Three Reasons You Should Budget for SAP Breach Costs
The average cost of a data breach has now surpassed $4 million. This is according to the latest study from the Ponemon Institute issued earlier this month. The study surveyed 383 organizations in 12 countries. It revealed that not only are data breach costs increasingly across the board, the probability that organizations will suffer a breach impacting 10,000 or more records is 25 percent.
The global results mask significant differences between countries and industries. For example, average data breach costs are highest in the U.S ($7M) and sectors such as healthcare, education and financial services. However, regardless of country or industry, the majority of breaches (48%) are caused by cyber attacks rather than human error or system glitches.
The results of the Ponemon study are contested by the report Beneath the Surface of a Cyberattack from Deloitte Advisory. According to the report, actual costs are far higher than indicated by the Ponemon study which focuses upon measuring direct and tangible costs for breach notification, forensic investigations, legal fees, public relations, regulatory fines and other areas. Deloitte estimate that such costs account for less than 5% of the total business impact of data breaches. The strategic impact of breaches in terms of increased insurance premiums, loss of intellectual property, reputational harm and other hidden costs is far higher than the direct impact. This is illustrated by a breach of patient records experienced by a healthcare company cited in the report. Only 3.5% of the $1.6 billion lost by the company as a result of the breach was associated with direct costs.
Both of the studies echo the results of an earlier report from the Ponemon Institute that placed the average cost of data breaches impacting SAP systems at $4.5M. The report also revealed that 65% of companies had experienced one or more SAP breach within the last 2 years. The significant impact of data breaches and the likelihood that organisations will experience a breach if they haven’t already done so suggests that breach costs should be planned and budgeted. However, aside from region, sector and other factors, there are three reasons that could negatively impact the extent your organization budgets for SAP breach costs. The reasons are outlined below.
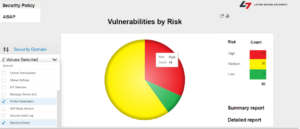
1. You do not effectively identify, prioritize and apply security patches for SAP systems
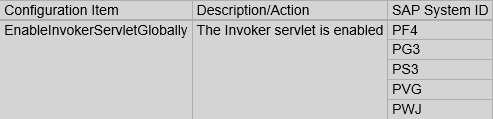
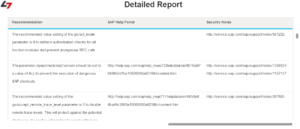
The majority of exploits for SAP systems do not target zero-day vulnerabilities. Most exploits focus upon long-standing and well-known vulnerabilities that can be removed by regularly upgrading SAP systems and applying Security Notes provided by SAP. A case in point is the invoker servlet vulnerability addressed by the recent alert issued by US-CERT. This vulnerability was disclosed in 2010 and addressed by several Notes issued by SAP in the same year.
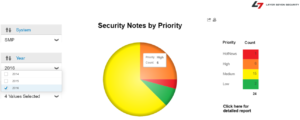
2. You do not effectively manage vulnerabilities in SAP systems
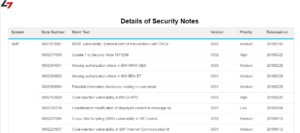
SAP systems can present a wide attack surface to attackers if they are poorly configured and monitored. A comprehensive vulnerability management program for SAP systems should include continuously monitoring and removing vulnerabilities in areas such as remote function calls, gateway servers, message servers, client-server and server-to-server communication, password policies, session management, audit settings, ICF services, UME settings, Java services and user privileges.
3. You do not effectively discover and respond to malicious events in SAP systems
SAP systems include a wide array of logs that should be continually monitored for indicators of a potential attack. This includes events such as logons or attempted logons with standard users, changes to RFC destinations, ICF services or global settings, trusted system logons, RFC callbacks, path traversals and suspected XSRF attacks. Alerts for such events should be triggered and automatically transmitted to incident response teams to ensure attacks are blocked and contained.
Customers that implement strong patch, vulnerability and threat management programs for SAP systems can justifiably budget far less for SAP breach costs that those that do not by reducing both the likelihood and impact of a potential breach. In fact, they may be able to remove the need to budget for breach costs altogether and rely upon on cyber insurance by satisfying the due diligence requirements of cyber insurance policies.
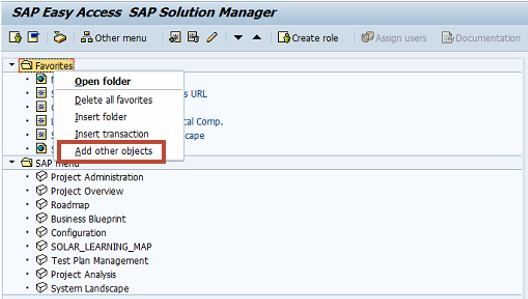
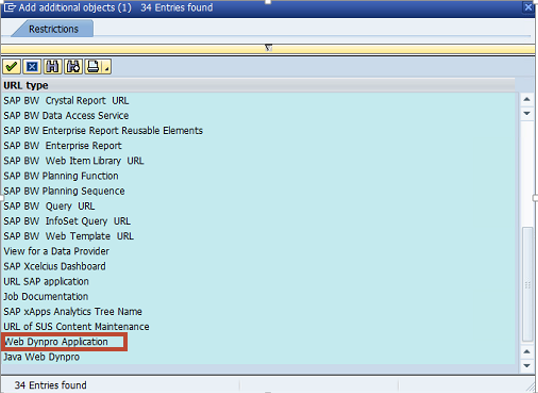
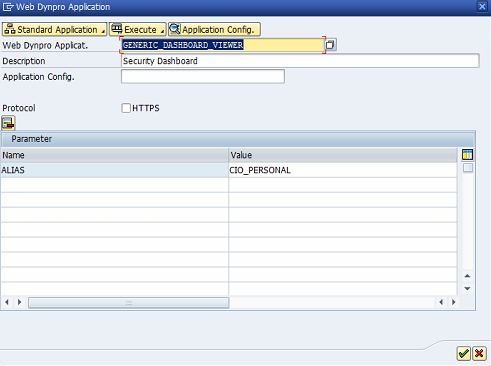
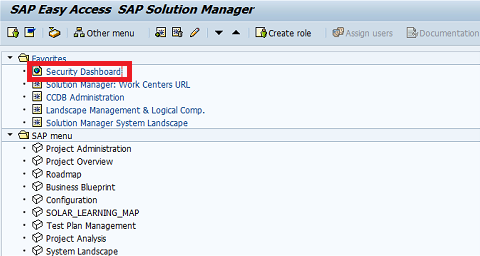
Customers that haven’t Implemented patch, vulnerability and threat management capabilities can address the gap by leveraging standard tools available in SAP Solution Manager without licencing third party software. This includes System Recommendations for patch management, Configuration Validation for vulnerability management and E2E Alerting for threat management. Layer Seven Security empower customers to unlock the capabilities of SAP Solution Manager for automated vulnerability scanning and security alerting. To learn more, contact Layer Seven Security.