Workarounds for SAP Security Notes
Corrections for Common Vulnerabilities and Exposures (CVEs) impacting SAP solutions are delivered via patch day notes and support packages released through the SAP Support Portal. In most cases, the corrections include automated fixes that are applied as updates or upgrades for impacted software components. Applying the automated fixes is the preferred method for addressing SAP CVEs. However, in some cases, it may not be possible to apply an automated fix. The corrections may have adverse side effects such as disabling or removing required services, programs or features. There may also be challenges related to applying prerequisite notes required to implement corrections. Corrections may require extensive testing or downtime, and it may not be possible to allocate the resources or schedule maintenance windows. Lastly, customers may not have access to corrections if, for example, their SAP solutions are supported and maintained by third parties instead of SAP.
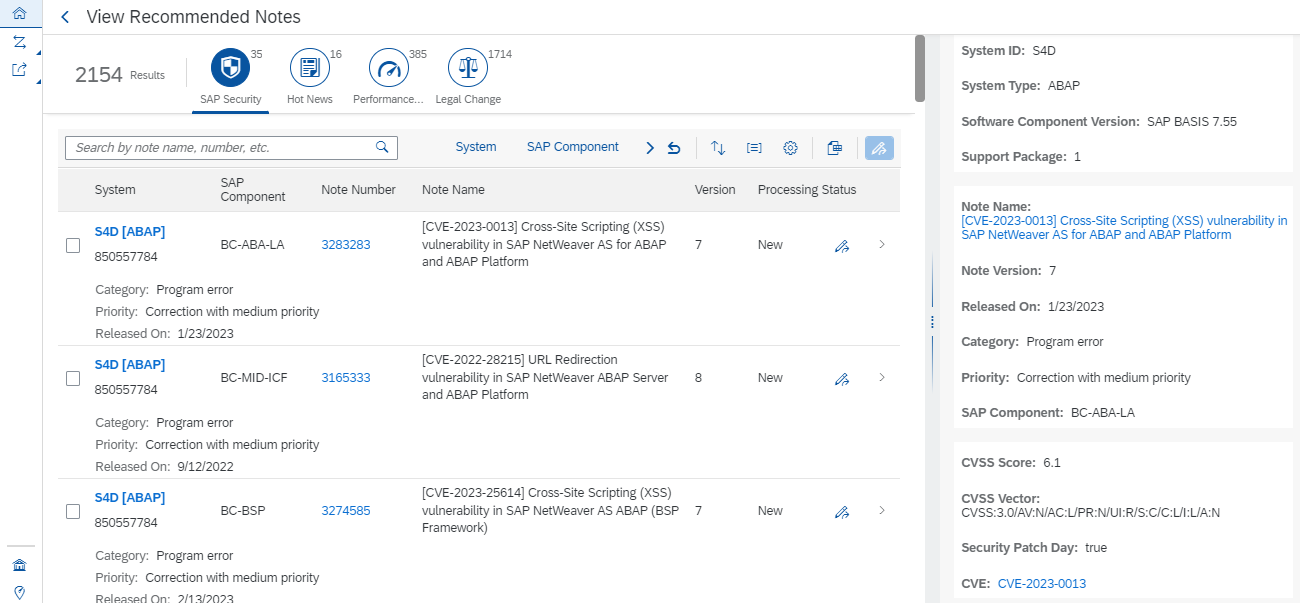
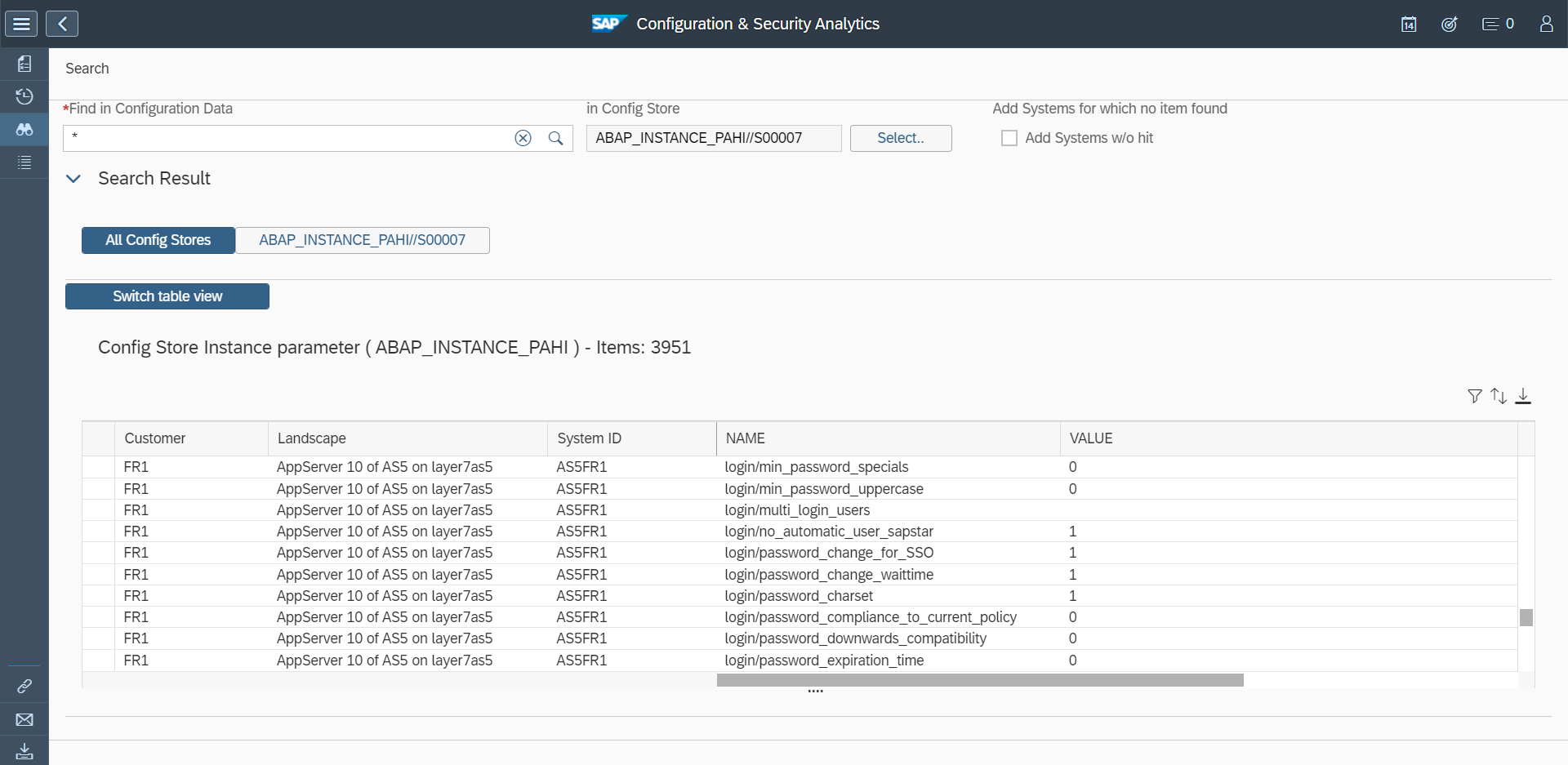
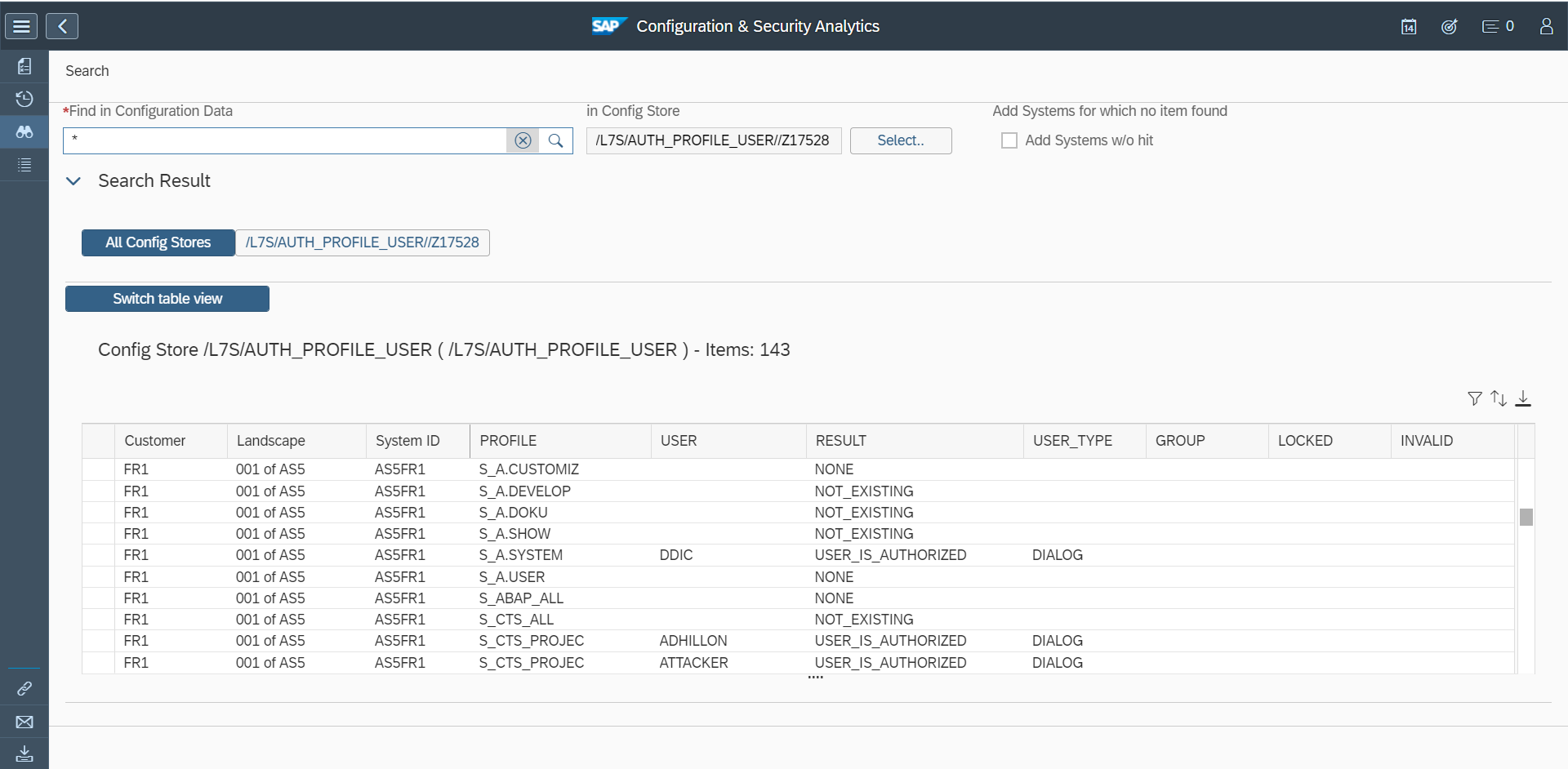
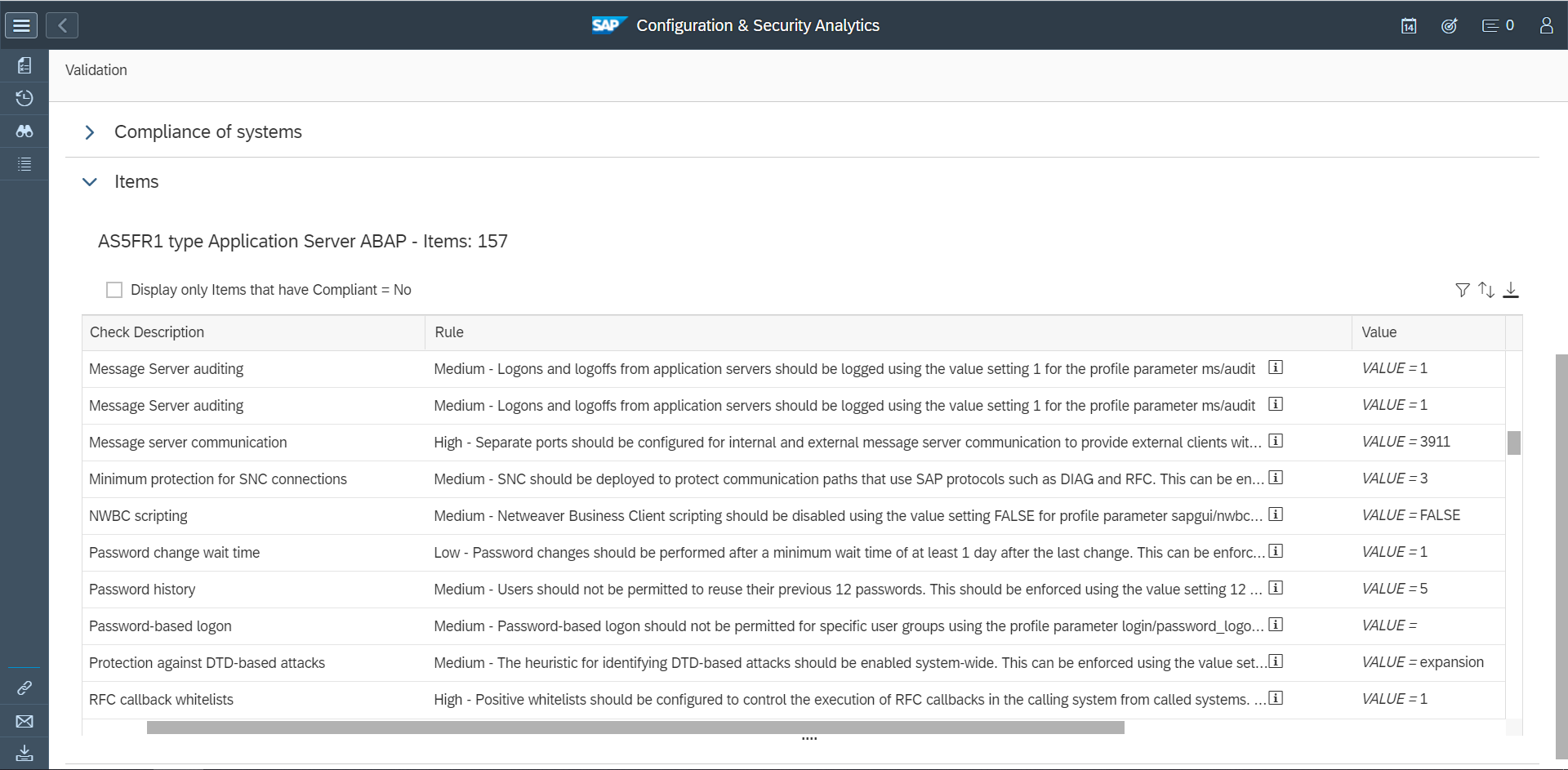
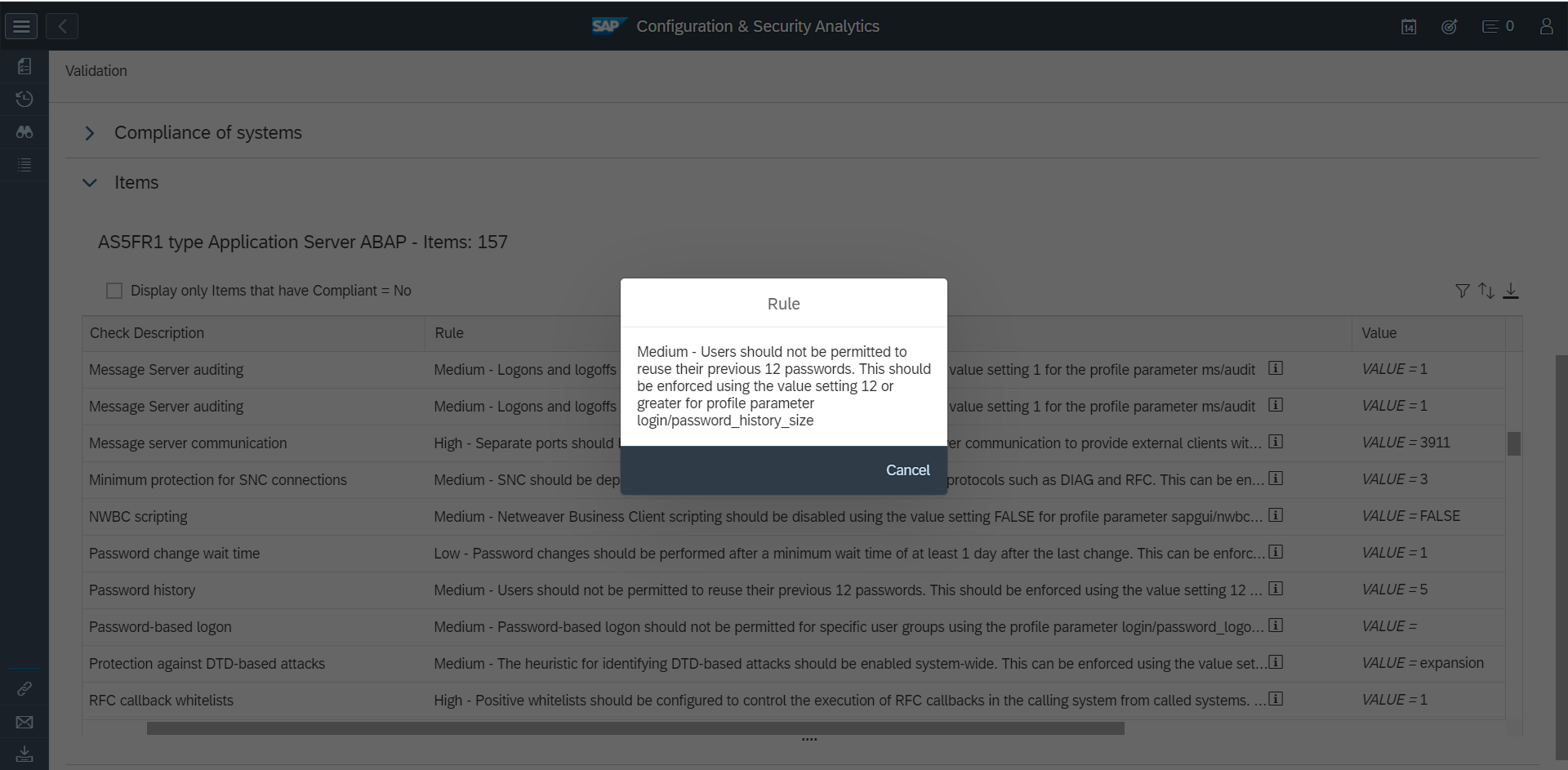
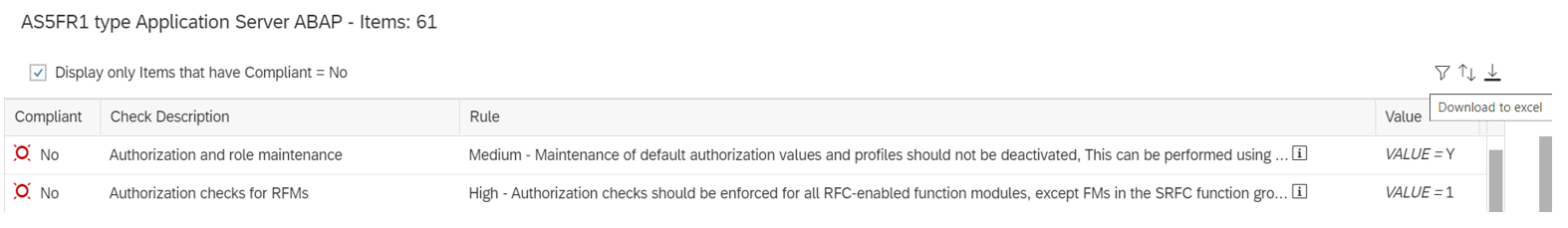
For these reasons, it is often necessary to identify and apply workarounds for SAP CVEs. While SAP