New SEC Rules For Cybersecurity Incident and Risk Management Disclosures

The Securities and Exchange Commission (SEC) issued a final rule on July 26, 2023 that will require public companies to disclose material cybersecurity incidents on Form 8-K within four business days of discovery. In addition, the SEC will now require public companies to disclose on an annual basis in Form 10-K their process for assessing, identifying and managing material risks from cybersecurity threats, as well as information on how companies’ boards and officers govern cyber risk management.
The incident reporting requirements become effective for companies, other than smaller reporting companies, on December 18, 2023. Smaller reporting companies will not be subject to the rule until June 15, 2024. All reporting companies will be subject to the disclosure rules covering their cybersecurity risk management process in annual reports for fiscal years ending on or after December 15, 2023.
For purposes of both the new Form 8-K requirements and the required annual risk management disclosure, a “cybersecurity incident” is defined as “an unauthorized occurrence, or a series of unauthorized occurrences, on or conducted through the registrant’s information systems that jeopardizes the confidentiality, integrity, or availability of a registrant’s information systems or any information residing therein.” The rules also define a “cybersecurity threat” as any potential occurrence that could result in a cybersecurity incident. The rules cover all “information systems” which is defined to include electronic information resources owned or used by the registrant that are used to collect, process, maintain, use, share, disseminate, or dispose of information used to maintain or support the registrant’s operations.
The new rule adds item 1.05 to Form 8-K covering “material cybersecurity incidents.” When the rules become effective, public companies will have to disclose information relating to a material cybersecurity incident four business days after they determine they have experienced one. The disclosure must include the following information: (i) a description of the material aspects of the nature, scope, and timing of the incident and (ii) an