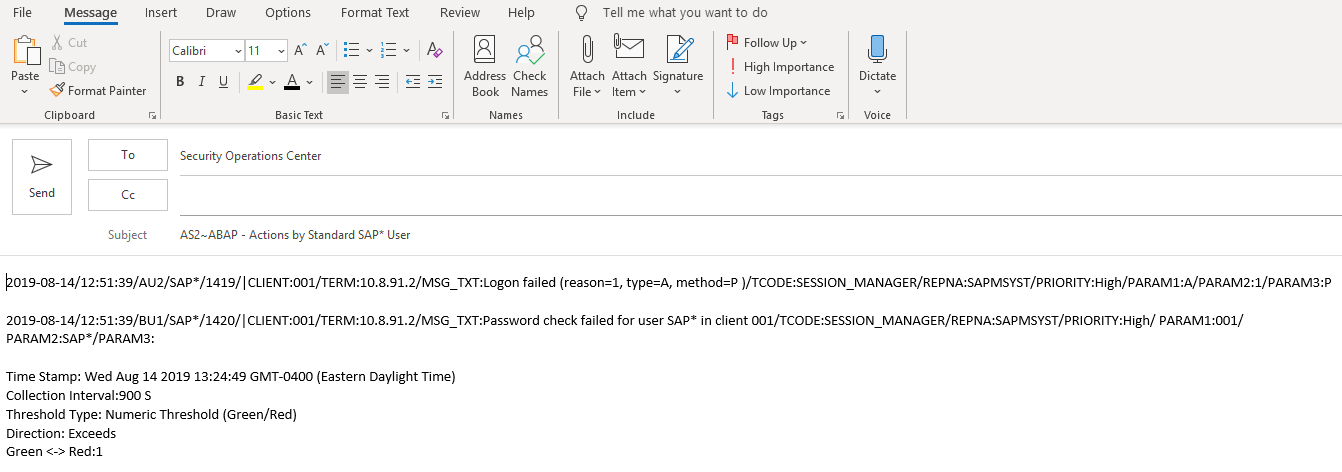
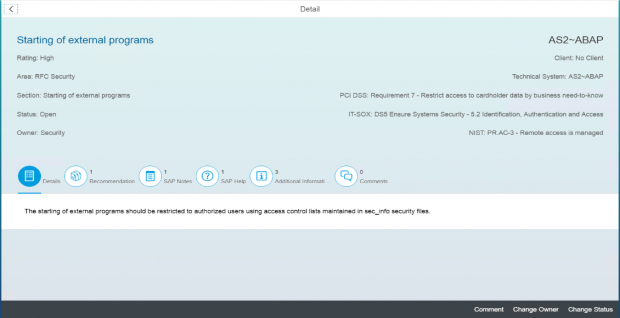
The Cybersecurity Extension for SAP also monitors database and operating logs to detect indicators of compromise in Microsoft platforms and trigger alerts and email/ SMS notifications for security incidents. This includes system, role and user changes, direct access to user tables, changes to database schemas, user groups, scheduled tasks, stored procedures, passwords and firewall settings, failed logons including attempted remote logons, packets blocked by host firewalls, remote procedure calls, service activation, device and program installation, and changes to system auditing.