Database Security with the Cybersecurity Extension for SAP
Protecting SAP systems against cyber threats requires integrated measures applied not just within the SAP layer but across the technology stack including network, operating system, and database components. As repositories of business-critical and sensitive information, databases warrant specific attention for hardening and monitoring efforts. This includes identifying and addressing configuration weaknesses, excessive privileges, and weak audit policies, encrypting data in transit and at rest, removing vulnerable stored procedures, and detecting and responding to privilege abuse or escalations.
SAP Solution Manager is uniquely positioned to monitor the security of SAP databases given its deep connectivity into SAP platforms. This article outlines the architecture and data collection procedures for database monitoring with Solution Manager. Next month’s article will explore database-level security reporting and event monitoring with SolMan.
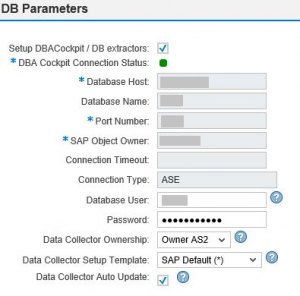
Establishing connectivity to databases supporting SAP systems is a standard step during the mandatory configuration procedures for Solution Manager. Connection information is entered into the DB Parameters section during the Enter System Parameters step of Managed System Configuration. This includes the database host, port, and user credentials.
The connection supports the DBA Cockpit for database administration and monitoring. It also supports database extractors used by the Extractor Framework. The Extractor Framework performs data collection and distribution for monitoring and alerting in Solution Manager. The framework operates regular extractors to snapshot configuration, user, system, change and event-related data from systems. The snapshots are stored in areas such as the SolMan Configuration and Change Database (CCDB) and queried by other applications in SolMan including Configuration Validation and the Monitoring and Alerting Infrastructure (MAI). The concept of running or scheduling security scans is foreign in Solution Manager. Periodic jobs run the extractors to refresh the data. Therefore, there is no need to schedule scans or connect directly to systems to compile data when reviewing security-related information. Job Monitoring in Solution Manager can be used to monitor the relevant jobs and alert for job errors or warnings.
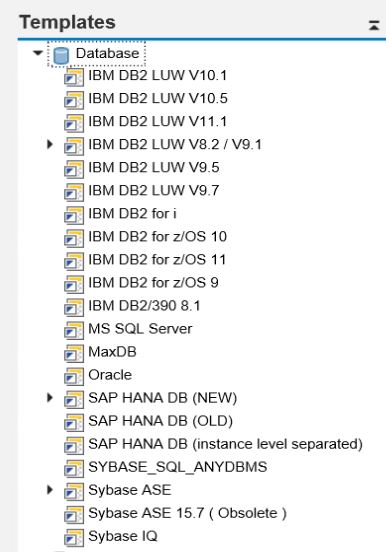
Solution Manager automatically applies preconfigured templates for databases once they are successfully connected for monitoring. SolMan installations are packaged with templates for all platforms supported by SAP systems including SAP databases such as HANA, Sybase and MaxDB, and third-party databases from Oracle, IBM and Microsoft. Template contents can vary based on the specific version and release of databases.
Templates for HANA platforms including metrics and alerts for monitoring system availability, performance and security. They also include CCDB stores to extract current values for HANA parameters, and details of active users, audit policies and users with critical database and system privileges.
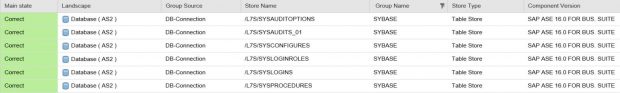
The extractor framework and SAP-delivered templates may not provide coverage for monitoring all the security-related areas for each database platform. Therefore, customers or partners can either define their own templates or create/ modify extractors, metrics, alerts and CCDB stores to extract additional data. In the example below, we’ve added several custom stores to extract and query data for Sybase ASE that is not available in a standard Solution Manager installation. This includes runtime values for all Sybase parameters, active users, roles assigned to database users, enabled stored procedures, audit settings, and database event logs with event IDs, user IDs, and timestamps.
The stores are assigned to the custom /L7S/ namespace to avoid any conflict with SAP and other namespaces.
The extractor framework regularly refreshes the data through background jobs. Database security policies are then applied by Solution Manager against the CCDB to identify vulnerabilities and security-related events in the platform. The data is also monitored by the MAI which triggers alerts and notifications for critical risks. The results are replicated to an internal Business Warehouse (BW) in Solution Manager.
In next month’s article, we will discuss how you can use Service Level Reporting and BusinessObjects to create detailed and user-freindly reports to convey the results of database security monitoring with SAP Solution Manager.