assessment of the material impact or reasonably likely material impact of the incident on the company, including the financial impact and the impact on operations. However, companies need not disclose “specific or technical information about its planned response to the incident or its cybersecurity systems, related networks and devices, or potential system vulnerabilities in such detail as would impede the registrant’s response or remediation of the incident.” The adopting SEC release notes that, in assessing the impact of the incident, companies should consider qualitative factors (impact on reputation, actual or potential litigation or regulatory investigations, or competitiveness) as well as quantitative factors.
The determination of materiality relies on the standard securities law formulation that considers whether there is a substantial likelihood that a shareholder would consider the information important in making an investment or whether the information would significantly alter the “total mix” of information available about the company. The determination must be made “without unreasonable delay” following discovery of the incident and the filing must indicate if any required disclosure has not been determined or is not available at the time of the filing. That said, the SEC advises that while the determination “need not be rushed prematurely, it also cannot be unreasonably delayed in an effort to avoid timely disclosure.” Significantly, the release notes that the fact that the full extent of the incident is not yet known or that further investigation will be necessary “should not delay the company from determining materiality.” Examples of unreasonable delay include delay in scheduling a board committee meeting to determine materiality or revision of internal policy to extend assessment deadlines or to change the criteria used to determine incident reporting to management or the board.
The rule identifies two circumstances in which a disclosure delay is permissible. First, the Form 8-K filing may be delayed if disclosure would pose a substantial risk to national security or public safety. The delay is permissible if the U.S. Attorney General has notified the SEC that a substantial risk exists, in