Securing Administrative Access in SAP AS Java
The misuse of administrative privileges is a common method used by attackers to compromise applications and propagate attacks to connected systems. The elevated privileges granted to administrative accounts are a prized target for attackers and provide a fast path to accessing or modifying sensitive data, programs and system settings.
User privileges for Java applications are administered through the User Management Engine (UME) in the SAP NetWeaver Application Server for Java (AS Java). The UME is the default user store for AS Java and can be configured to use LDAP directories, AS ABAP, or the system database of AS Java as the data source for user-related data.
UME permissions granted to users can include administrative actions such as Manage_All, Manage_Roles, Manage_Users, Manage_User_Passwords, and other privileged functions. Administrative actions are bundled into roles and granted to users organized into user groups. Standard user groups include the Administrator group, as well as groups such as SAP_J2EE_ADMIN and SAP_SLD_ADMINISTRATOR. The latter includes users with administrative access to the System Landscape Directory. Standard roles include Super Admin and, for Enterprise Portals running on AS Java, Portal System Admin, Portal User Admin and Portal Content Admin.
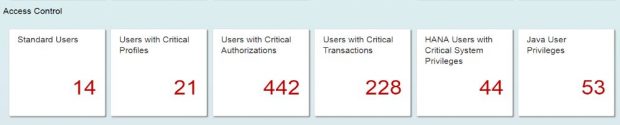
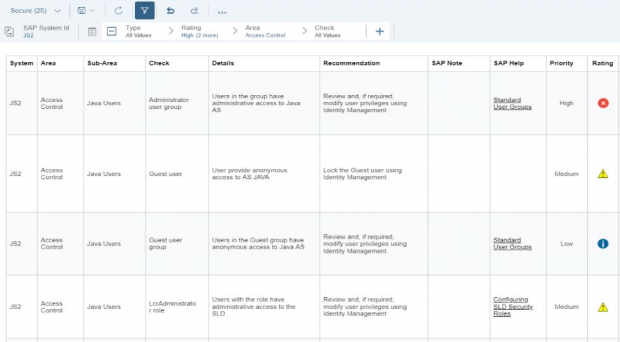
Access to administrative roles and rights in AS Java should be granted to required users only, based on the principle of least privilege. Users with administrative privileges in AS Java systems can be detected using the Cybersecurity Extension for SAP Solution Manager. The results are displayed in security reports and dashboards. Alerts are also triggered by the extension for new users granted privileged roles and actions for possible privilege escalations. The extension also detects users with administrative rights in ABAP and HANA platforms, as well as SAP-compatible databases including IBM, Microsoft, Oracle and Sybase.