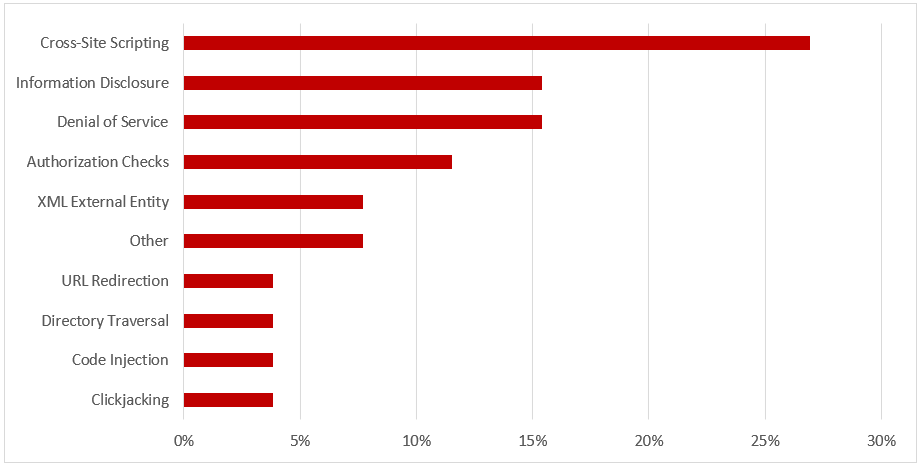
SAP Security Notes, June 2017
Note 2416119 was reissued in June with updated release information and solution instructions. The note provides instructions for maintaining the property URLCheck ServerCertificate in Java Application Servers. The instructions are intended to mitigate the risk of man-in-the-middle attacks by securing client-server HTTPS connections. Certificates signed by Certificate Authorities should be maintained in client keystores to avoid possible failures in HTTPS calls. Detailed instructions are available in the Manual Activities section of Note 2416119 and in the Resolution section of Note 2452615.
Note 2444321 corrects a program error in the SsfVerifyEx function of the SAP Common Cryptographic Library (Common CryptoLib). The error can lead to a failure in authorization and authentication checks for certificates. SAP-delivered applications do not use the vulnerable SsfVerifyEx function. However, SsfVerifyEx may be called by custom programs through the function module SSFW_KRN_VERIFY within the SSFW function group and the method VERIFY_XML within the SAP class CL_SEC_ SXML_DSIGNATURE.
Notes 2313631 and 2389181 deal with Denial of Service vulnerabilities impacting the Launchpad and Central Management Console (CMC) within Business Intelligence and the Instance Agent Service (sapstartsrv), respectively. The Launchpad and CMC are popular portals used to access BI content.
Sapstartsrv is a host-level service for controlling and monitoring SAP processes.
Note 2427292 includes corrections for an information disclosure vulnerability in the Microsoft Management Console (MMC) that could enable attackers to discover the password of hidden users. The credentials could be used to start or stop Java systems via the MMC Web Service.