which case a delay of up to 30 days is permissible with additional extensions possible if the substantial risk continues to exist. Second, for a company subject to the breach disclosure rules of the Federal Communications Commission relating to customer proprietary network information, disclosure may be delayed if the company notifies the SEC no later than the day disclosure would otherwise be required under the SEC rules.
The SEC also adopted new Item 106 to Regulation S-K that will require a reporting company to provide disclosure in their annual report that identifies “the registrant’s processes, if any, for assessing, identifying, and managing material risks from cybersecurity threats in sufficient detail for a reasonable investor to understand those processes.”
This formulation represents a revision of the rule included in the March 9, 2022 proposed regulations which would have required a more granular discussion of a company’s cybersecurity risk management structure. The agency agreed with commenters who argued that a more detailed level of disclosure went beyond the level that is material to investors and could increase vulnerability to an attack by revealing important operational details of the risk management process.
The final rule also focuses on a non-exclusive list of three areas of disclosure that will help investors to place the disclosed cybersecurity processes in context:
- Whether and how the cybersecurity processes have been integrated into the registrant’s overall risk management system or process;
- Whether the registrant engages consultants, auditors or other third parties in connection with their cybersecurity processes; and
- Whether the registrant has a process to identify material risks from cybersecurity threats associated with the use of third-party service providers.
Separately, the new rules will require disclosure about the board’s oversight of the company’s cybersecurity risk. Specifically, the disclosure must include information on how the board manages the oversight process, i.e., through a board committee or subcommittee, and the process whereby the board or board committee is informed about such risks. The agency dropped language in the proposed regulations that would have required disclosure of board level cybersecurity expertise.