provides workarounds for some CVEs, primarily for critical hot news security notes, the majority of SAP CVEs do not include workarounds. However, it is often possible to identify potential workarounds by analysing the details of each note. Often details of impacted programs, reports, function modules, services, or other objects are reported in the Symptom and Solution sections of notes. Object names may also be disclosed in supporting FAQs for security notes, if available.
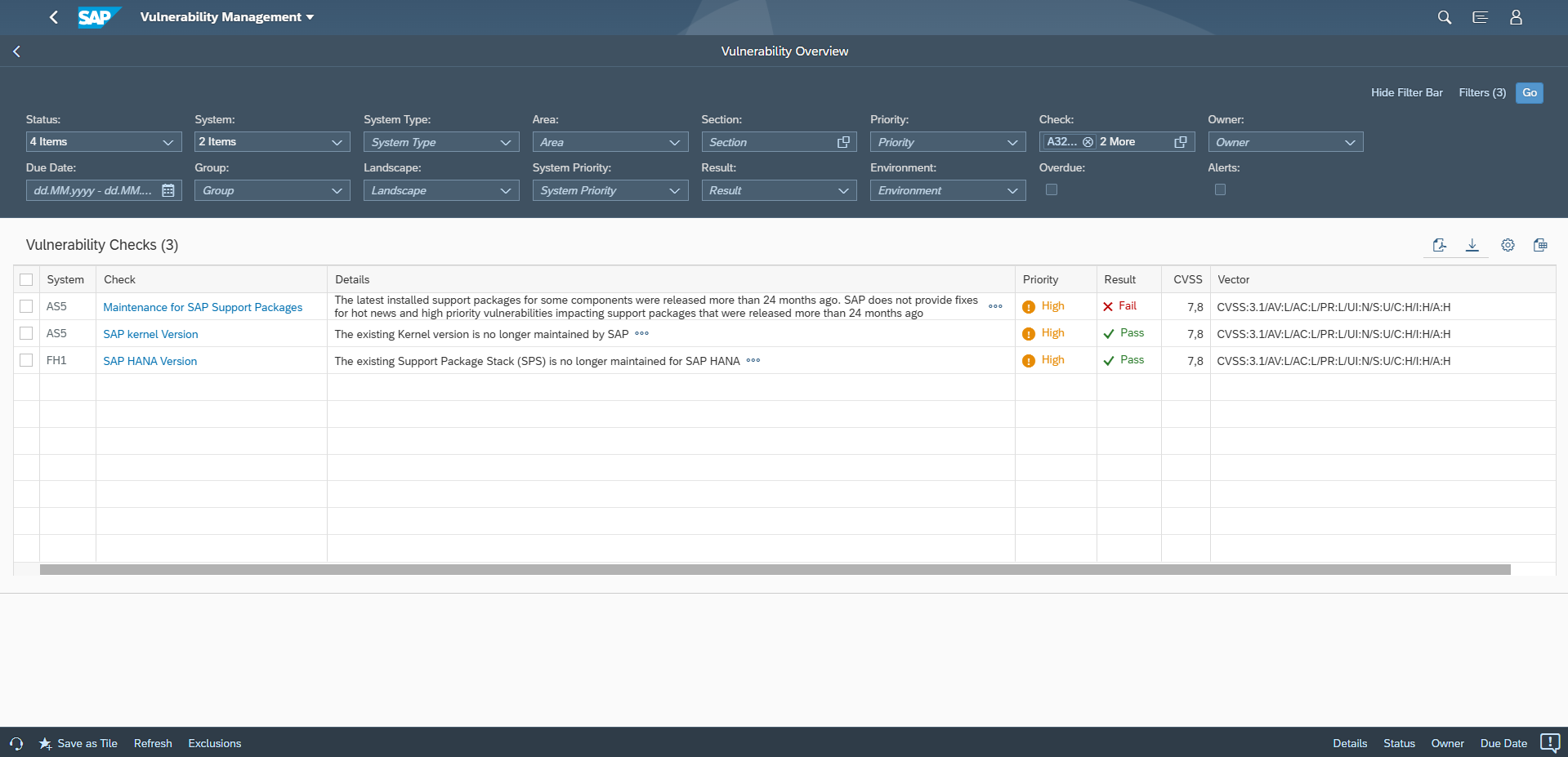
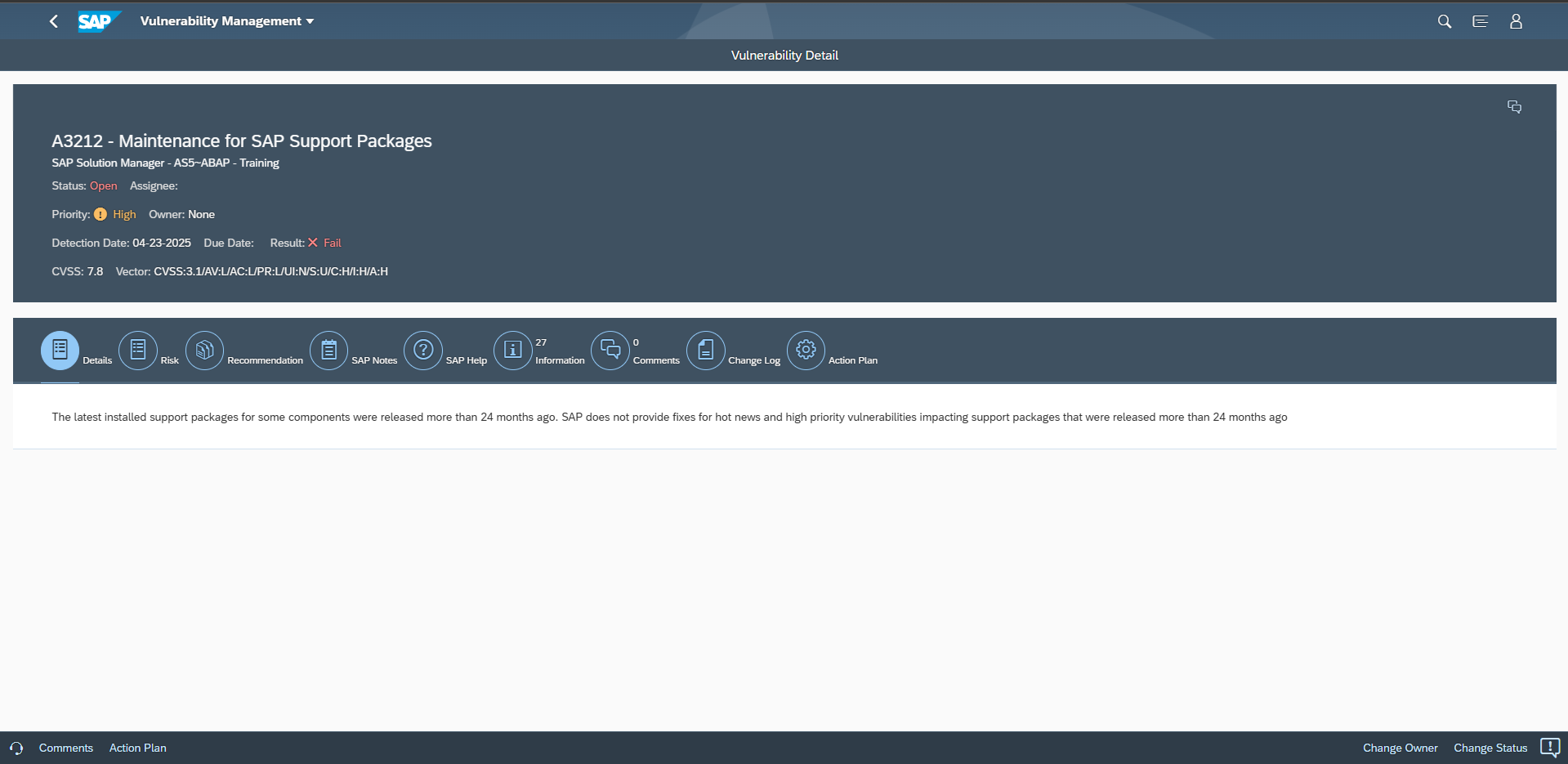
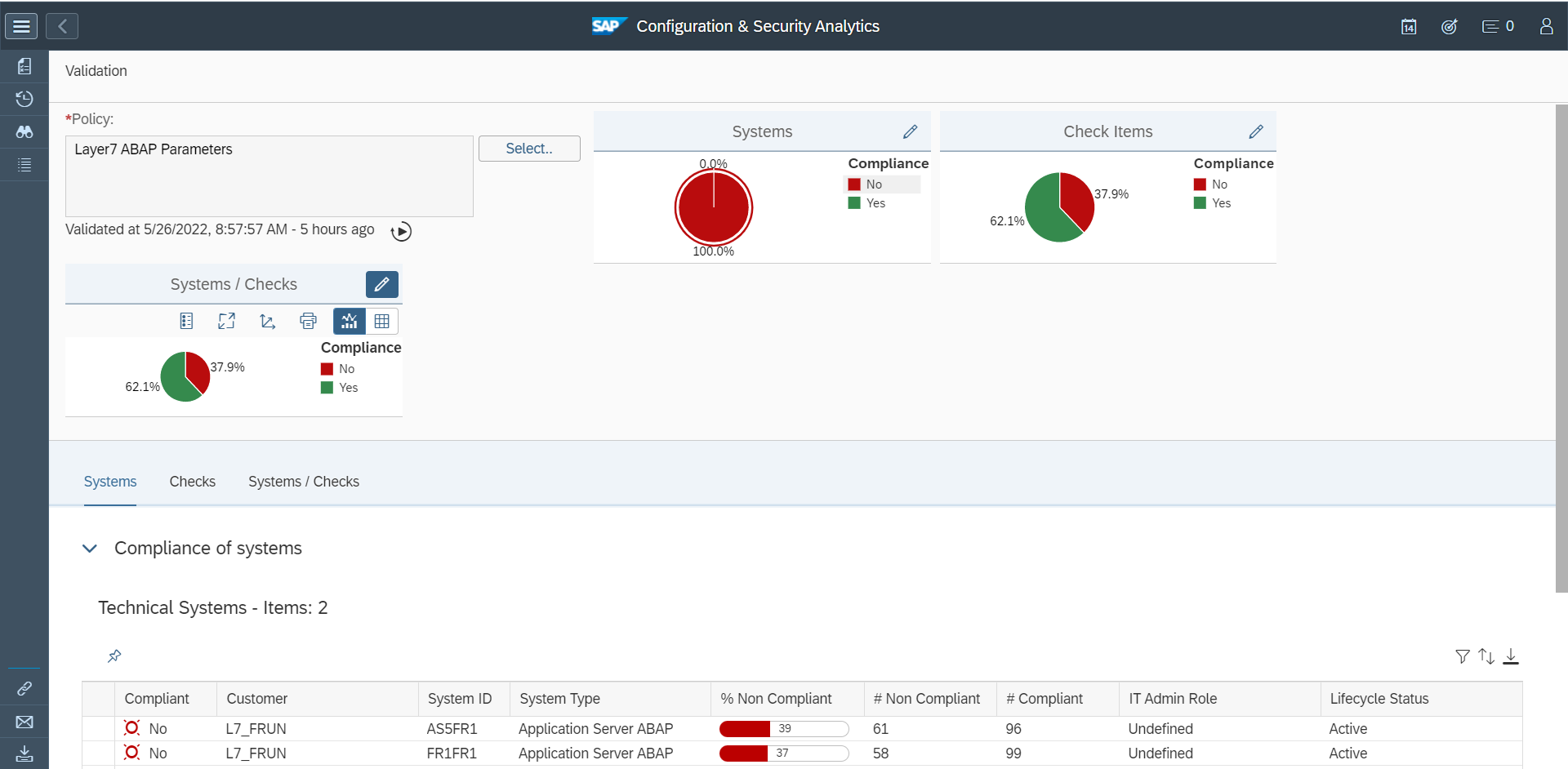
The section for Common Vulnerability Scoring System (CVSS) may also include indicators for potential workarounds. SAP provides a CVSS score for each note based on the values for each key in the framework. The values are included in the CVSS section. The vector string that includes values for each key are also disclosed in CVE databases. Values such as Local (L) for Attacker Vector (AV) may indicate that local access is required for vulnerability exploitation. In this case, network and host firewalls may be sufficient to block external access to SAP ports and services. The value High (H) for Privileges Required (PR) may suggest that administrative privileges are required and therefore restricting administrative access may mitigate the vulnerability.
