How to Block RFC Callback Attacks in Your SAP Systems
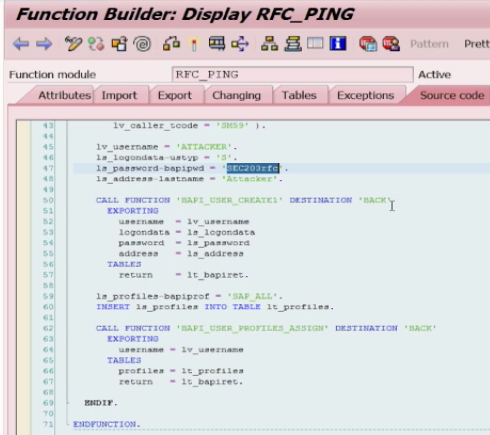
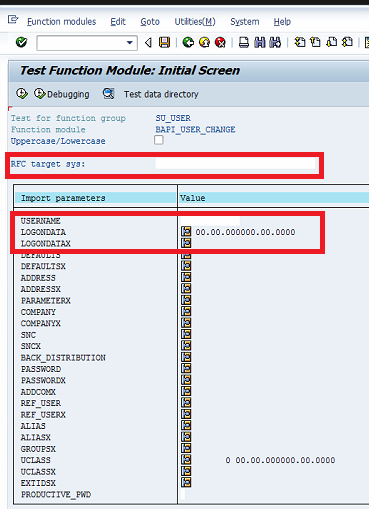
Callback attacks exploit weaknesses in RFC security to execute function modules in calling systems. The impact of such attacks can be severe, ranging from the creation of dialog users with system-wide privileges to modifying or extracting sensitive data. This can occur if client systems execute malicious code within the function modules of connected systems. In the following example, the source code for the standard function module RFC_PING within a compromised system has been modified to create a new user with the SAP_ALL profile in any client system that connects to the system and calls the function module to perform a connection test.
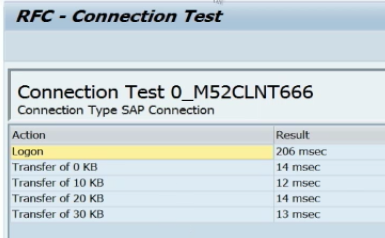
The called system will exploit the callback functionality of RFC calls to firstly execute the BAPI_USER_CREATE1 function module to generate the dialog user in the calling system and secondly, run the BAPI_USER_PROFILES_ASSIGN function module to assign the SAP_ALL profile to the new user. Once this is complete, the attacker will be able to logon directly into the calling system with the new user. Since this is performed in the background, administrators that perform the connection test from the calling system would not be able to detect the exploit based on a review of the test results returned by the system (see below).
Callback attacks can be exploited to hop from development or test systems to productive systems by exploiting insecure RFC destinations between systems in different environments. Such attacks rely on the privileges of RFC users in client systems. Therefore, it’s important to restrict the authorizations of technical users to the minimal required for each scenario.
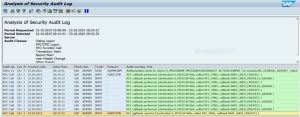
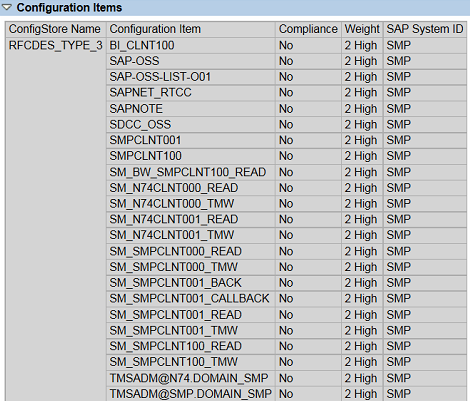
They also count on the ability to call any function module within client systems to run exploits. This should be controlled by enabling positive whitelists for RFC callbacks. Whitelists are controlled by the profile parameter rfc/callback_security_method. Empty whitelists should be enabled by default for all new RFC destinations. For existing destinations, rfc/callback_security_method should be set to 1 and the DUI event should be enabled in the Security Audit Log. This will log RFC callbacks executed within the system. The called function modules are displayed in the message text (see below).
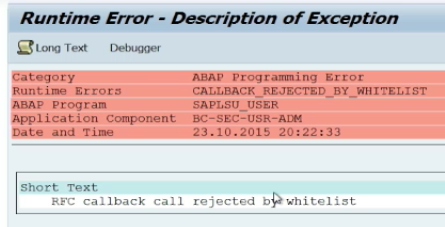
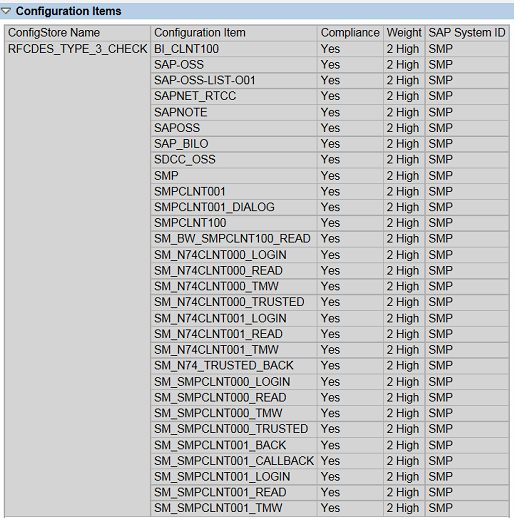
The log results are available in RFC destination maintenance using transaction SM59. Administrators can use the log results to automatically generate whitelists for permitted callbacks to specific function modules for each destination. Once the whitelists are generated, rfc/callback_security_method should be set 2 to enable the whitelists in simulation mode. At this point, the DUJ event should be enabled in the Security Audit Log to record rejected RFC callbacks. The log results should be periodically reviewed to update the whitelists before finally activating all whitelists through rfc/callback_security_method=3. Once activated, callbacks to function modules outside the whitelists are rejected by client systems (see below).