The disclosure must also identify management’s role in assessing and managing material risks from cybersecurity threats with a focus on three areas:
- Identification of the management positions and committee that are responsible for assessing and managing cybersecurity risks and the relevant expertise of such persons or committee members;
- The process by which such persons are informed about and monitor the prevention, detection, mitigation, and remediation of cybersecurity incidents; and
- How such persons report information about cybersecurity risk to the board and/or the appropriate board committee.
Source: Kilpatrick Townsend & Stockton LLP
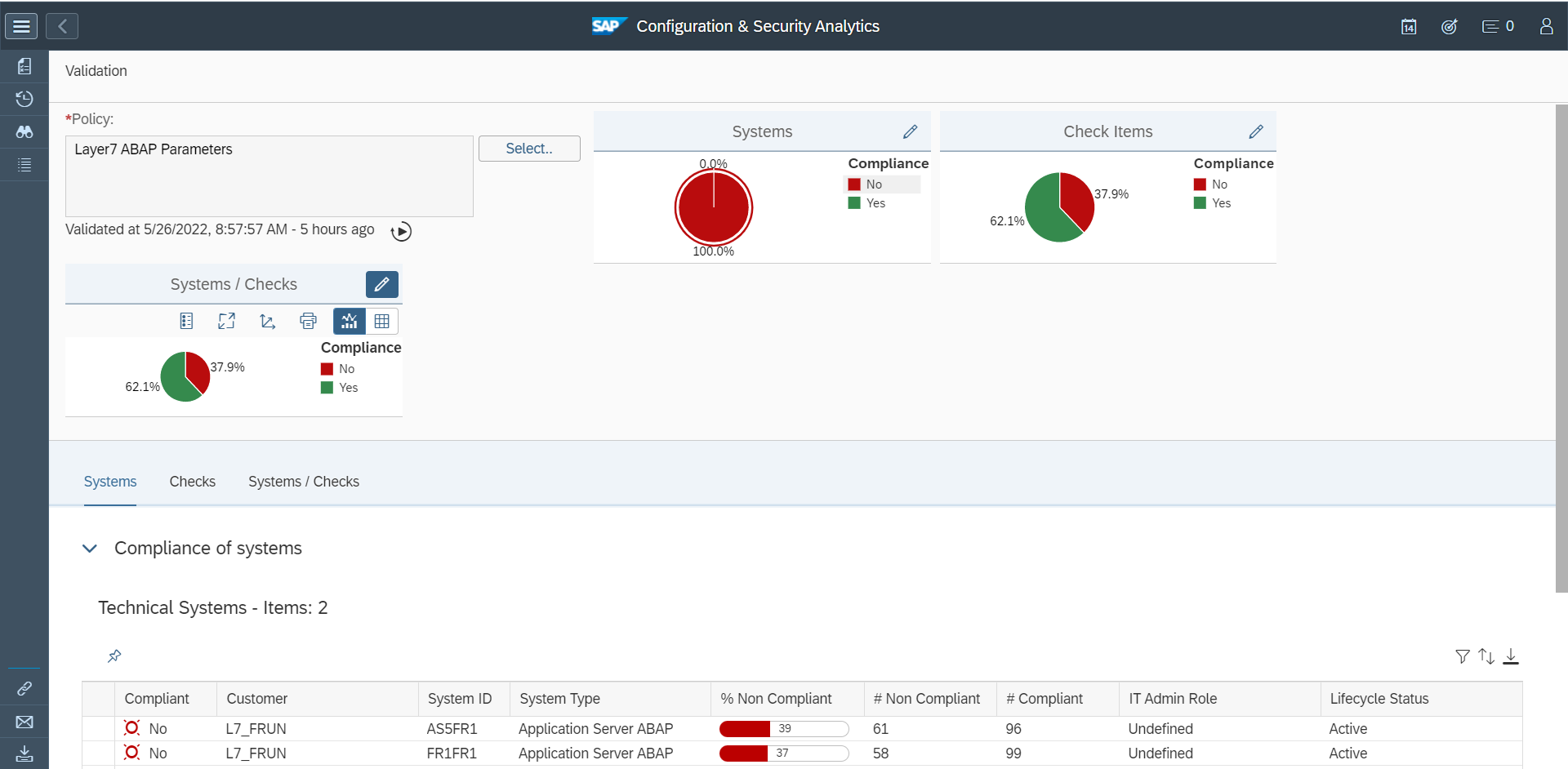
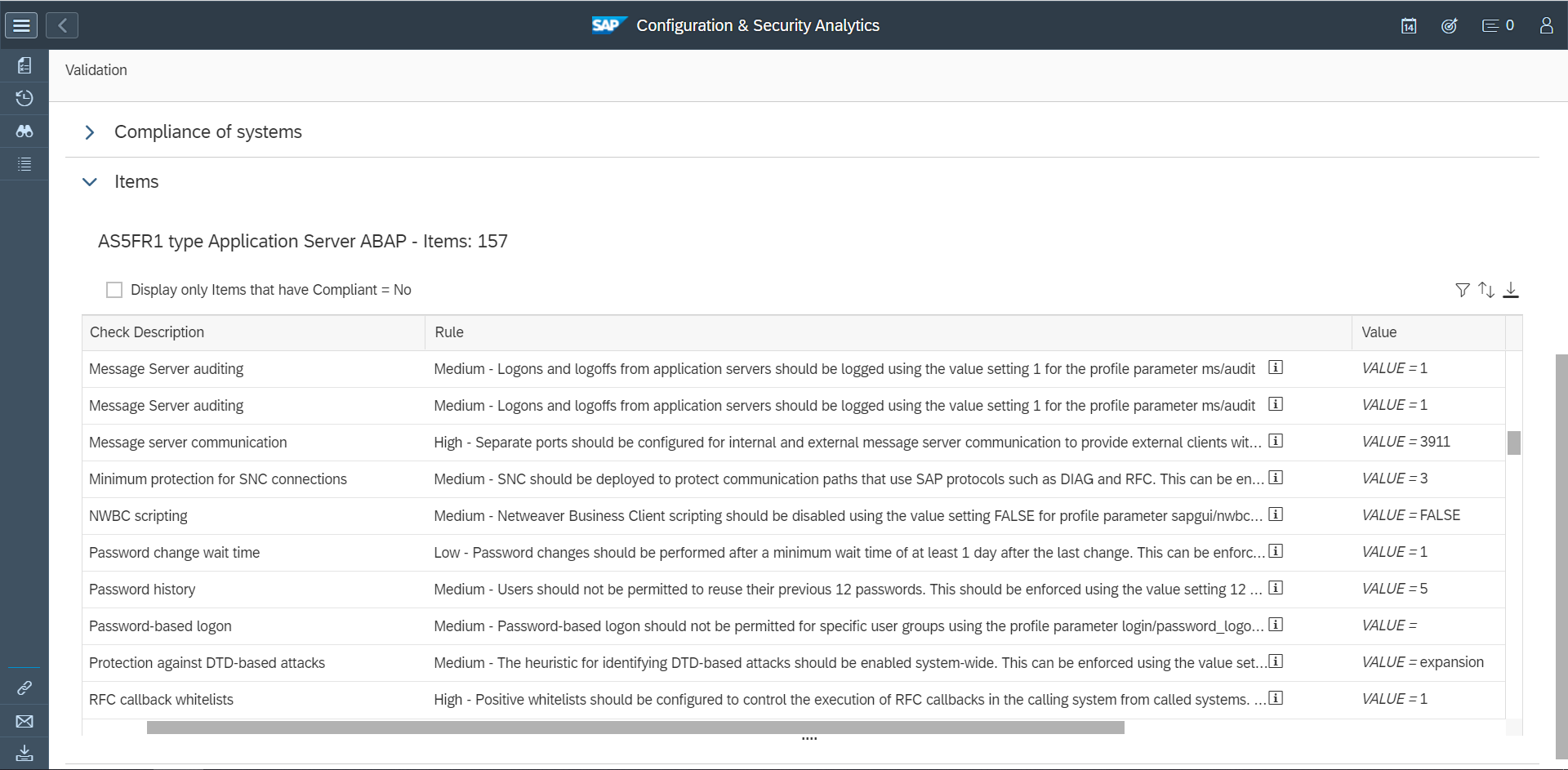
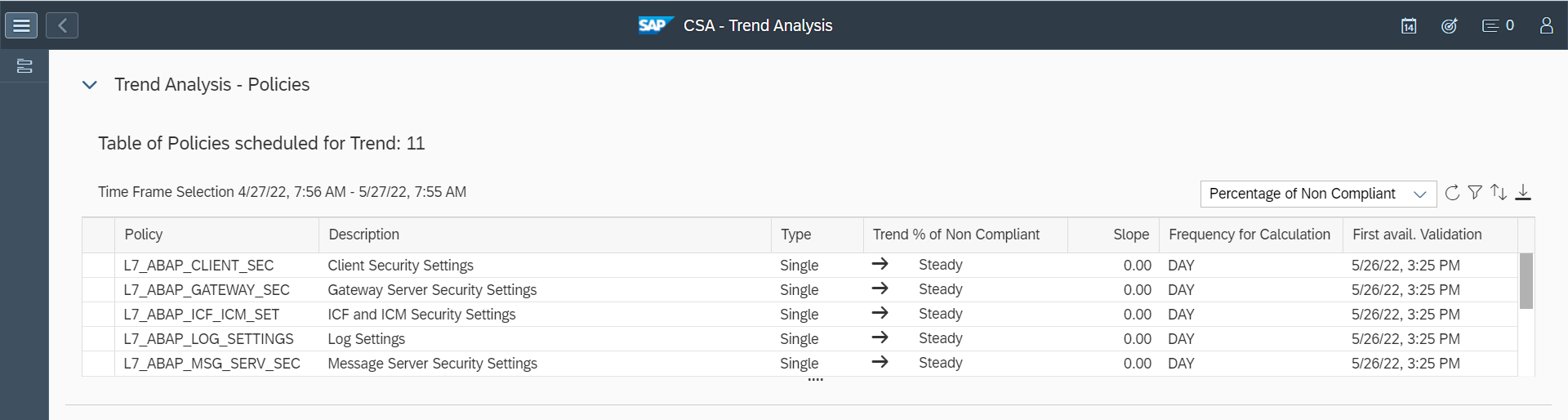
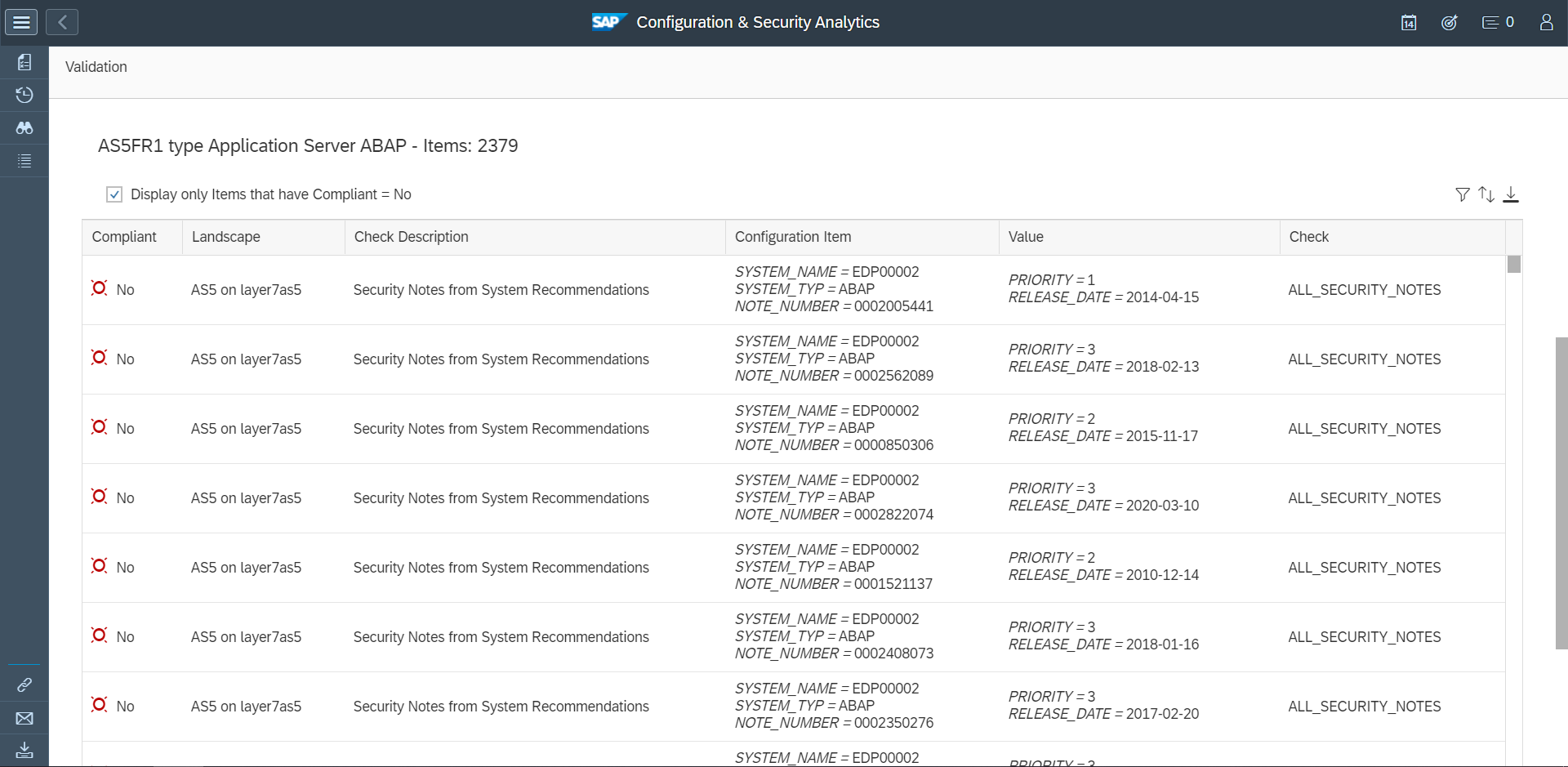
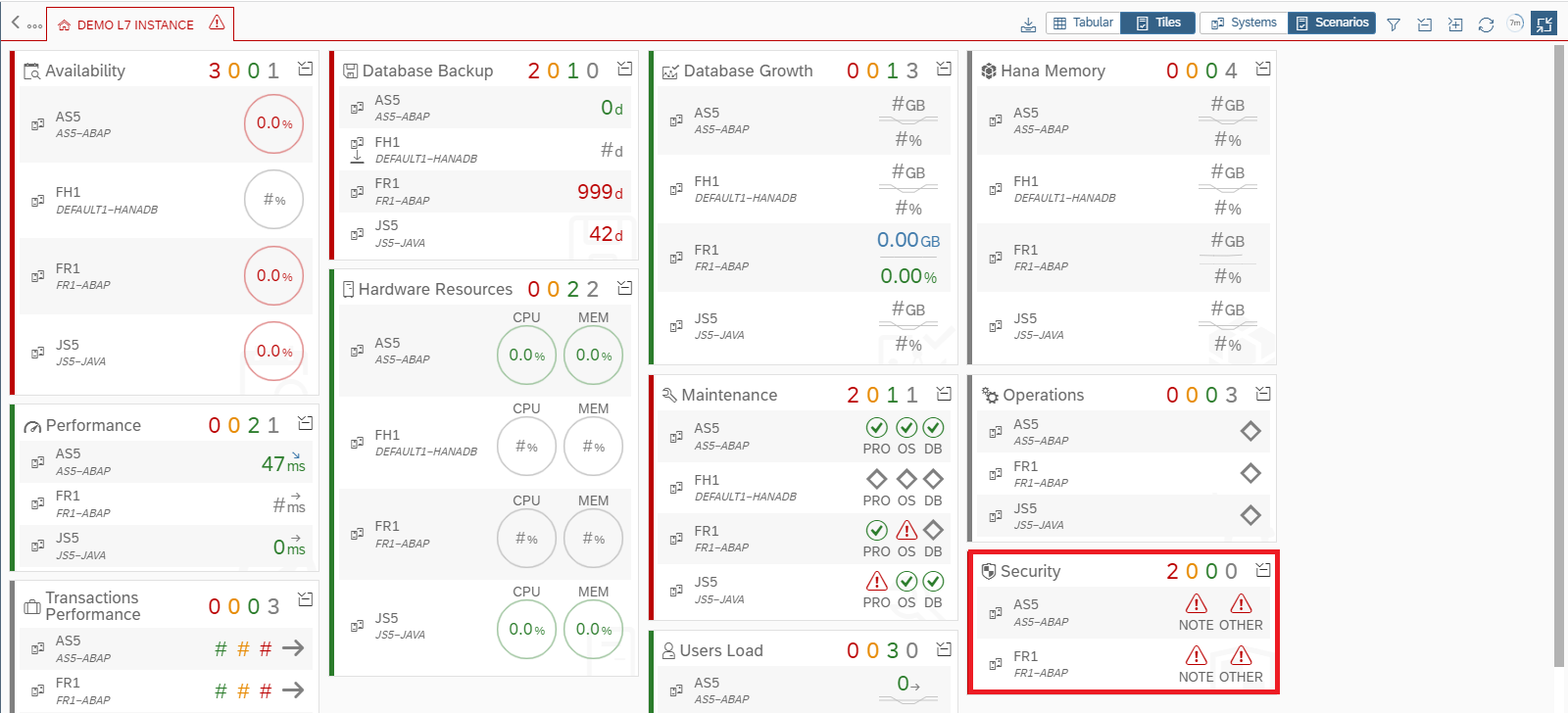
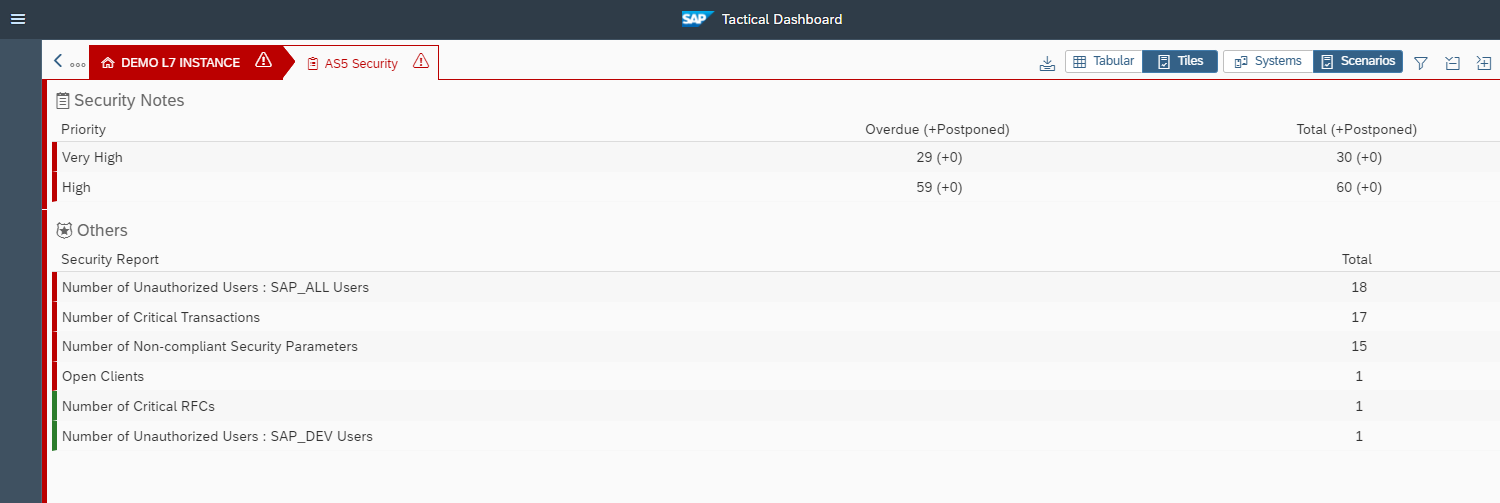
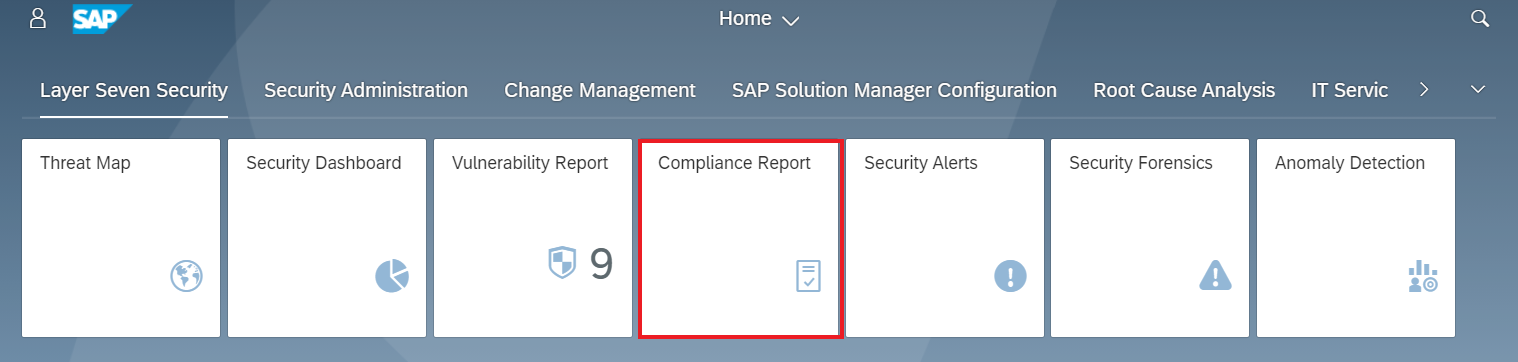
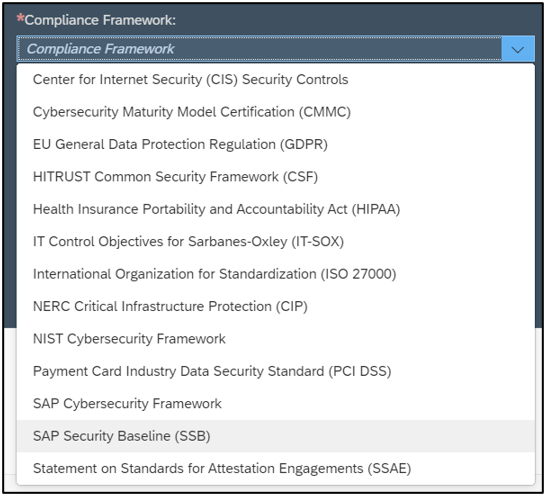
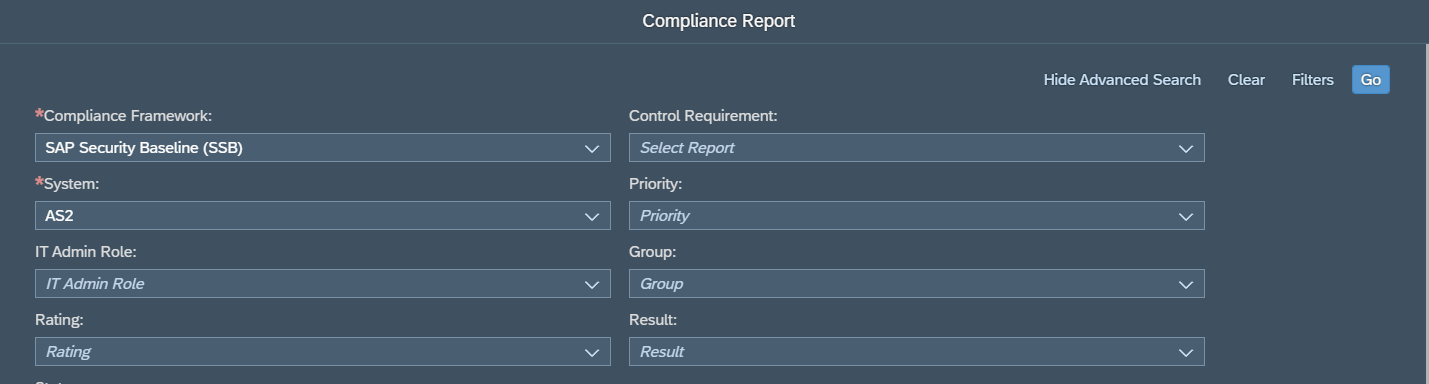
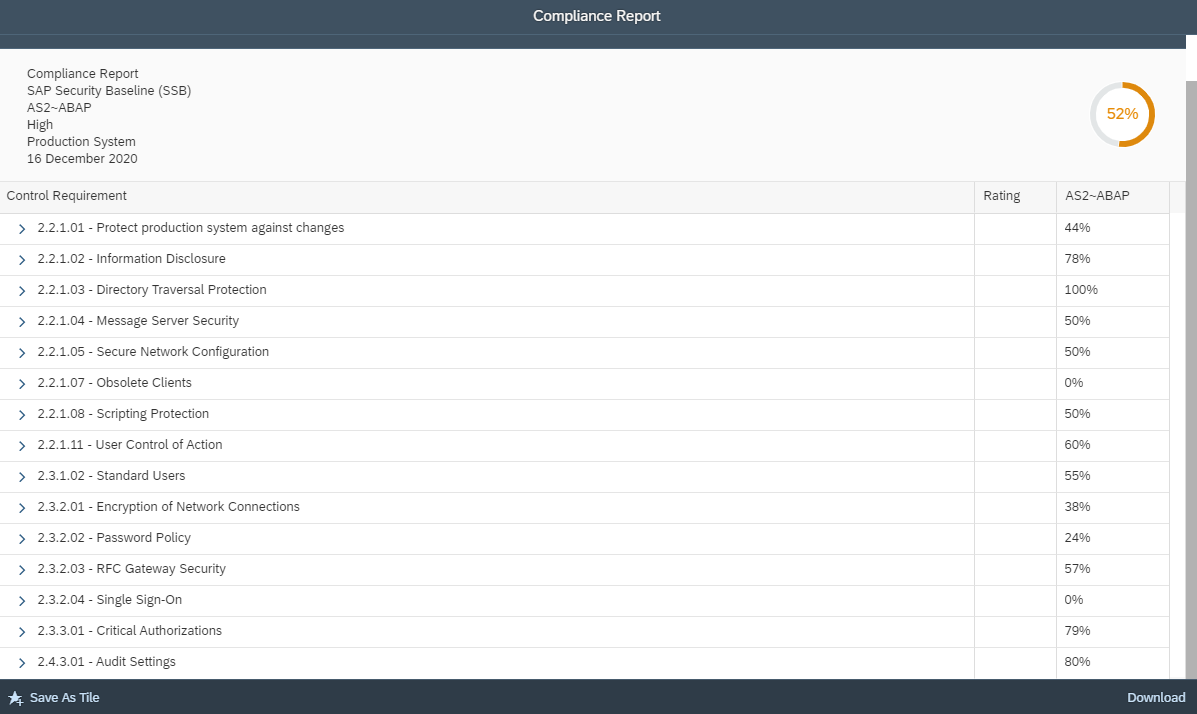
