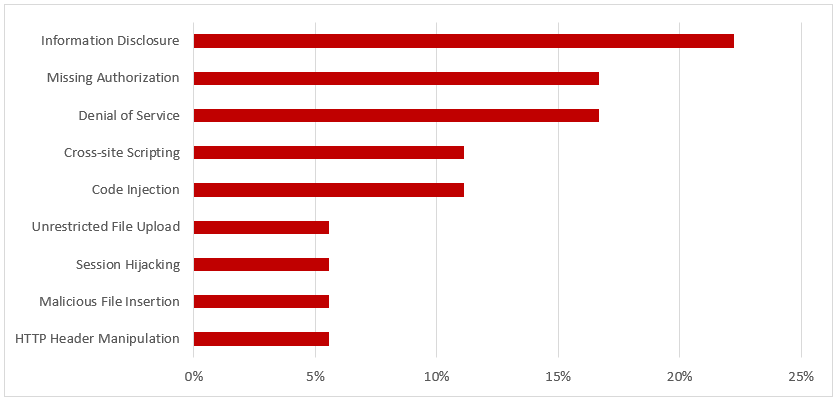
SAP Security Notes, July 2018
Notes 2017041 and 2016974 patch high-risk information disclosure vulnerabilities in SAP Environment, Health & Safety Management (EHSM). The vulnerabilities could be exploited to leak sensitive information stored or processed by the transactional Fiori apps Inspect Safety Controls and Retrieve Safety Information. The apps support the performance and tracking of safety control inspections.
Note 2641674 provides corrections to support virus scanning for OData v2 connections in the SAP Gateway using the SAP Virus Scan Interface (VSI). This will protect against the insertion of untrusted files and malware.
Note 2597913 includes a kernel patch to remove a Denial of Service vulnerability in the SAP Gateway that could enable attackers to provoke resource exhaustion by flooding specific services. The relatively low CVSS score for the note is misleading. Exploitation of the vulnerability requires network-level access only and does not require any privileges in the system. Furthermore, the impact in terms of system availability is high.
Note 2622434 removes passwords in route strings that are forwarded from one SAProuter to another. Route strings define permitted connections, users and services between hosts. The leakage of passwords could lead to targeted attacks against the SAProuter.
Finally, Note 2664767 removes the logging of sensitive data in logs for SAP Dynamic Authorization Management (DAM) by NextLabs. DAM supports attribte or policy-bsed control to manage user privileges.