US-CERT Issues Alert for SAP Invoker Servlet Vulnerability
US-CERT published an alert yesterday to warn SAP customers of the dangers posed by the invoker servlet vulnerability in AS Java systems. According to the alert, there is evidence to suggest that SAP systems at 36 organizations have been exploited by the vulnerability. The organizations are based in the United States, United Kingdom, Germany, China, India, Japan, and South Korea, and operate in industries that include oil & gas, telecommunications, utilities, retail, automotive and the pubic sector.
The invoker servlet vulnerability arises when servlets can be called directly either by servlet name or by fully-qualified class name. This can be exploited to bypass authentication and authorization rules defined in the web.xml files of Java applications. In the cases referenced by the US-CERT alert, attackers appeared to have exploited the invoker servlet to call a Java component that enabled them to execute OS commands and create user accounts in SAP systems.
The vulnerability was patched by SAP in 2010. SAP also modified the default configuration of AS Java to disable the invoker servlet in versions 7.20 and later. Corrections were provided in Notes 1445998 and 1467771. The evidence of the active exploitation of the invoker servlet vulnerability five years after the underlying flaw was patched by SAP demonstrates that the greatest risk posed to SAP systems is the exploit of known weaknesses rather than so-called zero-day vulnerabilities.
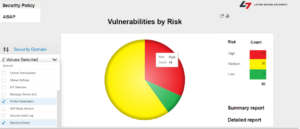
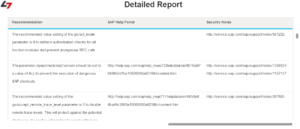
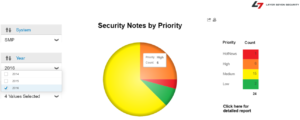
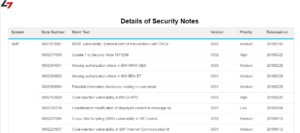
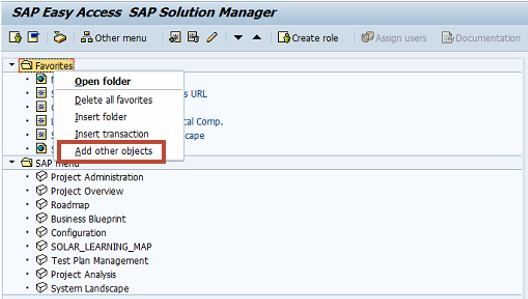
The invoker servlet should be disabled at a global level by setting the EnableInvokerServletGlobally key to false. The key is located in the global properties of each J2EE instance. You can follow the three steps below to discover systems in your landscape vulnerable to the exploit using SAP Solution Manager.
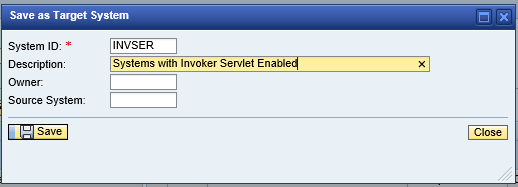
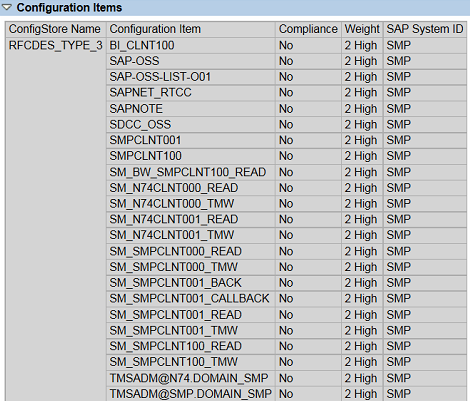
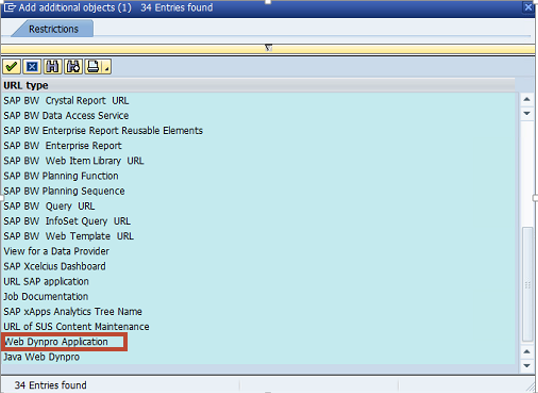
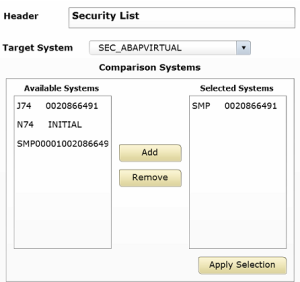
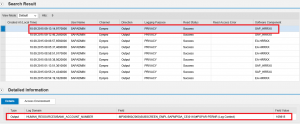
1. Create a target system in Configuration Validation to check the value of the key for all systems using the servlet_jsp store. See below.