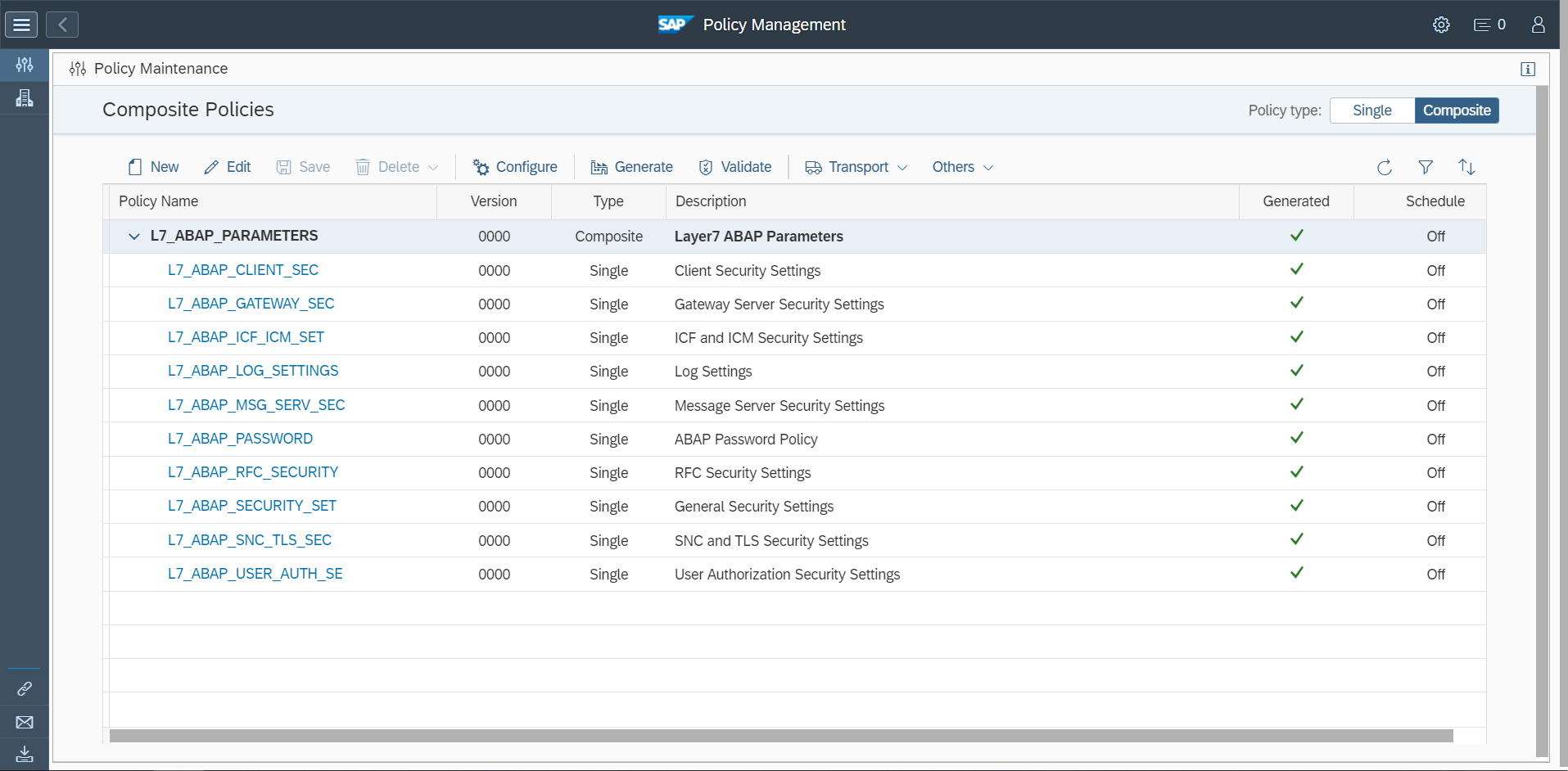
Network filtering using firewalls and managing roles and authorizations are examples of workarounds that can be applied to address SAP CVEs. Other actions may include disabling vulnerable objects, and modifying system settings such as profile parameters to harden SAP systems and eliminate or lessen the exposure to vulnerabilities.
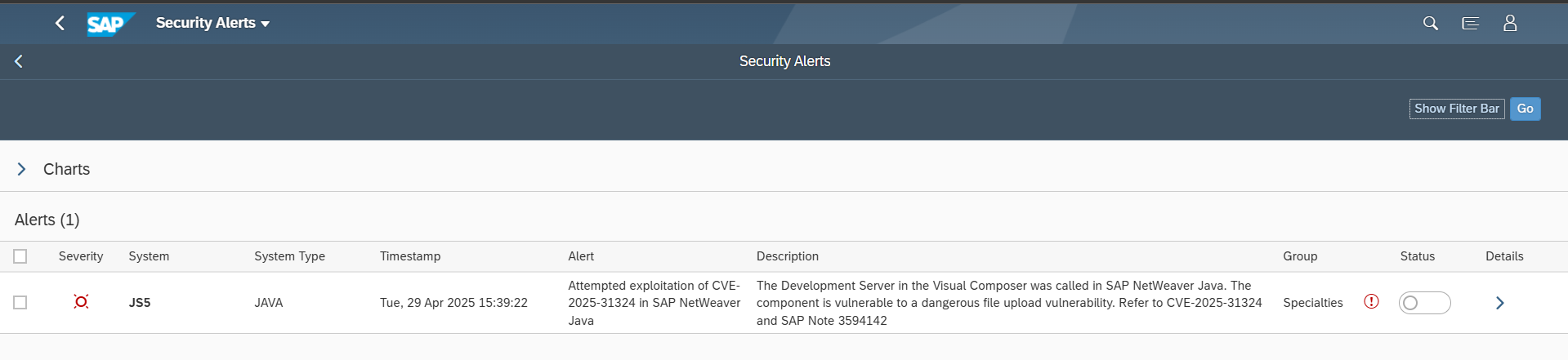
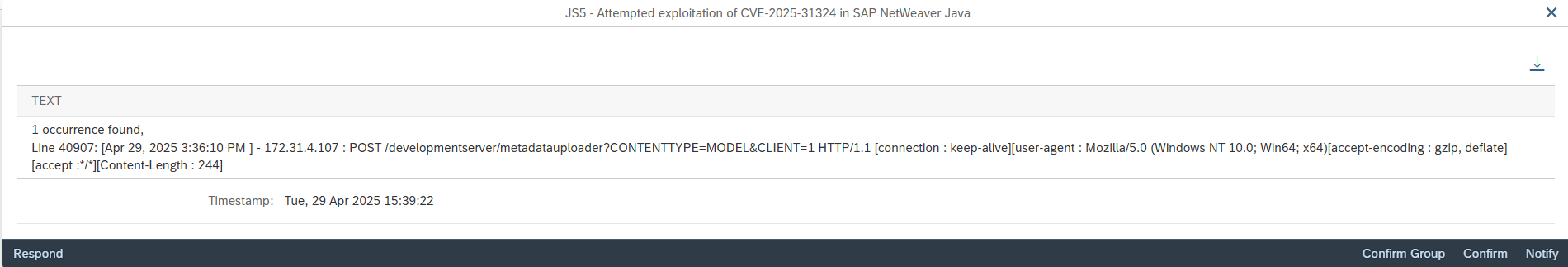
Monitoring and responding to indicators of compromise may also mitigate the risk of some CVEs. Based on the analysis of SAP notes, it may be possible to build and apply patterns for SAP logs using SIEM solutions to detect and alert for the potential exploitation of CVEs.
