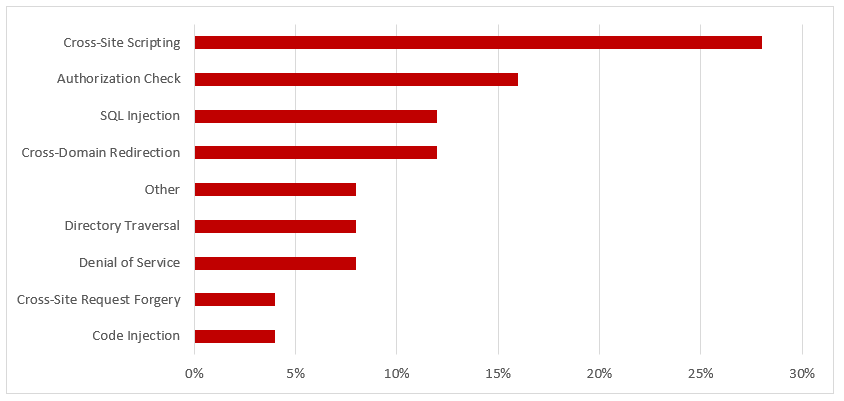
SAP Security Notes, August 2017
Note 2381071 patches a critical cross-site Ajax vulnerability in the Prototype JS library of BusinessObjects. Ajax is a method often used by JavaScripts to exchange data between servers and clients to update parts of web pages without refreshing or reloading entire pages. This minimizes network bandwidth usage and also improves response times through rapid operations. Ajax is an acronym for Asynchronous JavaScript and XML since it’s applied via XmlHttpRequest objects that interact dynamically with servers using JavaScript. XMLHttpRequest objects call server-side objects like pages and web services.
Browsers commonly apply a same-origin policy that prevent pages from accessing external resources that have a different scheme, hostname or port than existing pages. However, same-origin policies can be bypassed using procedures such as cross-origin resource sharing. This could be exploited to transmit or load sensitive data to/ from malicious servers. The cross-site Ajax request vulnerability addressed by Note 2381071 applies to versions 4.0 – 4.2 of BusinessObjects. Corrections are included in the patch levels for each relevant support package.
Note 2486657 deals with a high-risk directory traversal vulnerability in the NetWeaver AS Java Web Container. The Web Container is a component of the J2EE Engine and provides the runtime environment for Java applications including servlets and BSPs.
It receives HTTP requests from clients via the AS Java dispatcher. The requests are processed by applications in the Web Container to access business objects in the EJB Container. Note 2486657 improves input validation for file paths to prevent applications using the Servlet API exposing resources in parent directories or other directories outside the application context.
Other important notes include Notes 2376081, 2423540, 2524134 and 2280932 that patch a code injection vulnerability impacting iviews in Visual Composer, a URL redirection vulnerability in the SAP NetWeaver Logon Application, and a missing authorization check in the Security Provider Service.