SAP Zero Day Vulnerability CVE-2025-31324 / Security Note 3594142
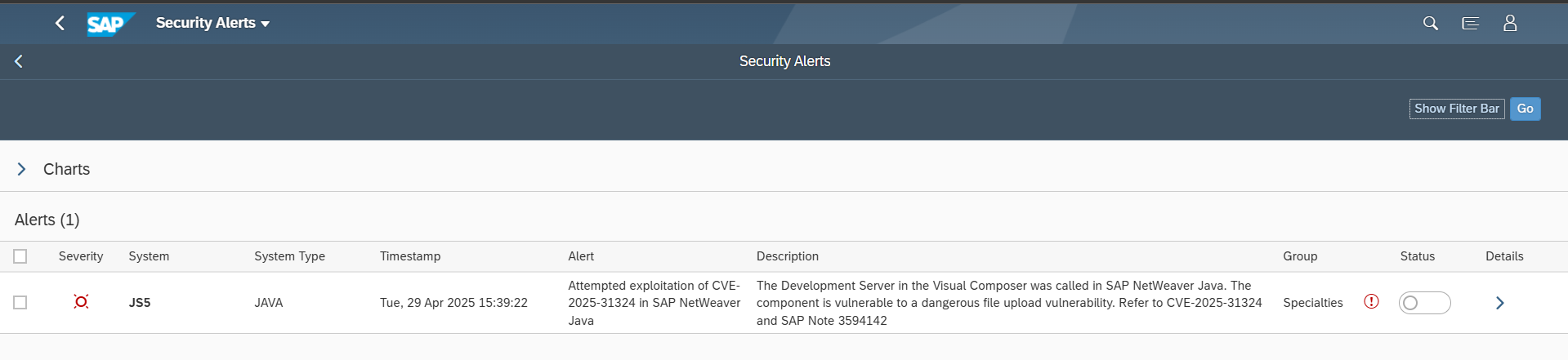
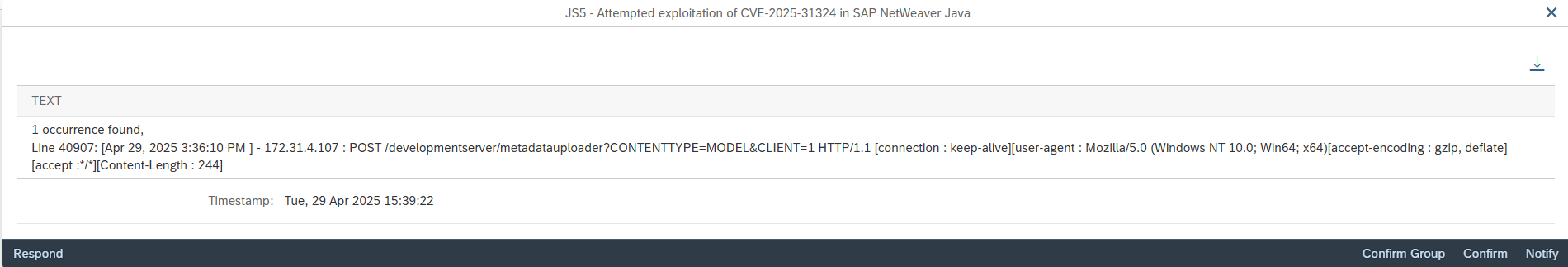
On April 22, ReliaQuest released details of a zero-day vulnerability that the company discovered during investigations into customer incidents involving the upload and execution of malicious files in SAP NetWeaver Java systems. According to the findings of the investigation, threat actors were able to take full control of the target systems by exploiting a vulnerability in the Metadata Uploader endpoint within the Development Server of the Visual Composer component in SAP NetWeaver Java. The exploitation involved specific POST requests that led to the installation of JSP webshell files in the directory j2ee/cluster/apps/sap.com/irj/servletjsp/irj/root/. The webshells enabled threat actors to execute remote commands and obtain full control of SAP systems using the privileges of the SAP operating system user <SID>ADM.
The vulnerability was reported to SAP by ReliaQuest. SAP disclosed the vulnerability as CVE-2025-31324 on April 24 and released a patch in security note 3594142. The CVSS score for the CVE is 10/10 and the security note is rated hot news. The patch applies authentication and authorization to prevent unauthorized access and file upload.
Security note 3594142 provides an automated correction for version 7.50 of the Visual Composer Framework in NetWeaver Java systems. In accordance with the general SAP maintenance strategy, patches are only provided for support packages released within the last 24 months. Please refer to the SAP 24-Month Rule for SAP Security Patching for more information regarding the strategy. Versions 7.0-7.40 of SAP NetWeaver Java are no longer maintained by SAP. Mainstream maintenance for version 7.50 is available until the end of 2027. Extended maintenance will be offered until the end of 2030.
Visual Composer is available in all 7.x versions of SAP NetWeaver Java. Manual instructions are provided for versions lower than 7.50 in KBA 3593336. The recommended solution is to remove the vulnerable component by following the instructions in option 0 of the KBA. If the component is required, you can block access to the Development Server of the Visual Composer using either Access Control Lists (ACLs) defined for the Internet Communication Manager (ICM) or URL restrictions implemented using firewall rules.
Layer Seven Security has released an update for the Cybersecurity Extension for SAP to enable the detection of attempted and successful exploitation of CVE-2025-31324 in SAP NetWeaver Java Systems. This includes POST requests to the vulnerable component and discovering the presence of malicious files in target directories. The solution also checks version information for SAP NetWeaver Java to ensure systems are able to apply automated corrections from SAP rather than manual workarounds.