Discover Security Patches for your SAP Systems using System Recommendations
One of the most startling facts revealed by the 2015 Cyber Risk Report is that over 44 percent of data breaches stem from the exploitation of known vulnerabilities that are over two years old. This suggests that effective patching can dramatically lower the likelihood of a successful data breach and, when employed with other countermeasures such as system hardening to prevent misconfigurations, it can reduce the risk to negligible levels.
Developing a workable patch management process that addresses the numerous threats confronted by SAP systems presents a formidable challenge for organizations. The need to maintain high levels of availability and control changes that may negatively impact system performance or even lead to software regression often delays the implementation of critical patches. In some cases, it prevents the application of security patches altogether.
The risks posed by weaknesses in patching procedures should not be understated and are borne out by the findings of the HP study. Statistics reveal a direct correlation between ineffective patching and significantly higher levels of susceptibility to security threats that lead to data breaches.
Traditionally, SAP customers have relied upon tools such as RSECNOTE and SAP EarlyWatch Alert (EWA) to identify patches and verify their implementation status. RSECNOTE can be executed using transaction SA38 or ST13. It should return relevant Security Notes and convey whether Notes are successfully implemented, require implementation or are manually confirmed. EWA is a diagnosis report that is run from SAP Solution Manager for managed systems on a weekly schedule. The system configuration checks performed by EWA should include an identification of relevant Security Notes.
EWA, however, no longer performs any meaningful check for security-relevant Notes. Fewer than 10 percent of the 364 Patch Day Notes and Support Pack Notes released by SAP in 2013 were checked and reported through EWA. By 2014, EWA had lost all relevance for security patching: none of the 389 SAP patches released last year were checked by EWA.
RSECNOTE has not fared any better. According to Note 888889 updated in September 2014, the tool is effectively deprecated by SAP and should no longer be relied upon.
RSECNOTE and EWA have been replaced by tools with more powerful calculation engines capable of supporting more detailed analysis of not just Hot News and Security Notes, but also Java patches and Notes for general, performance and legal areas.
These tools include System Recommendations (SysRec), accessible through the Change Management Work Center of SAP Solution Manager. SysRec uses the SAP-OSS RFC destination to connect directly to SAP Global Support and check the status of Notes in managed systems. The results are based on the specific kernel, patch and support package level of systems maintained in the Solution Manager System Landscape (SMSY). This minimizes the risk of both false positives and false negatives.
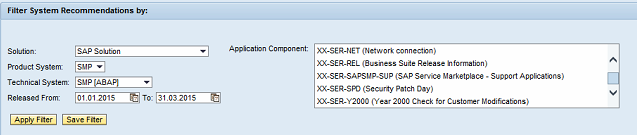
SysRec can be filtered by SAP system, component and date range. Only components are that are applicable to the selected system are displayed by SysRec.
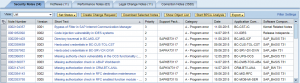
Priority levels and the implementation status of each Note are displayed in the returned results. The Download Notes option can be used to download all or selected Notes from the SAP Service Marketplace. Click on the image below to enlarge.
SysRec can be used to identify both ABAP and Java patches. However, Java patch notes are displayed in the Corrections tab rather than the tab for Security Notes.
The Create Request for Change option is used to trigger a change request to implement the relevant Notes when using ChaRM.
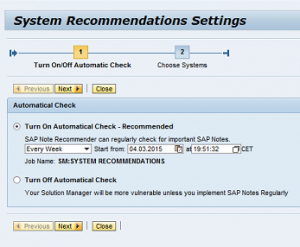
The automated job SM:SYSTEM RECOMMENDATIONS should be scheduled to collect information on the status of implemented Notes from managed systems. The frequency of the automatic check can be set to daily, weekly or monthly.
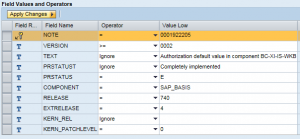
Once corrections are identified and applied, the implementation status of the Notes should be validated across all systems in your landscape. This can be performed using Configuration Validation. The implementation status of Notes is recorded in the PRSTATUS field of the ABAP_NOTES store. The PRSTATUS of completely implemented notes should be E. Therefore, you can define operators to search for Notes implemented in a reference system with the identical component and release dependencies that have the same PRSTATUS. Based on the example below, for instance, Configuration Validation will check that version 2 of Note 1922205 for component SAP_BASIS is completely implemented (PRSTATUS = E), taking into account the release dependencies.
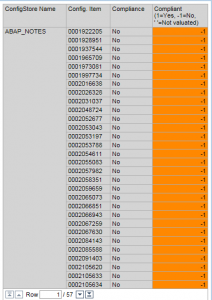
Notes that are not completely implemented in comparison systems are flagged as non-compliant in BW reports generated by Configuration Validation.