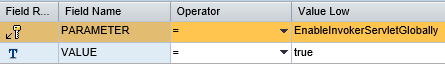
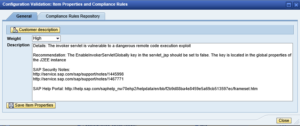
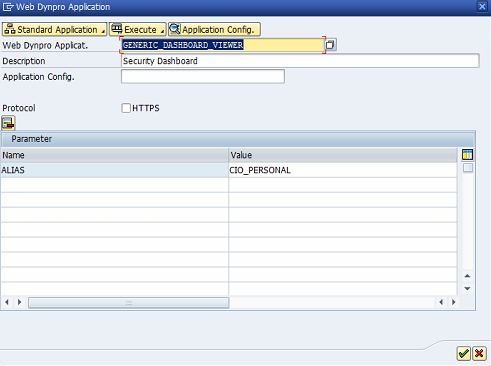
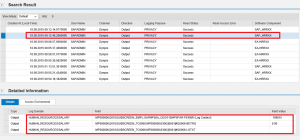
2. Edit the target system by removing all parameters in the servlet_jsp store except EnableInvokerServletGlobally. Set the value for the key to true and maintain the weight/ info. See below.
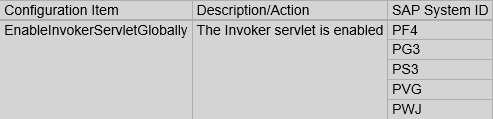
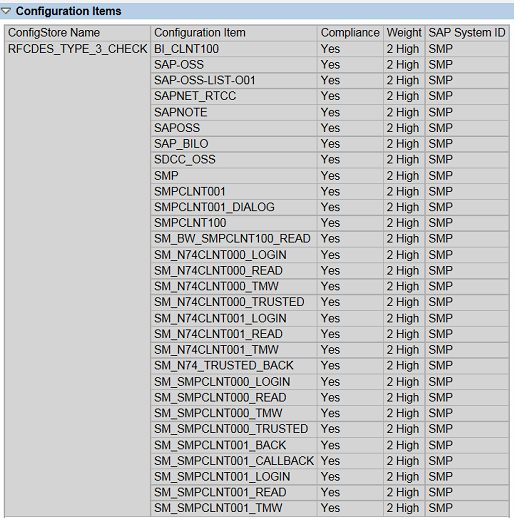
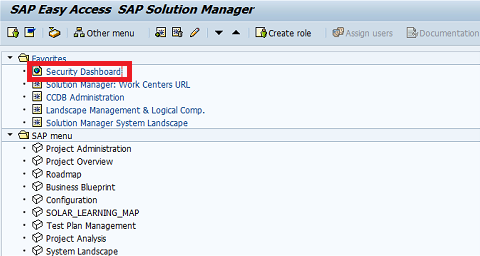
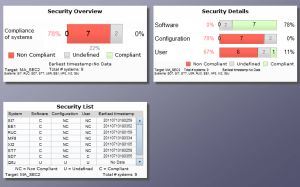
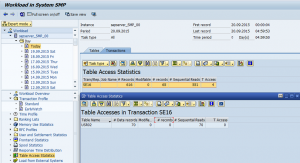
3. Run the weighted validation report for all Java systems and review the results of systems with the EnableInvokerServletGlobally set to true. See below.
The invoker servlet vulnerability is one of the 500+ checks performed by security rulesets provided by Layer Seven for ABAP, Java, HANA, and database systems. The rulesets can be imported into your Solution Manager systems in seconds to perform daily automated scans for vulnerabilities in SAP systems. To learn more, contact Layer Seven Security.