10KBLAZE: Secure Your Systems with SAP Solution Manager
On May 2, the Department of Homeland Security issued an alert for SAP customers in response to the disclosure of new exploits targeting vulnerable SAP components. According to some reports, the so-called 10KBLAZE exploits could impact 90% of SAP installations worldwide. The exploits target misconfigurations in the gateway server and message server installed in most SAP systems including S/4HANA, ERP and CRM. The successful execution of the exploits could enable attackers to exfiltrate or modify data and provoke a denial of service without authentication. In other words, attackers can completely compromise target SAP systems without any user credentials.
The new exploits target known vulnerabilities addressed by notes and advisories released by SAP since 2005. Note 821875 details measures to secure the message server, including restricting external access, separating internal and external communications, and maintaining secure access control lists. The profile parameter ms/monitor should be set to 0 to prevent external programs such as msmon from administering the message server at the operating system level. Access to transaction SMMS should also be restricted since the setting can be changed dynamically using the Message Server Monitor within the application server. A separate port for internal communication between application servers should be defined using parameter rdisp/msserv_internal. This will prevent external clients from intercepting or rerouting internal message server communications. The port should not be exposed to clients or intranets. Finally, the parameter ms/acl_info should specify the file containing a restrictive access control list of hosts, domains, IP addresses or subnets for application servers permitted to log on with the message server.
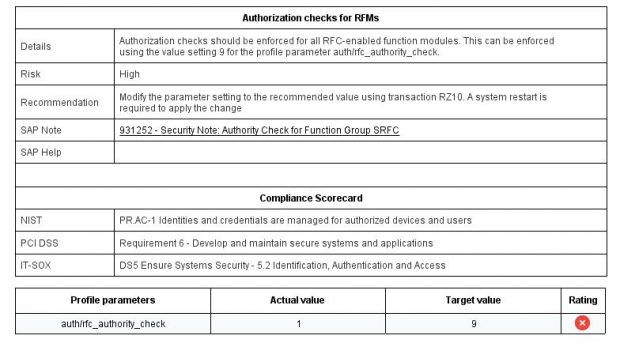