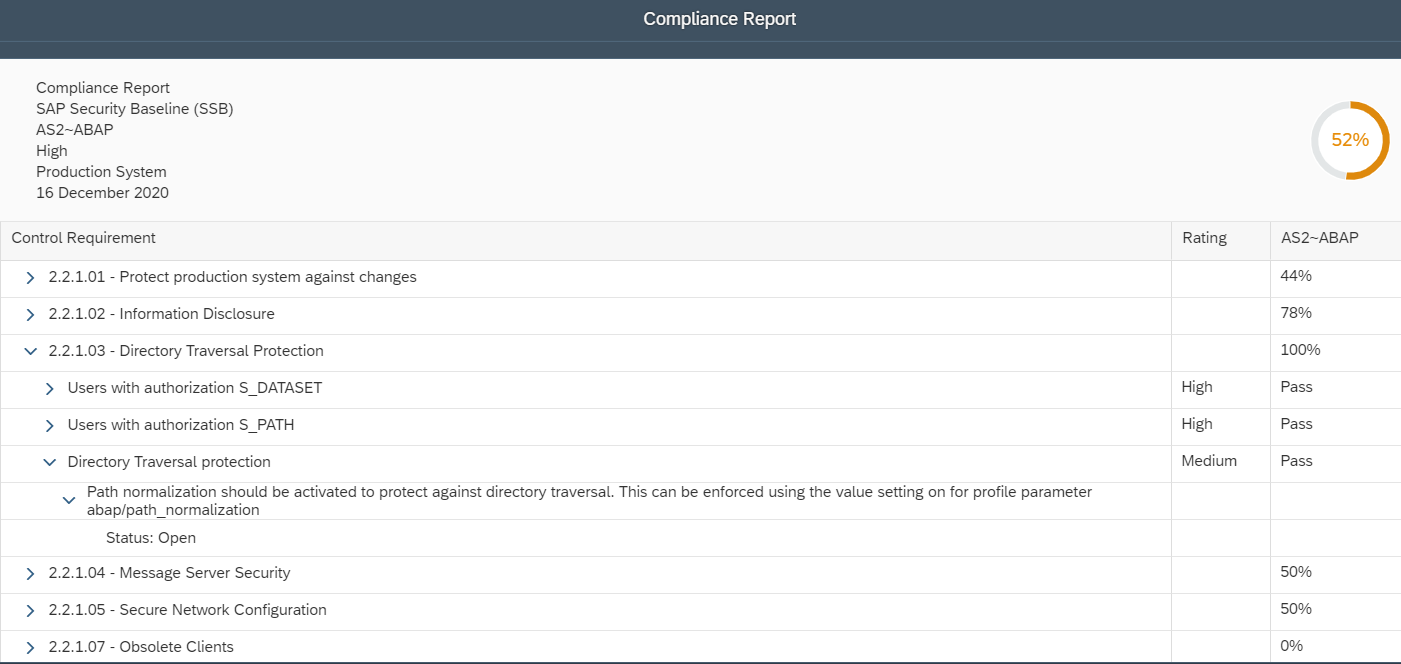
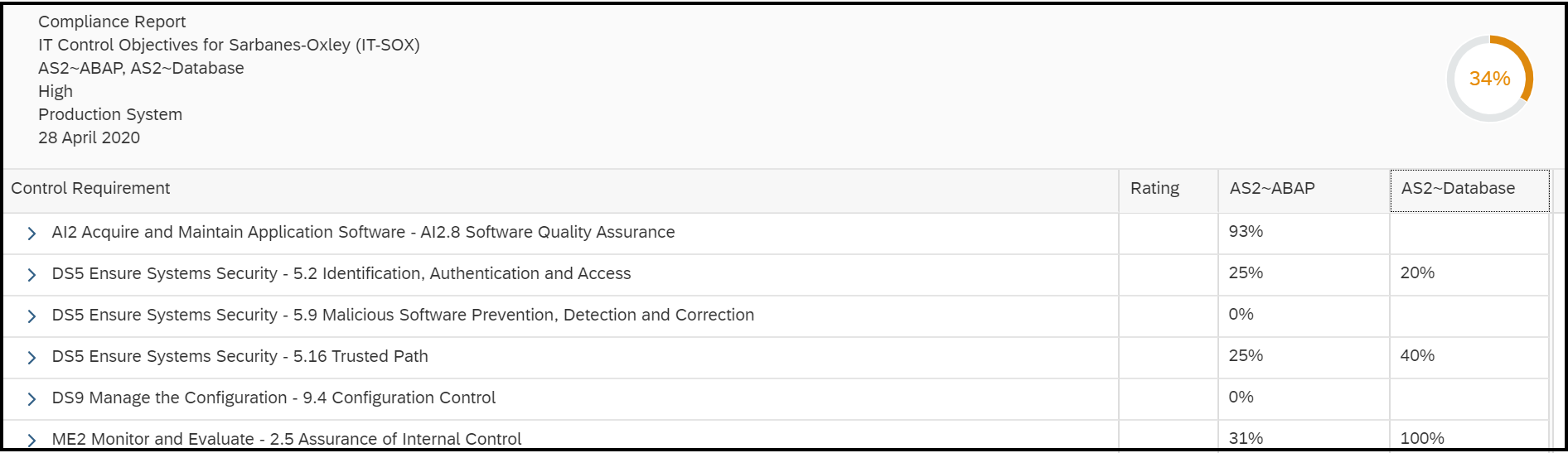
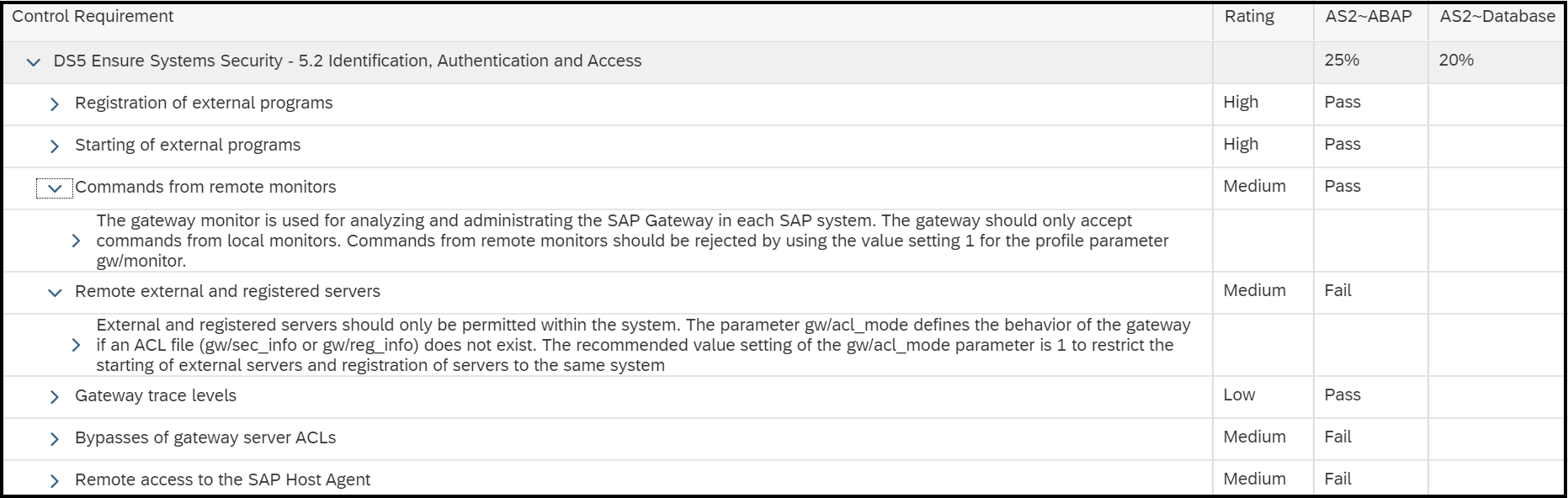
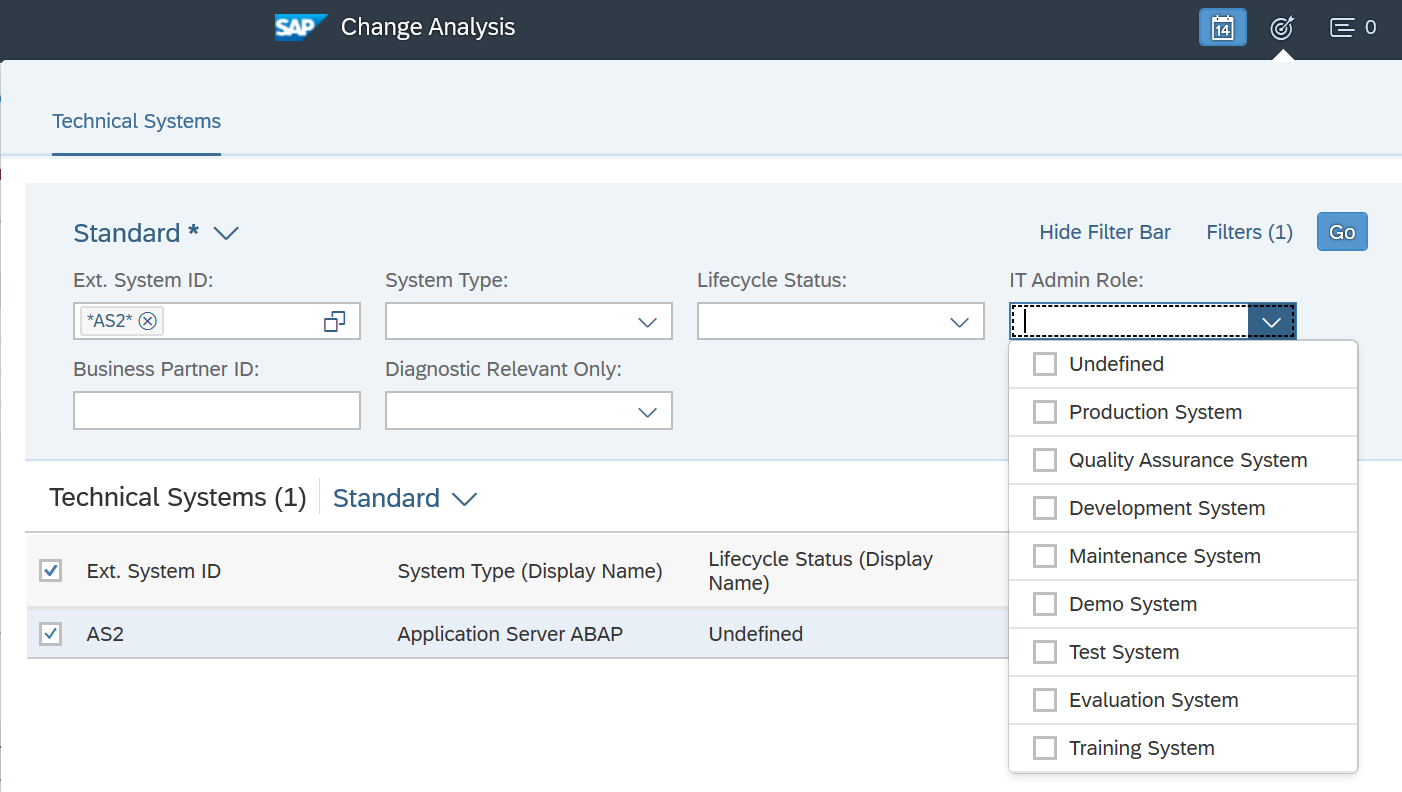
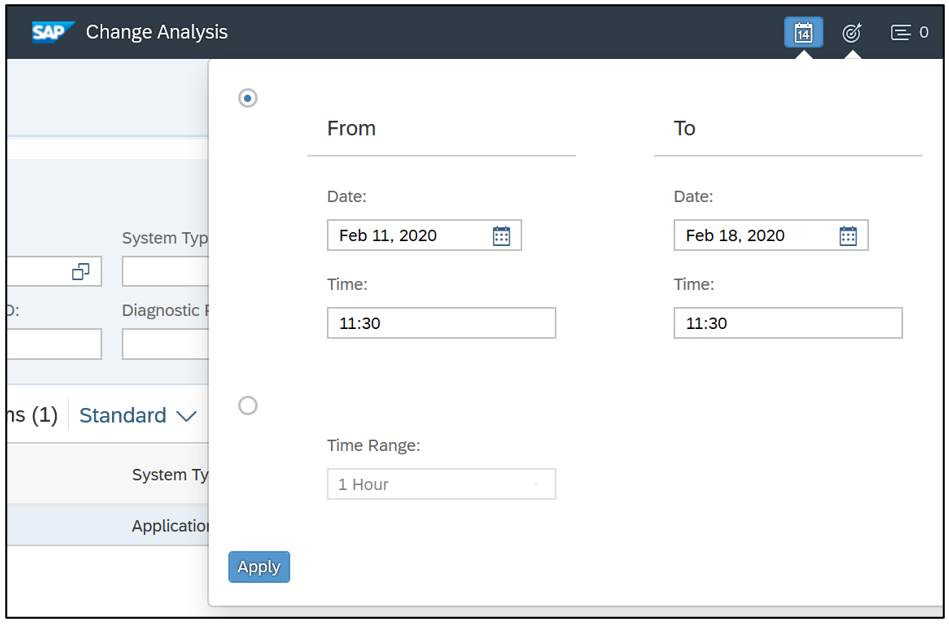
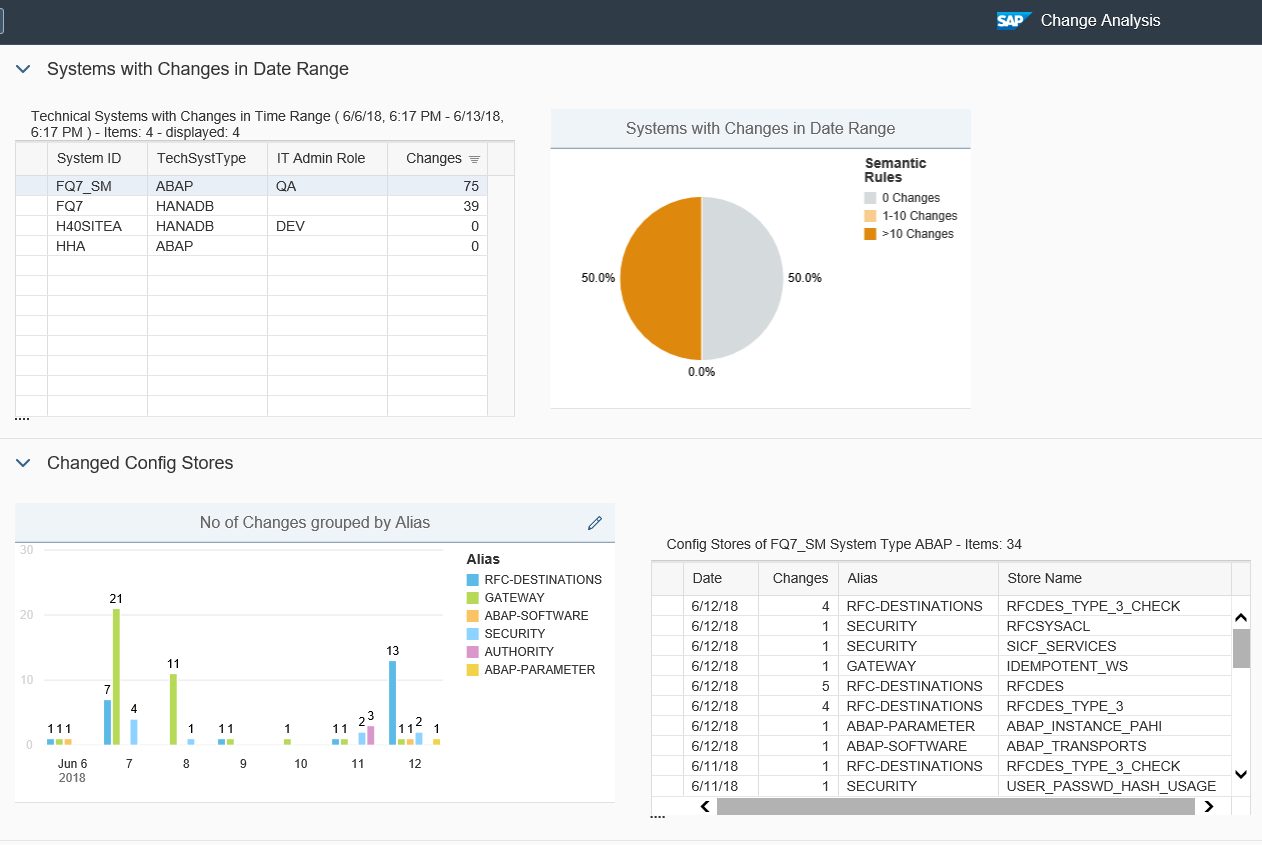
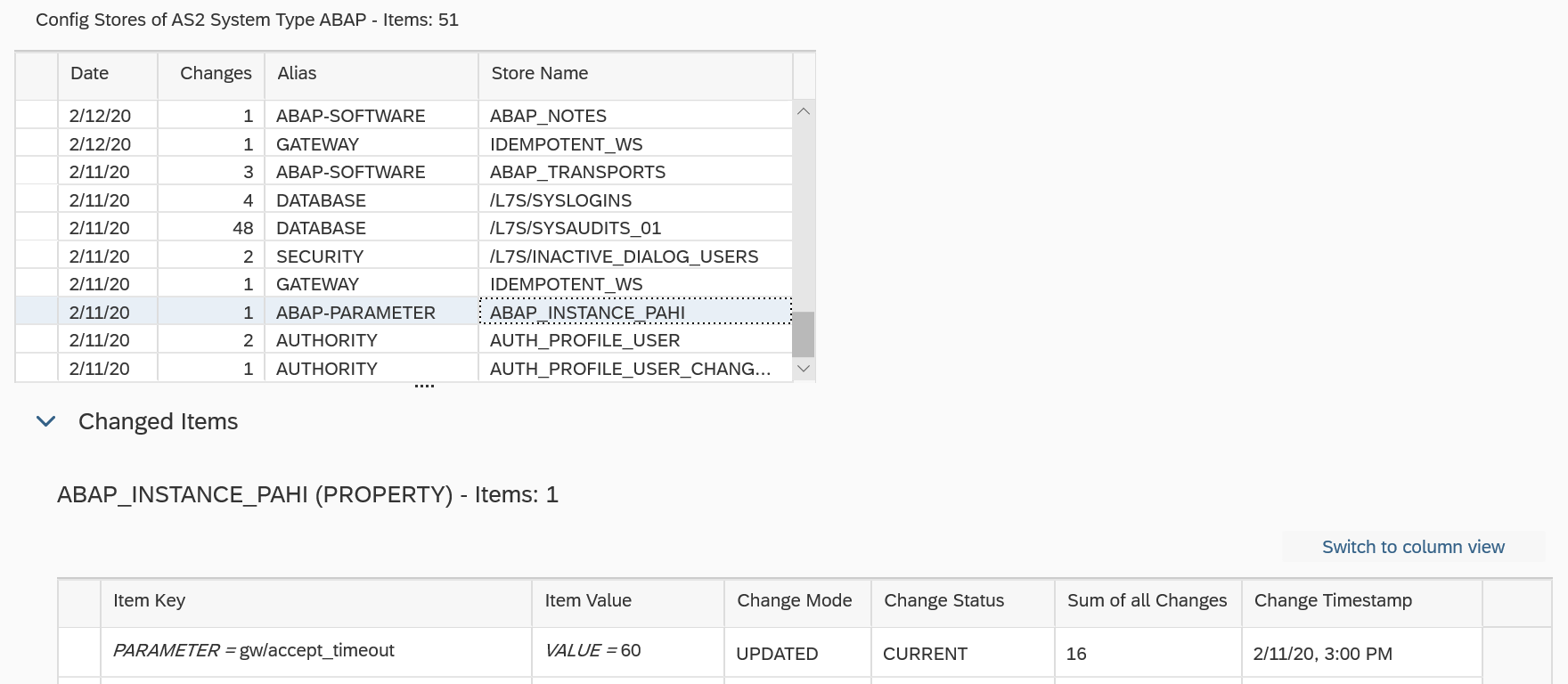
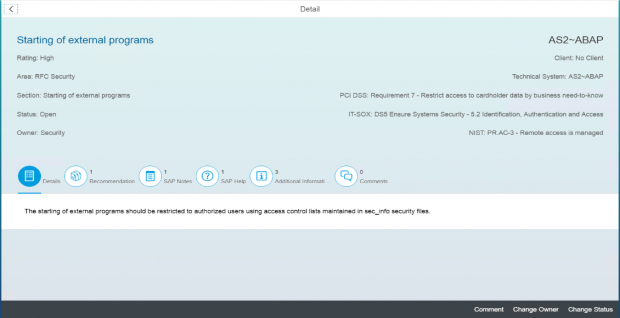
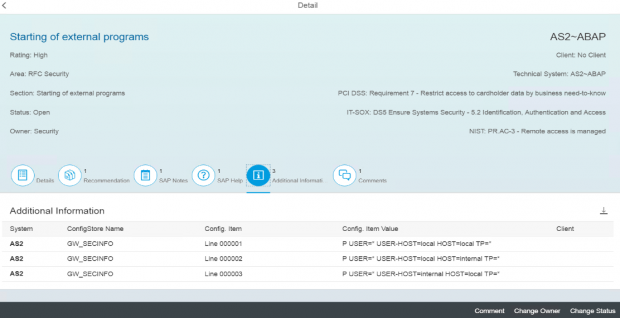
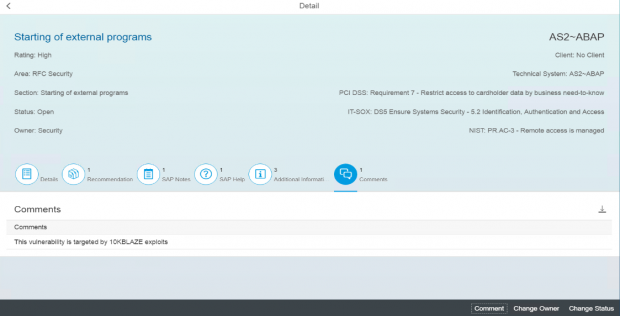
Cybersecurity Extension for SAP
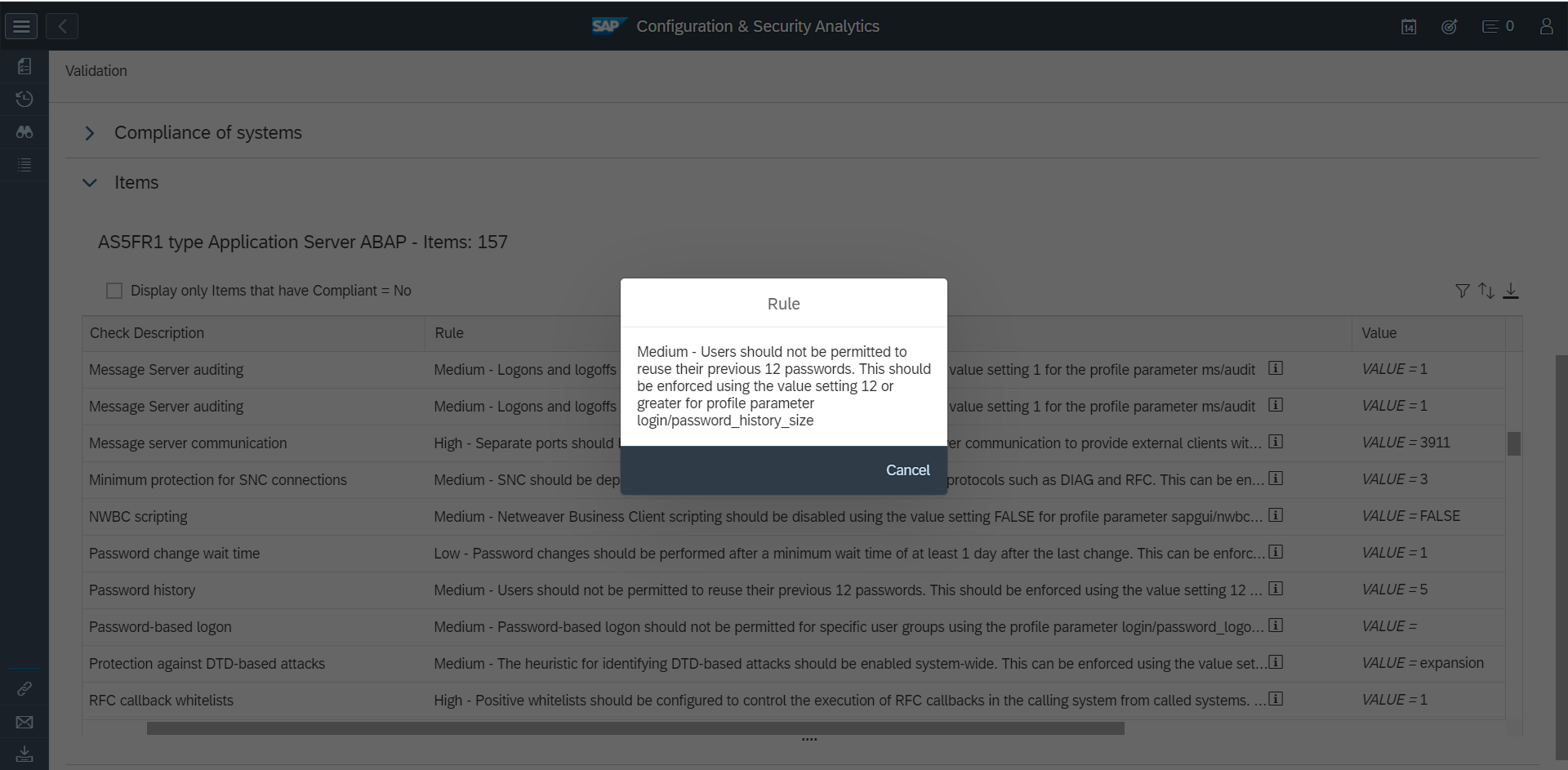
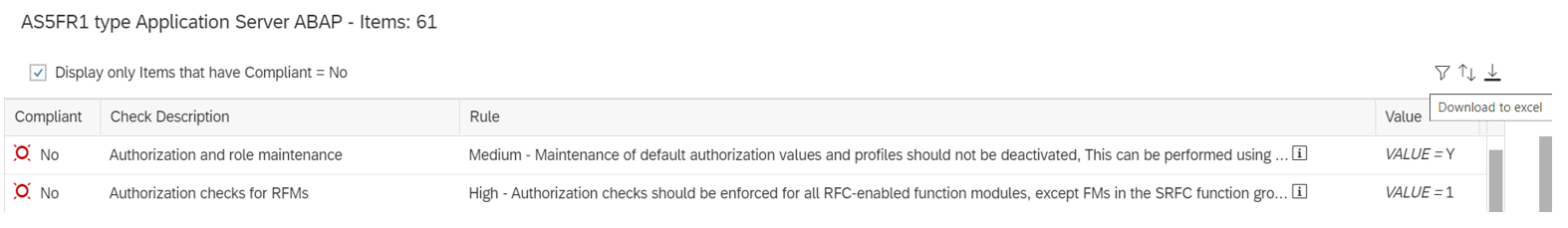
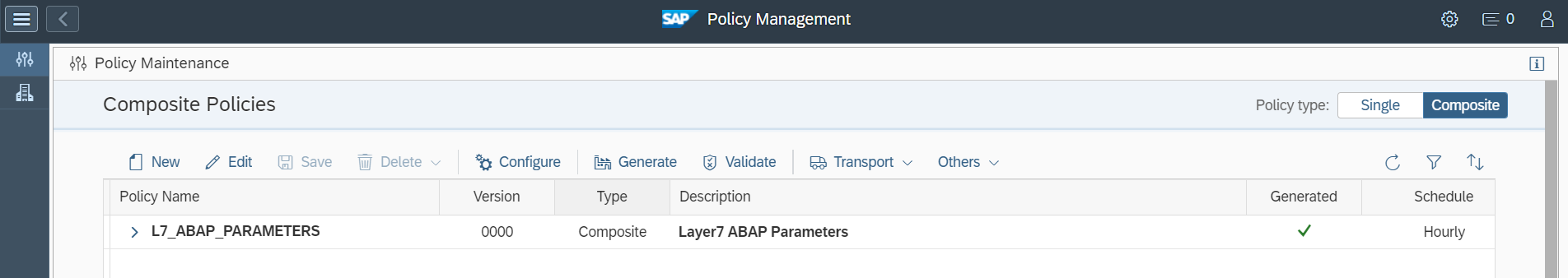
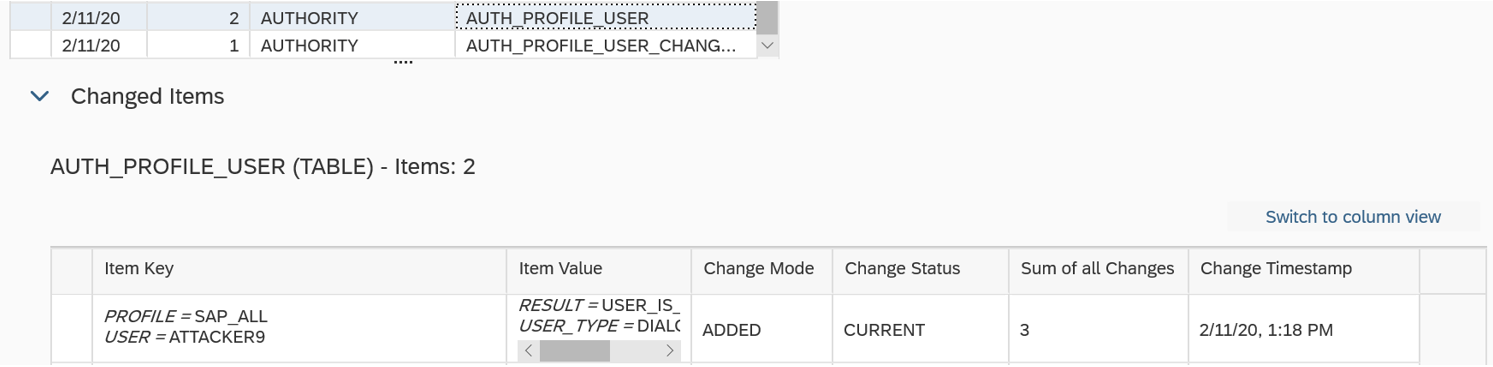
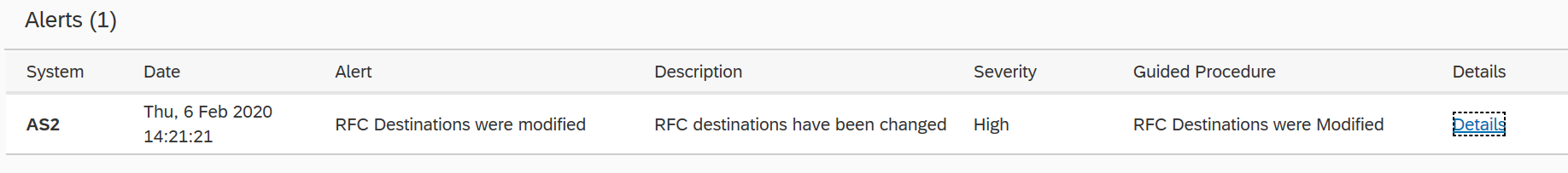
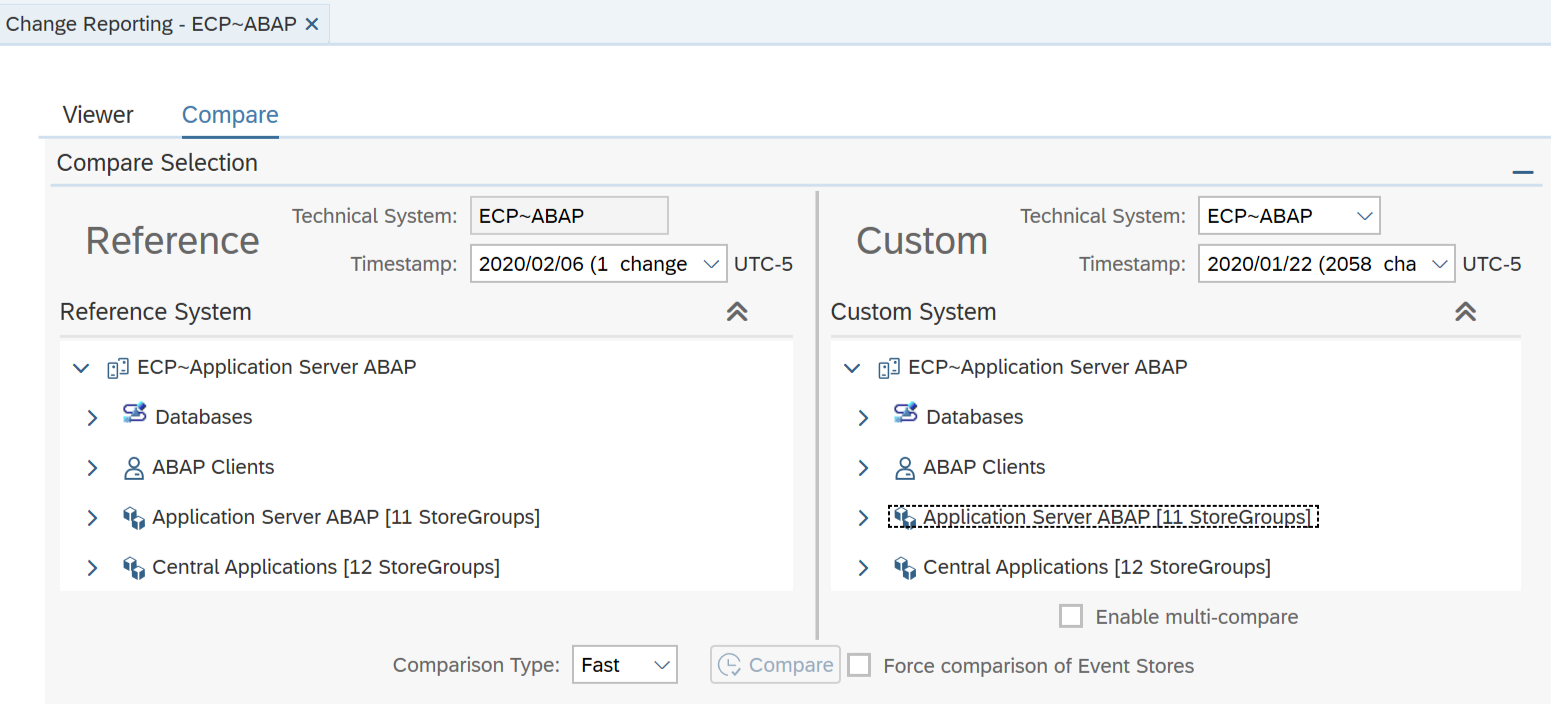
The Cybersecurity Extension for SAP (CES) enables organizations to secure mission-critical SAP solutions from cyber threats that may require public disclosure in accordance with the new SEC rules. CES implements industry-leading vulnerability management, patch management, threat detection and response for SAP to minimize the risk of cybersecurity threats and enable the detection and investigation of security incidents.