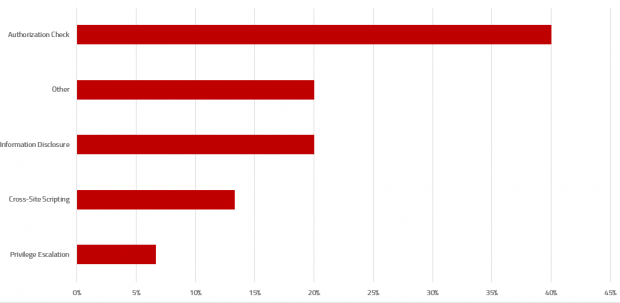
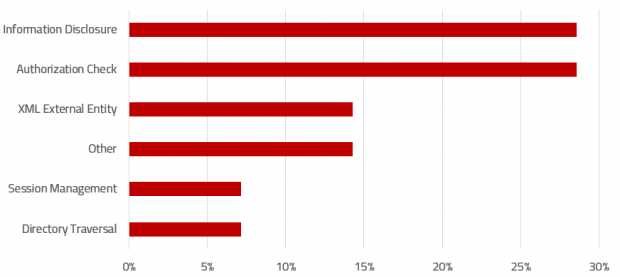
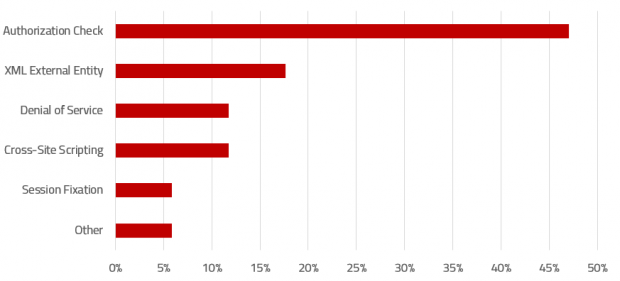
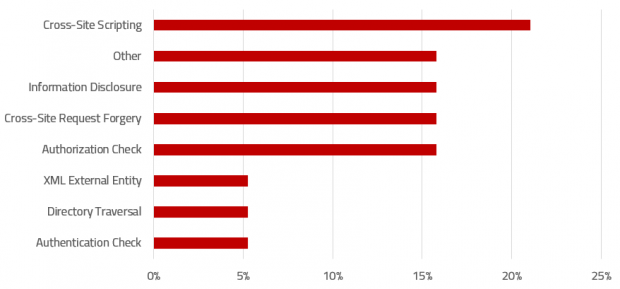
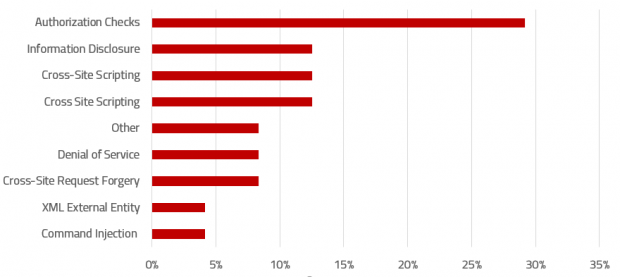
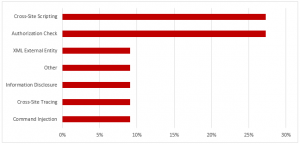
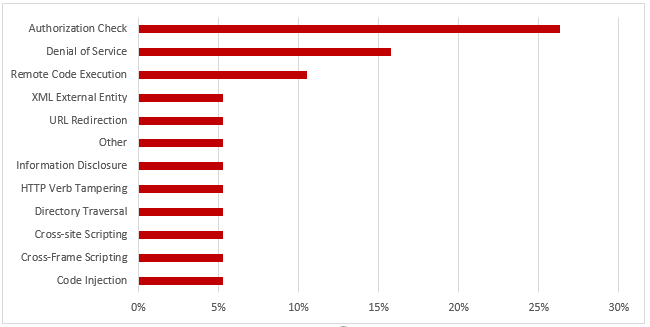
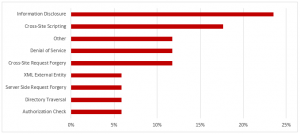
SAP Security Notes, July 2019
Hot News Note 2808158 patches a critical code injection vulnerability in the SAP Diagnostics Agent. The Agent is required to monitor operating systems and discover the database cluster topology from SAP Solution Manager. It is not required for monitoring the security of SAP systems with Solution Manager. Security-relevant data is collected or monitored primarily through RFC connections maintained between Solution Manager and managed systems.
The vulnerability impacts the OS Command Plugin in transaction GPA_ADMIN. The transaction is used to create and maintain guided procedures. Note 2808158 provides a patch for the LM_SERVICE in SP levels 05-09 of Solution Manager 7.2.
Note 2774489 addresses a high priority OS command injection vulnerability in SAP Process Integration (PI). ABAP Tests Modules of PI could enable attackers to execute privileged OS commands. The relevant support packages listed in the note should be applied to remove the vulnerable source code in the modules.