ACLs should also be defined for the gateway server to control access to starting external programs. This can be performed using the gateway security file sec_info. The correct syntax for the file depends on the kernel level. For kernel 7.20 and higher, the setting USER-HOST=LOCAL is recommended to protect against 10KBLAZE exploits. This will allow connections from the same server instance. The setting USER-HOST=INTERNAL could be vulnerable but is required for SID clusters. For detailed guidance, refer to Note 1408081. The ACLs should be supported by the setting gw/acl_mode to 1. This parameter defines the behavior of the gateway server if sec_info does not exist.
Since some 10KBLAZE exploits are targeted at modifying or redirecting data packets, enabling SNC to authenticate and encrypt client-server communications is recommended.
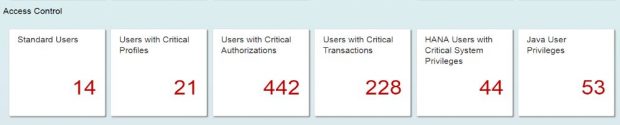
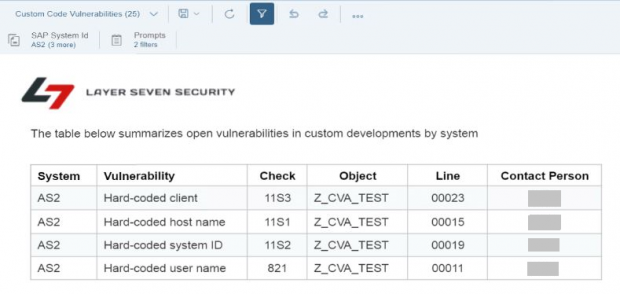
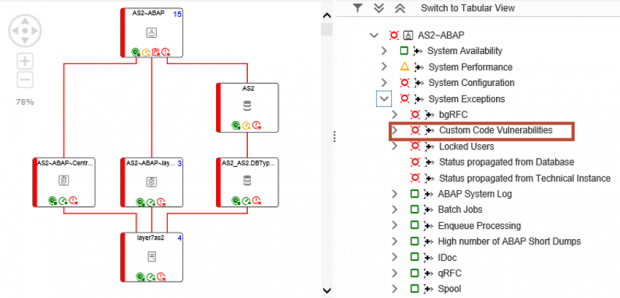
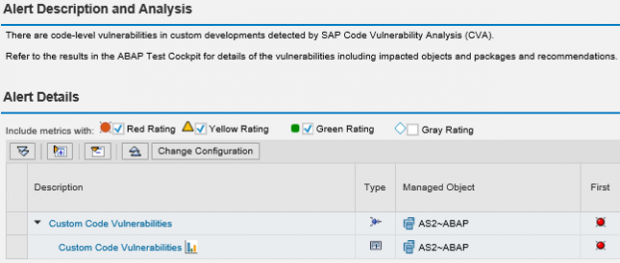
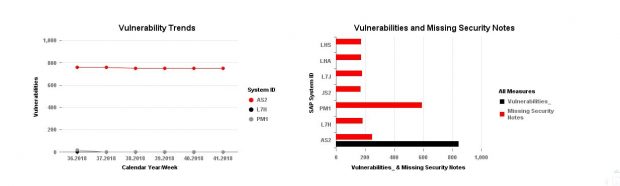
SAP systems vulnerable to 10KBLAZE exploits can be discovered using SAP Solution Manager. The Cybersecurity Extension for SAP Solution Manager automatically monitors security settings for the message server and gateway server including profile parameter settings, access control lists and users with critical transactions such as SMMS. The extension also monitors message and gateway logs for external monitor commands, successful and unsuccessful program starts, and other events. Alerts are triggered by the extension for suspected exploits.
The example below illustrates how you can discover insecure sec_info entries that could expose systems to 10KBLAZE exploits.
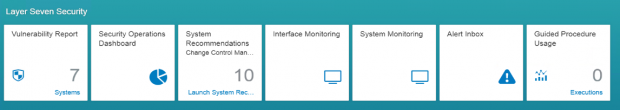
Click on Vulnerability Report in the Fiori Launchpad.
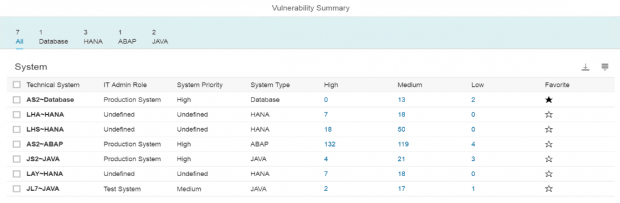
Filter by ABAP systems, select the check-box for the target system and click on Display.
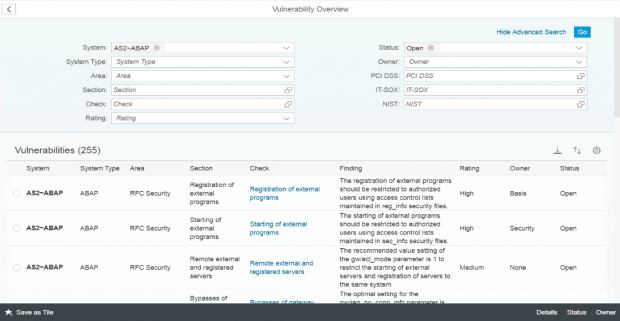
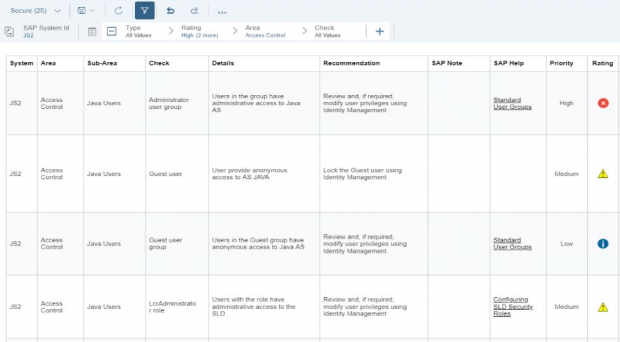
Filter for vulnerabilities in open status within the area of RFC Security. Click on the check for starting of external programs.
