SAP Security Notes, July 2017
Note 2442993 deals with a high-risk vulnerability in the Host Agent for SAP HANA. The Host Agent is automatically installed with every SAP instance on NetWeaver 7.02 and higher. The stand-alone component is used for controlling and monitoring SAP and non-SAP instances, databases and operating systems. Note 2442993 recommends upgrading to version 7.21 PL25 to remove a vulnerability in earlier versions that could be exploited by attackers to shutdown the Host Agent through malicious SOAP requests used for cross-platform communication via transport protocols such as HTTP and XML. A shutdown of the Host Agent could interrupt the availability of SAP services and explains the high CVSS score of 7.5/10 within the Note. Detailed instructions for upgrading the Host Agent are available in Note 1031096. The command ./saphostexec -upgrade should be performed after steps 1-4 outlined in the installation section of the Note.
Note 2476601 has an even higher CVSS score of 8.1/10. The note removes missing authentication checks in the SAP Point-of-Sale (POS) Xpress Server. The POS Xpress Server integrates components within the SAP POS suite including applications, clients and databases. Xpress Servers with Internet connectivity are particularly vulnerable to exploits targeting the missing authentication checks patched by the Note.
Note 2478377 recommends upgrading Sybase products impacted by Sweet32 attacks that target design weaknesses in some 64-bit block ciphers such as Triple-DES and Blowfish commonly used by the Internet protocols TLS, SSH and IPSec. The Sweet32 attack was discovered by researchers from the French National Research Institute for Computer Science (INRIA) in 2016 and can be used to recover HTTP session cookies in some specific scenarios.
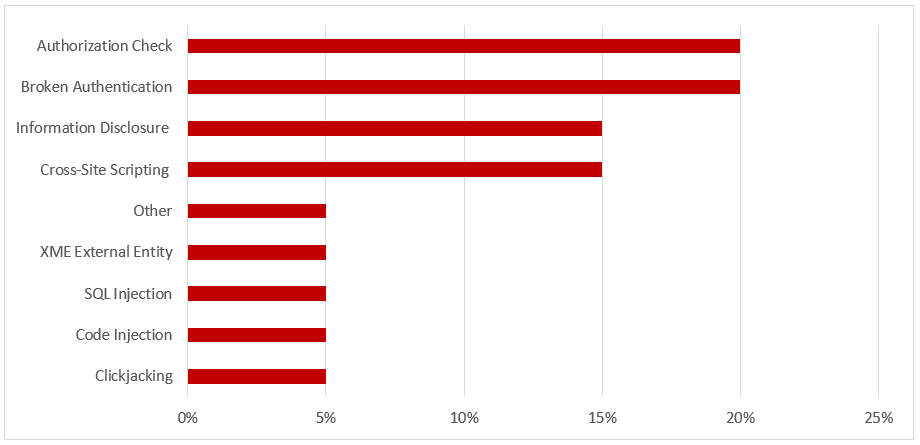
Notes 2100926, 2184221 and 2185122 introduce switchable authorization checks for certain RFC enabled function modules in Business Warehouse, Public Services, and Master Data Governance. Switchable authorization checks supplement checks for the S_RFC authorization object and should be activated using transaction SACF.