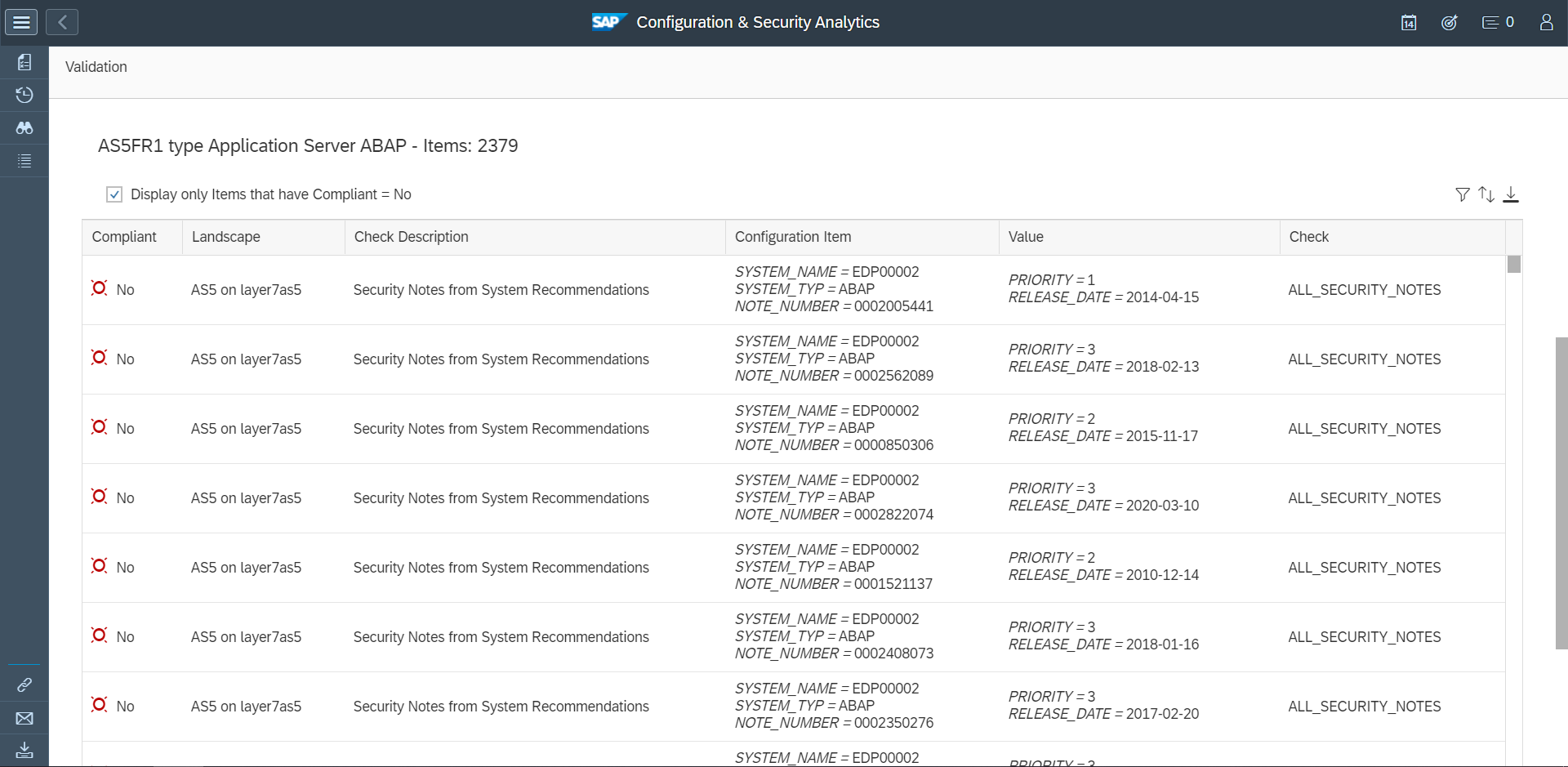
The Cybersecurity Extension for SAP automates the discovery of required SAP security notes based on installed software components and versions in each relevant system. It also includes workarounds for notes where customers are not able to implement automated corrections from SAP. The solution also includes patterns for detecting and alerting for the exploitation of SAP CVEs. Alerts can be forwarded to SIEM solutions for centralized security monitoring and incident response.