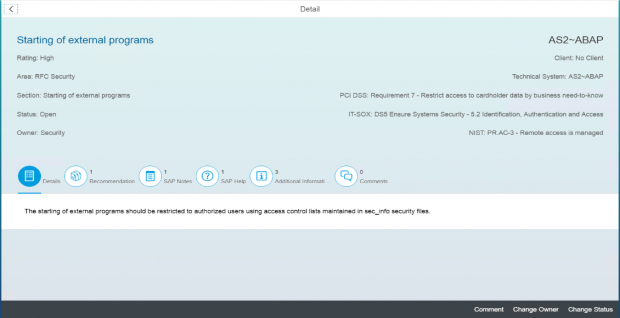
Review the details and recommendation. Click on the linked SAP Notes and SAP Help.
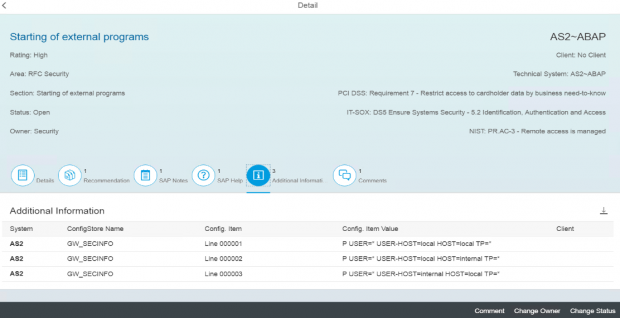
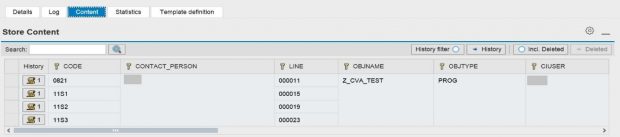
Click on Additional Information to review the insecure entries in the sec_info ACL.
Focus on entries with the setting USER-HOST=internal.
Click on the download icon to export the current settings.
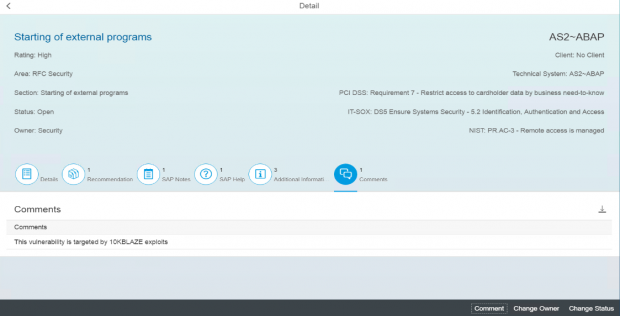
If required, add comments in the Comment section.
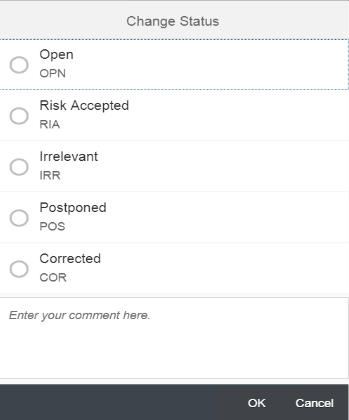
The finding for the system will be automatically removed from the report once the sec_info entries are updated. However, you can manually change the status using the Change Status option. Note that status changes are tracked in the extension.
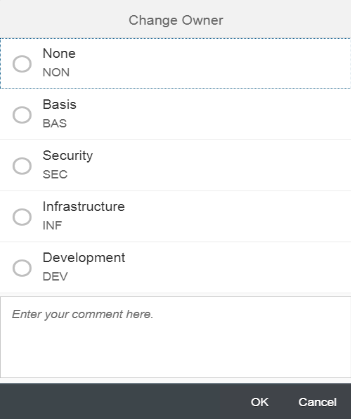
You can also assign responsibility for remediating the finding to specific groups using the Change Owner option.