How to Discover Missing Security Notes for Your SAP Systems using ConVal
Earlier this month, the New York Stock Exchange released a definitive guide to cybersecurity targeted at directors and officers of public companies. Developed with Palo Alto Networks, the guide includes contributions from over thirty-five industry experts and contends with a wide range of questions including legal and regulatory issues, cyber insurance, supplier risks, and incident detection and response. It also discusses investor perspectives towards cybersecurity and cites a recent survey of 130 global institutional investors with an estimated $3 trillion under management that reveals 4 out of 5 institutions would blacklist the stocks of hacked organizations. The full report can be downloaded here.
According to the guide, cybersecurity risk management plans should include several critical countermeasures. One of the most important is effective patch management. In fact, the report points out that “system compromise and data breach are rarely the result of some sophisticated attack that no one has ever been seen before. The bulk of effective attacks use vulnerabilities that have been known for years…..Lack of patching and other standard security issues are normally the culprits” (p95).
This suggests that more active and rapid patching can significantly lower the risk of successful cyber attack. For SAP customers, this calls for the regular application of SAP-delivered security patches to address programming and other flaws. Security fixes are generally released by SAP on Security Patch Day, scheduled for the second Tuesday of every month. Corrections are packaged in Hot News, Security and Support Package Notes that are available through the SAP Support Portal.
There are several options for discovering relevant Security Notes for SAP systems. The first is directly through the SAP Support Portal using preconfigured filters for registered systems and products. Automatic email notifications can be setup through the Portal for newly released Notes.
The second is System Recommendations (SysRec). You can refer to our earlier post for guidance on how to Discover Security Patches for your SAP Systems using System Recommendations.
The third is a standard report available in Configuration Validation (ConVal). Although this approach draws upon SysRec, it consolidates missing SAP patches for all systems across landscapes. This is useful if you need to check the patch status of several systems at the same time. The instructions below provide a step-by-step guide for detecting unapplied SAP Security Notes using ConVal.
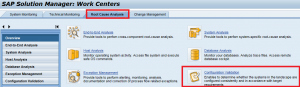
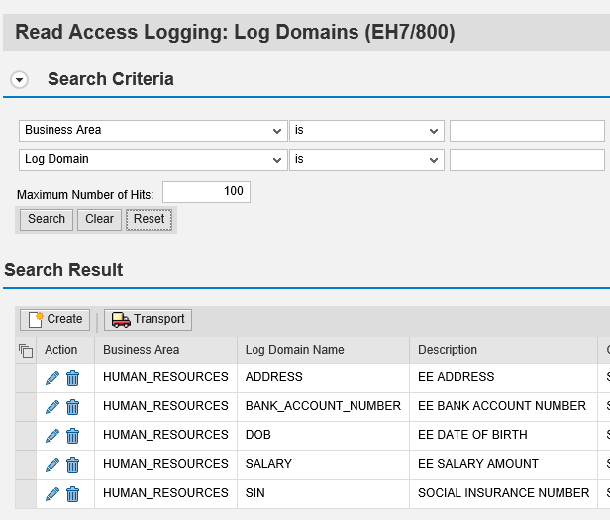
Step 1. Open Configuration Validation from the Root Cause Analysis or Change Management work center in SAP Solution Manager. Click on the image below to enlarge.
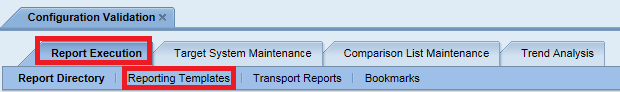
Step 2. Select the Reporting Templates option from the Report Execution tab.
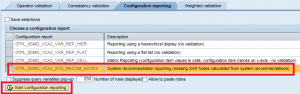
Step 3. Select the report highlighted below and click ‘Start configuration reporting’.
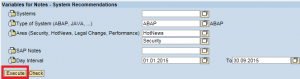
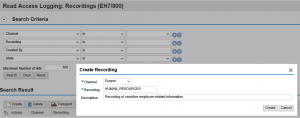
Step 4. Maintain the filters for the report by selecting specific SAP System IDs (SIDs), system types, areas, and the date range. In the example below, we have selected Hot News and Security Notes released between Jan-Sep 2015 for all ABAP systems in the landscape. Click Execute when you are done.
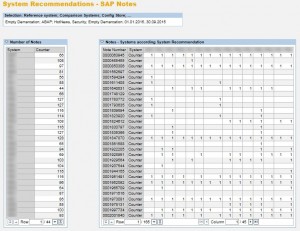
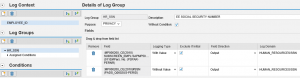
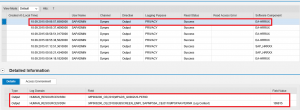
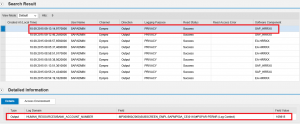
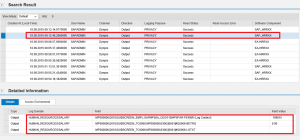
Step 5. Analyze the results. In the report below, the table on the left provides a count of missing Notes by SID. The table on the right displays the unapplied Notes in each row against SIDs in each column.
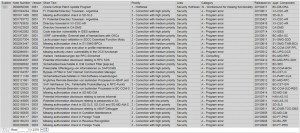
The details of each unapplied Note are provided in the lower section of report. This includes version, description, priority level, and impacted application components. The results can be filtered by priority level to focus on Hot News and High Priority patches. Results can also be exported to .xls and other file formats for further analysis.